Protection method of PHS mobile communication PIM card authentication data
A mobile communication and authentication technology, applied in the field of mobile communication, can solve the problems of low writing authority, easy rewriting and destruction of authentication data, etc., and achieve the effects of reducing the number of maintenance, facilitating promotion, and increasing robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049]The method of the present invention is further developed in conjunction with the accompanying drawings and embodiments. First, the main basic points for explaining the inventive method are as follows:
[0050] (1) CRC check:
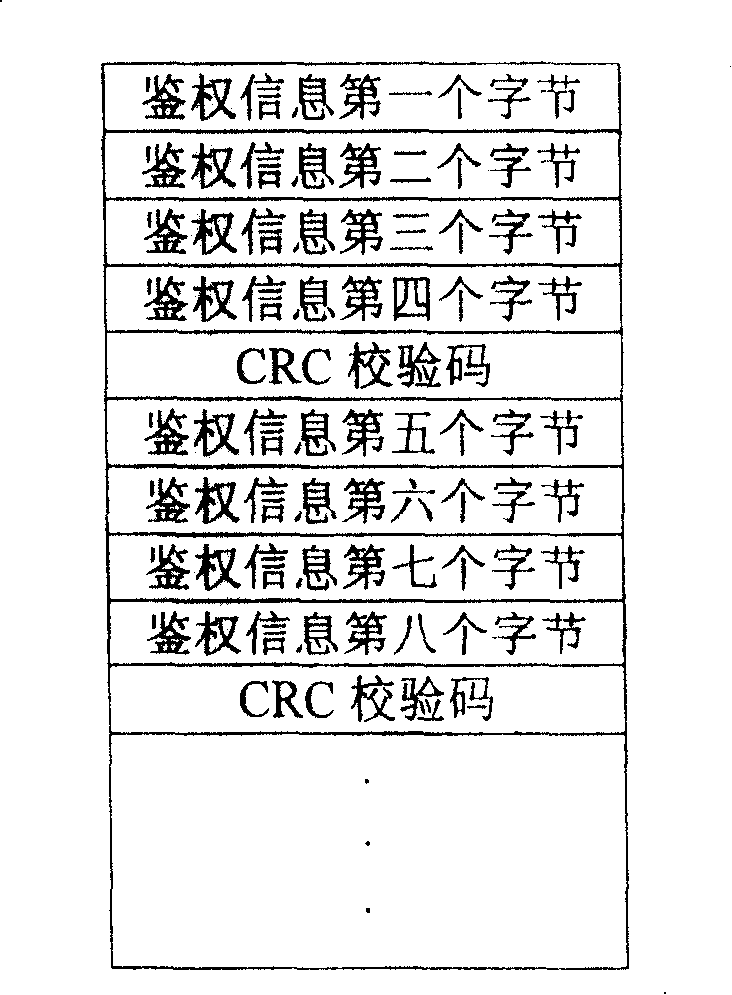
