Patents
Literature
57results about How to "Reduce crime" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Fraud Resistant Biometric Financial Transaction System and Method
ActiveUS20100014720A1Out of controlReduce scrap rateElectric signal transmission systemsImage analysisLivenessBiometric data
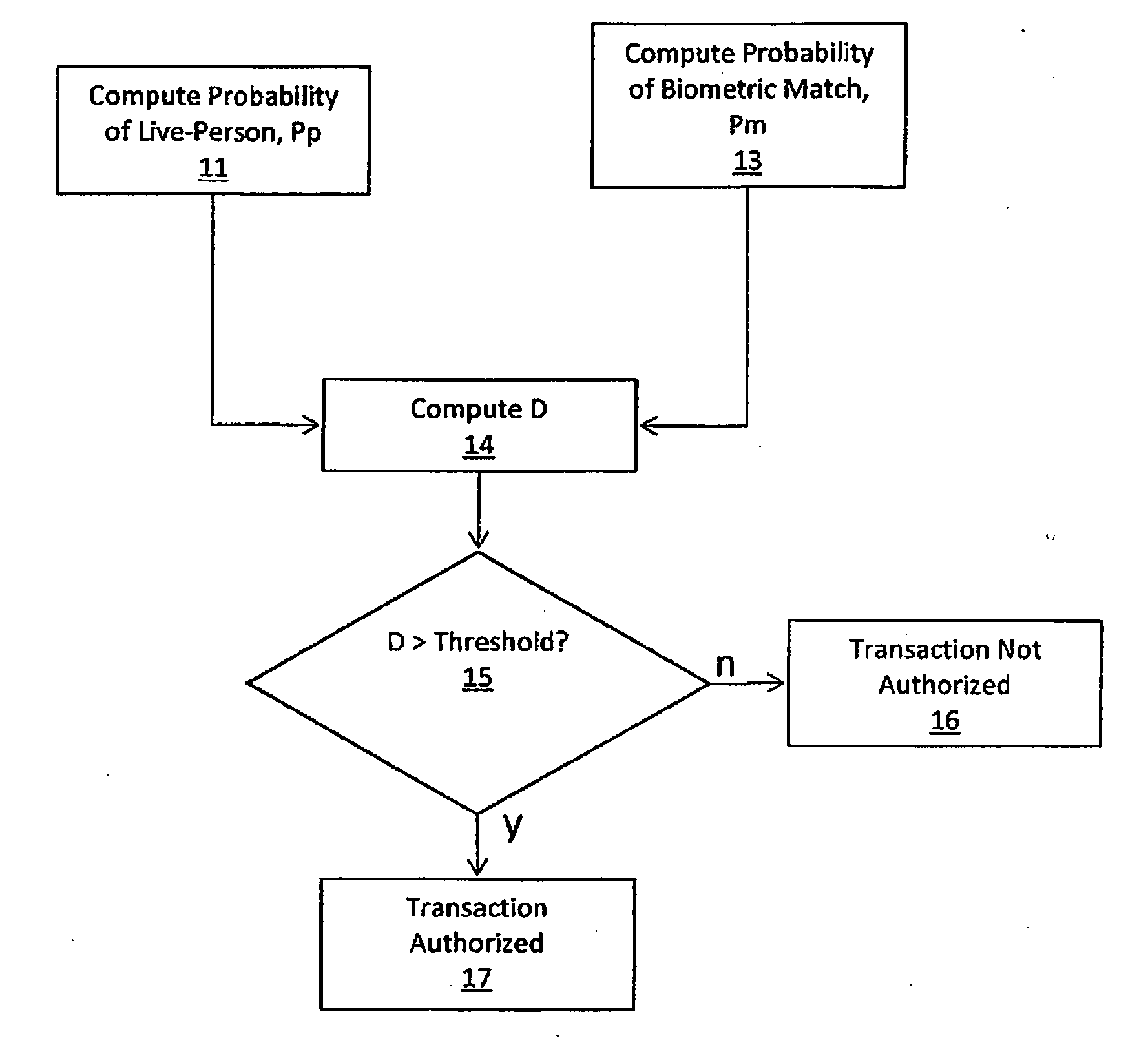
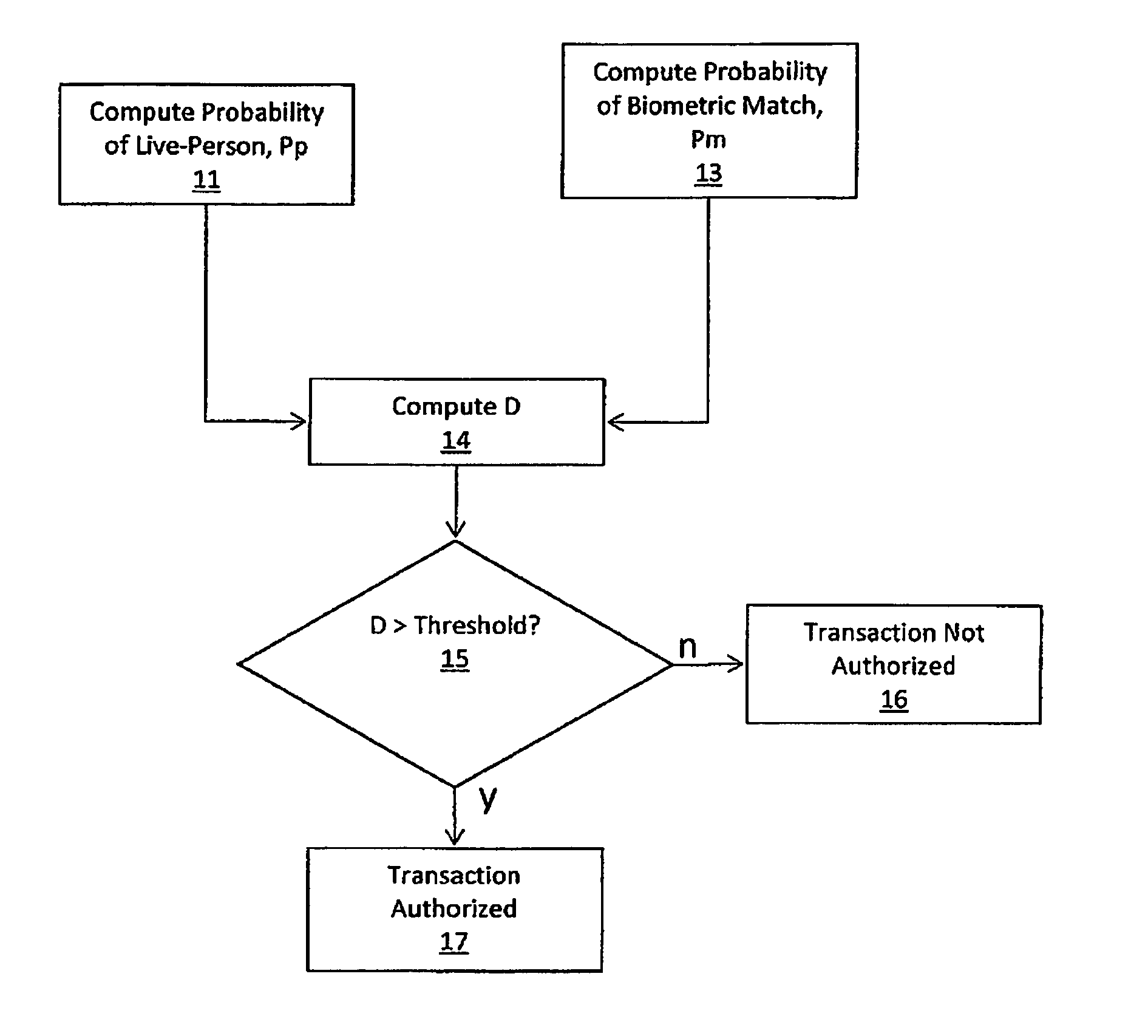
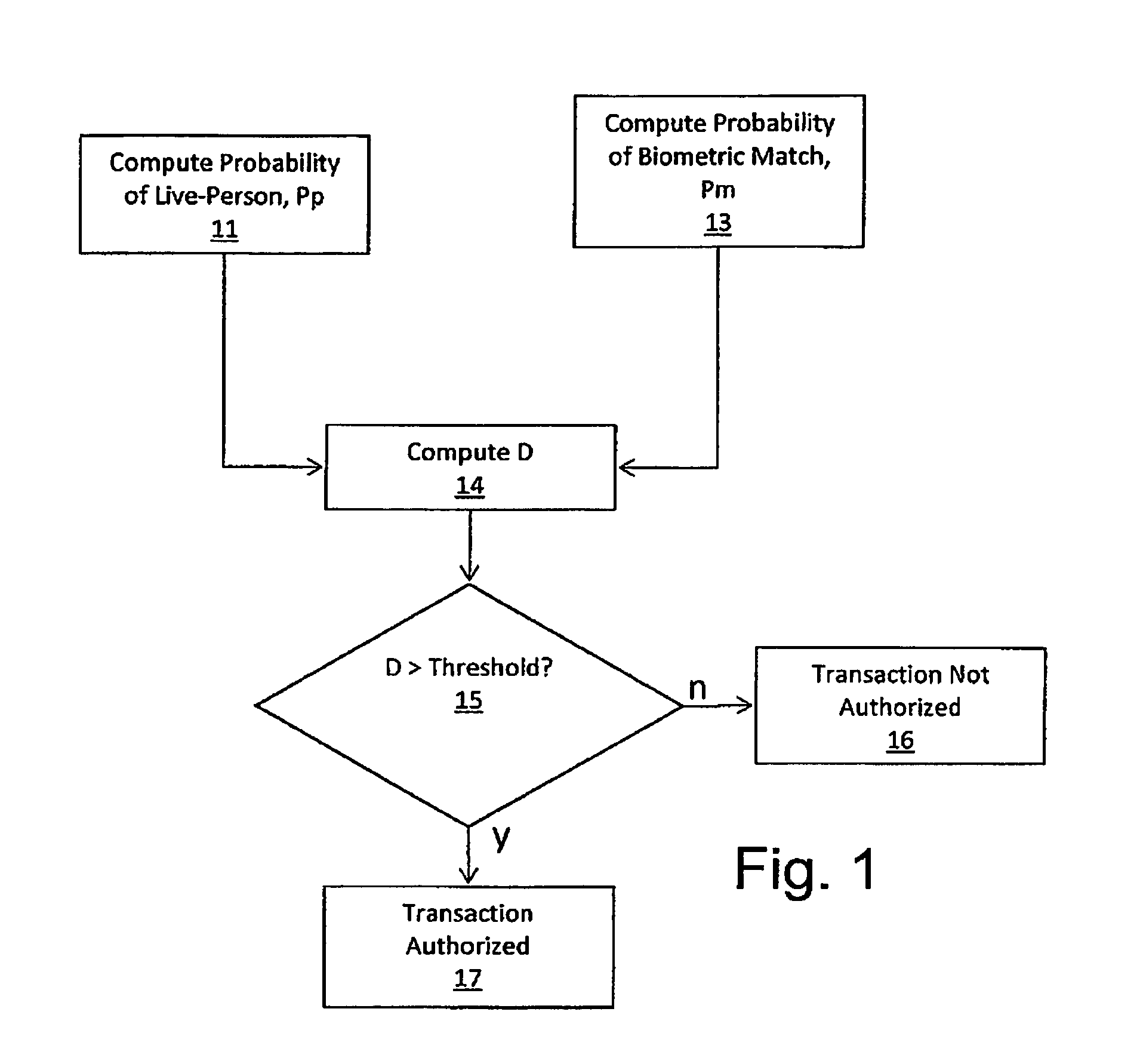
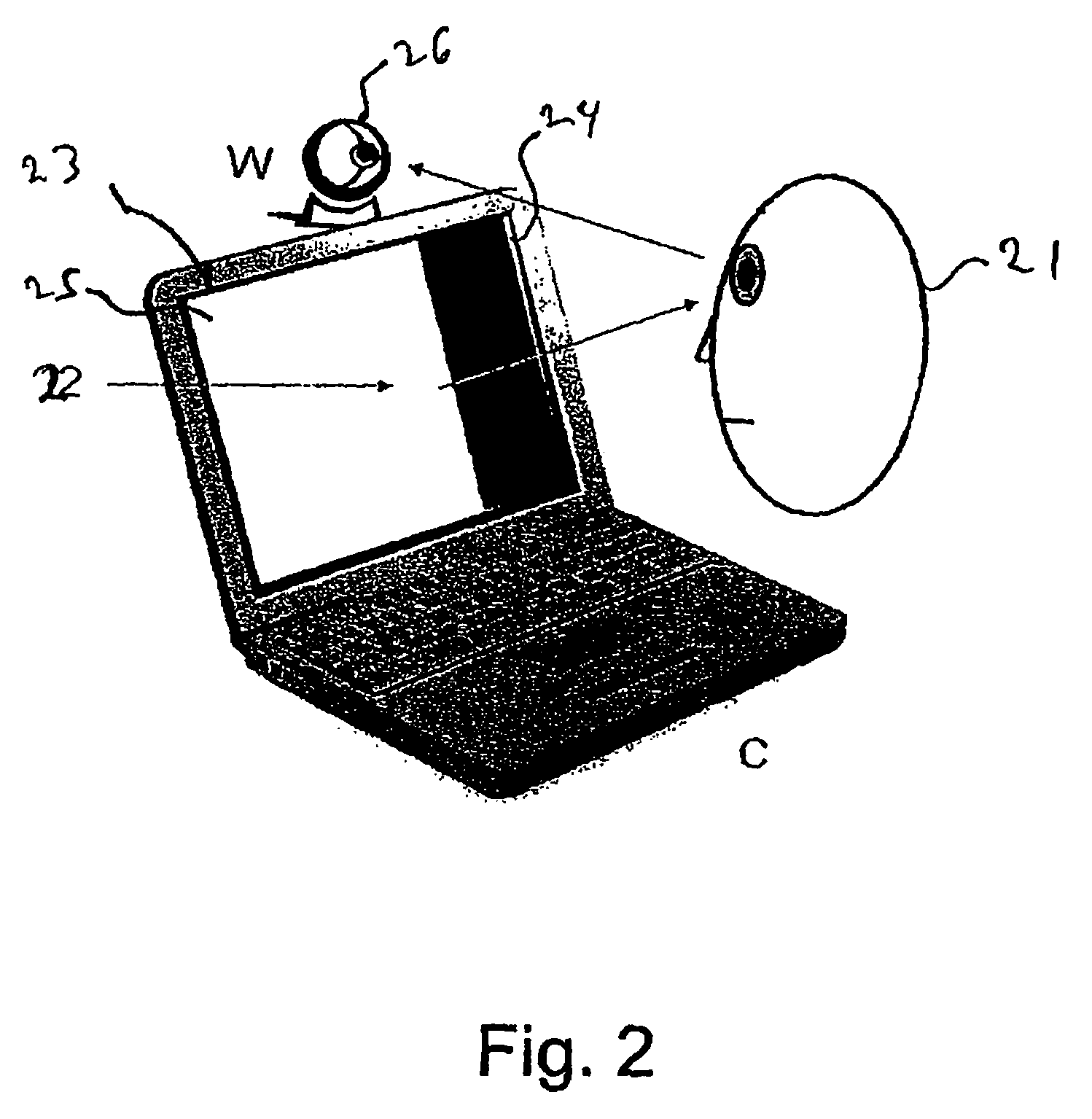
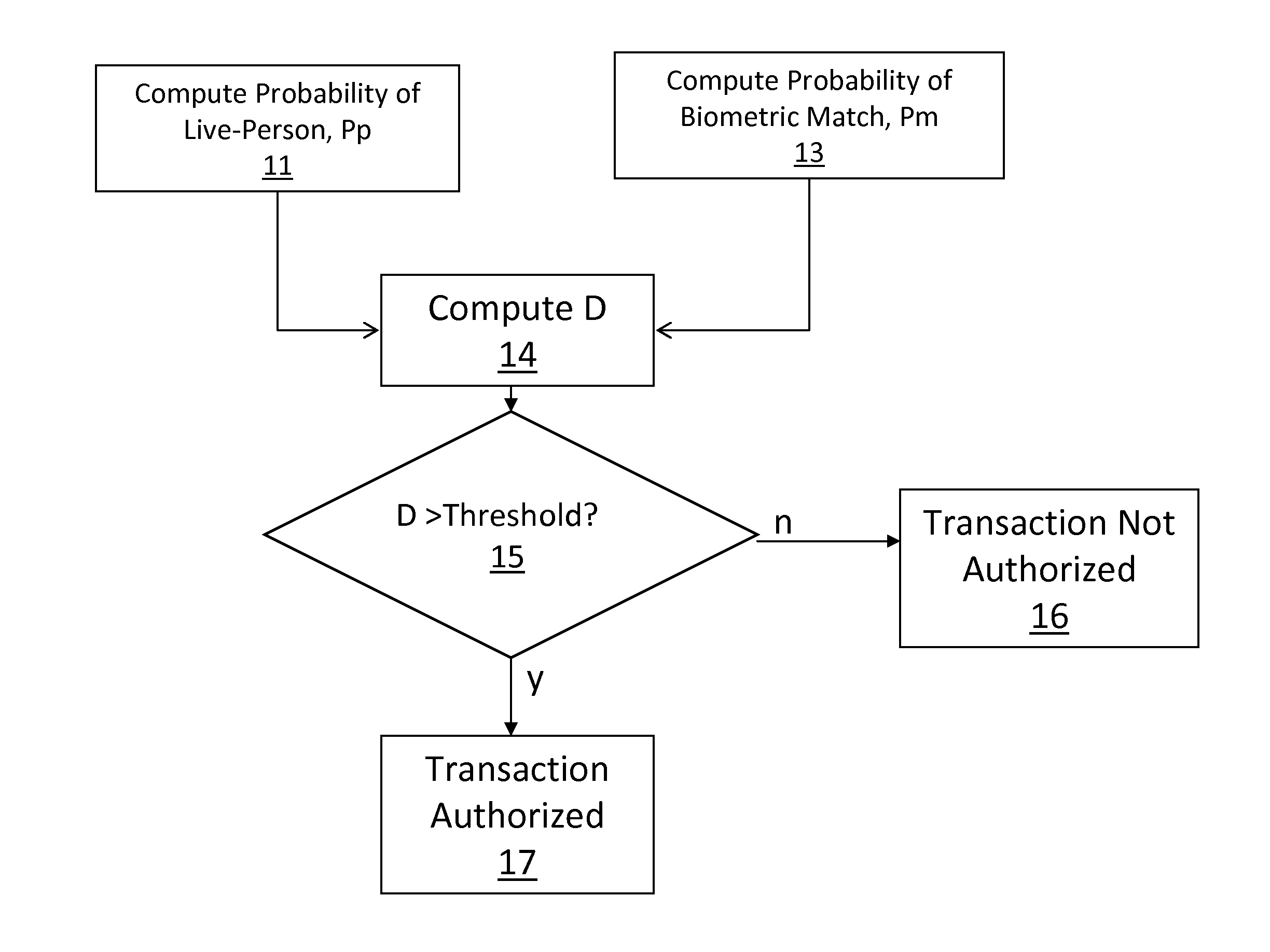
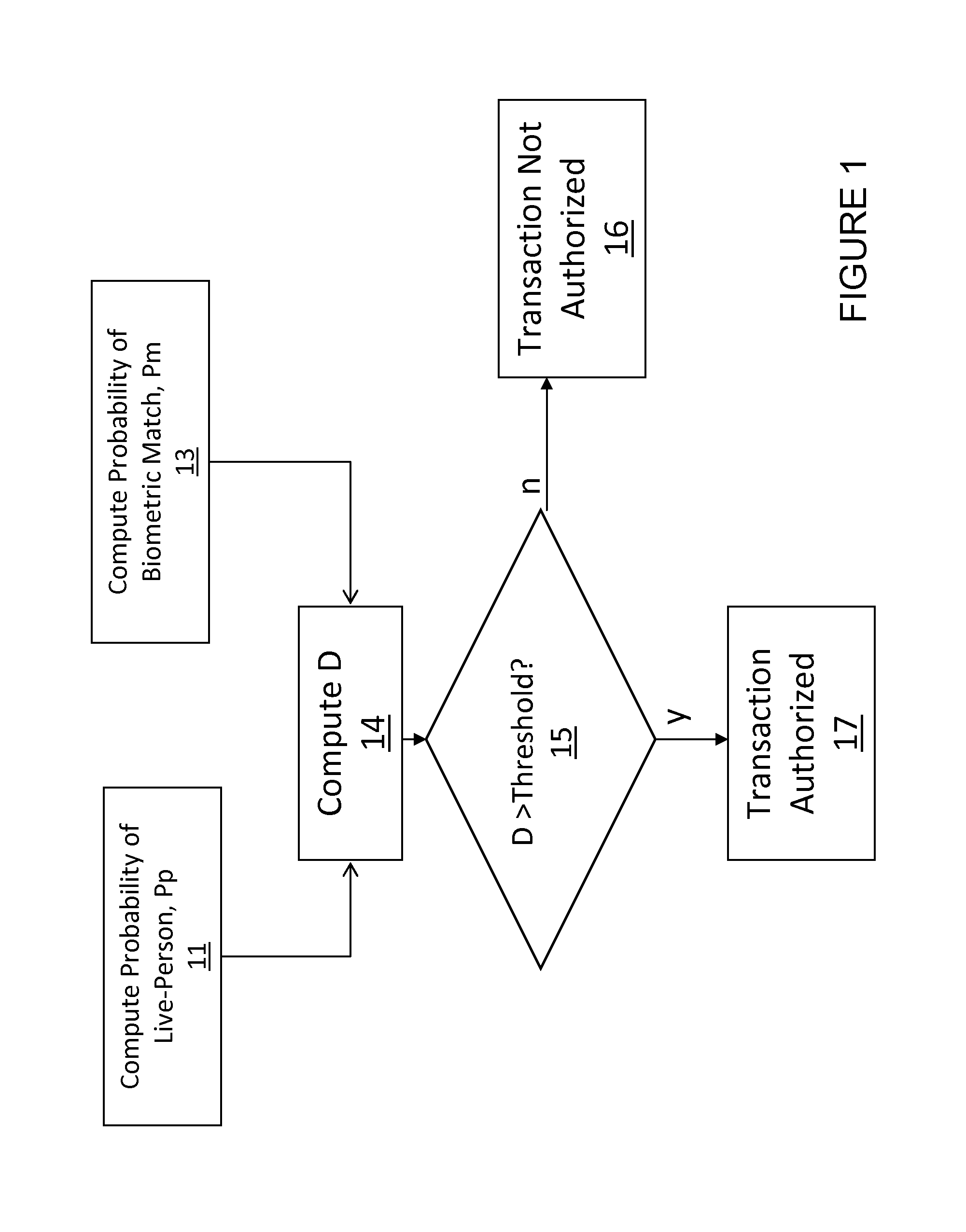
A method and system for authenticating financial transactions is disclosed wherein biometric data is acquired from a person and the probability of liveness of the person and probability of a match between the person or token and known biometric or token information are calculated, preferably according to a formula D=P(p)*(K+P(m)), wherein K is a number between 0.1 and 100, and authenticating if the value of D exceeds a predetermined value.
