Fraud resistant biometric financial transaction system and method
a biometric and financial transaction technology, applied in the field of fraud-resistant biometric financial transaction authentication systems and methods, can solve the problems affecting the accuracy and speed of financial transactions, and limiting the ability to tell an impostor from an authentic person, so as to reduce defeat the system. , the effect of reducing the rejection rate of true authentics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
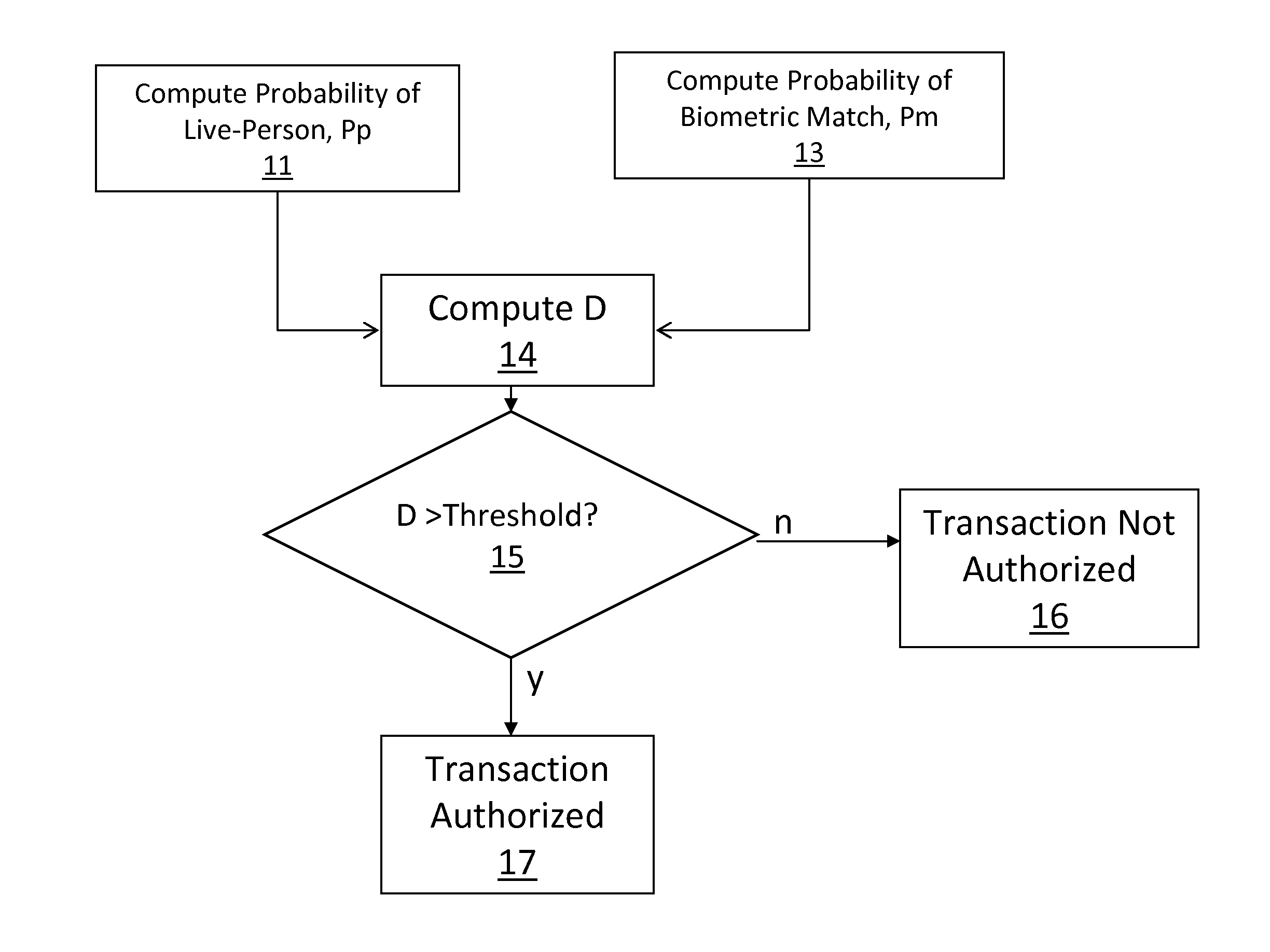
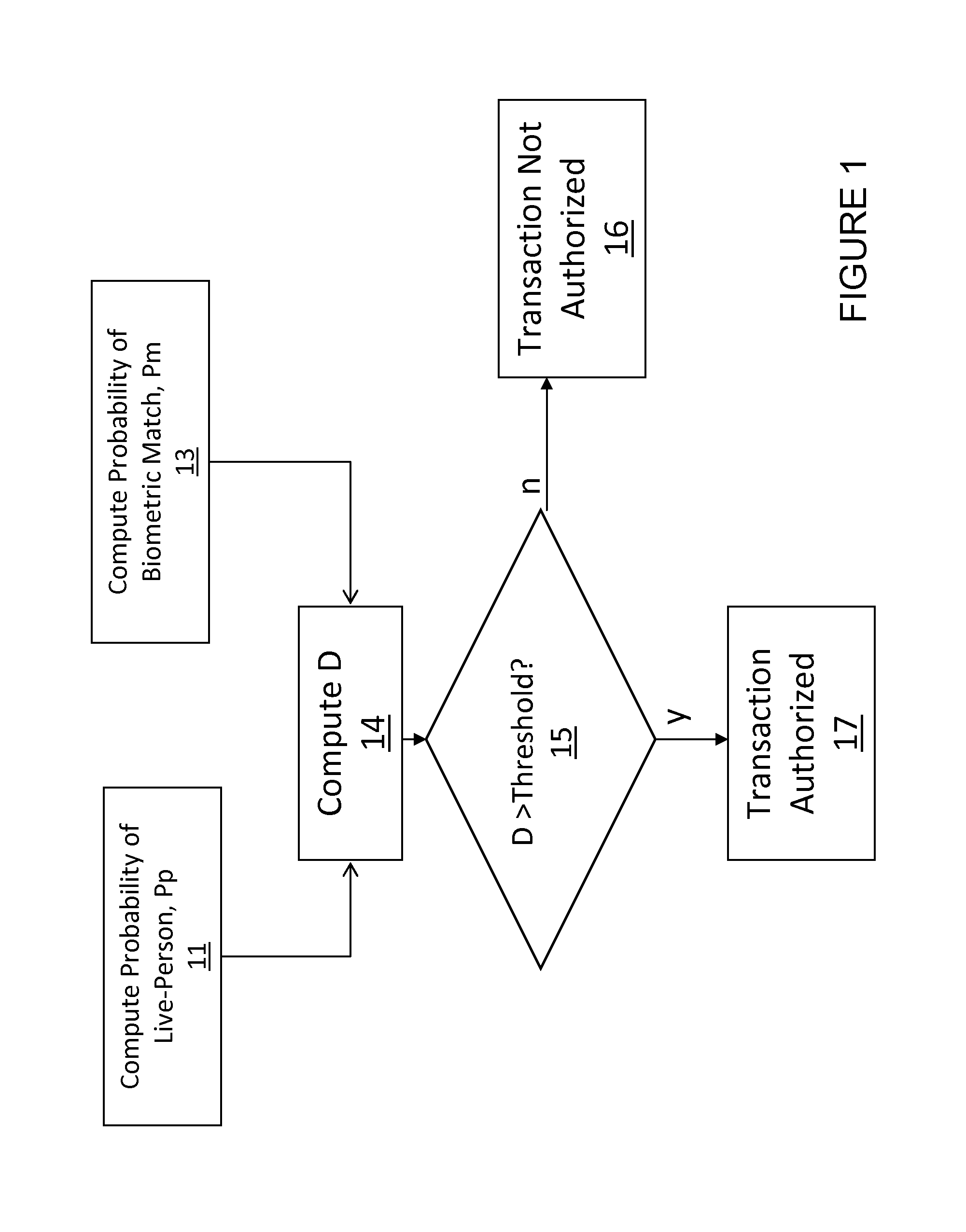
[0036]Referring first to FIGS. 1 and 2, the overall process is to compute 11 the probability, Pp, of a live person being presented, compute 13 the probability of a biometric match, Pm, computing 14 D according to the aforementioned formula, wherein at decision block 15 if D exceeds a preset threshold, the transaction is authorized 17 or, if D does not exceed the preset threshold, the transaction is not authorized, 16.