[0051] ① Write PIM ID and authentication data, where the format of authentication data is as follows figure 1 , write the authentication data into the file. Since this embodiment uses a 32-bit CRC check, the data to be written is grouped by 4 bytes. If it is less than 4 bytes, it will be filled with "0xff", and finally , according to the verification code generation formula "f(x)=
[0052] X^32+X^26+X^23+X^22+X^16+X^12+X^11+X^10+X^8+X^7+X^5+X^4+X^ 2+X^1+X^0" to get the original check digit and put it in the last byte of each group. The method of writing PIM ID data is the same as the method of writing authentication data.
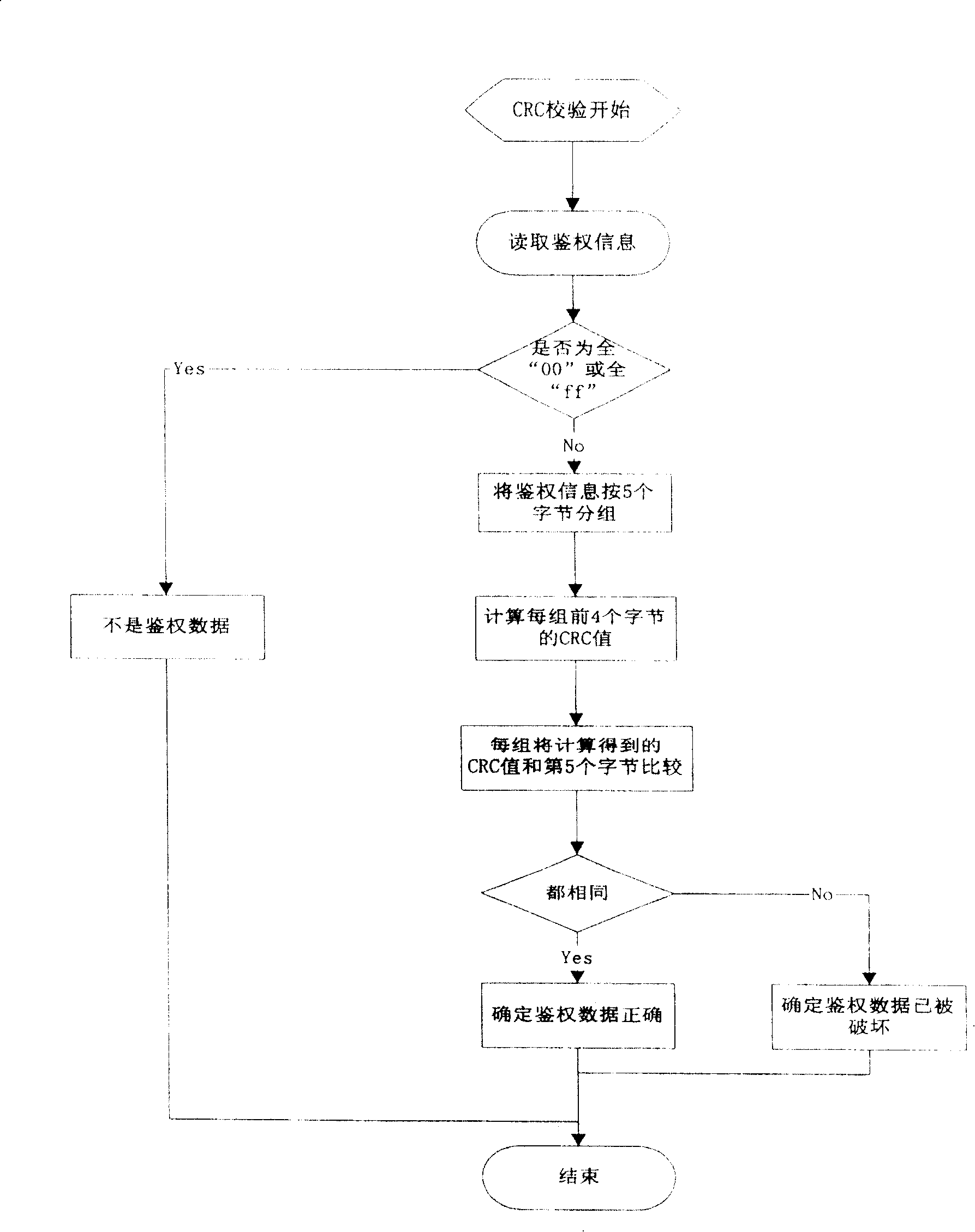
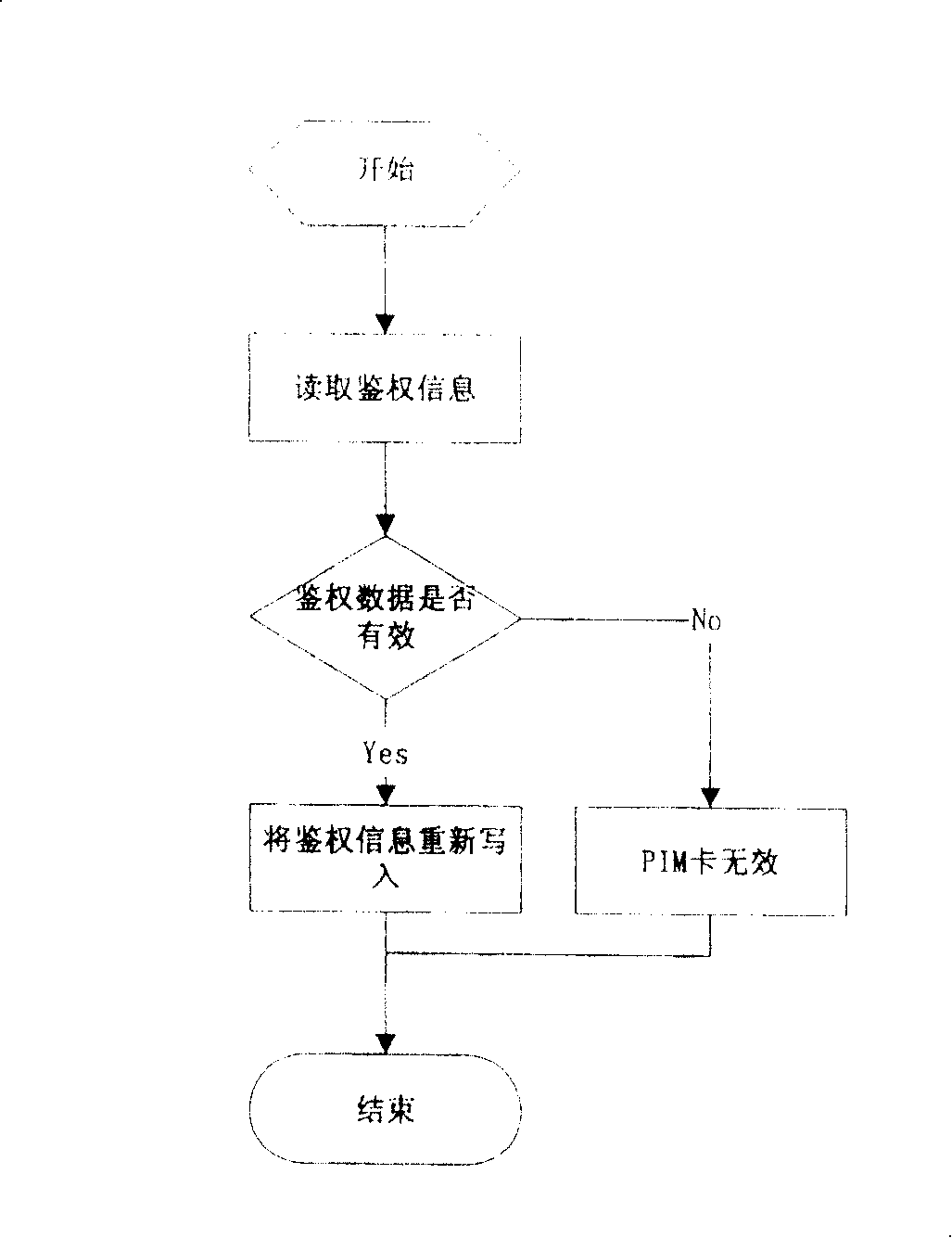
[0053] ②PIM ID and authentication data verification, the process is as follows figure 2 As shown, the authentication dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com