Owner:EYELOCK
Fraud resistant biometric financial transaction system and method
ActiveUS8280120B2Out of controlReduce scrap rateElectric signal transmission systemsImage analysisLivenessBiometric data
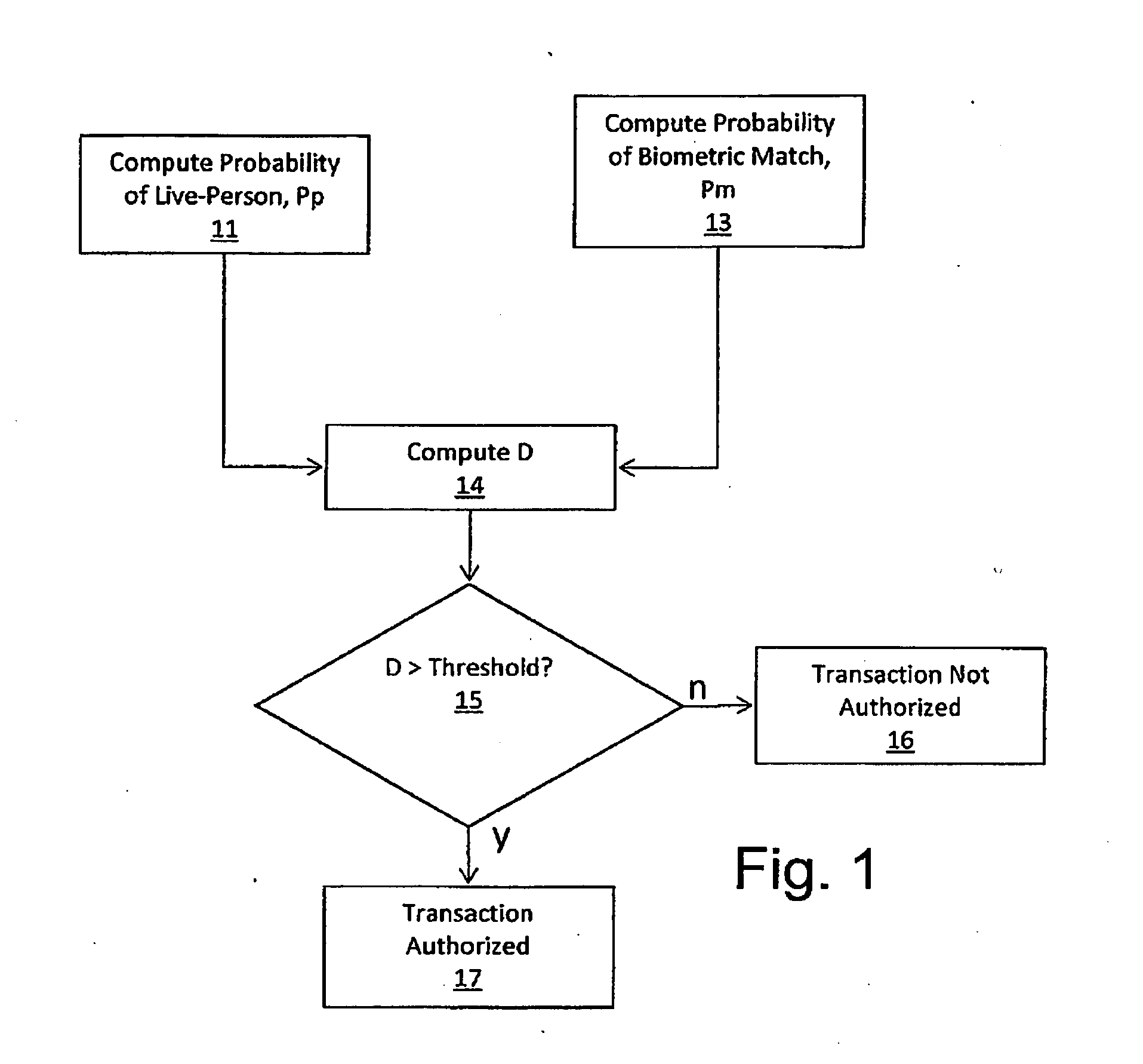
A method and system for authenticating financial transactions is disclosed wherein biometric data is acquired from a person and the probability of liveness of the person and probability of a match between the person or token and known biometric or token information are calculated, preferably according to a formula D=P(p)*(K+P(m)), wherein K is a number between 0.1 and 100, and authenticating if the value of D exceeds a predetermined value.
Owner:EYELOCK
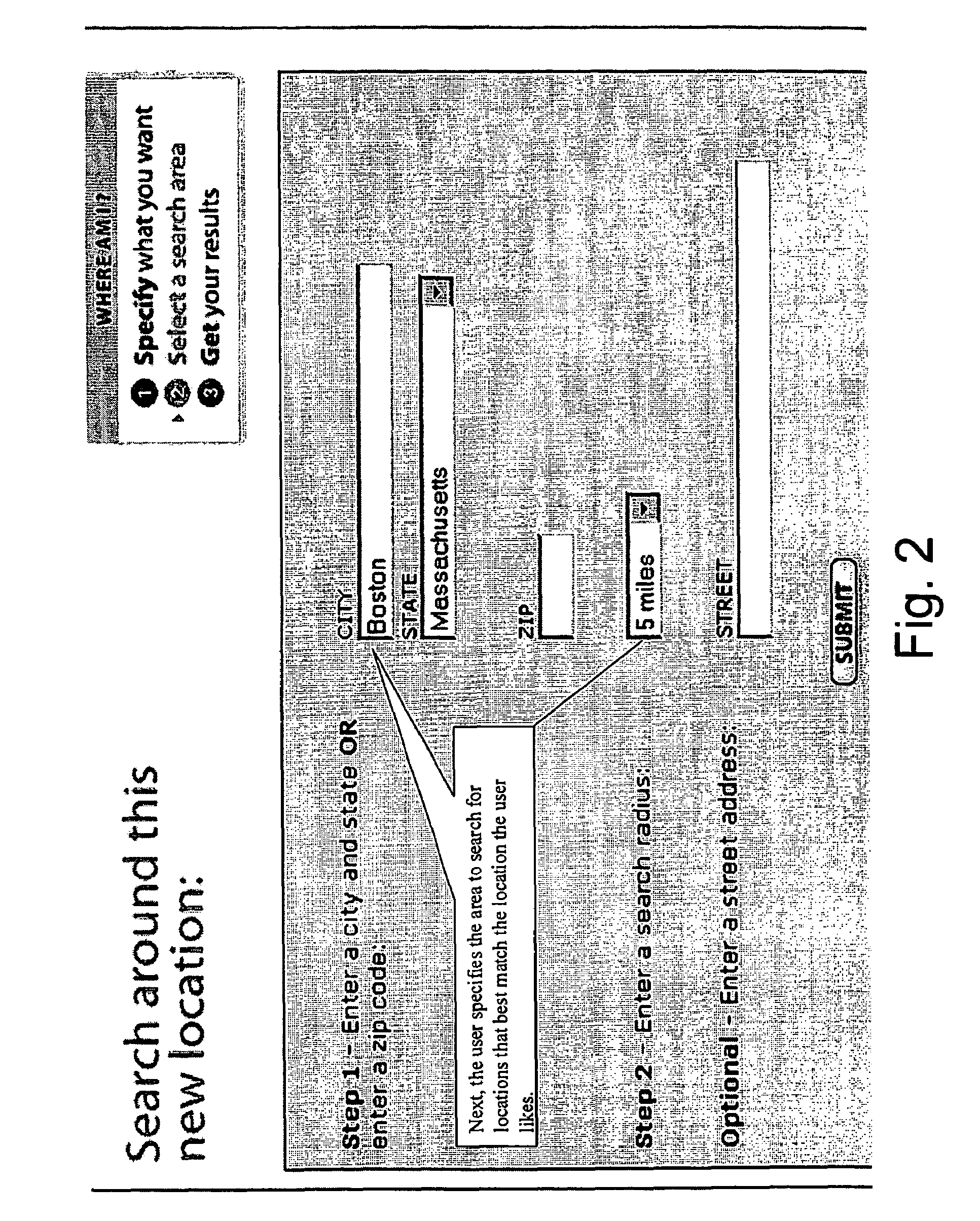
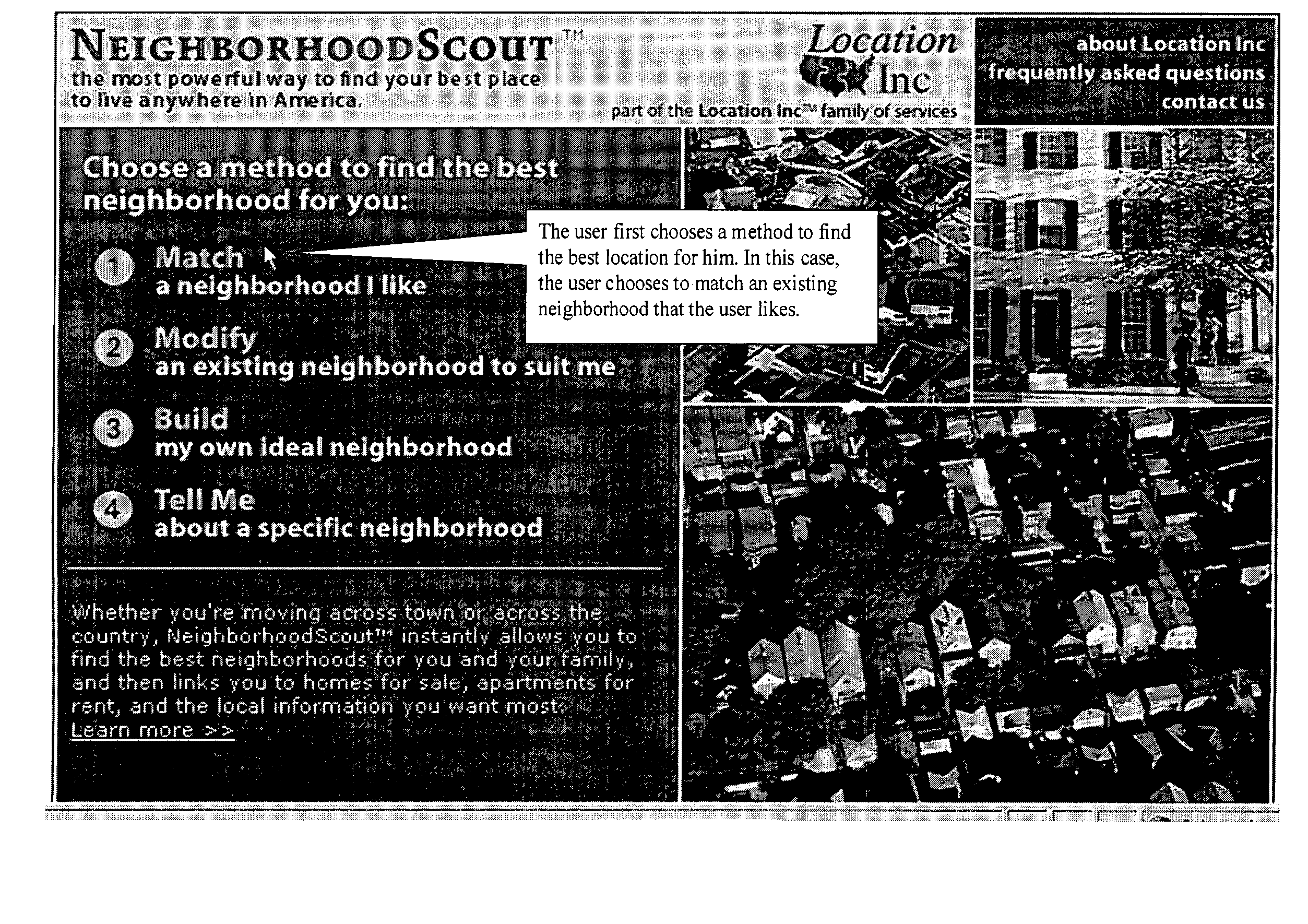
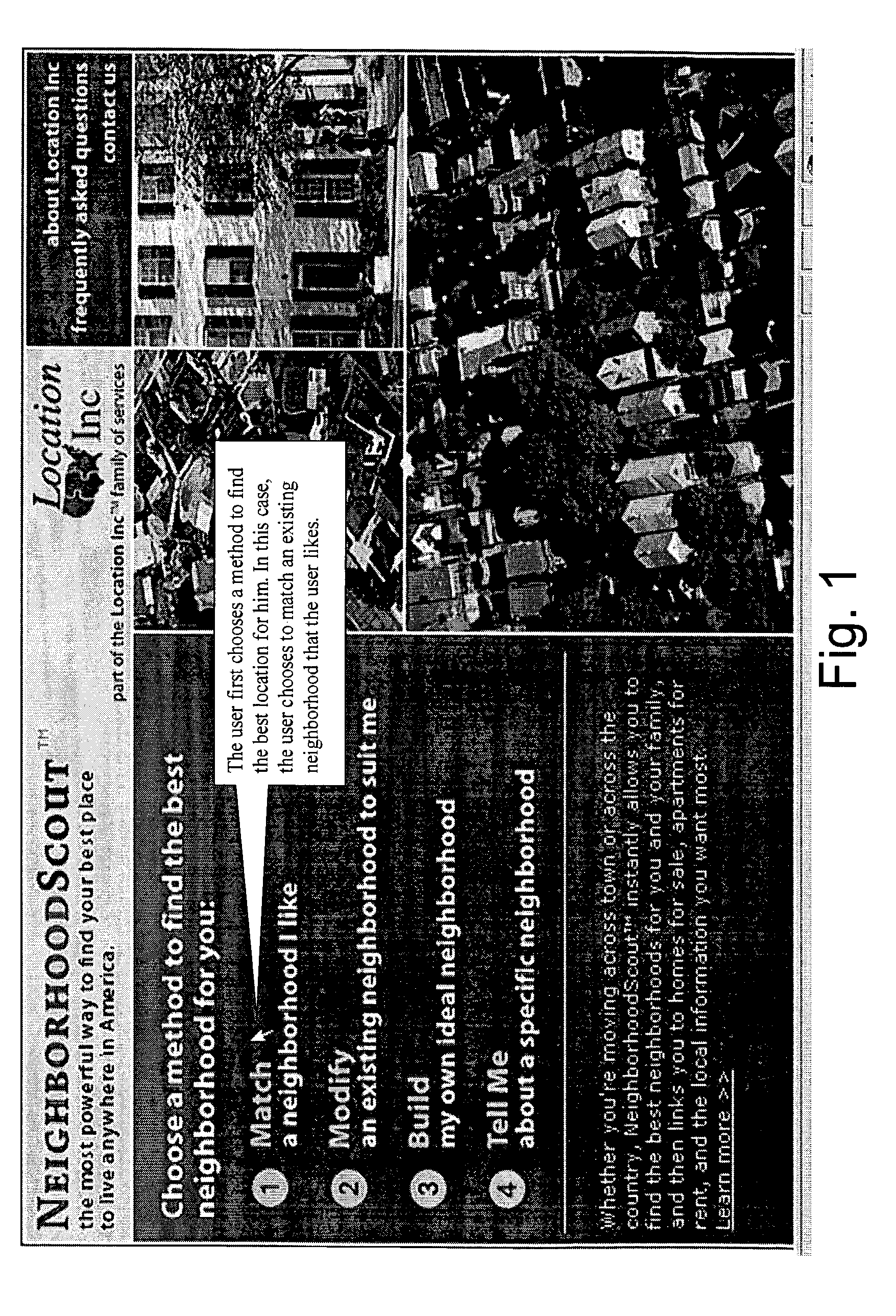
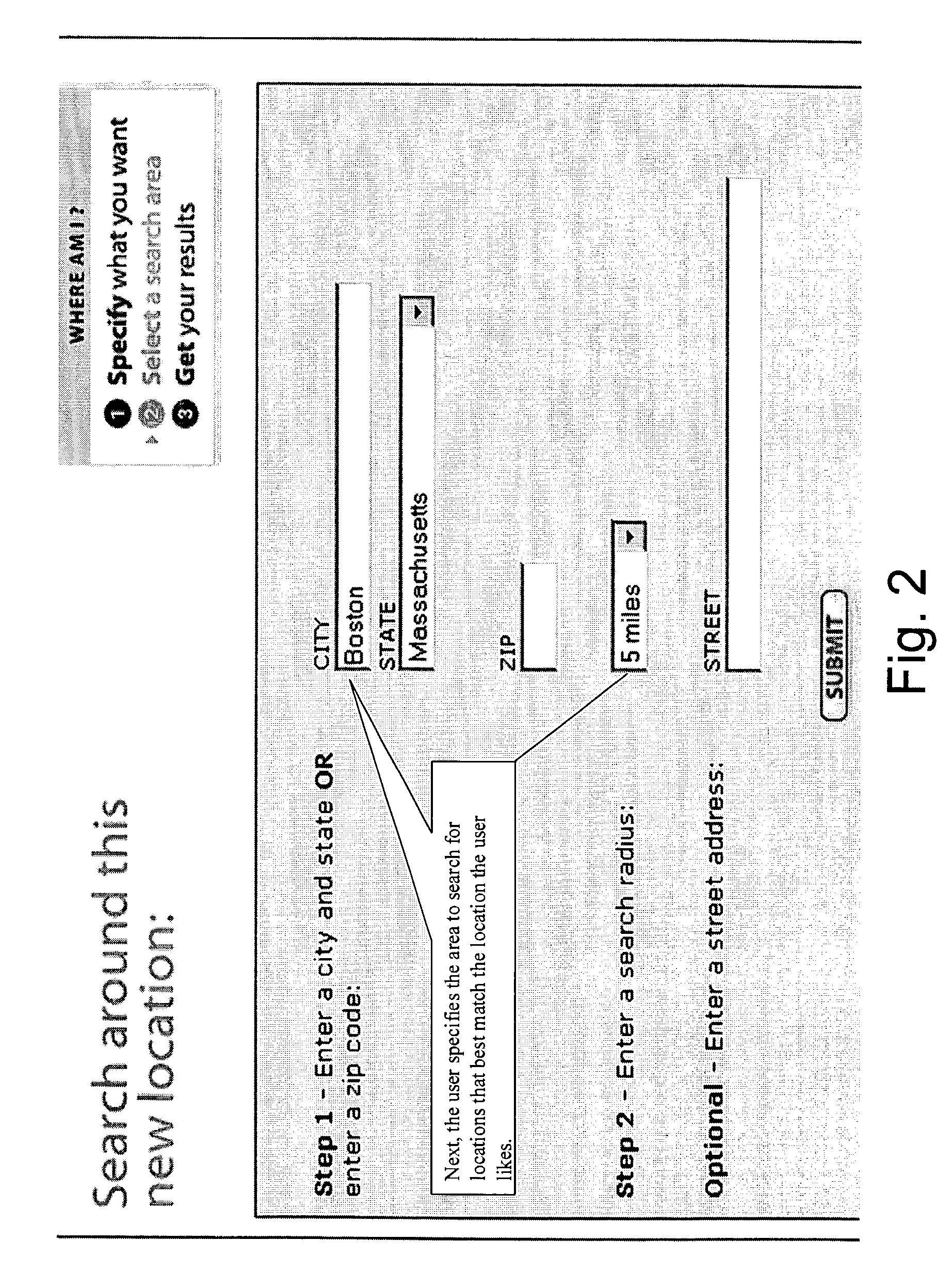
Method for analyzing demographic data
InactiveUS20080016051A1Easy to identifyReduce crimeWeb data indexingGeographical information databasesDemographic dataComputer science
A computer implemented method of generating an ordered list of geographical locations having similarities in preselected categories relative to a first geographical location.
Owner:LOCATION GROUP
Fraud resistant biometric financial transaction system and method
ActiveUS20120321141A1Out of controlReduce scrap rateDetecting live finger characterSpoof detectionLivenessBiometric data
A method and system for authenticating financial transactions is disclosed wherein biometric data is acquired from a person and the probability of liveness of the person and probability of a match between the person or token and known biometric or token information are calculated, preferably according to a formula D=P(p)*(K+P(m)) , wherein K is a number between 0.1 and 100, and authenticating if the value of D exceeds a predetermined value.
Owner:EYELOCK
Infection control monitoring system
ActiveUS20150077258A1Encourage participationImplementation is particularly straightforwardDiscounts/incentivesAlarmsControl measureMultiple infections
The invention provides an automated hand hygiene / infection control monitoring sensor-based system suitable for improving hand hygiene and multiple infection control measures and ensuring compliance by health care workers as well as visitors to hospitals and clinics. The use of biometric identification devices such as cameras for face recognition and profiling, microphones for voice recognition, etc. permit highly accurate identification without the use of removable identification devices such as identification badges which may include bar codes, magnetic strips or wireless devices such as RFIDS. Identification badges are removable and hence susceptible to being lost, misplaced, etc. Visitors are typically not assigned identification badges and hence enforcement of hand hygiene policies is minimal. Additional applications include reducing food contamination in food industry, the spread of diseases in schools, in businesses, in corporations and governmental facilities and public access facilities such as public restrooms, dining areas and transportation.
Owner:MINNESOTA IMAGING & ENG
Self-service insurance method and insurance self-service teller suitable for same method
InactiveCN106127587AEasy to useImplement queryFinanceApparatus for meter-controlled dispensingDisplay deviceCard reader
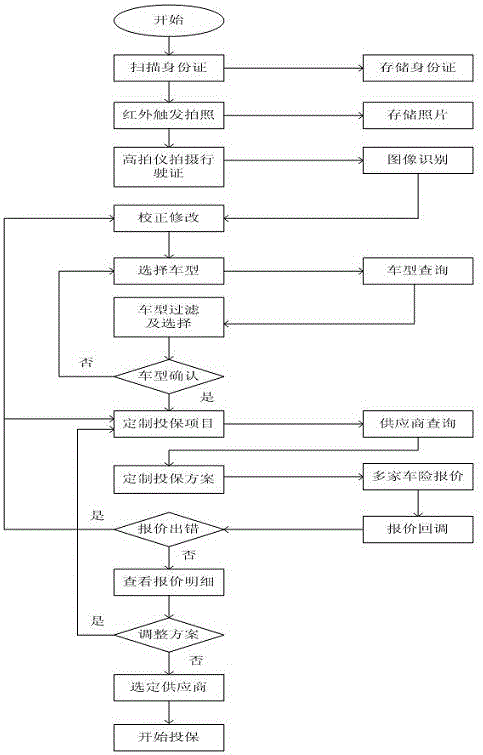
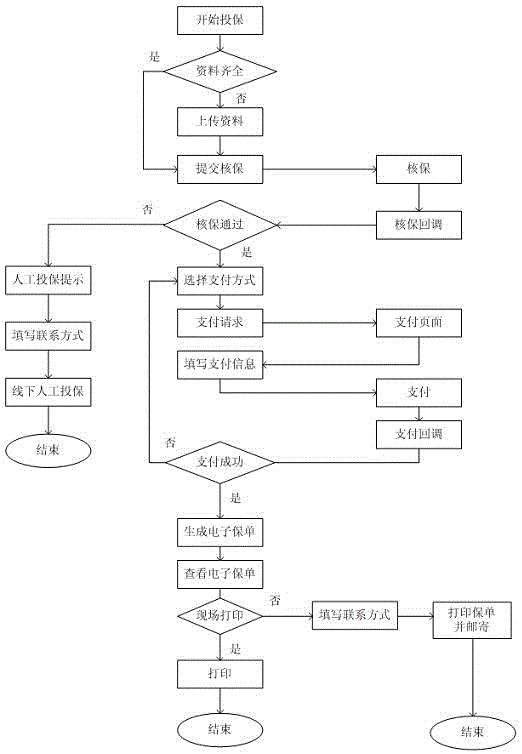
The invention relates to a self-service insurance method and an insurance self-service teller suitable for the same method. The method is characterized in that the self-service teller sends an insurance scheme customized by a user to an insurance service network, insurance management systems of multiple insurance mechanisms accessed to the network make offers, and after the user selects an insurance mechanism, the user pays insurance premium through the self-service teller or other modes to obtain an insurance policy. The self-service teller mainly comprises a card reader, a touch screen, buttons / a keyboard, a display, a printer and a host. The invention enables the user to achieve insurance, renewal of insurance, payment, insurance policy printing, querying and the like on the self-service teller, so that the user is greatly facilitated, the cost of the insurance industry is reduced, and the efficiency is improved.
