Decentralized automatic phone fraud risk management
a fraud risk management and decentralized technology, applied in the field of decentralized automatic phone fraud risk management, can solve the problems of fraudulent entities that also try to harm the system, fraudulent entities may make fake reports, and the inability to insert fake transactions into the blockchain, so as to improve the robustness of the system and increase the false positive detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
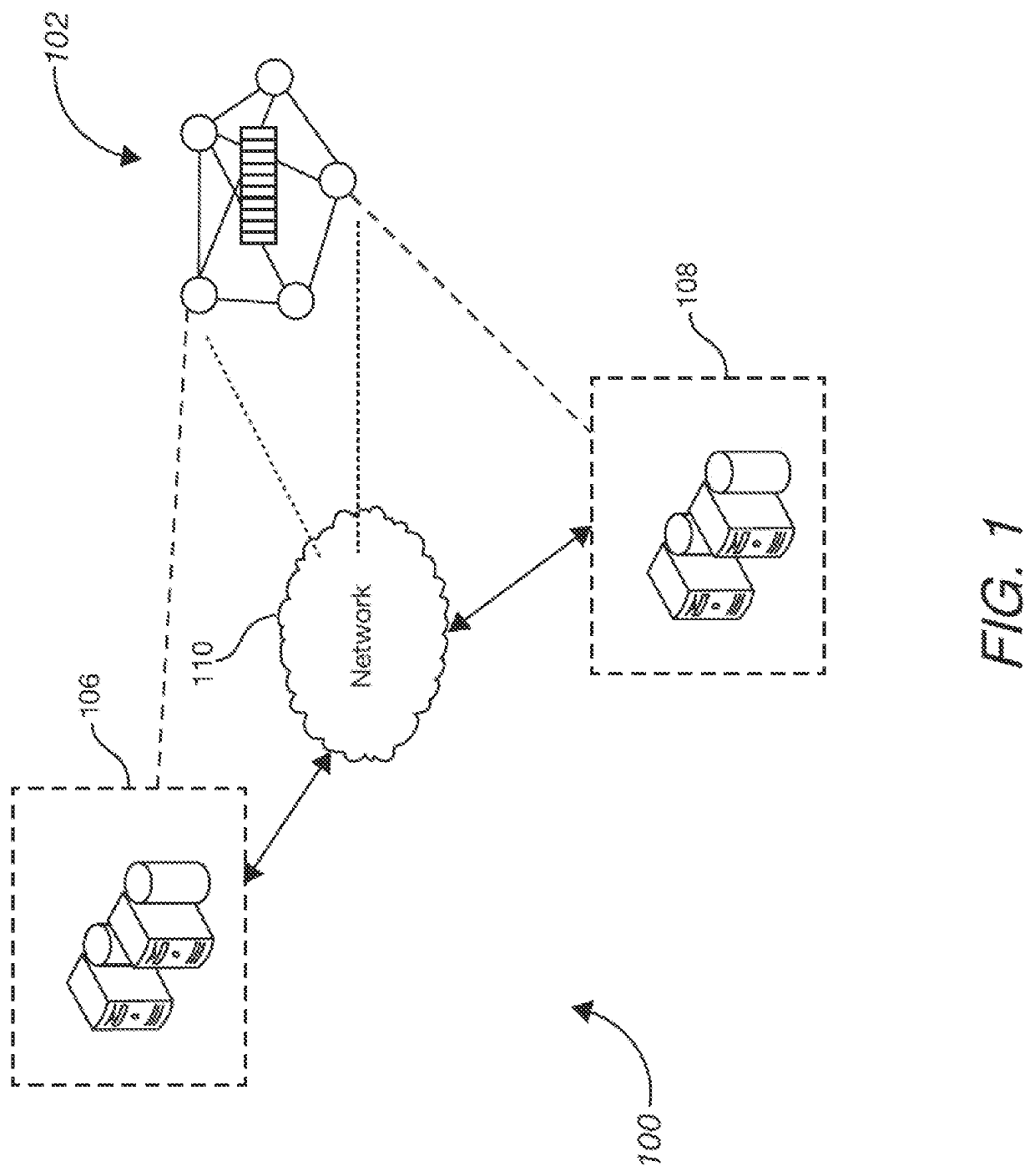
