System and method for detecting, alerting and blocking data leakage, eavesdropping and spyware
a technology of system and method, applied in the field of system and method for detecting, alerting and blocking data leakage, eavesdropping and spyware, can solve the problems of unauthorized access to sensitive information, high risk of malicious code attack on networked computing devices, and increased opportunity for cyber-crim
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
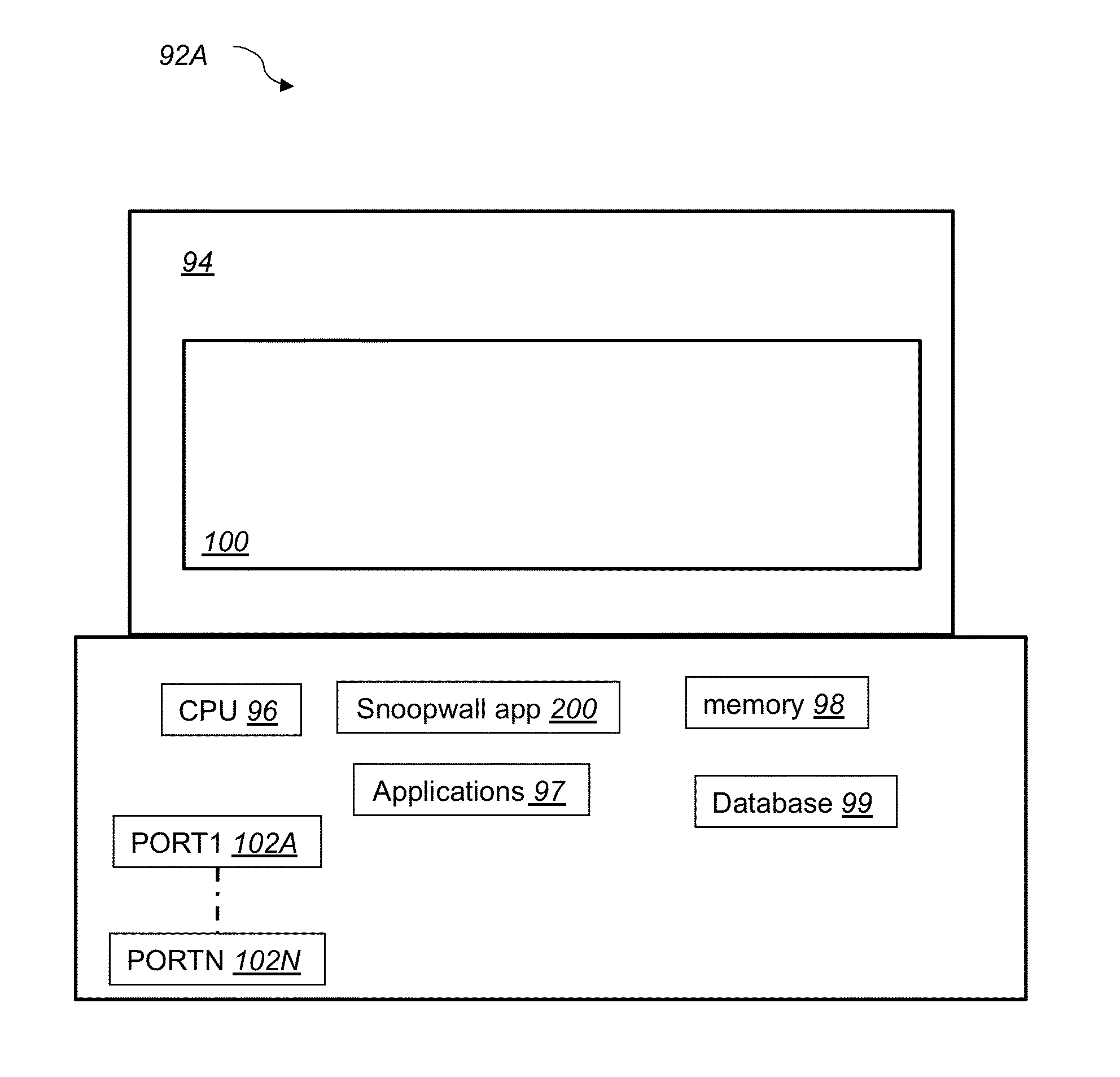