Owner:焦文华
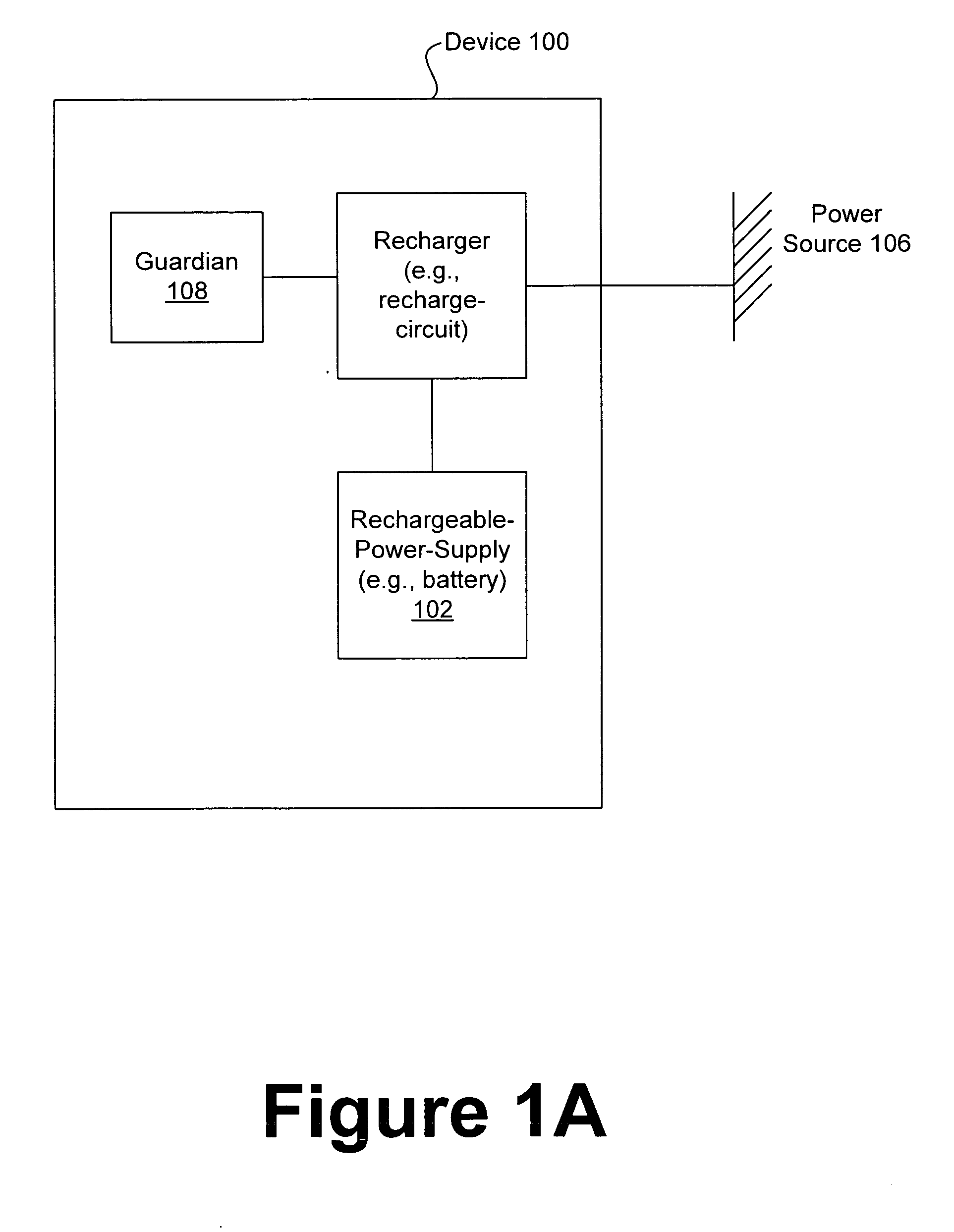
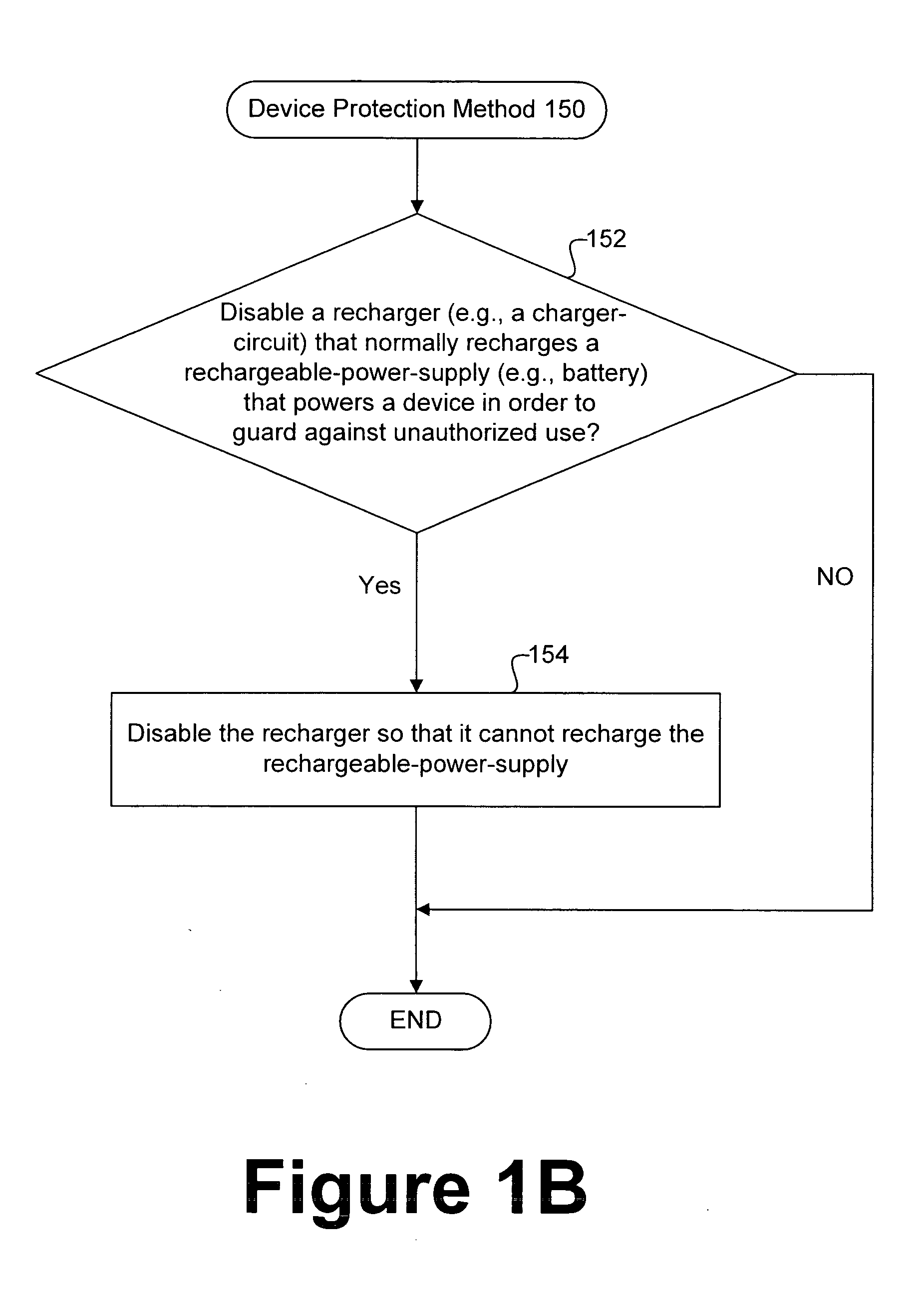
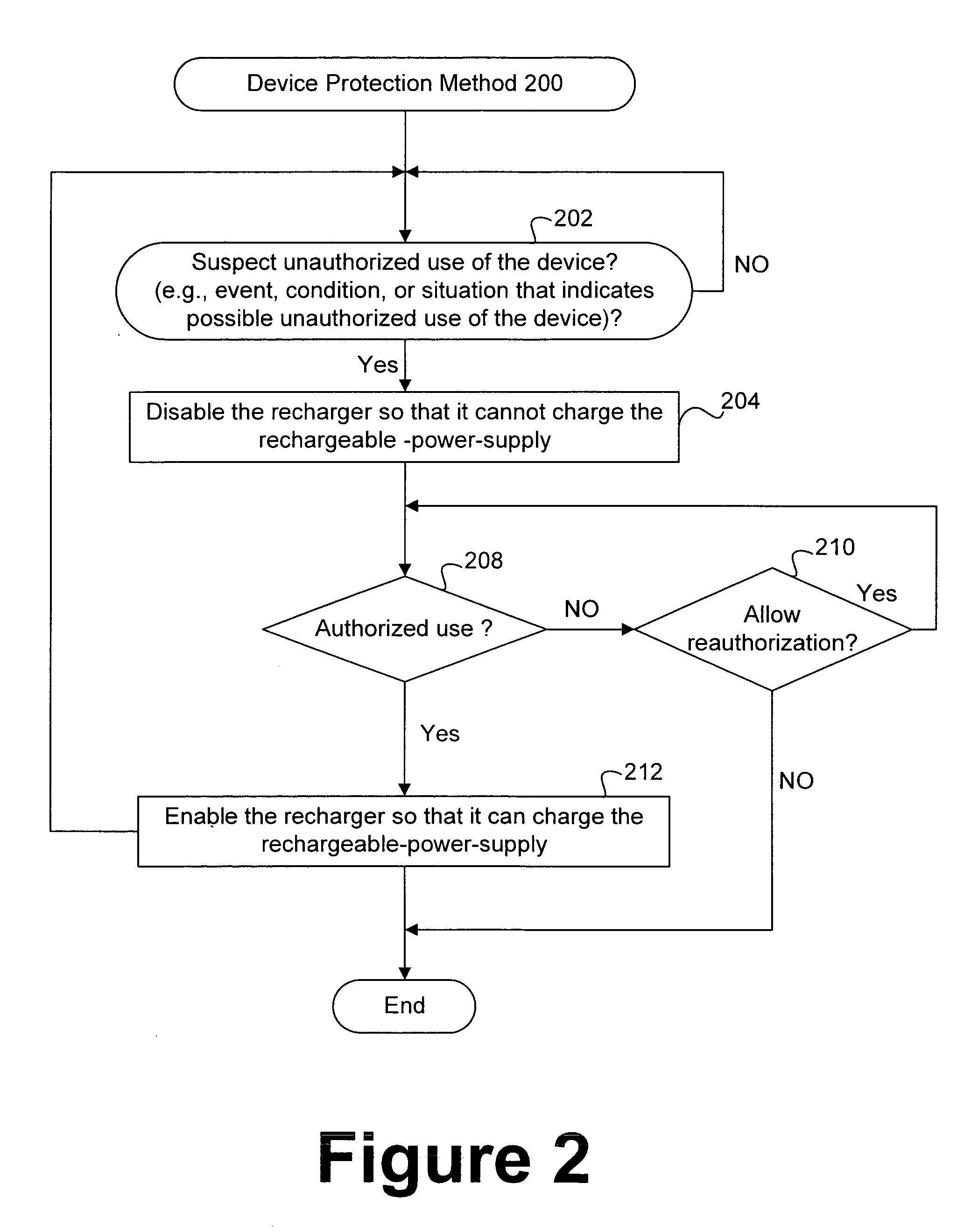
Protecting electronic devices from extended unauthorized use
ActiveUS20070138999A1Hindering normal use and enjoymentReduce crimeCircuit authenticationUnauthorised/fraudulent call preventionMusic playerEngineering
Owner:APPLE INC
Safe system and method for bank transaction system
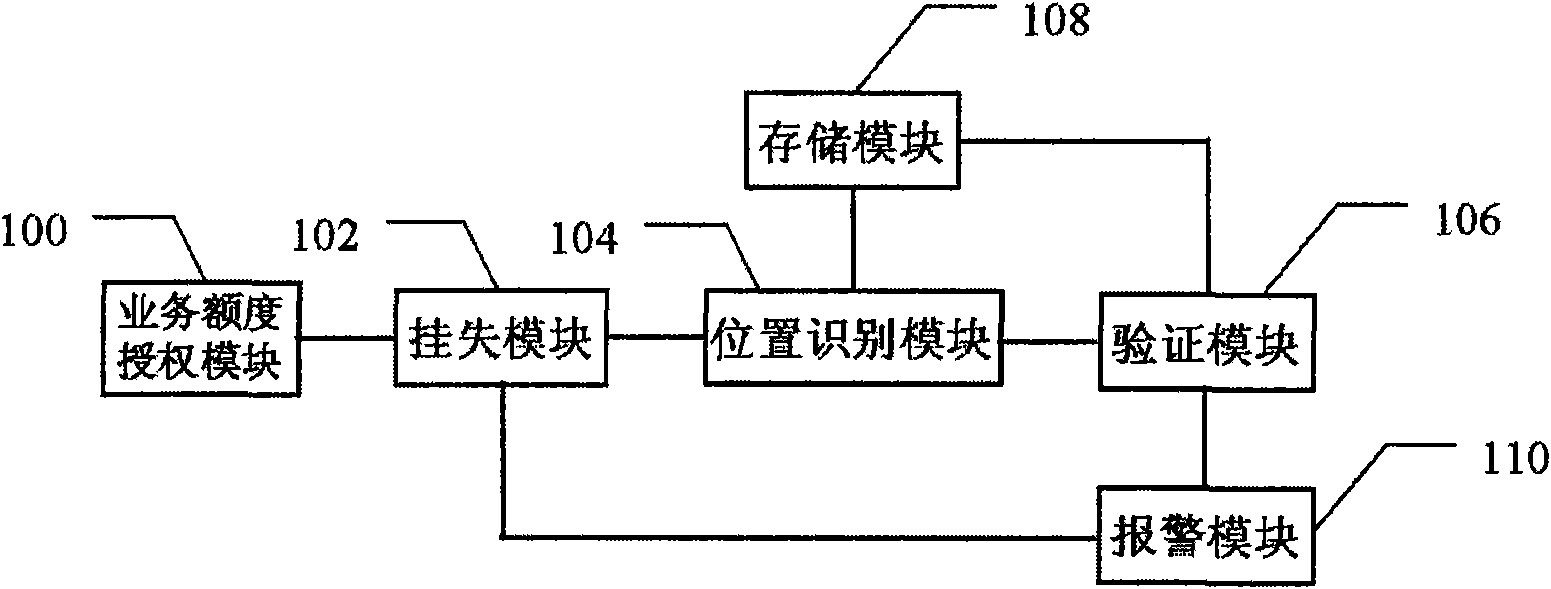
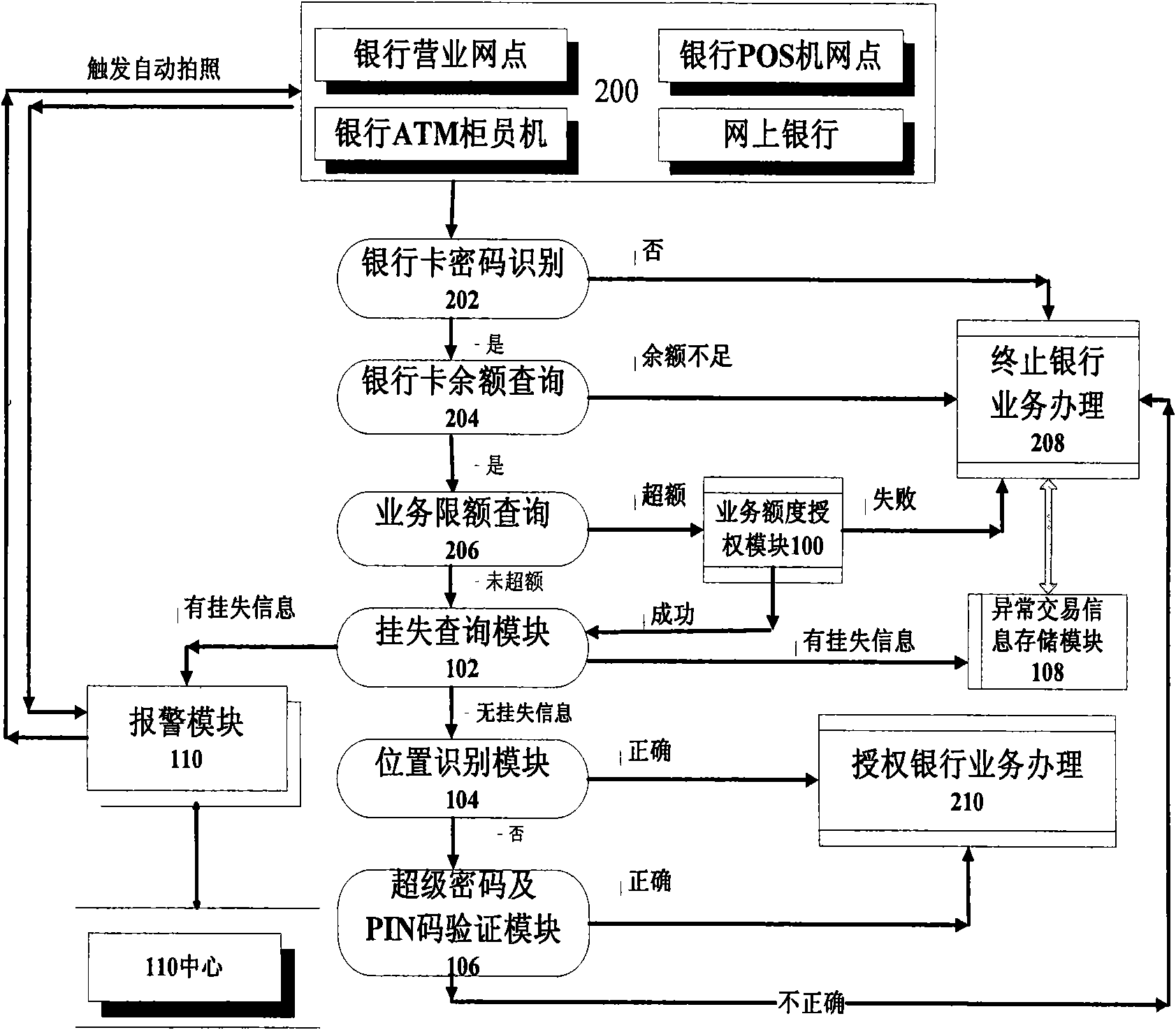
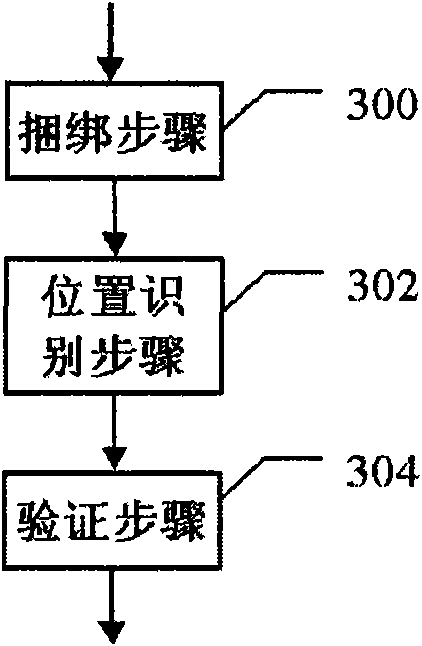
InactiveCN101588577AImprove securityStrong real-timeFinanceAssess restrictionBank accountMobile phone
The invention discloses a safe system and a method for a bank transaction system. The safe system comprises a position identification module which responses a bank service request and launches a position inquiring request to a position server of a mobile communication operator so as to determine whether a position of a mobile phone card bound with a bank account and a position sending the service request are identical; if the two positions are identical, the service is authorized to be executed; and if the two positions are not identical, the service is rejected. The transaction system adopting the technical scheme has high security, strong real-time performance and favorable applicability and can control all bank users and service counters in real time, thereby further improving the security of a bank payment system, reducing the operation risk of the bank users and being beneficial to the healthy development of commercial bank systems.
