A monitoring unit as well as method for predicting abnormal operation of time-triggered computer systems
a computer system and monitoring unit technology, applied in the direction of program control, non-redundant fault processing, program initiation/switch, etc., can solve problems such as program changes, errors that go undetected, and may already have been done a great deal of damage, and provide little or no protection against programming errors (including residual errors)
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
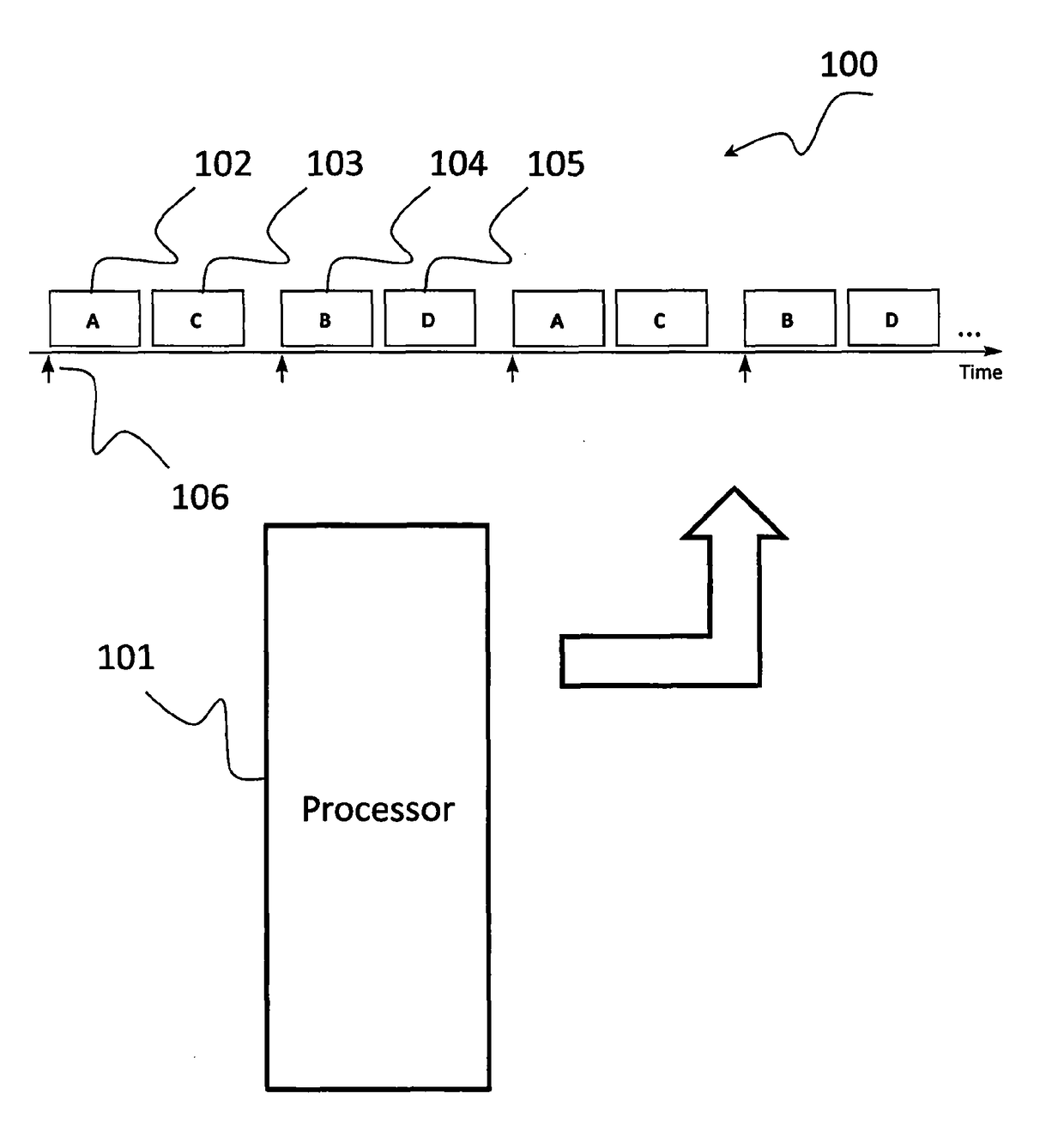