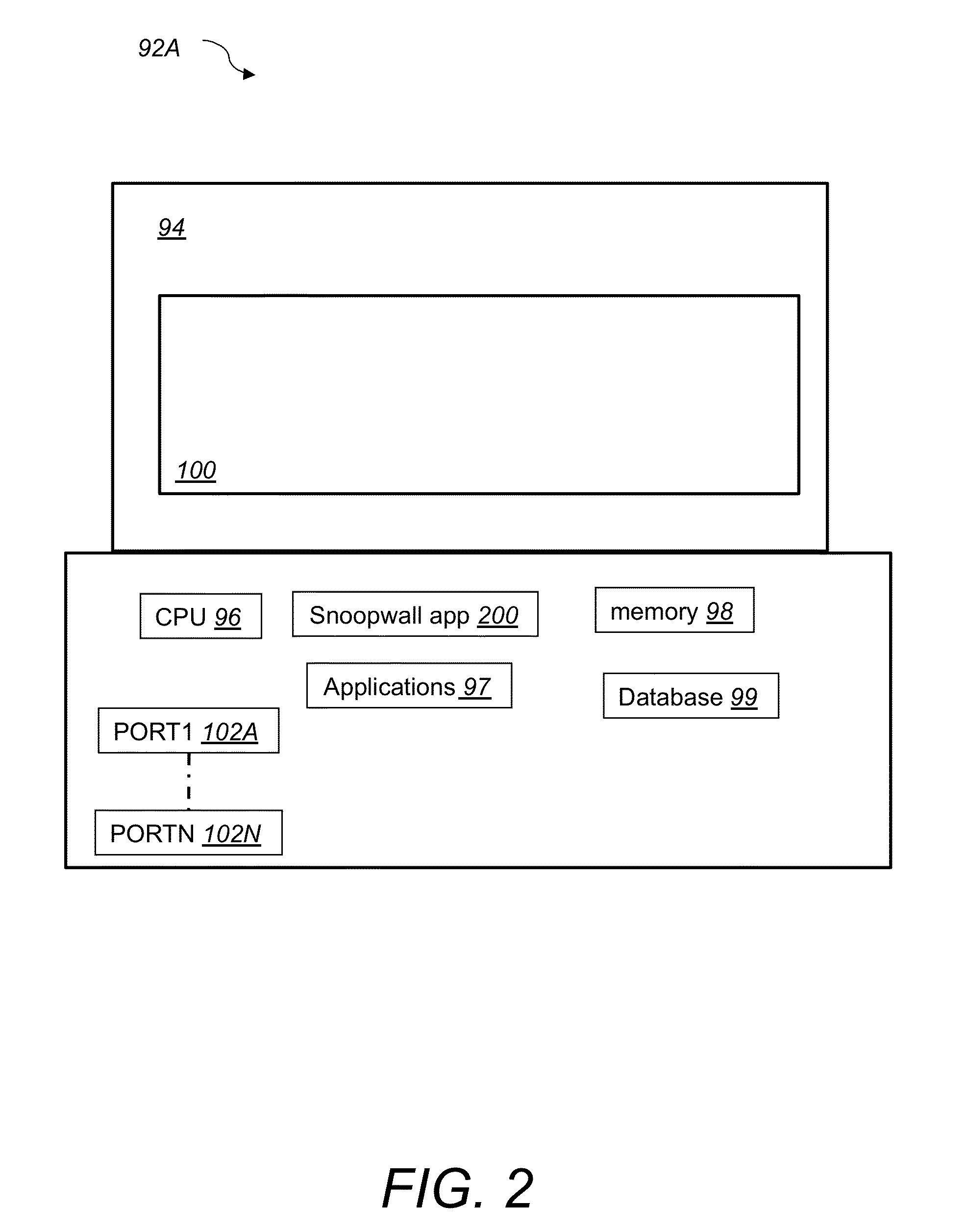
[0020]In general, the present invention relates to eavesdropping and spyware blocking technology, and more specifically it relates to systems and methods for blocking data leakage, eavesdropping and spyware technology in networked devices by controlling access to various high-risk data ports or hardware device interfaces. These high risk ports include Webcam, USB, Microphone, Flash Memory, Infrared, Bluetooth, Wireless, LAN, WAN, VPN, Cellular and GPS interfaces, among others.