Owner:罗邵波 +1
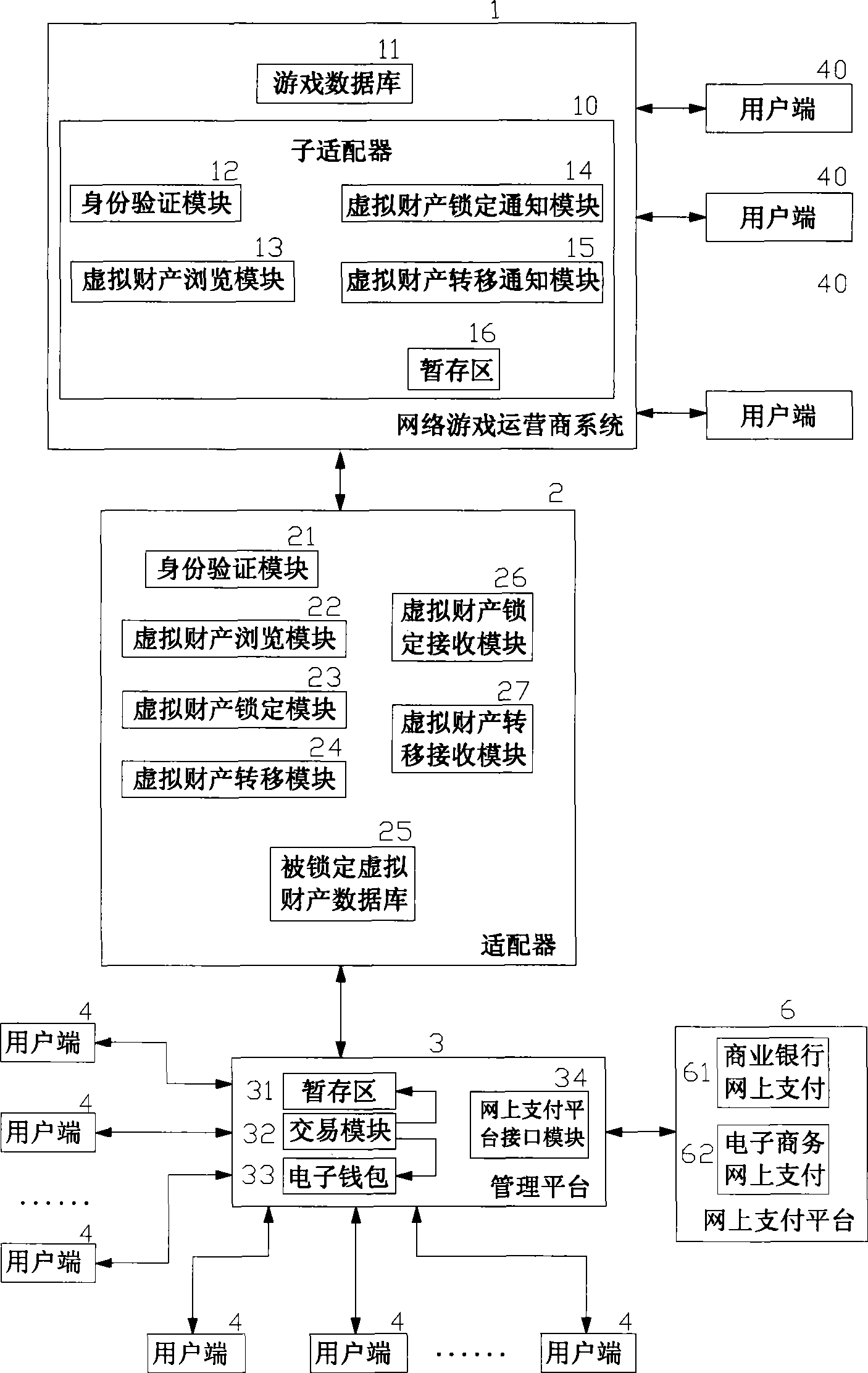
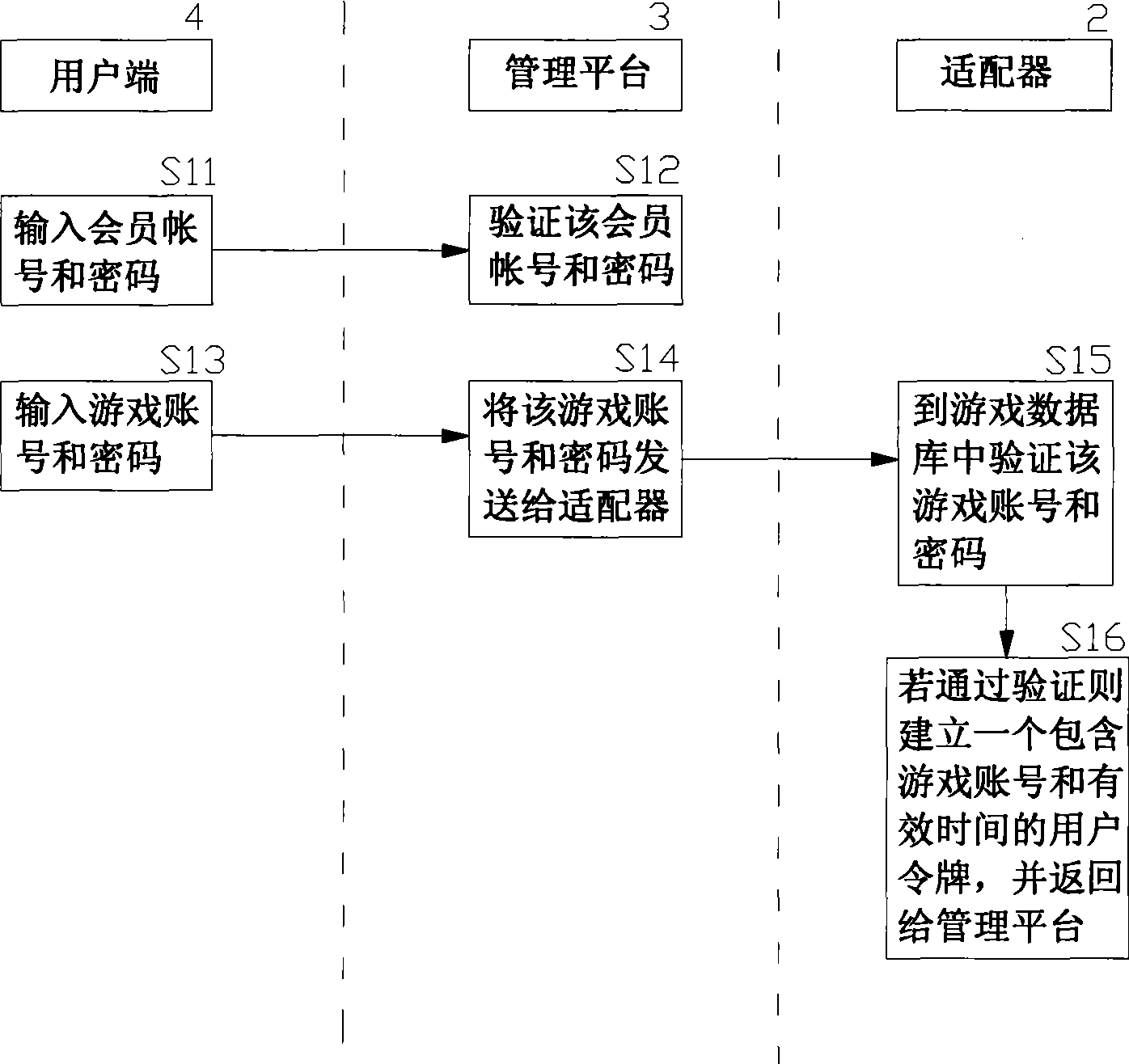
On-line payment method and system for network game virtual property trade
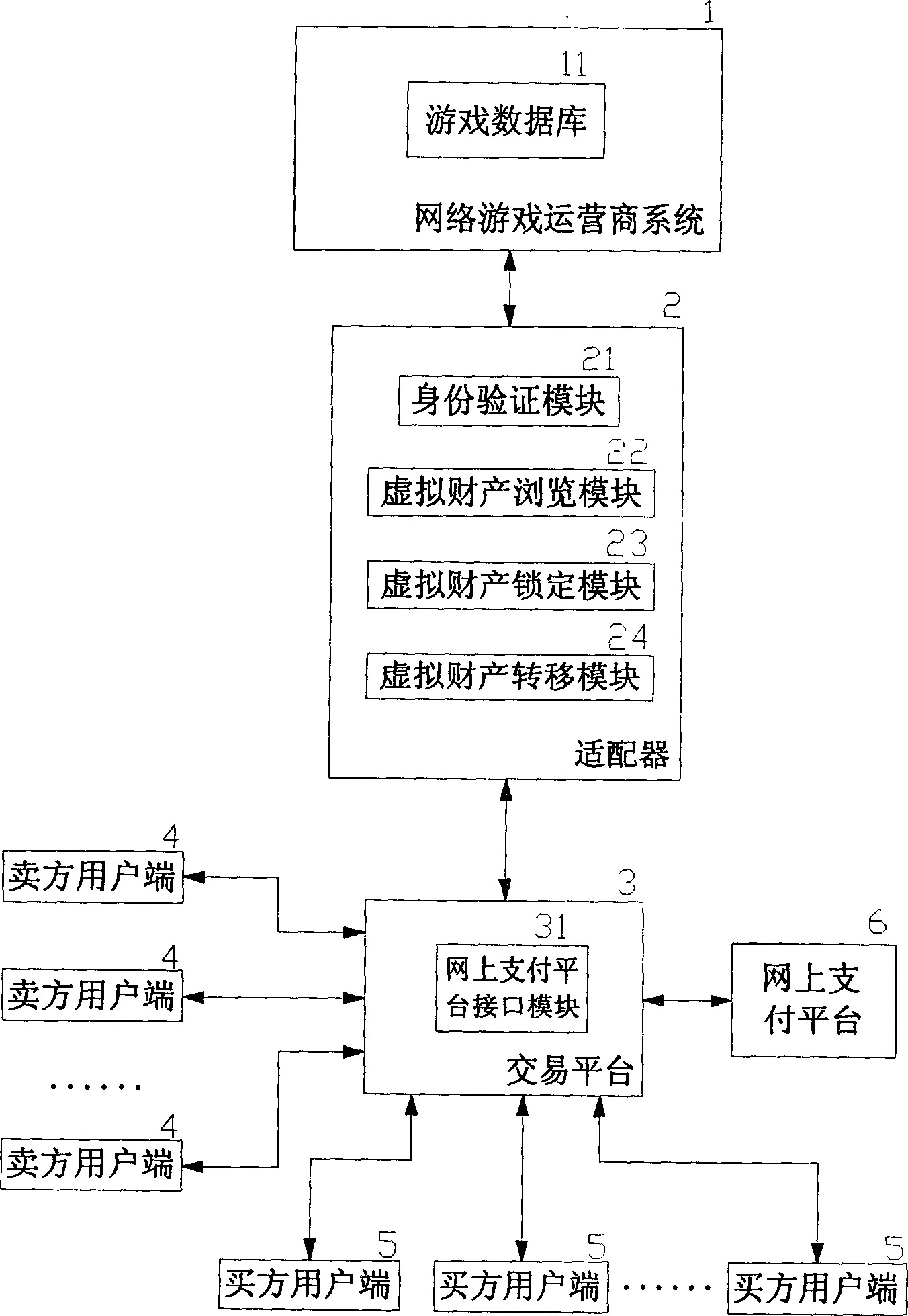
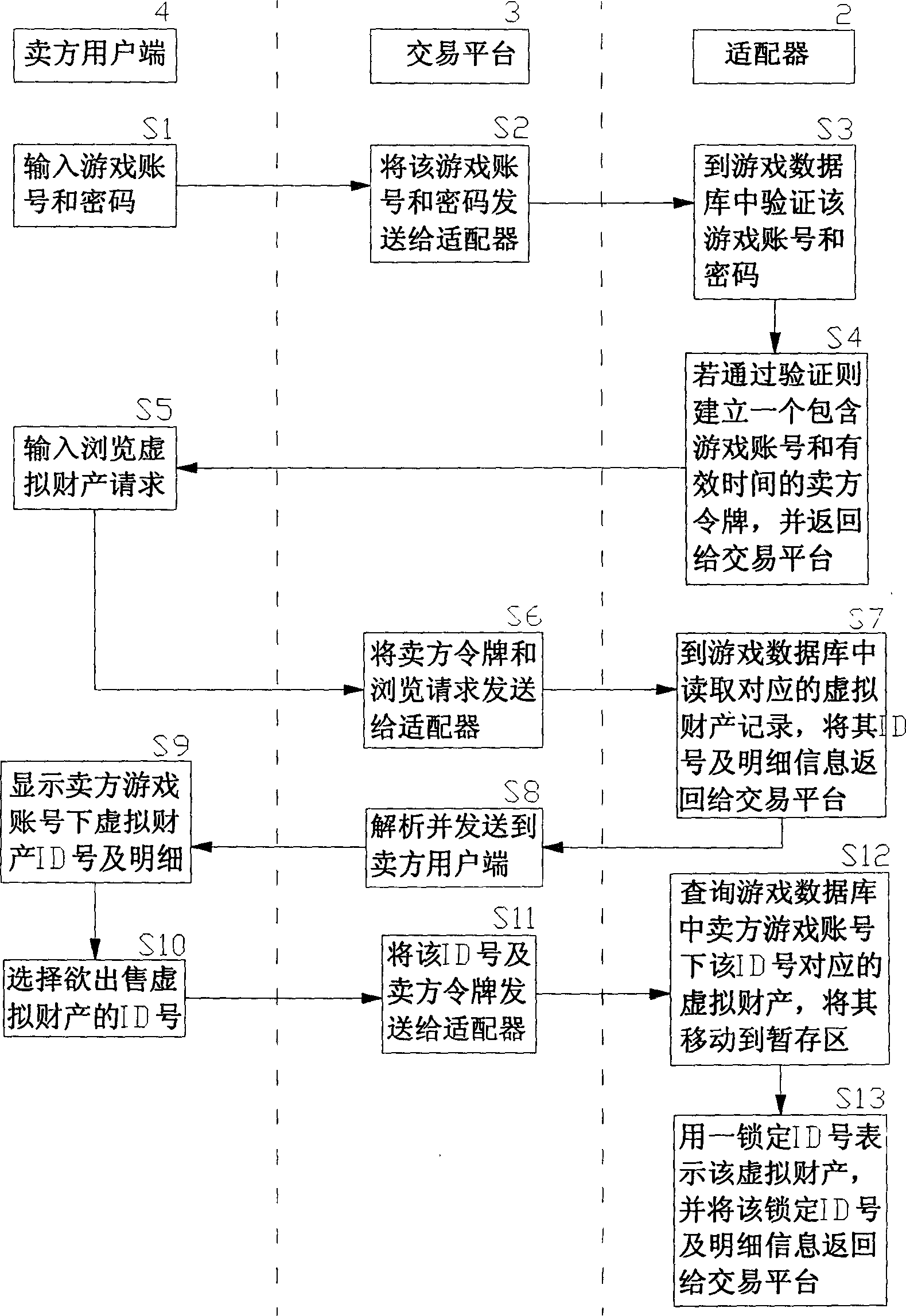
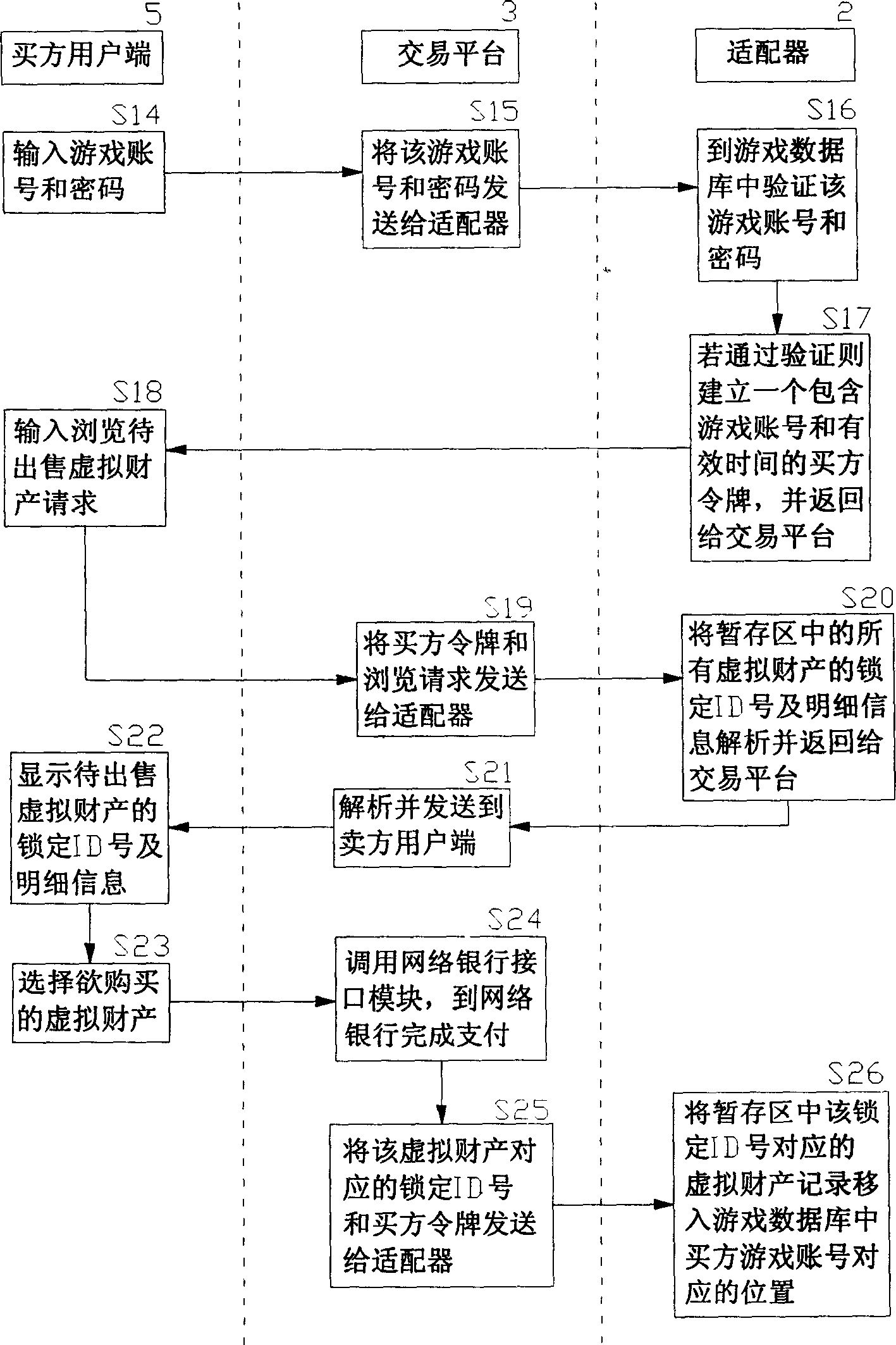
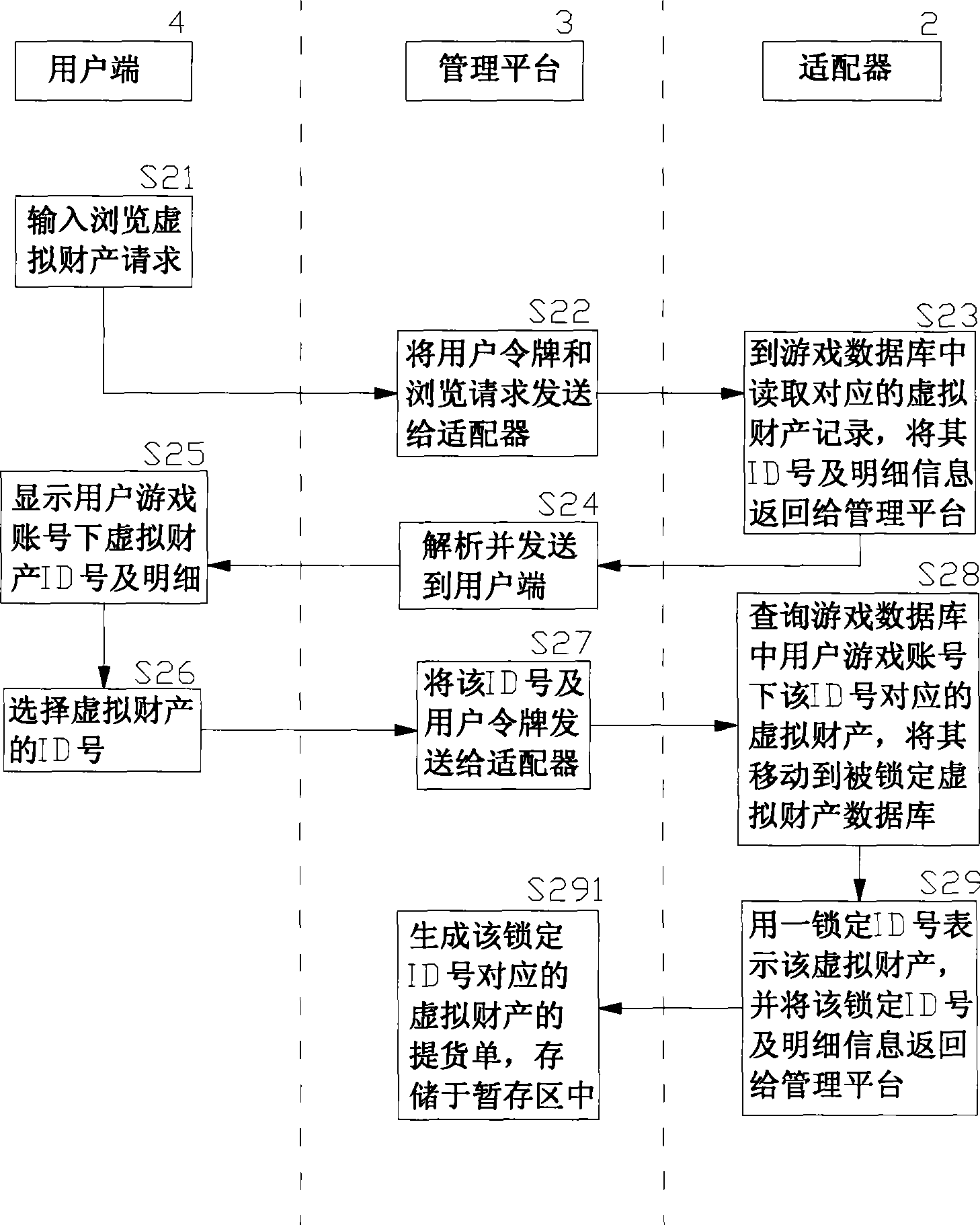
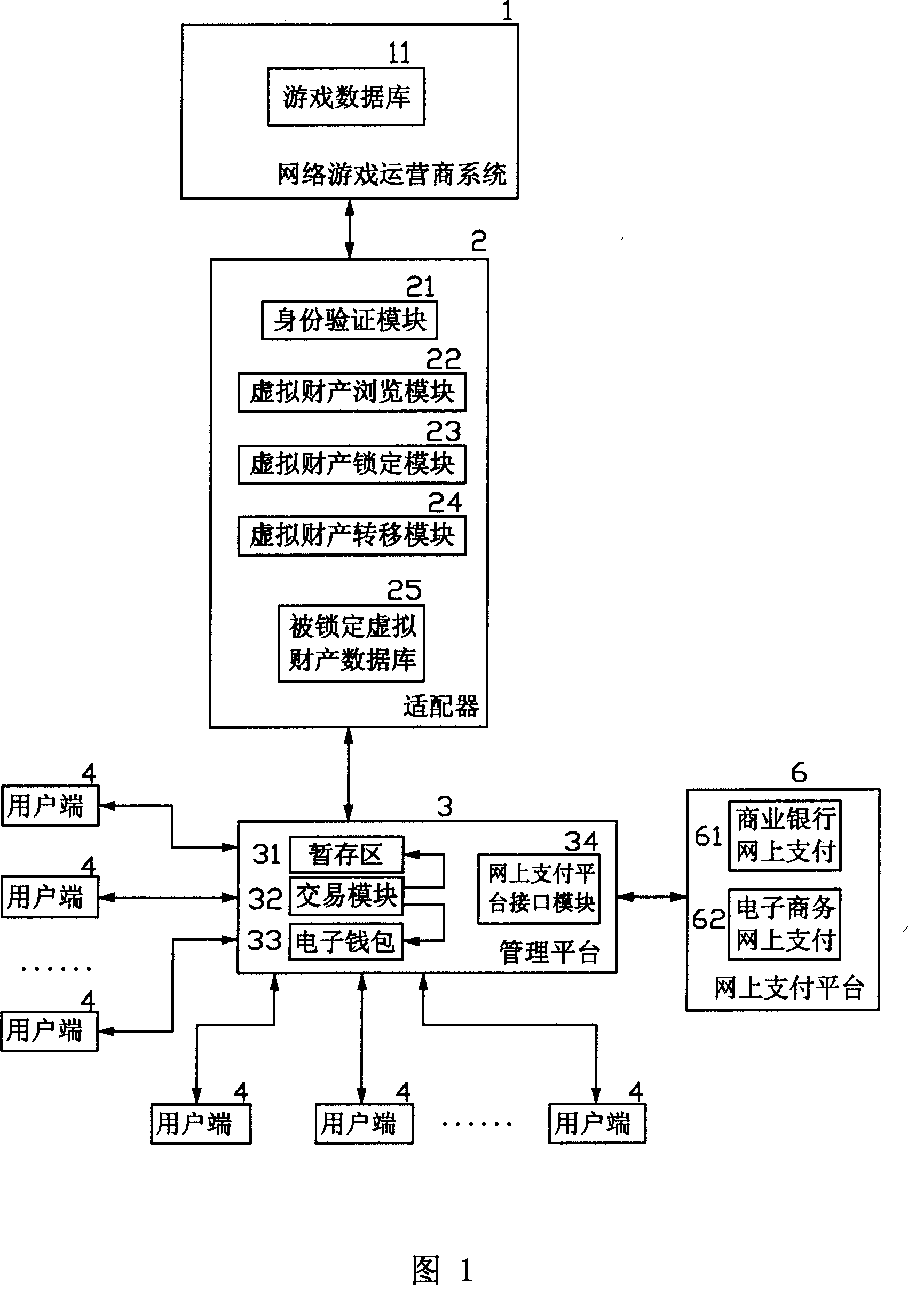
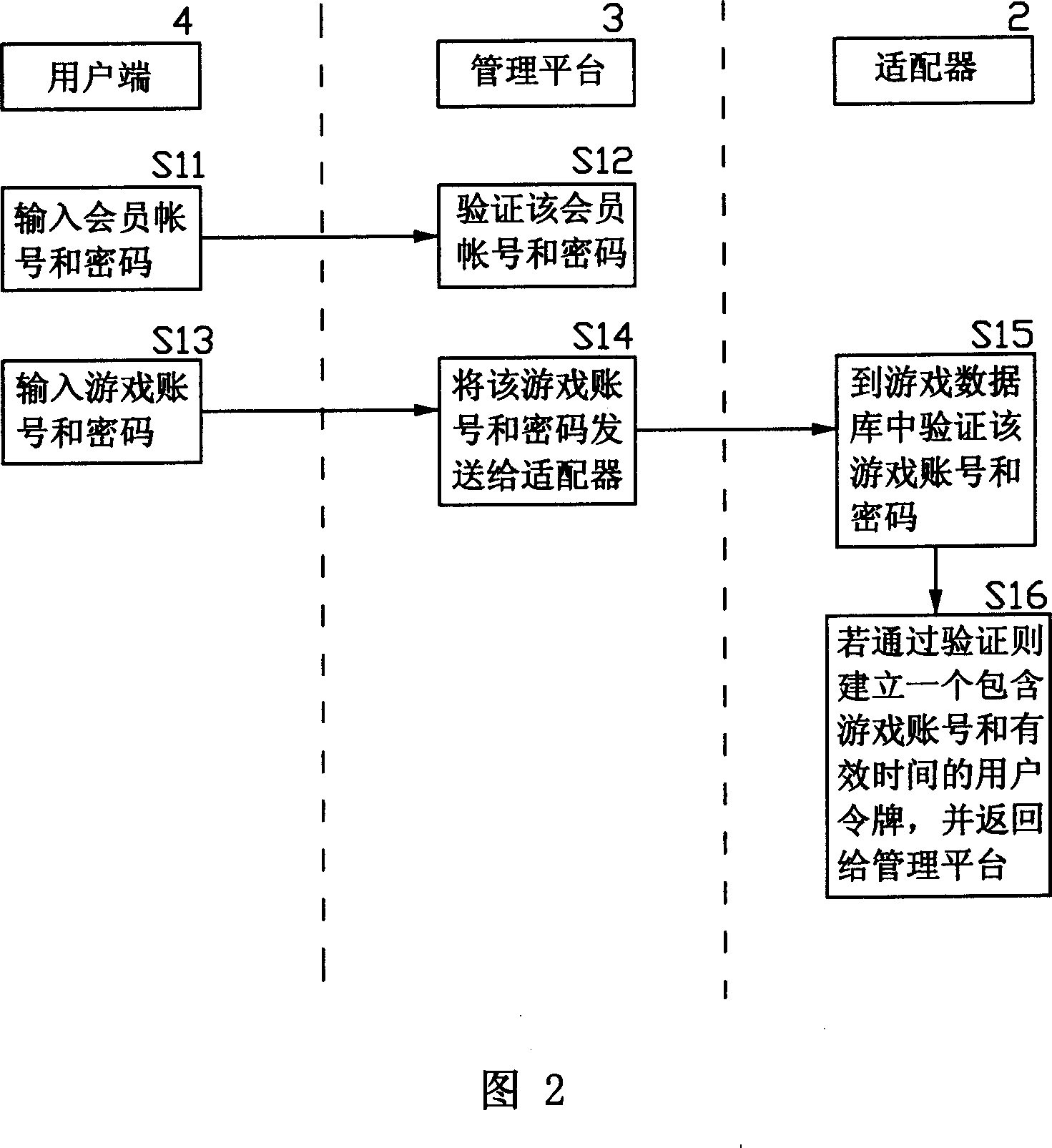
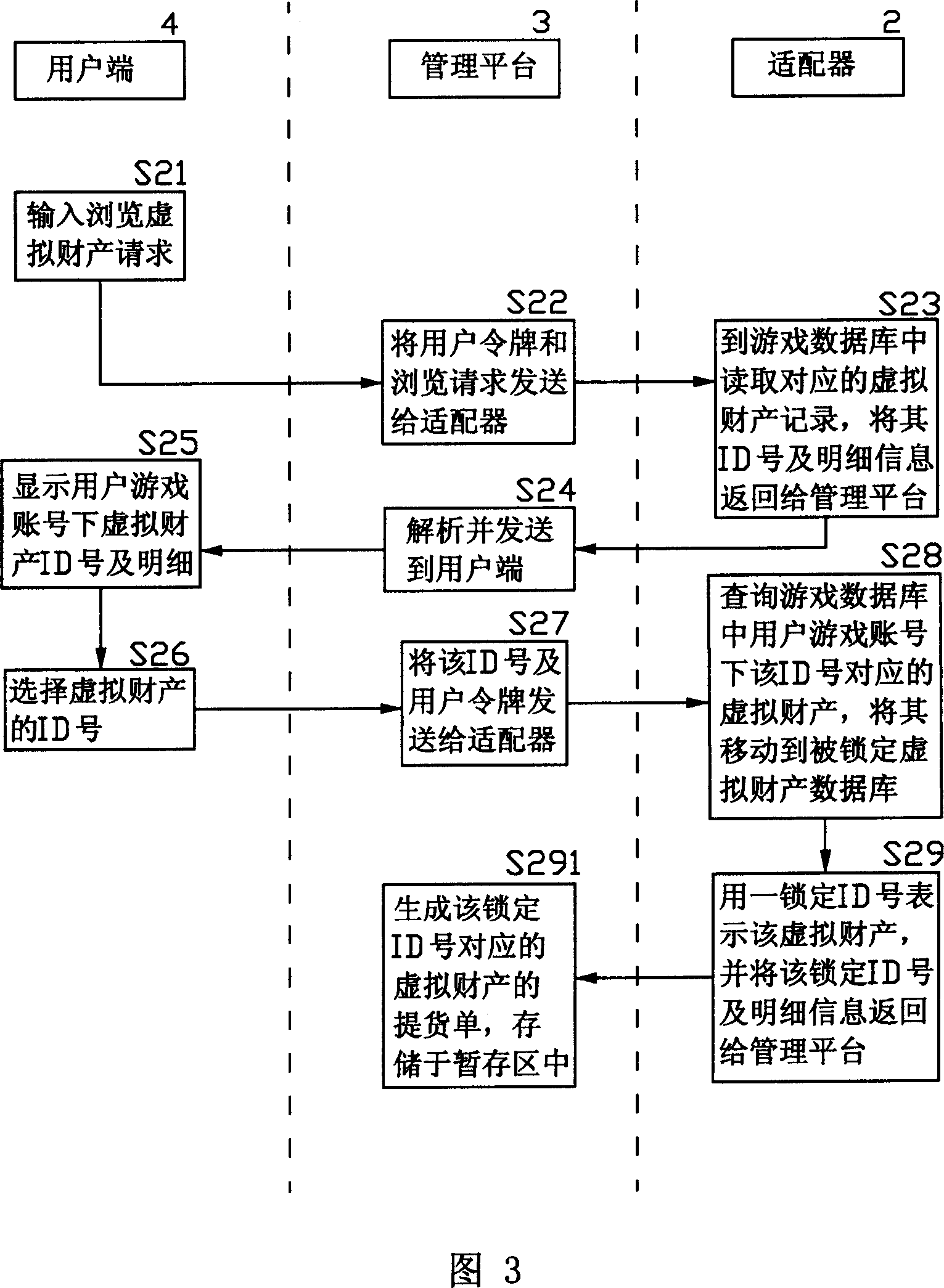
InactiveCN1818958AReduce crimeRealize complete online transactionPayment architectureCommerceVirtual propertyPayment
An online deliver method and system of the online-game dummy property exchange, the main principium is: establishing the exchange platform that has the function of online delivery and the user end that support multi-business end, setting a adapter between the exchange platform and the online-game organizer, exchange the data in the game database between the exchange platform and the online-game organizing system, to achieve the corresponding relation of the dummy property and the game account that form in the online-game and change by the operation of the business end, that can realize deliver really and safely of the online-game dummy property.
Owner:GOODHOPE CORP
Method for analyzing demographic data
InactiveUS7680859B2EasilyReduce crimeWeb data indexingDigital data processing detailsDemographic dataGeolocation
Owner:LOCATION GROUP
Method for analyzing demographic data
ActiveUS7043501B2Easy to identifyReduce crimeGeographical information databasesMarketingDemographic dataGeolocation
A computer implemented method of generating an ordered list of geographical locations having similarities in preselected categories relative to a first geographical location.
Owner:LOCATION GROUP
RFID based proximity sensor and alert system for fugitives, sex offenders, missing soldiers and the like
InactiveUS20080218335A1Reduce crimeSave livesLogisticsElectric signalling detailsProximity sensorEmergency rescue
A robust, wireless sensor system providing a low cost method of tracking people such as sex offenders, child molesters, etc., after their release from prison or other confinement, which protects society from such individuals and lessens their ability to repeat such offenses. The system and method of the invention can also be used to locate kidnapped persons, people buried in snow avalanches, missing or dead soldiers, etc. The system utilizes RFID tags placed on people or in specified locations and RFID transmitters that can resonate with the tagged people or objects. Such a trigger recognition arrangement combined with communication of information from the triggering can be used to obtain a signal alerting the transmitter carrier that the tagged object or person is nearby. The triggering action can also initiate a sequence of information transfers in which the transmitter broadcasts to a central command that a particular transmitter is or was in proximity to a specific object or person, and allows the command center to order the dispatch of authorized personnel, such as policemen, military personnel, emergency rescue workers, etc. to the triggering location.
Owner:ATTAR AMIR J
Automatic passenger and driving safety alarm device based on intelligent voice recognition and method thereof
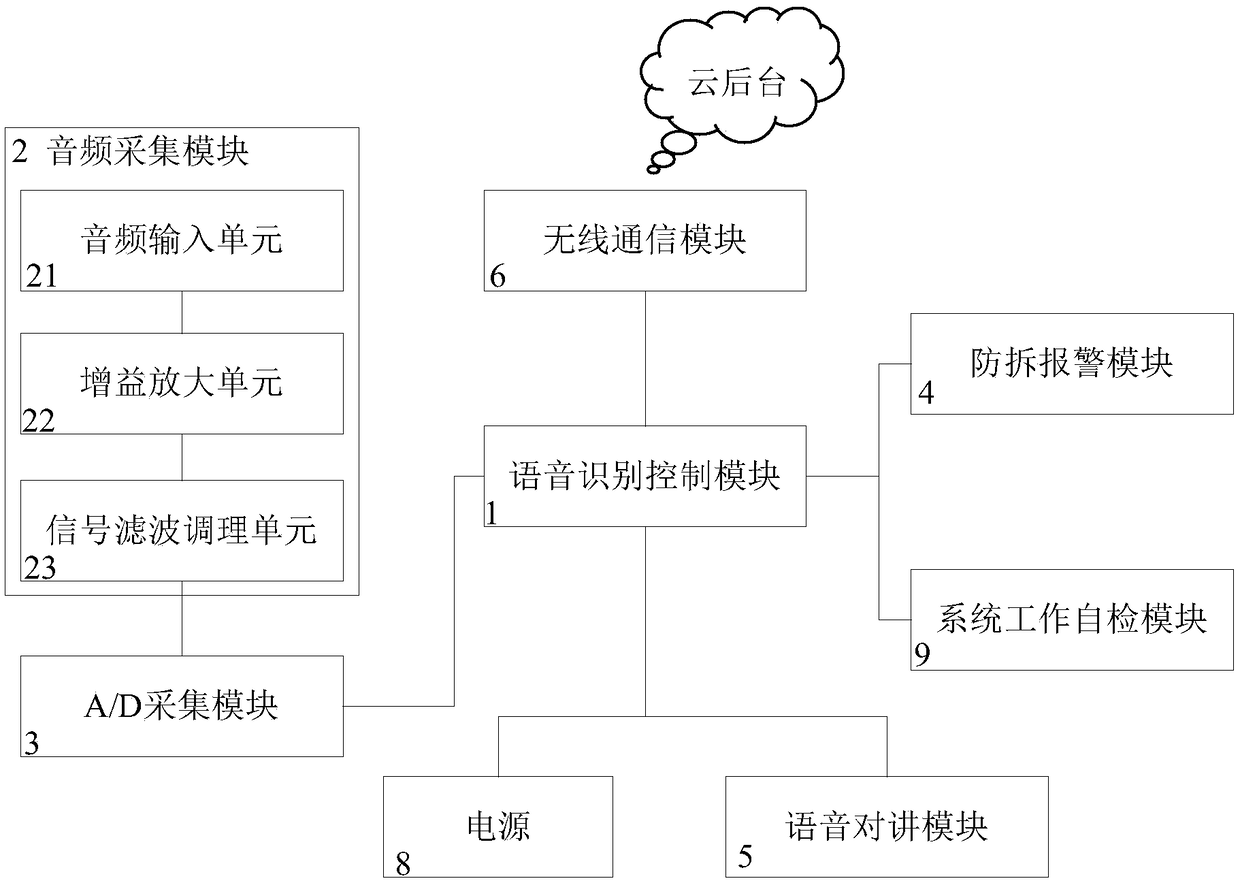
PendingCN108877146AReduce security regulatory black holesReduce crimeAlarmsSpeech recognitionVoice communicationEngineering
The invention discloses an automatic passenger and driving safety alarm device based on intelligent voice recognition. The voice data in a vehicle are collected in real time through a multi-path microphone pickup circuit, the device collects audio data in the vehicle in real time, and the audio is subjected to amplification filtering and voice extraction after preprocessing, and real-time communication is carried out with the cloud background through a wireless communication module. The invention further provides an automatic passenger and driving safety alarm method based on intelligent voicerecognition. The voice data are subjected to preprocessing and then are sent for feature extraction, the voice is transmitted to an acoustic model for comparison. If the voice falls into the alarm preset sensitive words, the alarm text information is output to the background, and the background is fed back to an online ride-hailing platform, so that the abnormal situation can be immediately processed. The safety supervision black hole of current online ride-hailing is reduced. The life and the safety of people in the vehicle can be guaranteed, voice communication can be directly carried out with a party involved, and illegal criminals of online ride-hailing can be effectively reduced.