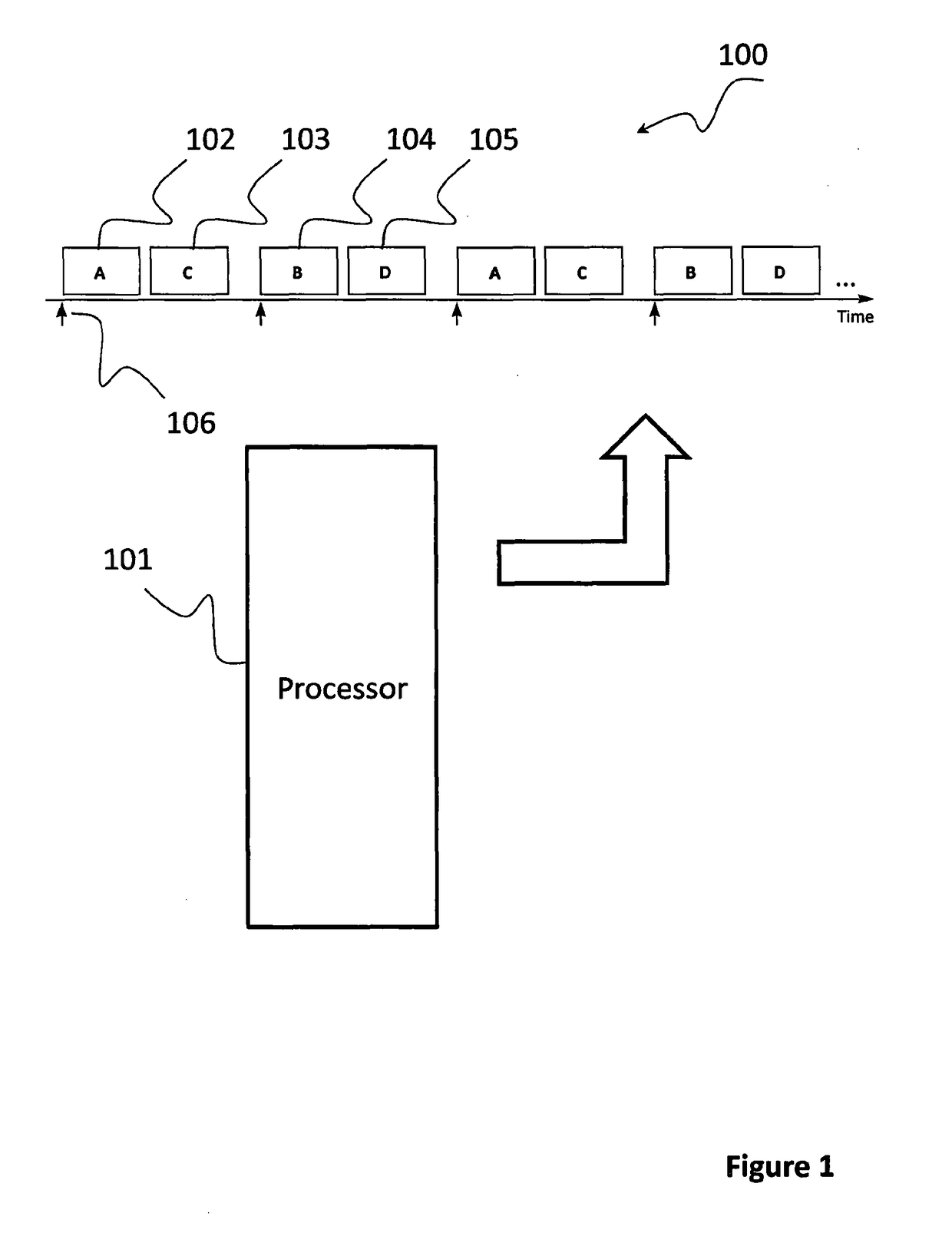
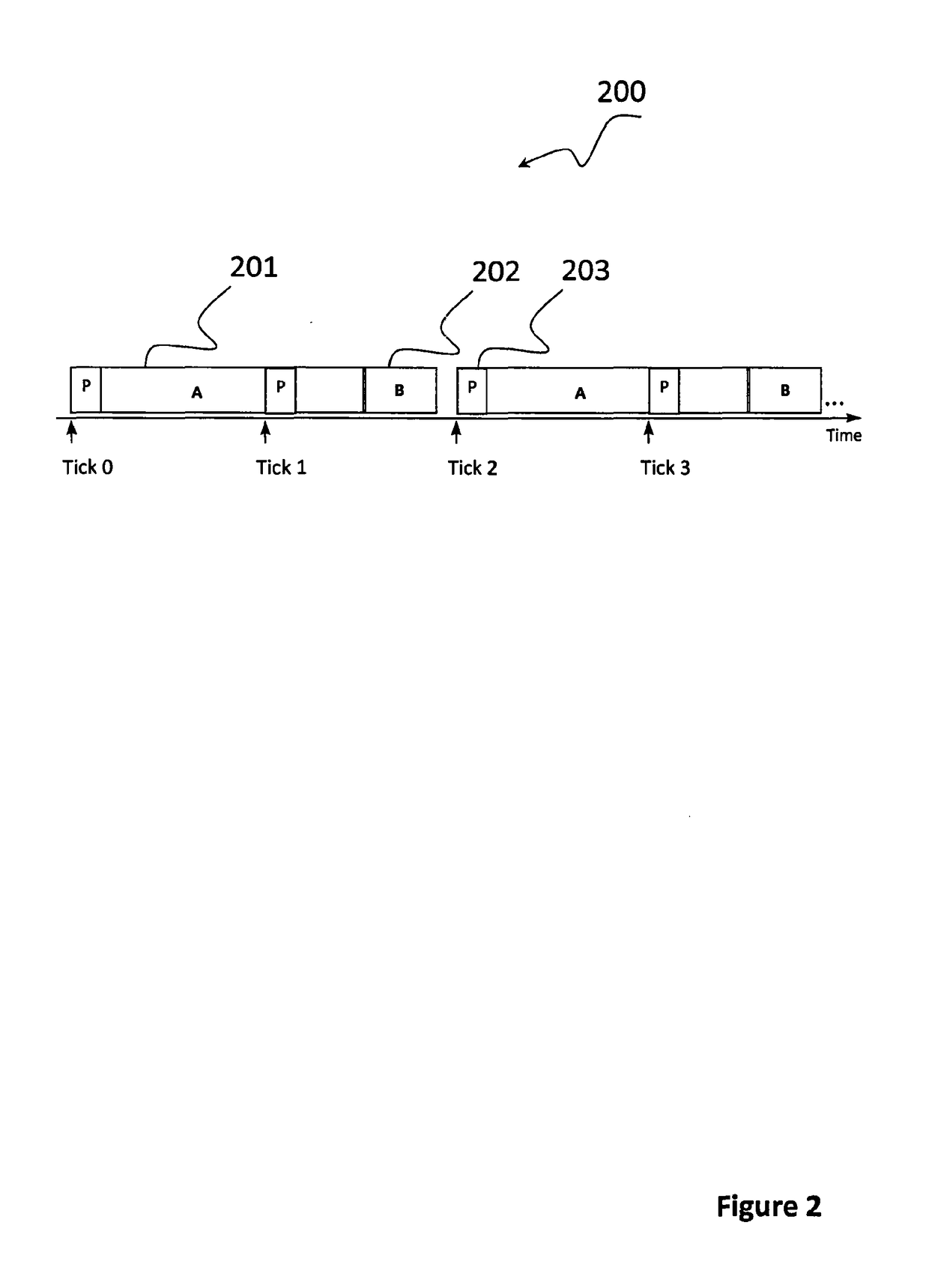
[0085]We begin by describing some existing techniques that are employed to create computer systems that execute tasks according to a predetermined task schedule. We then go on to describe how the present invention can be used to improve the reliability and security of such computer systems.
[0086]Computer systems that execute tasks according to a predetermined task schedule are sometimes referred to as time-triggered (TT) systems. TT systems are typically (but not necessarily) implemented using a design based on a single interrupt linked to the periodic overflow of a timer.
[0087]For example, FIG. 1 shows a TT computer system 100 made up of a Main Processor 101 that is executing a set of software tasks (in this case Task A 102, Task B 103, Task C 104 and Task D 105) according to a predetermined task schedule. In FIG. 1, the release of each sub-group of tasks (for example, Task A 102 and Task B 103) is triggered by what is usually called a “Timer Tick”106. The Timer Tick 106 is usually...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com