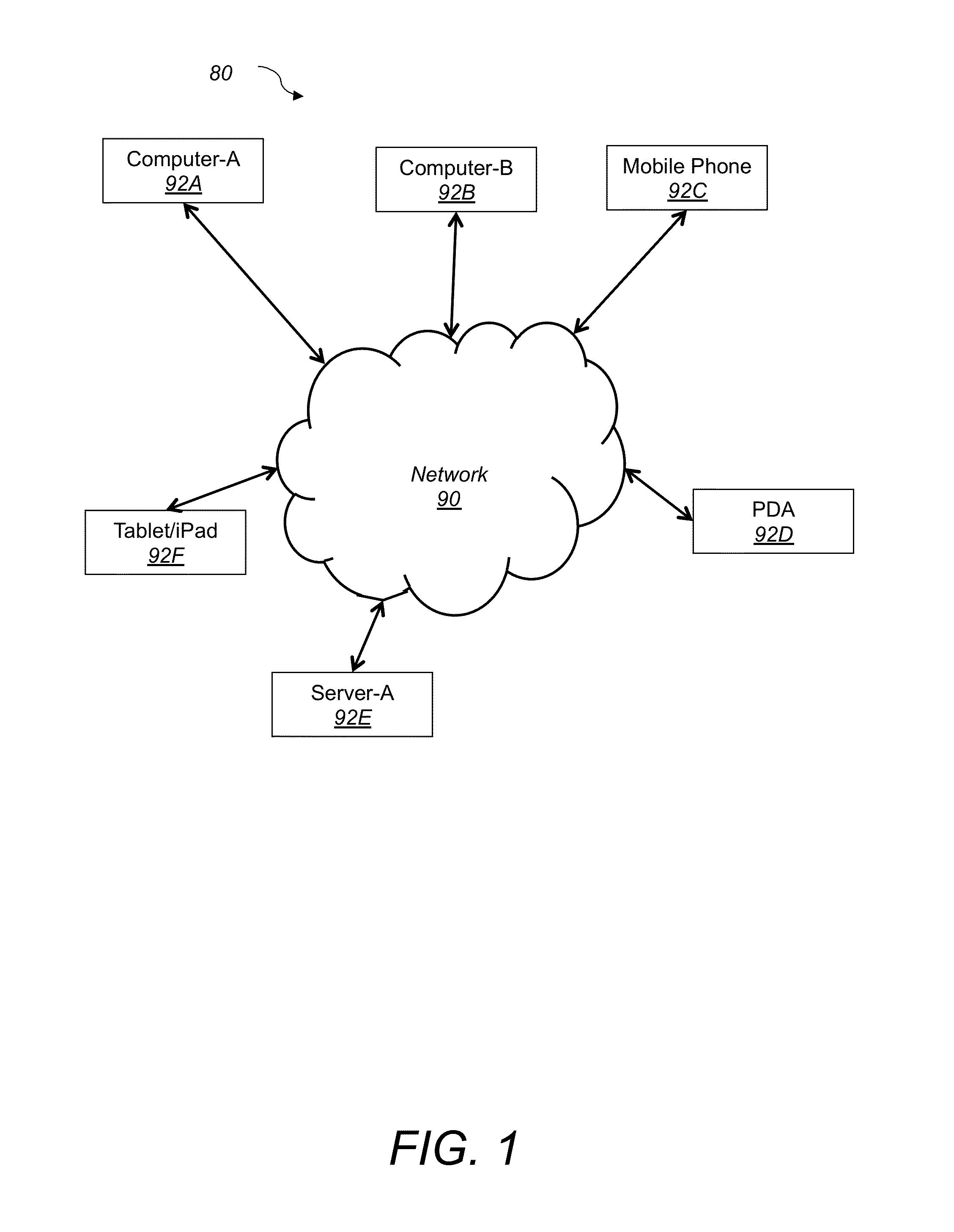
[0021]Referring to FIG. 1, a client-server system 80 for blocking data leakage, eavesdropping and spyware applications according to one embodiment of this invention includes computing devices 92A, 92B, mobile communication devices 92C, personal digital assistant devices 92D, Tablet / iPad™ device 92F and a server 92E. Devices 92A, 92B, 92C, 92D, 92F are connected to each other and to the server 92E via a network 90. In other embodiments, system 80 includes additional computing devices including personal computers...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com