Owner:深圳市尼欧科技有限公司
Network game virtual property on-line trading management method and system
InactiveCN101425164ARealize depositAchieve transferCommerceSpecial data processing applicationsVirtual propertyPayment
The invention relates to a method and a system for managing online transaction of virtual property of a network game, which has the main principle that a management platform which has the functions of online consignation, transfer, transaction, payment, and the like and can support a plurality of user ends is built; an adapter is arranged between the management platform and a network game operator system; and the data transaction can be carried out between the management platform and a data base of the network game operator system through a series of standardized definition made to the adapter, so that the online consignation, transfer, transaction and payment of the virtual property of the network game can be operated at the user ends.
Owner:好旺角(厦门)电子科技有限公司
Real-time identity recognition and authentication method for self-service equipment system of bank
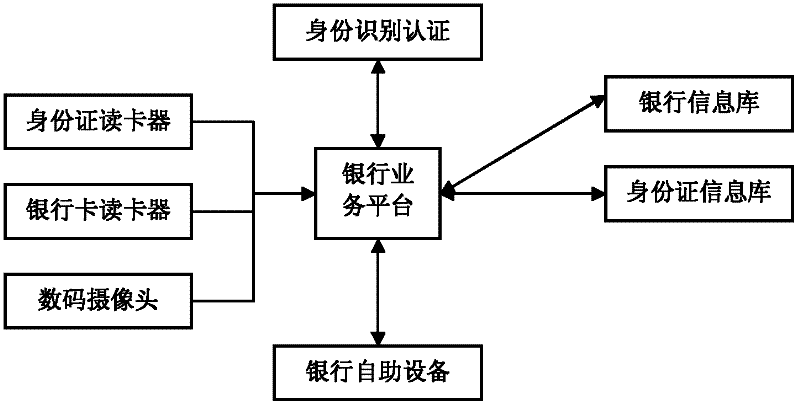
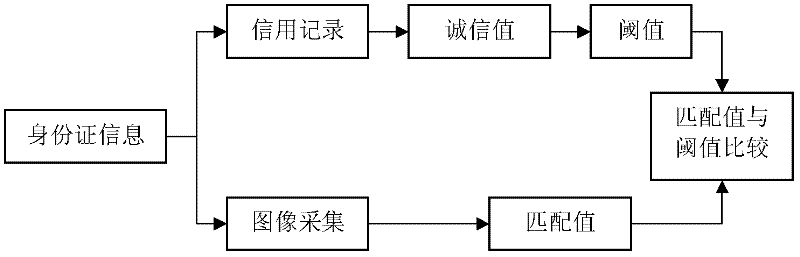
InactiveCN102364527ASolve the problem of inaccurate identification and authenticationStable identity authentication methodComplete banking machinesCharacter and pattern recognitionQuality of servicePattern recognition
The invention provides a real-time identity recognition and authentication method for a self-service equipment system of a bank. With face information and historical information, which can be simply and conveniently acquired, identity recognition and authentication are accomplished by using a multi-information fusion method. By using the conventional face recognition technology as main recognition basis and using identity card information and bank credit records as auxiliary information, the accuracy and stability of the identity recognition are guaranteed, and the method can be applied to the identity recognition and authentication of the self-service equipment of the bank, so that the working load of the bank is reduced, working efficiency and the quality of service are improved, and office intelligentization is realized.
Owner:UNIV OF SCI & TECH OF CHINA
Network game virtual assets on-line management method and system
InactiveCN101082941AGuarantee safe and reliableTransactions are more flexibleApparatus for meter-controlled dispensingCommerceVirtual propertyData exchange
The invention discloses an on-line managing method and system for virtual asset of network game, which is characterized by the following: building on-line managing platform with register, transfer, transaction and payment to support user end; establishing an accommodator between management platform and operational businessman of network game; giving a series of standardizing definition for accommodator; exchanging data between managing platform and game database of operational businessman of network game; realizing on-line register, transfer, transaction and payment of virtual asset of network game for user end.
Owner:GOODHOPE CORP
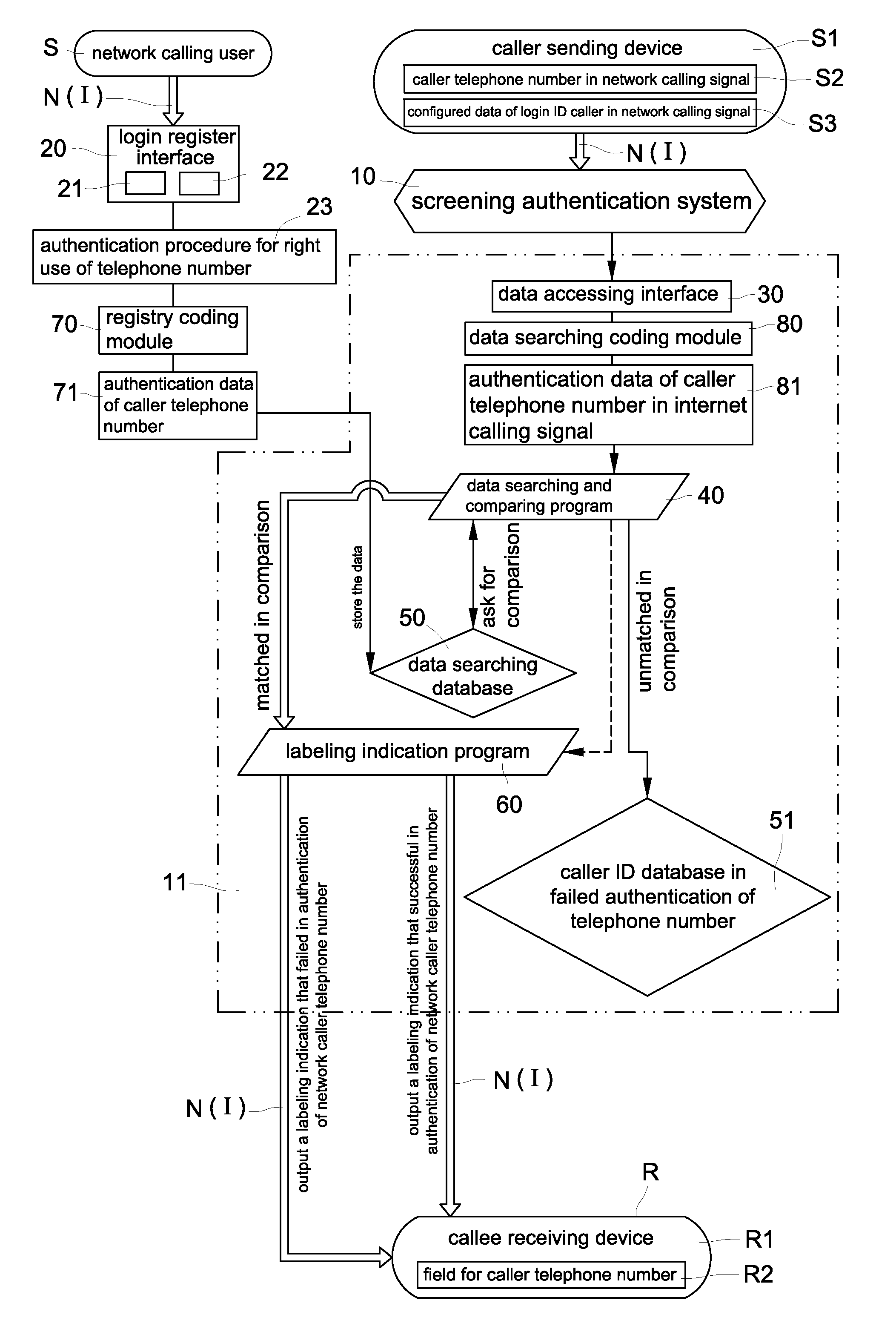
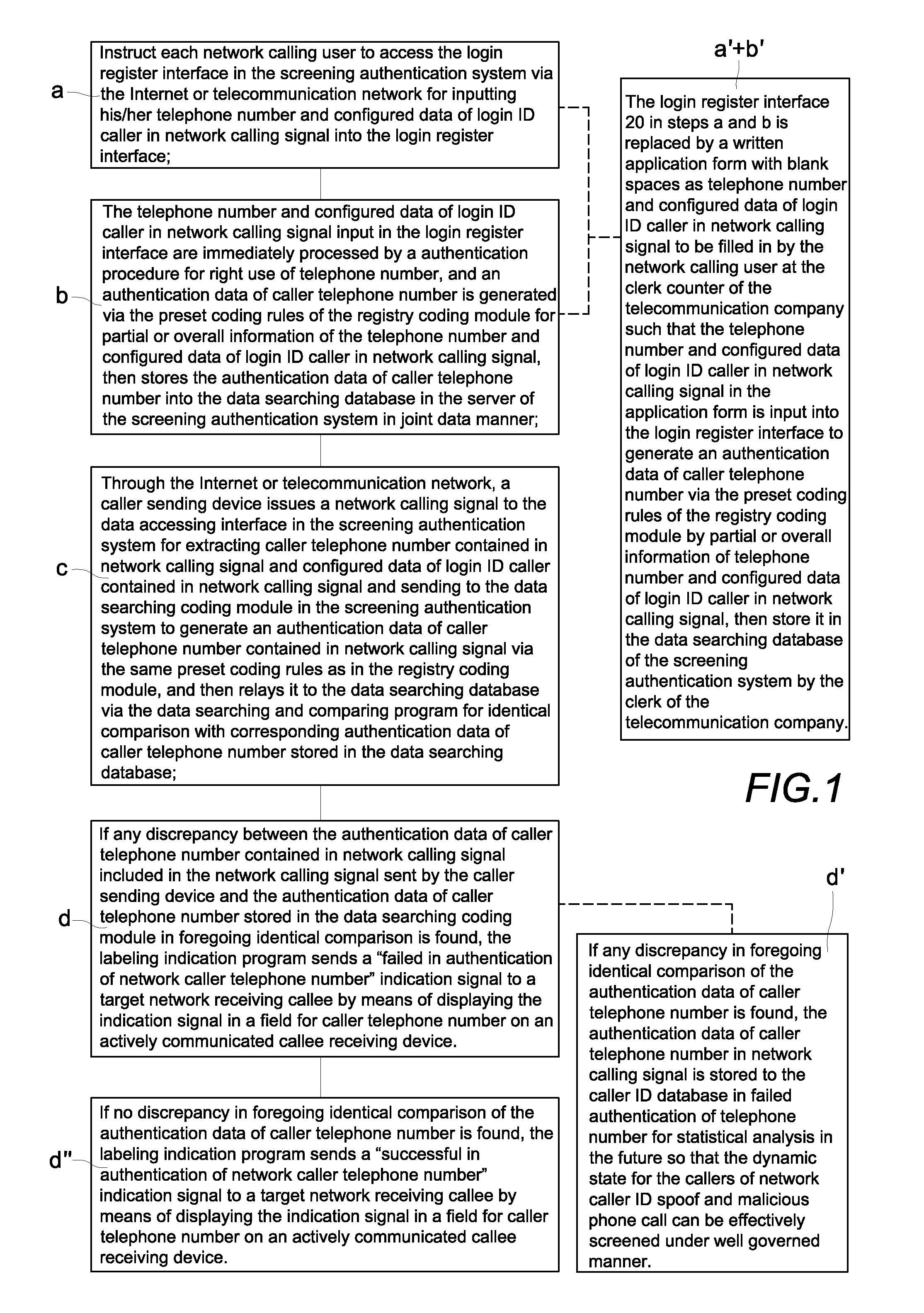
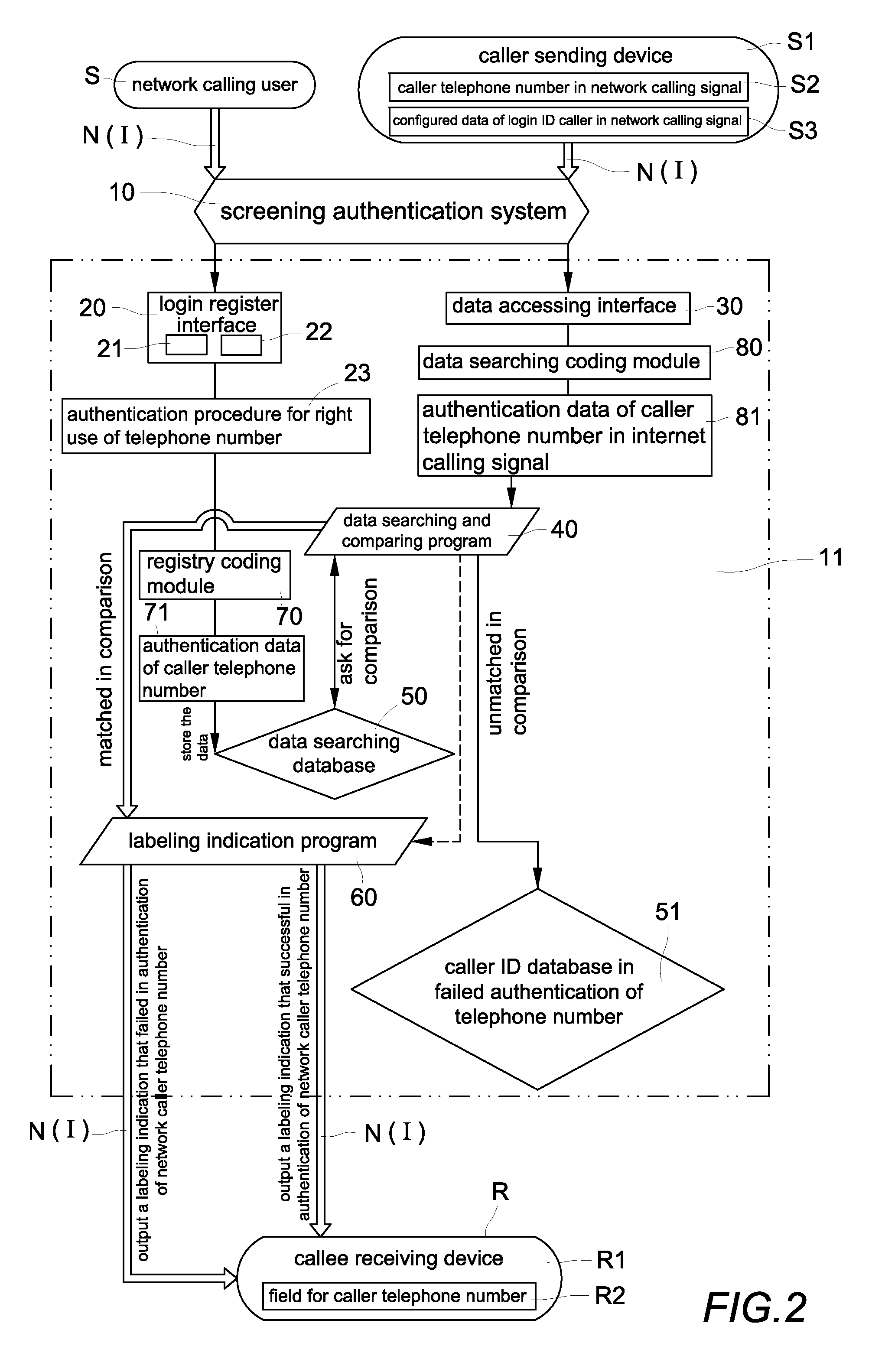
Authentication method and system for screening network caller ID spoofs and malicious phone calls
ActiveUS9264539B2Crime of fraudulent telephone calling can be effectively reducedReduce crimeSpecial service for subscribersCalled number recording/indicationCode moduleData access
An authentication method and system for screening network caller ID spoofs and malicious phone calls includes a screening authentication system with a server that includes a login register interface, a data accessing interface, a data searching and comparing program, a data searching database, a labeling indication program, a registry coding module and a data searching coding module. Authentication data is generated by the registry coding module from a caller telephone number and caller login identification data input during registration. Corresponding authentication data contained in a network calling signal from a caller sending device is generated by a data searching coding module. A data searching and comparing program compares the authentication data and, if any discrepancy is found, a labeling indication program sends a “failed authentication” signal to the target network receiving callee so that a fraudulent call is detected.