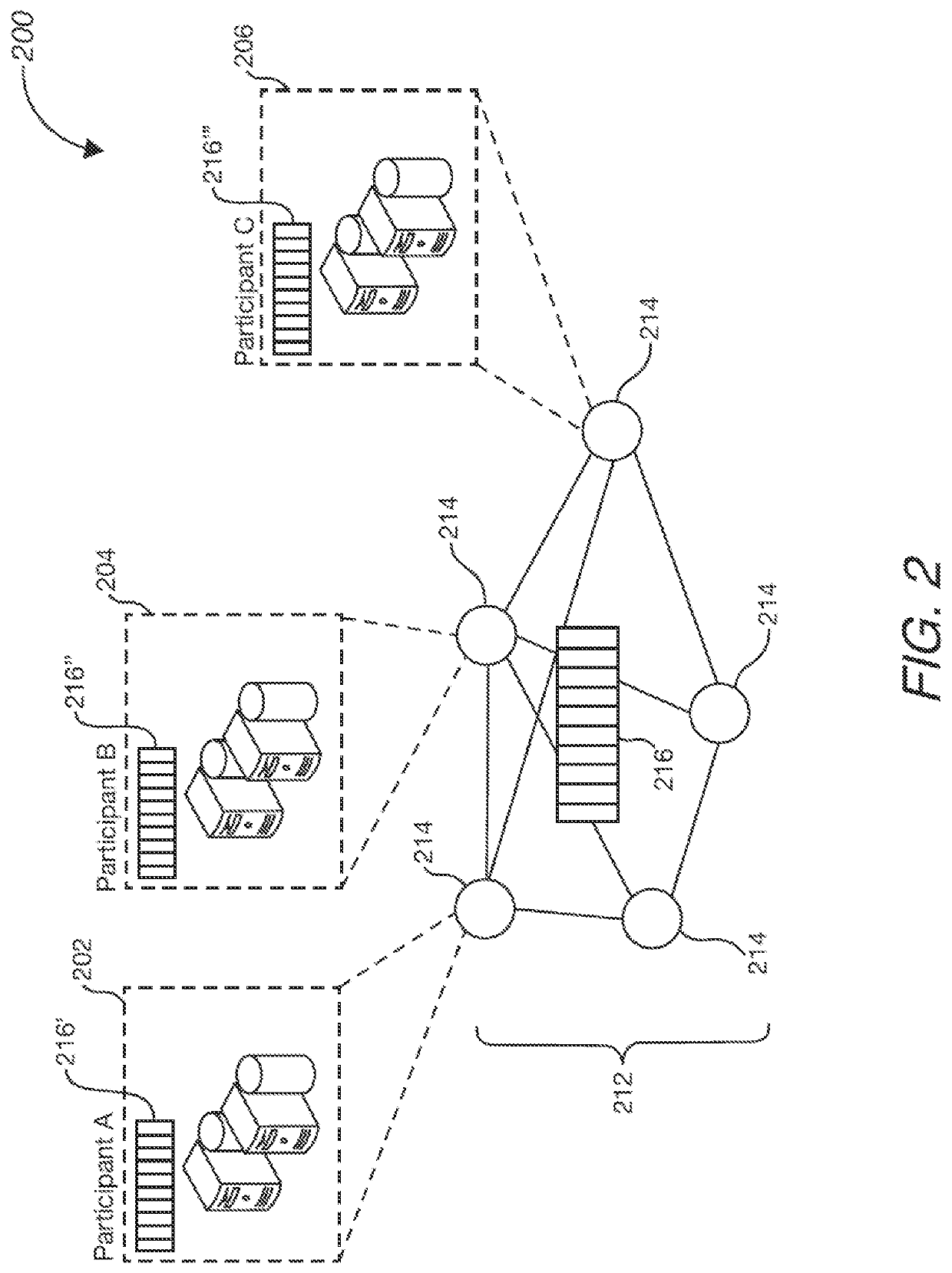
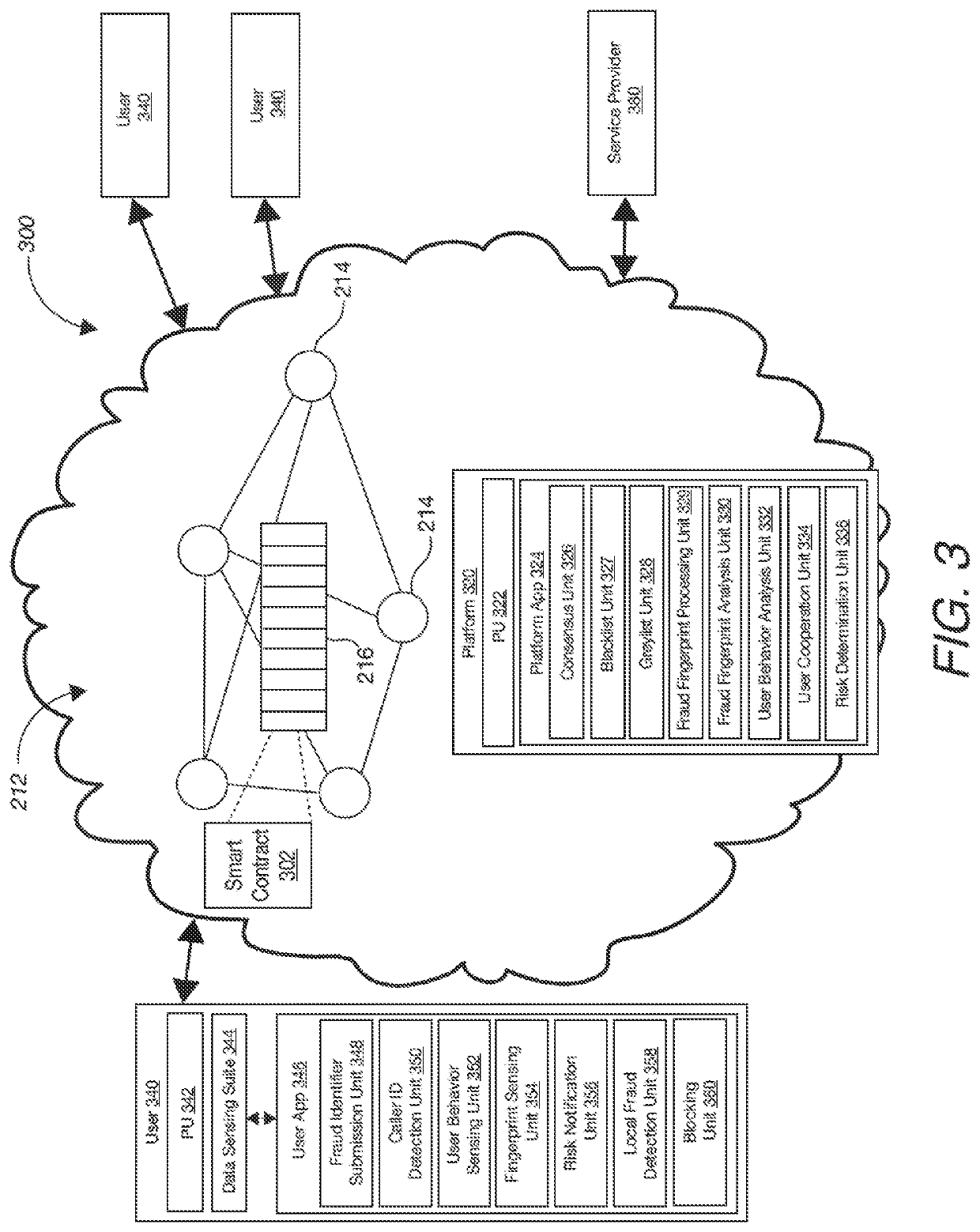
[0017]This specification describes technologies for managing phone fraud risk through a blockchain platform. These technologies generally involve user terminal devices providing information about one or more instances of phone fraud to a blockchain network. For example, the information includes a caller identification (“caller ID”) or a characteristic of a phone fraud event (“fraud fingerprints”), collectively referred to as “phone fraud identifiers.” The phone fraud identifiers are each stored in the blockchain database as a block or a chain of blocks. The stored phone fraud identifiers are further classified into categories or lists of phone fraud identifiers. When a user device detects a caller ID or a fingerprint of an incoming phone event, the detected caller ID or fingerprint is compared with lists of fraud identifiers to assess whether the incoming phone event involves a phone fraud risk.
[0018]To provide further context for embodiments of this specification, and as introduced...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com