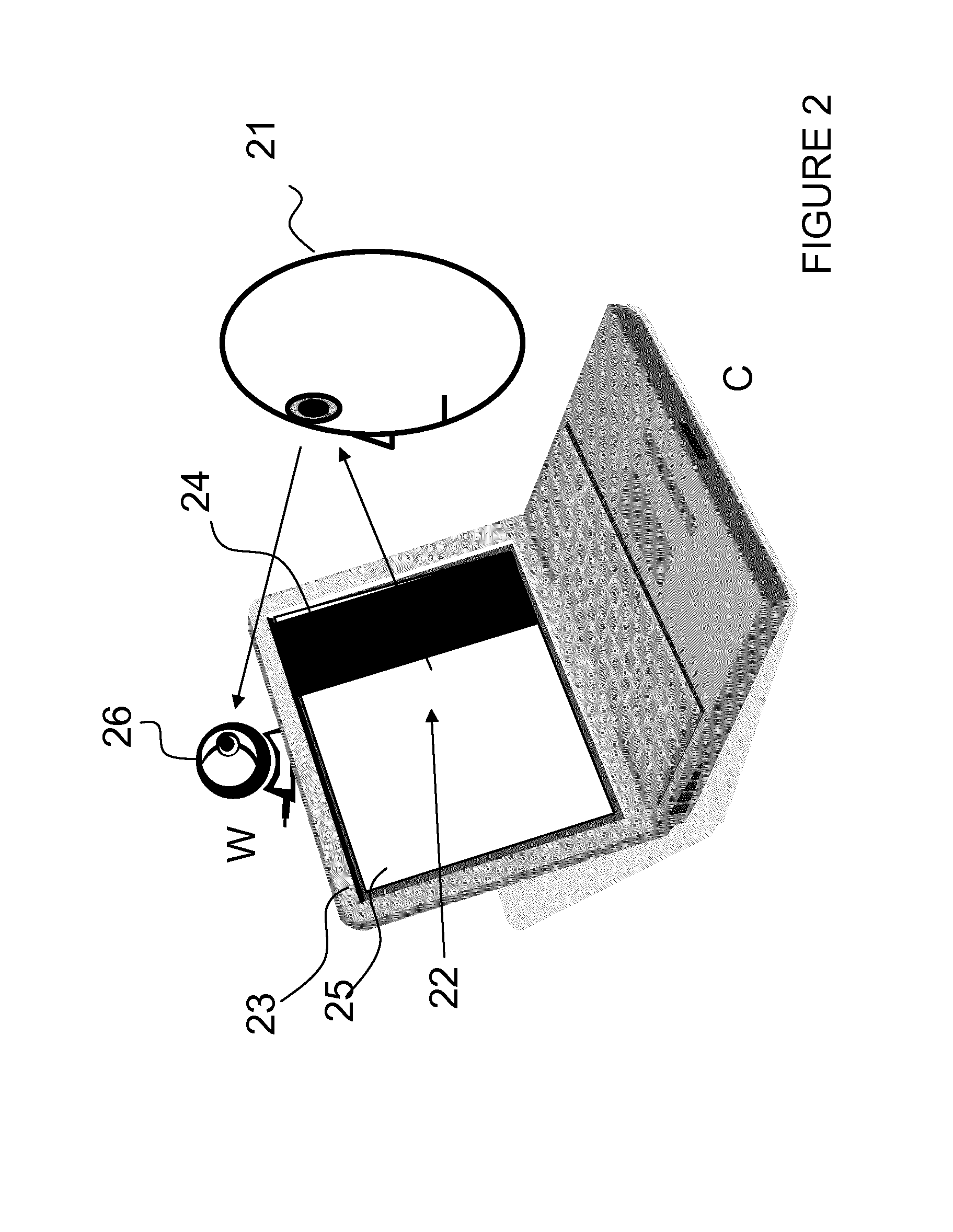
[0037]Referring now to FIG. 2, an example of a system and method of obtaining data used for calculating the probability of a live person 21 is shown. First, an image is displayed on a screen 23 with a black bar 24 on the right and a white area 25 on the left, and an image from a web camera 26 that the person 21 looks at is recorded. A second image is displayed on the screen (not shown), but this time the black bar is on the left and the white area is on the right and a second image from the web-camera 26 is recorded.
[0038]The difference between the two images is recorde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com