Owner:LIN CHUNG YU
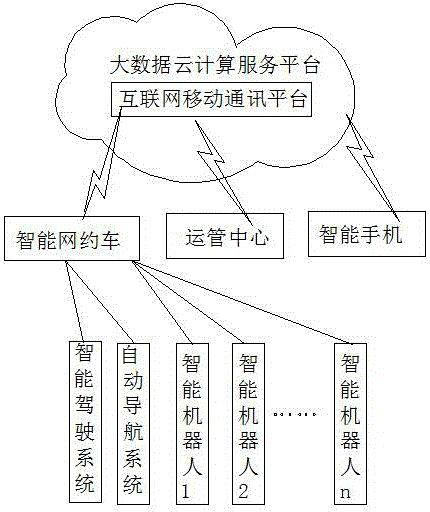
Big data cloud computing service-based steering wheel-free intelligent network reservation car system and operation method
PendingCN106549981AEase traffic congestionReduce consumptionData processing applicationsTransmissionIntelligent NetworkSteering wheel
The invention provides a big data cloud computing service-based steering wheel-free intelligent network reservation car system and an operation method. An intelligent driving system and an automatic navigation system which are connected with big data cloud computing services are arranged in an intelligent network reservation car; an intelligent robot composed of a touch screen, a mobile phone data interface or bank card interface, a camera and a voice interactive system is installed at the front of each seat; a luggage cargo monitoring camera which is connected with the intelligent robot and is used for monitoring luggage and cargo in real time is arranged in the trunk of the car; when monitoring information indicates that the trunk is opened or a passenger or a cargo owner gets off, the intelligent robot carries out real-time display or voice prompting; the intelligent driving system and the intelligent robot transmit the car use information of the passenger or cargo owner to a transport management center in real time through the Internet; the transport management center controls the intelligent driving system through the Internet to make the intelligent driving system automatically drive the intelligent network reservation car according to starting and termination paths required by the passenger or cargo owner; and the intelligent robot is connected with the transport management center in real time through the Internet and transmits the information of the interaction between the passenger or cargo owner and the intelligent robot and transportation expense settlement to the transport management center.
Owner:邹城众达知识产权咨询服务有限公司
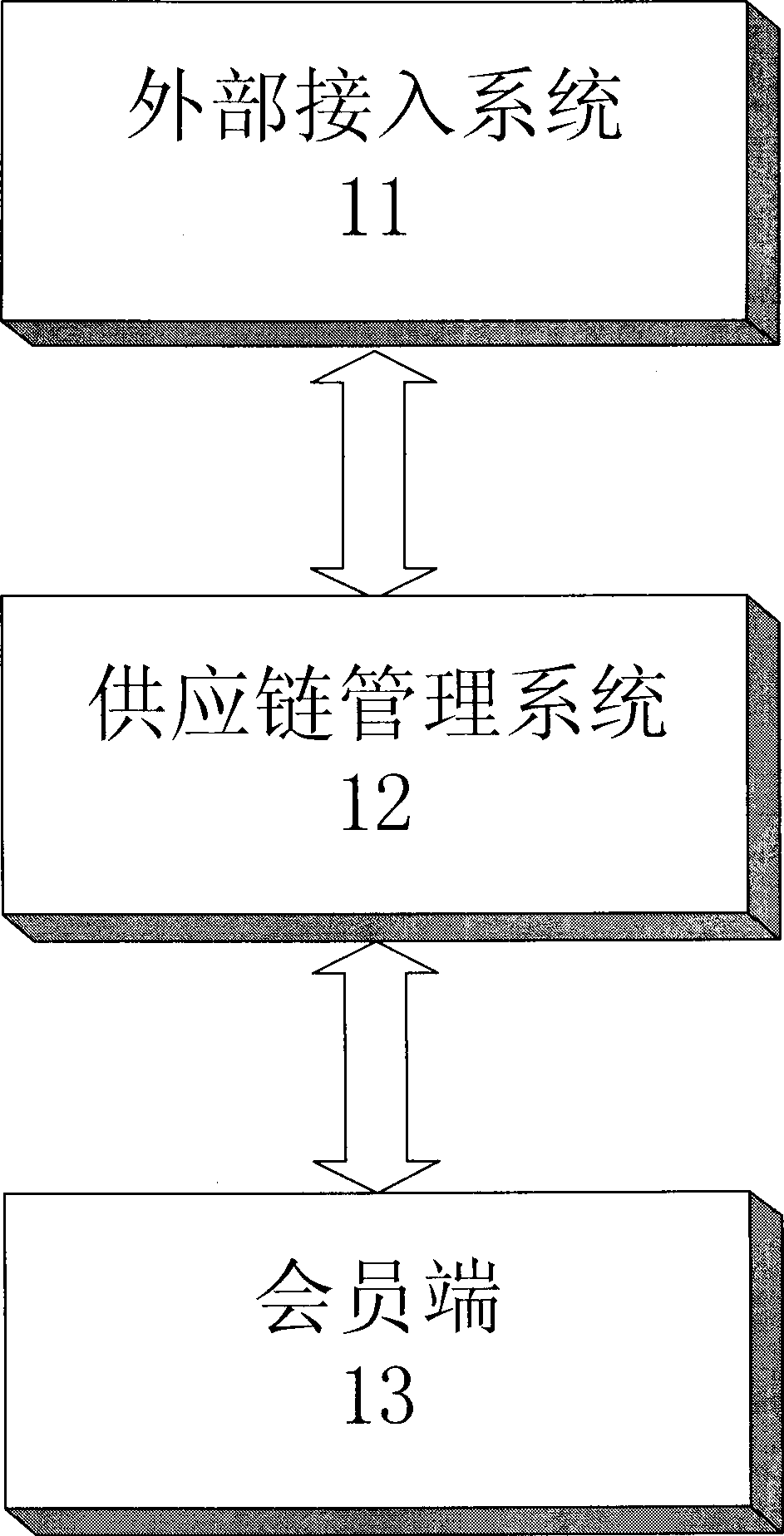
Supply chain management system and method
InactiveCN101388092AProtection of legitimate rights and interestsImprove management efficiencyCommercePaymentLogistics management
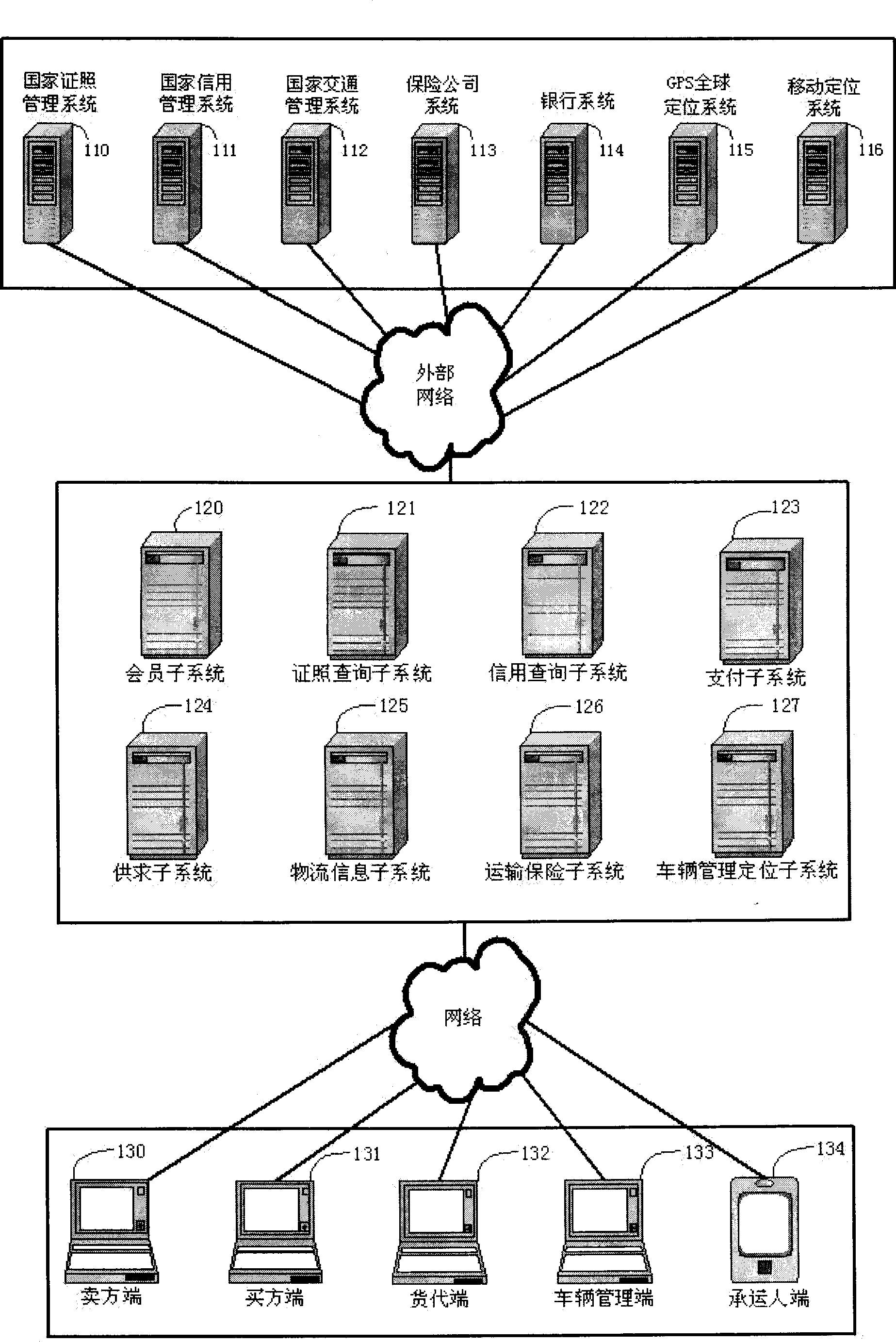
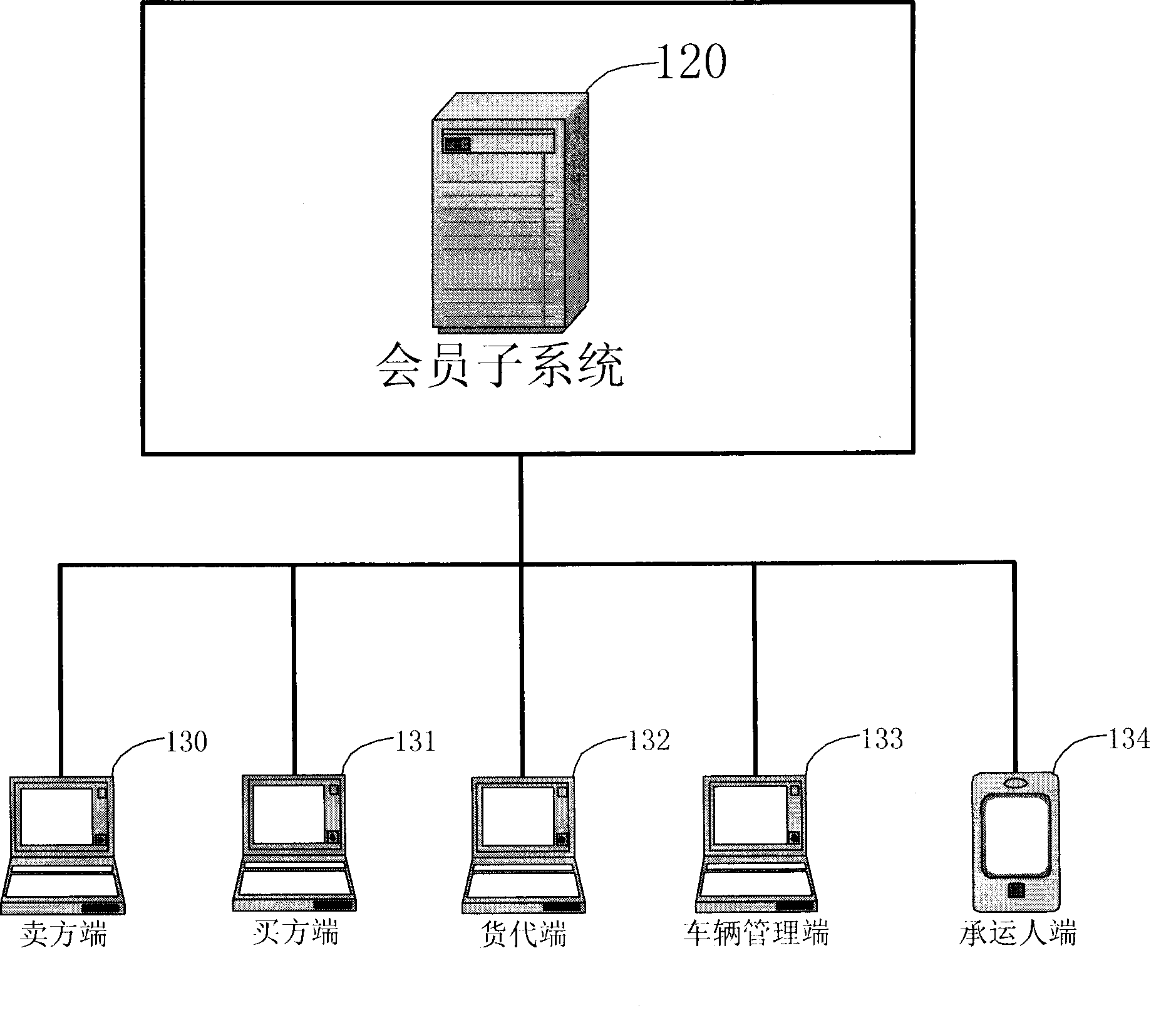
The utility model provides a supply chain management system and a method, in particular to a supply chain management system and a method for communication networks and the internet. The system comprises an external access system, a logistics management system and a client. The supply chain management system and the method can resolve the problems of supply chains and logistics industry in arrears with payment for goods and freight charges, empty driving of freight vehicles, difficult vehicle management, resource waste, low energy utilization rate, high logistics cost, goods lost and goods gaining via defraud and the like. The invention can be widely applied to supply chains, logistics, transportation and insurance fields.
Owner:SHENZHEN GUOXUNTONG TECH INDAL +1
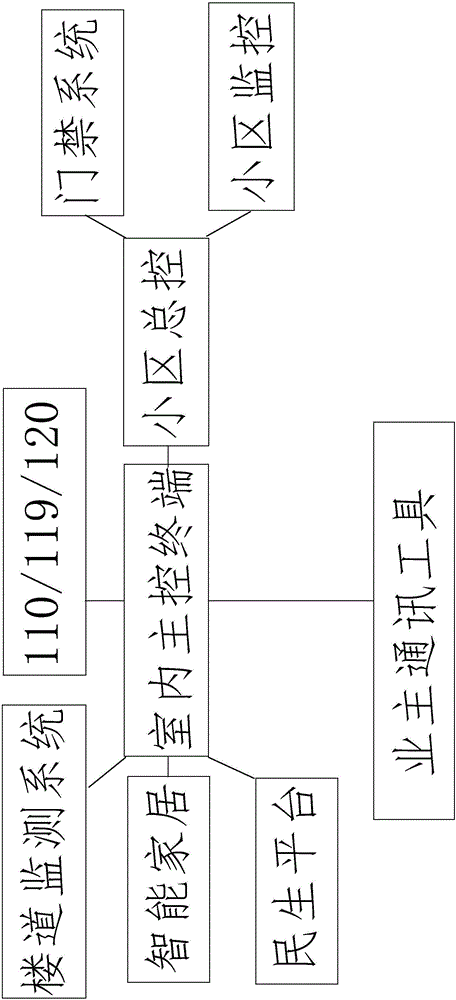
Intelligent security protection intercom system capable of controlling household appliances and realization method of intelligent security protection intercom system
InactiveCN106658235ASolve poor communicationImprove the quality of lifeAlarmsStations for two-party-line systemsTablet computerAnti virus
The invention discloses an intelligent security protection intercom system capable of controlling household appliances and a realization method of the intelligent security protection intercom system. The intelligent security protection intercom system mainly comprises an access control system, a corridor monitoring system, an indoor main control terminal and a community general controller; the corridor monitoring system includes a monitoring device, a loudspeaker, a microphone, an illumination device and a backup power source and is connected with the indoor main control terminal; and the indoor main control terminal is an intelligent terminal such as a tablet computer and is mainly equipped with an operating system, remote control software, a blocking system, anti-virus software, sound changing software, a loudspeaker, a microphone, a memory, a USB, Bluetooth and / or an infrared device, a programmable controller, a backup power source, a communication tool bound with the mobile phone card of an owner, and so on. With the intelligent security protection intercom system capable of controlling household appliances adopted, information sent by a people's livelihood platform can be received; the owner can be connected; one-key rescue can be realized; access control passwords can be changed; house maintenance requests can be submitted; programming can be performed to control a smart home; hackers can be blocked; early warning can be performed; calls can be transferred; remote responding can be realized; the owner will be called when an alarm is received; remote control is accepted; and the community general controller can be switched to the corridor monitoring system.
Owner:赵莉莉
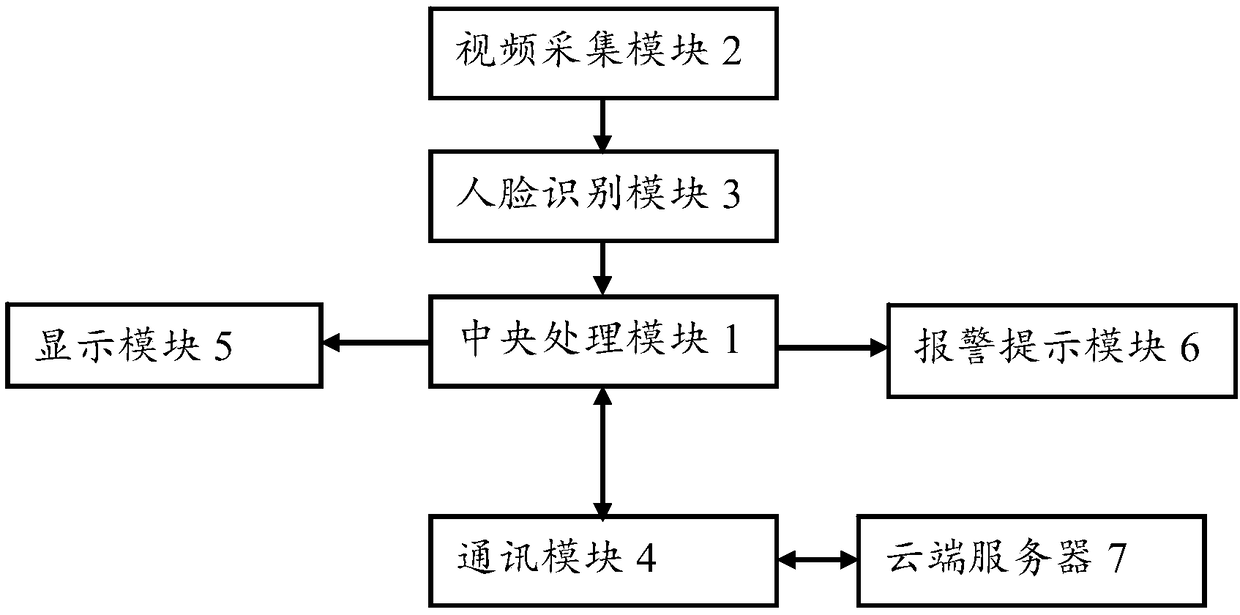
Face recognition system and method of law enforcement recorder
PendingCN109117821AImprove Law Enforcement EfficiencyIncrease intensityTelevision system detailsData processing applicationsTelecommunicationsImaging processing
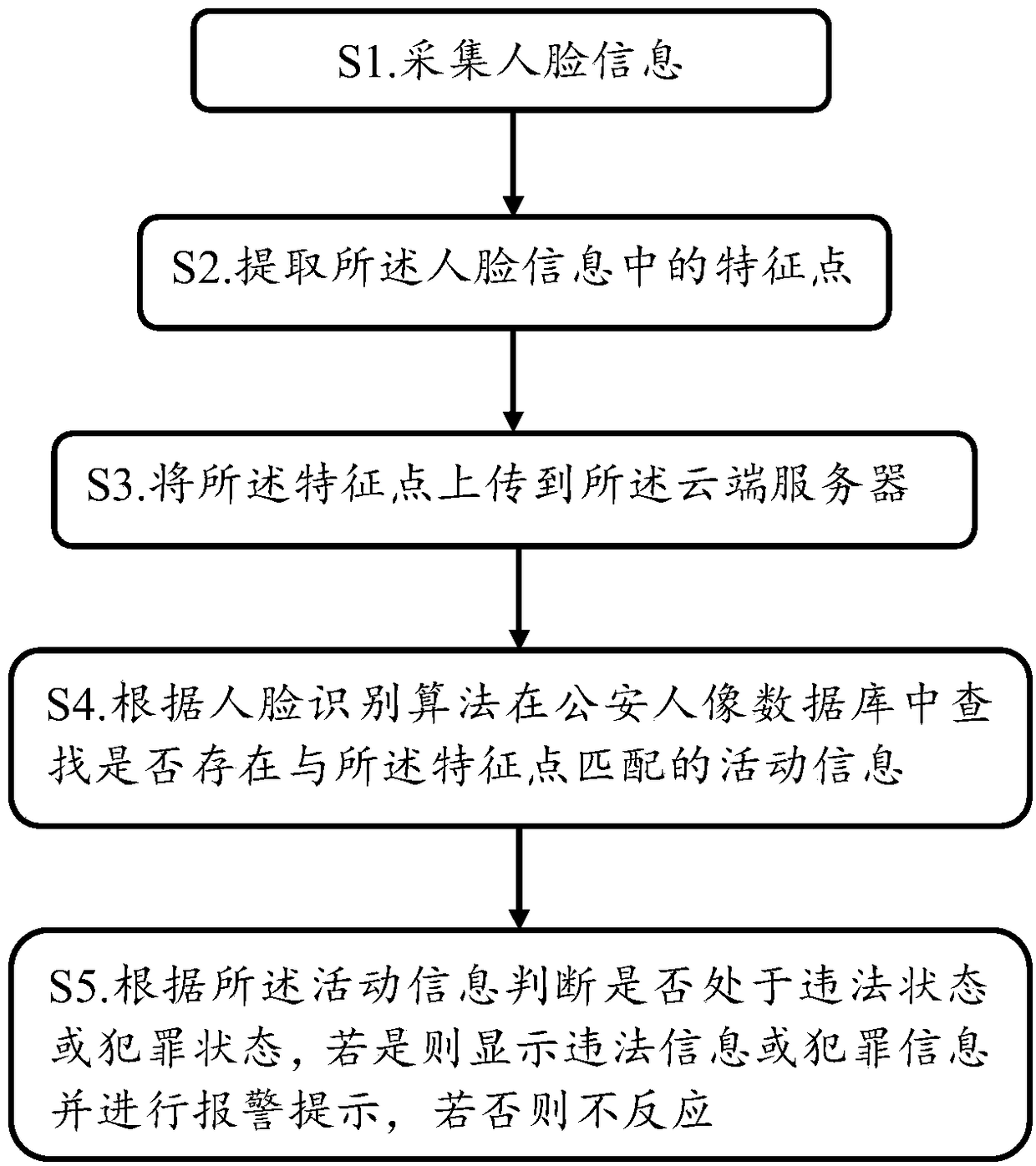
The invention relates to the technical field of law enforcement recorder, in particular to a face recognition system and method of law enforcement recorder. The system comprises a central processing module, a video acquisition module, a face recognition module, a communication module, a display module and an alarm prompt module connected with the central processing module, and a cloud server connected with the communication module. The invention has the advantages that: a video data or picture data is collected by a video acquisition module, a method for extracting feature points from video data (face information) by use image processing technology through a face recognition module, further sent to the cloud server for big data comparison, analysis of the current shooting range of people with illegal acts or more serious criminal acts or suspected criminal acts, to improve the law enforcement efficiency and law enforcement efforts of public security personnel.
Owner:UNIONMANTECH
Community personnel abnormal behavior monitoring scheme based on computer vision
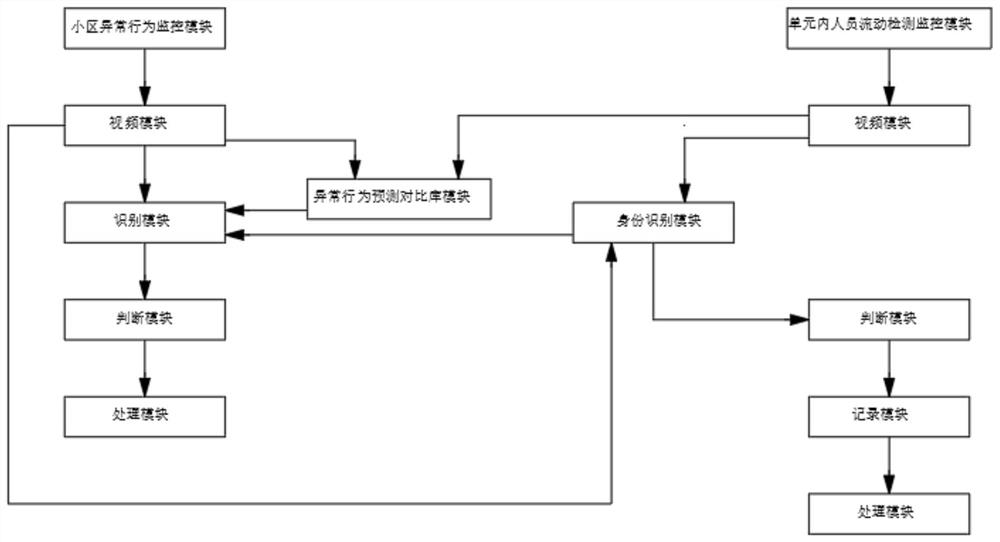
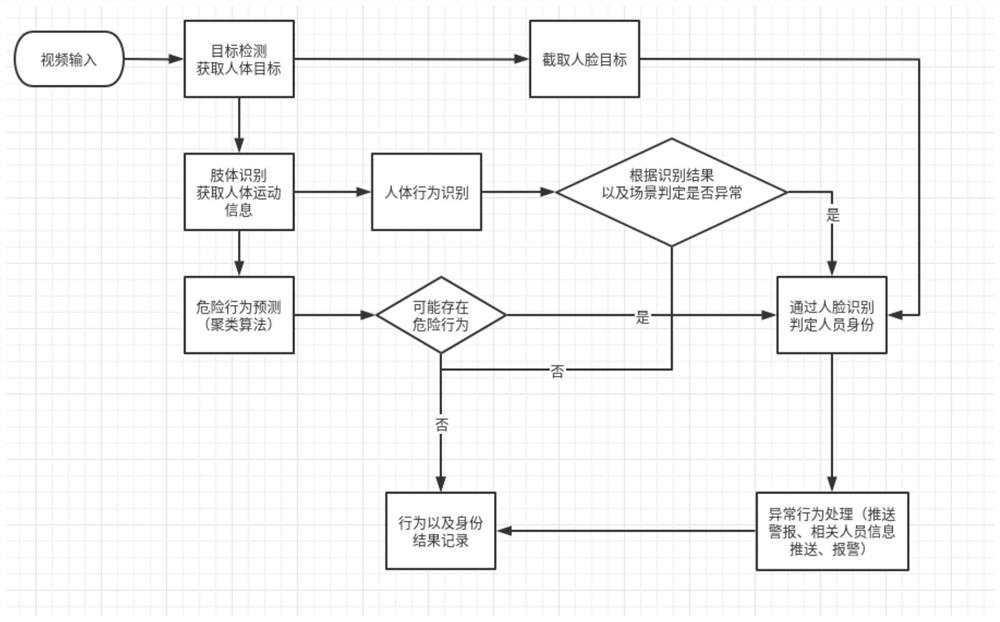
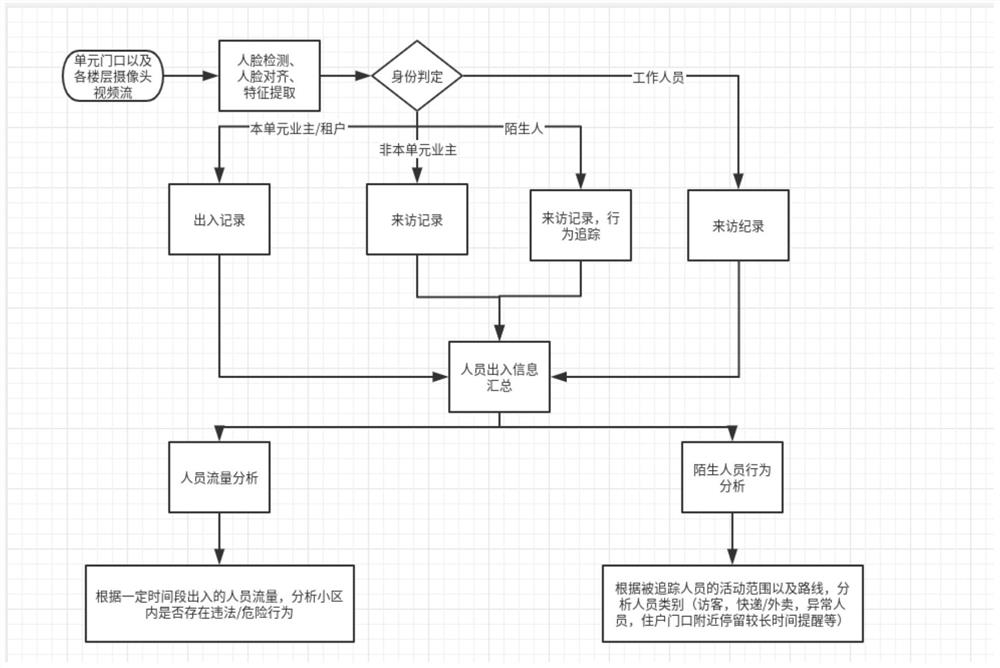
ActiveCN112132045AReduce crime and risky behaviorEnsure personal safety and property safetyCharacter and pattern recognitionAlarmsComputer securityData science
The invention discloses a community personnel abnormal behavior monitoring scheme based on computer vision in the technical field of monitoring systems, and realizes a safety protection monitoring system on the basis of an alternating current network by taking a camera as an acquisition port. According to the invention, by use of personnel and stranger flow and action areas detected in the camera,through computer vision and big data analysis, whether the personnel are personnel in a community is intelligently distinguished, various abnormal behaviors can be identified, abnormity can be foundin time, security personnel can be reminded to warn and stop some illegal and dangerous behaviors, and the safety of the personnel is improved. The cradle can purify the community environment, reduceillegal crimes and dangerous behaviors in the community, prevent community personnel from being hurt first and then obtain compensation and protection, so that the danger and illegal behaviors of thecommunity are killed in the cradle, the danger and illegal behaviors are truly prevented from happening, and the personal safety and property safety of community owners are guaranteed.
Owner:天津锋物科技有限公司
Safe anti-theft self-help single-door kiosk bank
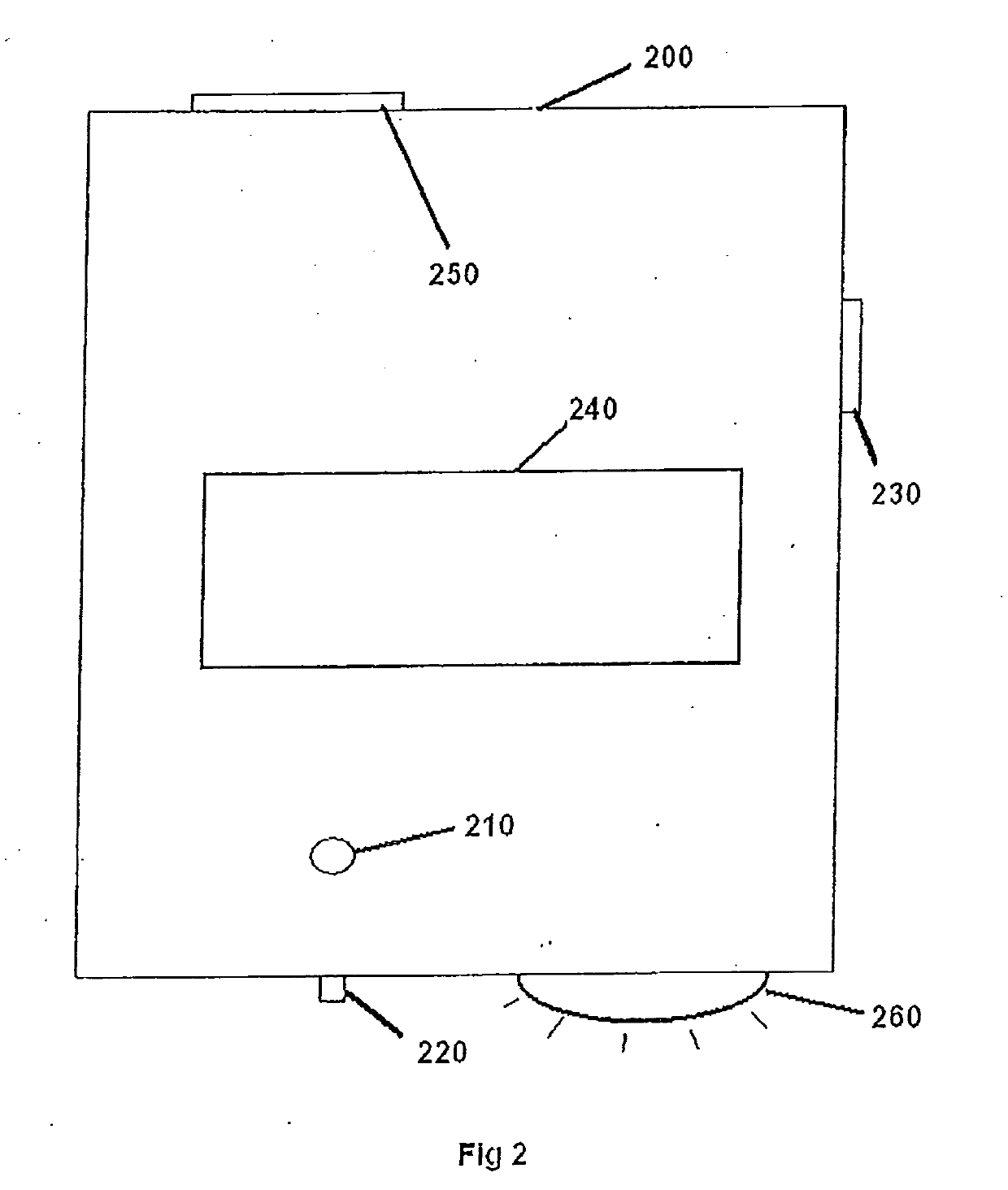
InactiveCN103291091AOperational securityIngenious designSmall buildingsSurveillance cameraEngineering
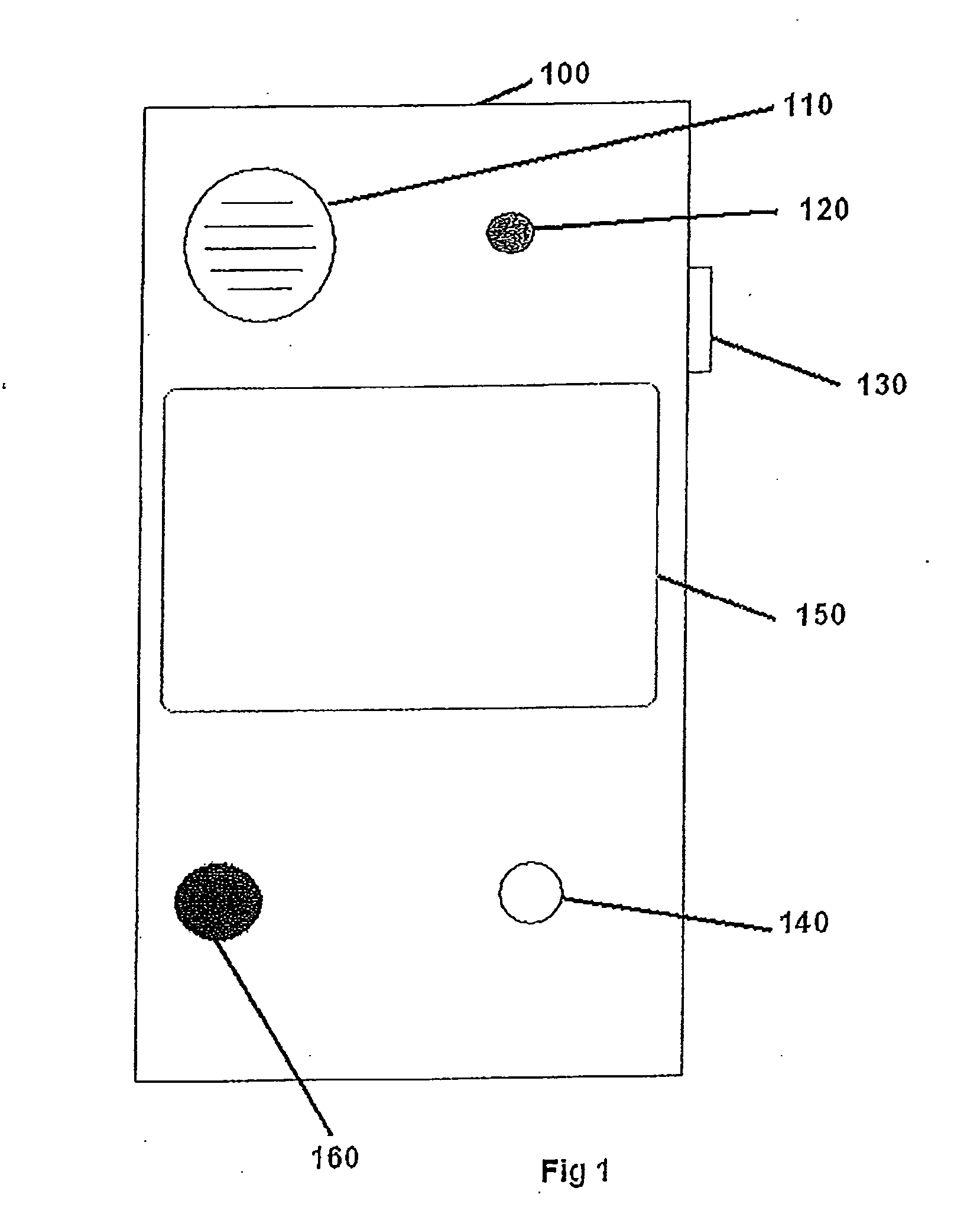
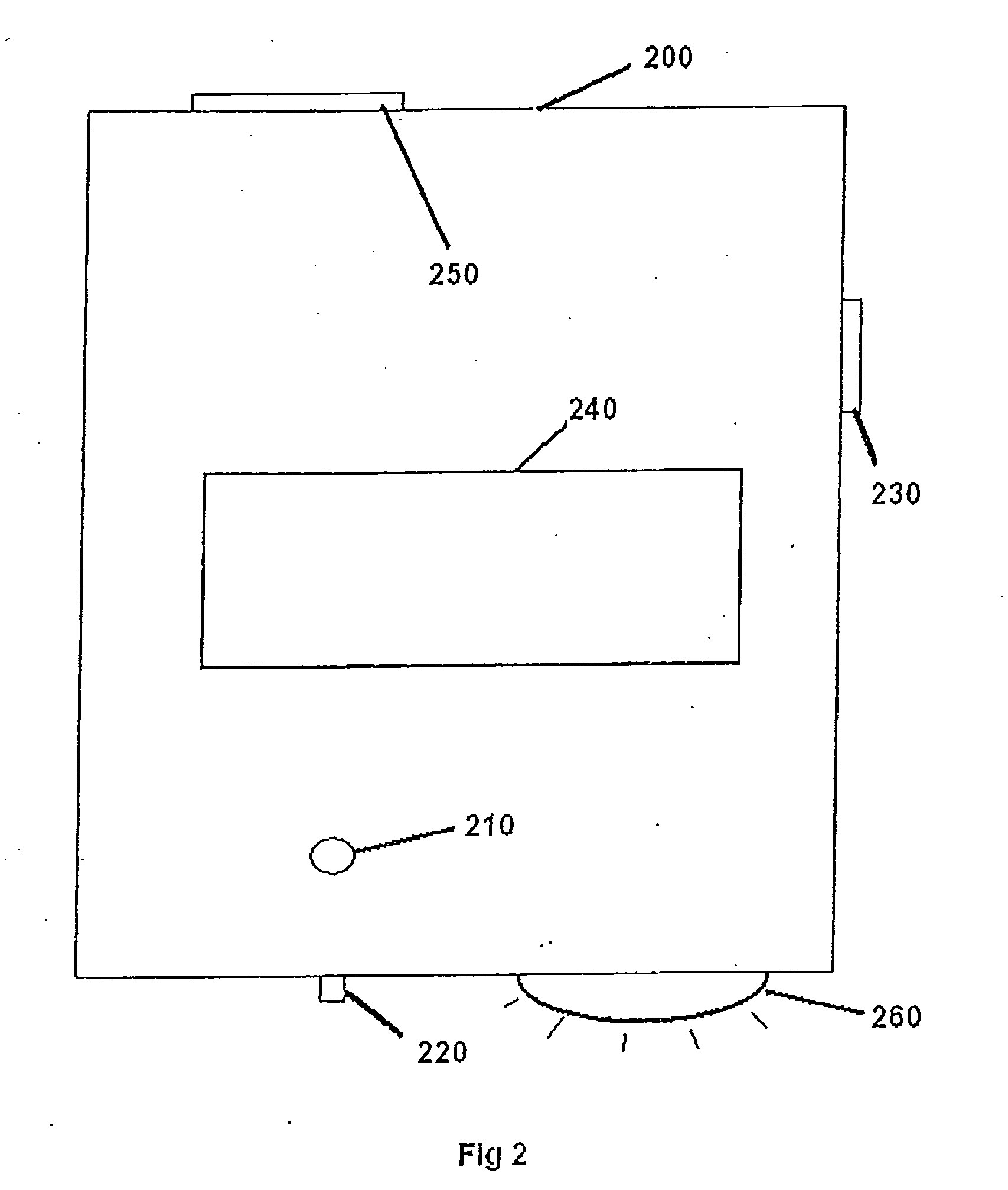
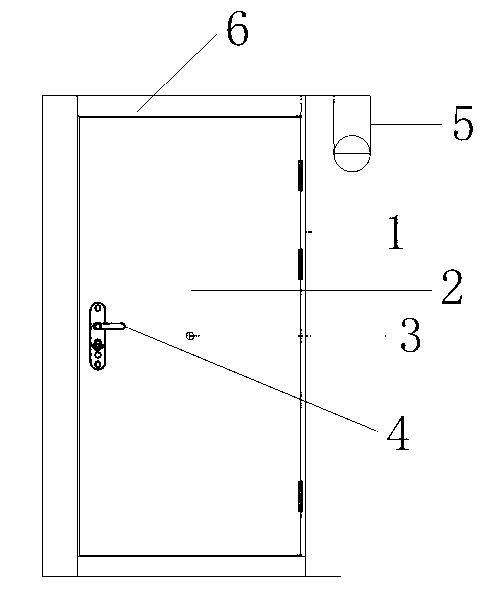
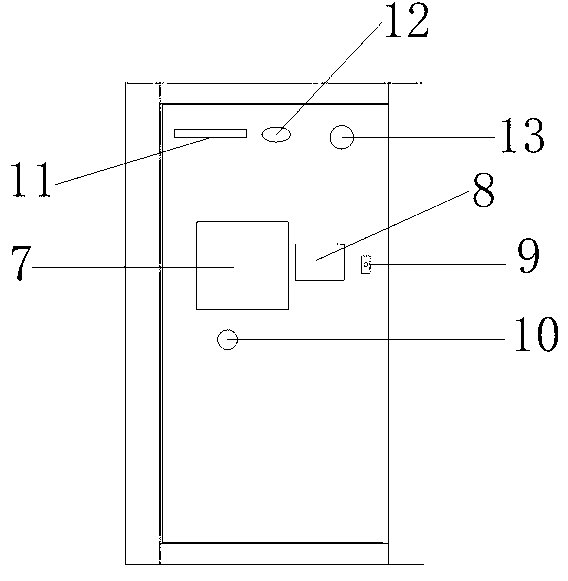
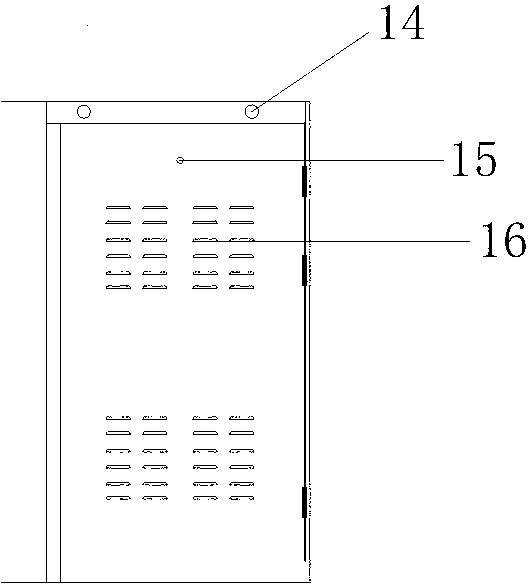
The invention discloses a safe anti-theft self-help single-door kiosk bank which comprises a kiosk body (1) and a security door (2). A door-opening button (3) and a door knob (4) are arranged on the security door (2), a kiosk external monitoring camera (5) is arranged at one corner of the top end of the kiosk body (1), an acrylic lamp box (6) is installed at the top end of the kiosk body (1), an ATM (7) is installed in the middle of the inner portion of the kiosk body (1), an automatic induction control device (10) is installed at the lower portion of the ATM (7), an alarm communicator (8) is arranged near the ATM (7), a going-out button (9) is arranged on the right side of the alarm communicator (8), and a lighting LED lamp (11), a ventilation port (12) and a kiosk internal monitoring camera (13) are sequentially arranged at the upper portion inside the kiosk body (1). The safe anti-theft self-help single-door kiosk bank is ingenious in design, novel in style, convenient to use, practical, safe and reliable, provides a safe and comfortable environment for people who deposit and withdraw money in and from the ATM, and provides a guarantee for reducing ATM crimes.
Owner:QINGDAO HONGFULIN AUTOMATION TECH
Volcanic rock sound-proof noise barrier
InactiveCN103184726ANoise reduction or eliminationStrong absorption capacityNoise reduction constructionNoise barrierEngineering
The invention belongs to the technical field of sound elimination and noise reduction, and relates to a sound-proof noise barrier / sound-proof noise screen board used on two sides of highways and railways and inside factories, in particular to a sound-proof noise barrier / sound-proof noise screen made of natural volcanic rocks. The sound-proof noise screen board / sound-proof noise barrier disclosed by the invention is formed by a volcanic rock hollow frame and multiple conical volcanic rocks arranged in the volcanic rock hollow frame, wherein multiple through holes are formed in an upper surface board of the volcanic rock hollow frame; the multiple conical volcanic rocks are arranged in the through holes with the bottom parts upward; the bottom parts of the conical volcanic rocks are tightly and upwards clamped on upper slabby rocks of the hollow frame; the cone bottom parts of the conical volcanic rocks are flush with an outer wall of the upper surface board of the volcanic rock hollow frame; the cone top parts of the conical volcanic rocks are placed downwards; the top parts of the conical volcanic rocks are tightly and downwards clamped on lower slabby rocks of the hollow frame; and the top surfaces of the conical volcanic rocks are flush with the lower slabby volcanic rocks. Multiple pieces of volcanic rock sound-proof noise screen board / sound-proof noise barrier are mounted and fixed on a steel structure column in an upper-lower parallel stacked manner, and thus an integral sound-proof noise barrier / sound-proof noise screen board can be formed.
Owner:刘仁栋
Management system for restricting young person top wire
InactiveCN101442424AReduce the family burdenReduce crimeUser identity/authority verificationData switching networksYoung personBody growths
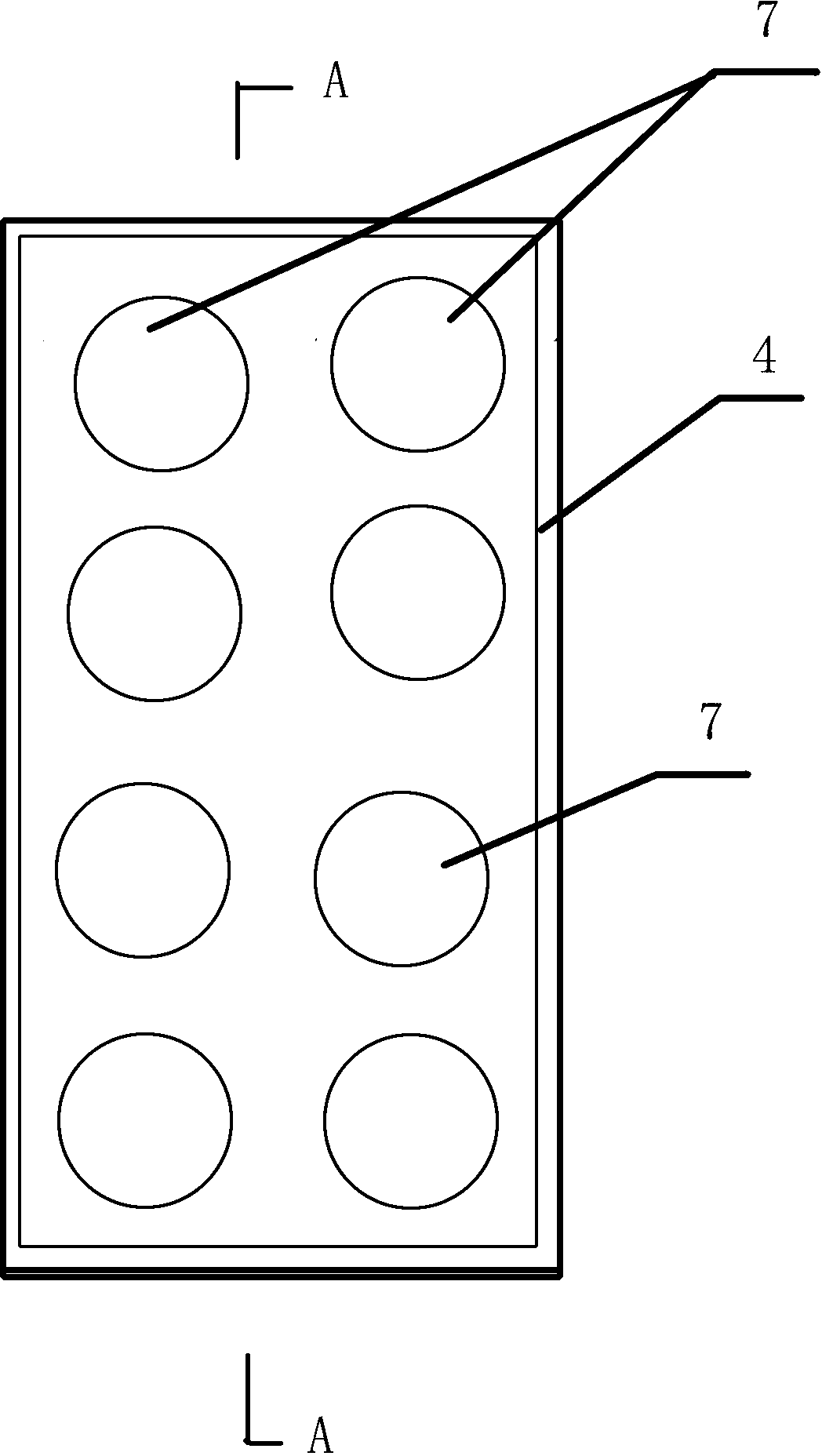
The invention provides a management system for restricting minor surfing, which is equipment organically combining smoke detecting technology, photographing technology, image and character acquisition technology and computer network software technology. The system realizes control of the minor surfing and prevention of surfing people from smoking at an Internet bar by the prior technologies of smoke detection, camera software control and network transmission, can completely control network criminal cases in surfing process, and can accurately and effectively provide arresting evidence of an at-large criminal hiding at the Internet bar in time for police. The invention solves the problem of management deficiency existing in the prior art, creates a good environment for sound mind and body growth for the minors, provides a smokeless, safe, fresh and comfortable surfing place for surfing people, and has a function of powerfully fighting against criminals and people at large.
Owner:祝永民 +1
Method for enabling hijacker not to dare to withdraw money with passwords
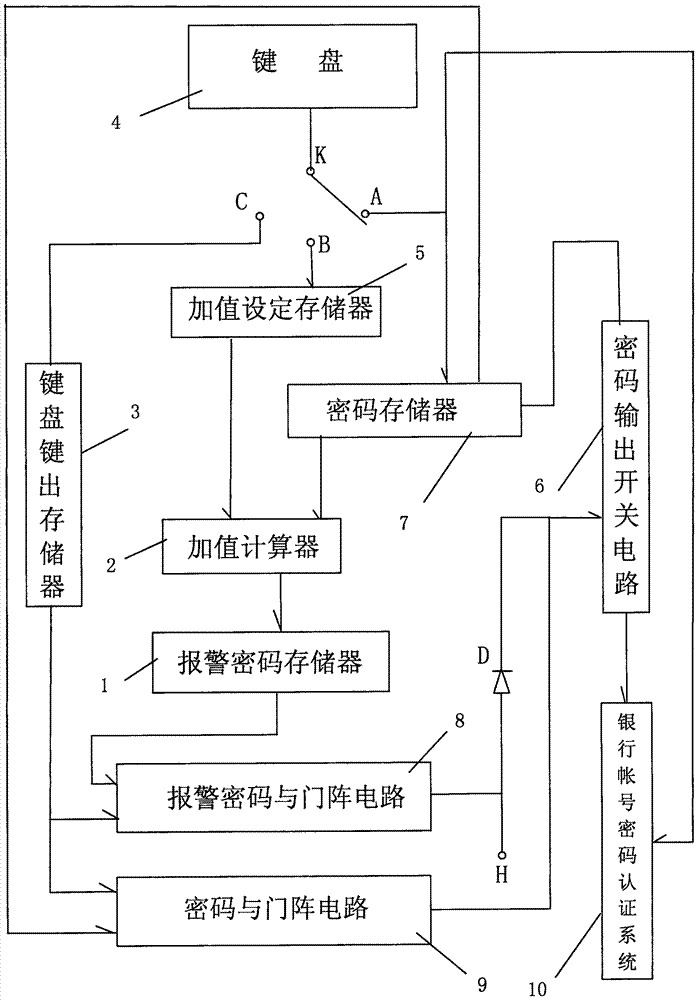
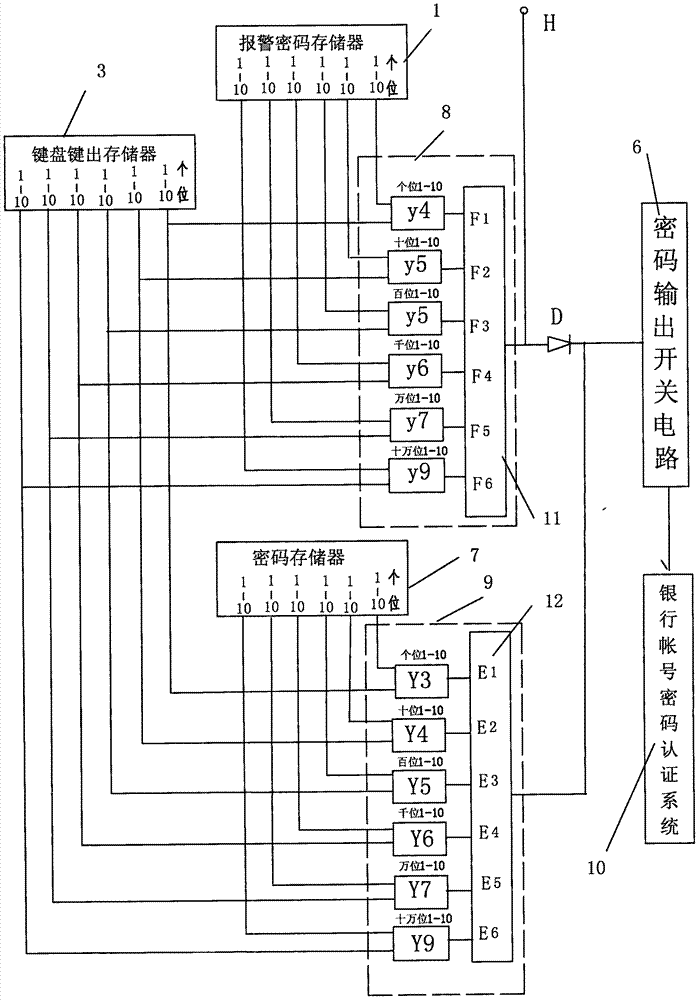
ActiveCN107578576AAvoid harmSolve the detection speed is slowComplete banking machinesDigital data authenticationPaymentPassword
The invention discloses a method for enabling a hijacker not to dare to withdraw money with passwords. In the method, a bank payment and collection tool is involved, an anti-hijacking contact is arranged on a password keyboard of the payment and collection tool, a depositor can use the anti-hijacking contact for inputting a 'add value number' into an 'add value setting storage device', wherein theadd value number is easy to remember and much lower than the digits of the passwords, 'alarm passwords' which are obtained by adding the 'add value number' to a 'password number' through an 'add value calculation device', in this way, the alarm codes have a password function, in addition, the function of giving an alarm to the law-enforcing department is achieved, and when the depositor suffers from threatening from the hijacker, the alarm passwords can be submitted to the hijacker or are used by self to give an alarm; the alarming function can be selected by the depositor , but the crime will experience shock power even if the bank payment and collection tool has the type of function and is selected by a small quantity of depositors, the hijacker dares not to withdraw money from a bank even if the hijacker asks the depositor for the passwords, and therefore the generation of invalid password obtaining cases will be reduced through the method.
Owner:张德珍
Floating population management method and system based on block chain
PendingCN112699418AReliable dataImprove securityDigital data protectionIndividual entry/exit registersFloating populationBlockchain
The invention belongs to the technical field of block chains, and relates to a floating population management method and system based on a block chain, which combine a security chip, an intelligent door lock and a block chain technology and are comprehensively applied to related scenes of floating population management. According to the floating population management method and system, privacy protection, data credibility, collaborative credible sharing, light weight, safety and reliability are achieved, wherein the intelligent door lock used in the method is internally provided with the safety chip, has the unique identity ID and cannot be copied or cracked; a built-in secret key of the safety chip is used for digital signature of block chain transaction in combination with the block chain technology; therefore, credibility of original data stored on the block chain is guaranteed, the door lock safety is greatly enhanced and related crimes are reduced; besides, the system is connected with the public security government affair block chain, the capacity that the time and content of uplink data cannot be tampered, traced and audited is achieved, the cooperation capacity between government affair institutions and departments can be improved conveniently, and accurate and efficient management of floating population is realized.
Owner:杭州宇链科技有限公司
Infection control monitoring system
ActiveUS20190279491A9Reduce crimeIncrease ratingsDiscounts/incentivesAlarmsEngineeringPublic Facility
The invention provides an automated hand hygiene / infection control monitoring sensor-based system suitable for improving hand hygiene and multiple infection control measures and ensuring compliance by health care workers as well as visitors to hospitals and clinics. The use of biometric identification devices such as cameras for face recognition and profiling, microphones for voice recognition, etc. permit highly accurate identification without the use of removable identification devices such as identification badges which may include bar codes, magnetic strips or wireless devices such as RFIDS. Identification badges are removable and hence susceptible to being lost, misplaced, etc. Visitors are typically not assigned identification badges and hence enforcement of hand hygiene policies is minimal. Additional applications include reducing food contamination in food industry, the spread of diseases in schools, in businesses, in corporations and governmental facilities and public access facilities such as public restrooms, dining areas and transportation.
Owner:MINNESOTA IMAGING & ENG
Monitoring system and method for state of resident identity card
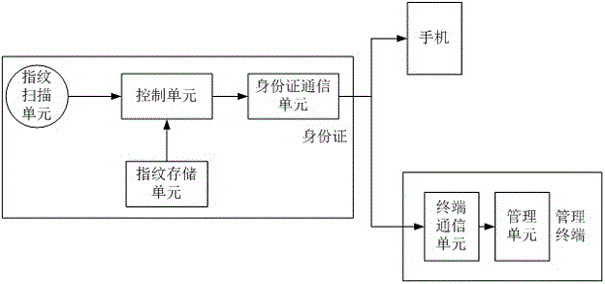
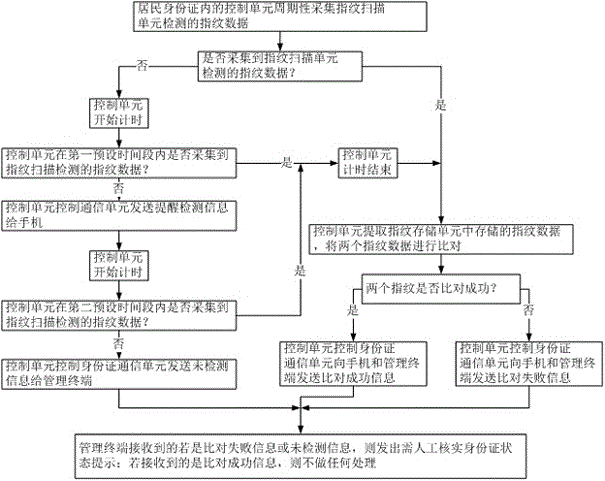
InactiveCN106485240ATimely processingStatus in real timeMultiple biometrics useCommunication unitMonitoring system
The invention discloses a monitoring system and method for the state of a resident identity card. A fingerprint scanning unit, a control unit, a fingerprint storage unit and an identity card communication unit are integrated in the resident identity card; the fingerprint scanning unit is used to verify the identity of a present card holder regularly, and if the present card holder is not a valid holder, the identity card notifies a bound mobile phone and a management terminal of verification failure of the identity card; when the valid holder forget to verify the identity regularly, the identity card sends information to the bound mobile phone to remind the valid holder of identity verification; and if the identity is not verified for a long time, the identity card notifies the management terminal, and a public system is warned whether the identity is in a loss state. Via the system and method, the valid holder and the public department can know the state of the identity card timely, preventive measures can be taken timely when the identity card is in the loss state, and crimes are reduced.
Owner:NANJING COLLEGE OF INFORMATION TECH
Novel domestic security alarm system
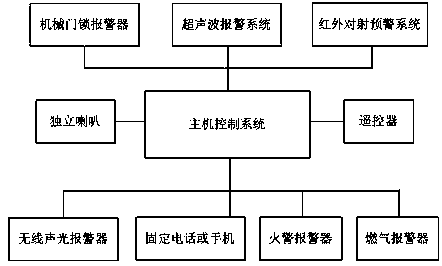
InactiveCN104077865AIntuitive and convenient queryIntuitive and easy controlsBurglar alarmEarly warning systemInformation transmission
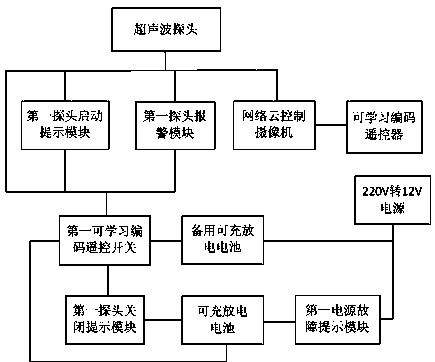
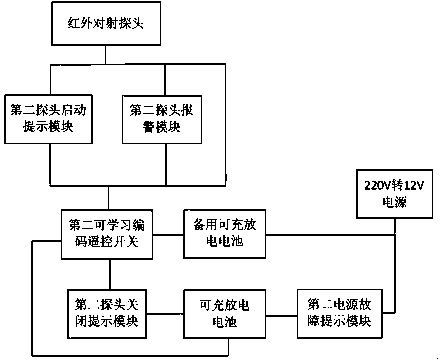
The invention discloses a novel domestic security alarm system which comprises a host machine control system, an ultrasonic wave alarm system, an infrared bijection early warning system, a mechanical door lock alarm apparatus and a fixed-line telephone or a mobile phone. The ultrasonic wave alarm system, the infrared bijection early warning system and the mechanical door lock alarm apparatus are respectively connected with the host machine control system, and the fixed-line telephone or the mobile phone is connected with the host machine control system. The infrared bijection early warning system has the expelling capacity, the ultrasonic wave alarm system can give an alarm before an interloper enters a room, alarm information and integral system working state information are provided for a user, the whole system has the transmitting capacity for the information such as self checking starting, normal closing, illegal closing, outage, switch damage, 220V-12V substation equipment damage, outage in a family and intruding alarming, motions can be automatically completed by the system, a report can be automatically given in time when needed, and waiting for inquiring by the user is not needed; corresponding mobile phone software is provided, and therefore the capacity of control, information searching and system setting is visually and conveniently provided.
Owner:李波
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com