Software-action description, fetching and controlling method with virtual address space characteristic
A technology of address space and virtual space, which is applied in the field of software behavior anomaly detection and protection based on program behavior, can solve the problems of high false alarm rate, missed detection, false detection, and time-consuming problems, so as to improve accuracy and efficiency, The effect of improving detection accuracy and improving recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The technical solutions of the present invention will be further described below in conjunction with specific embodiments.
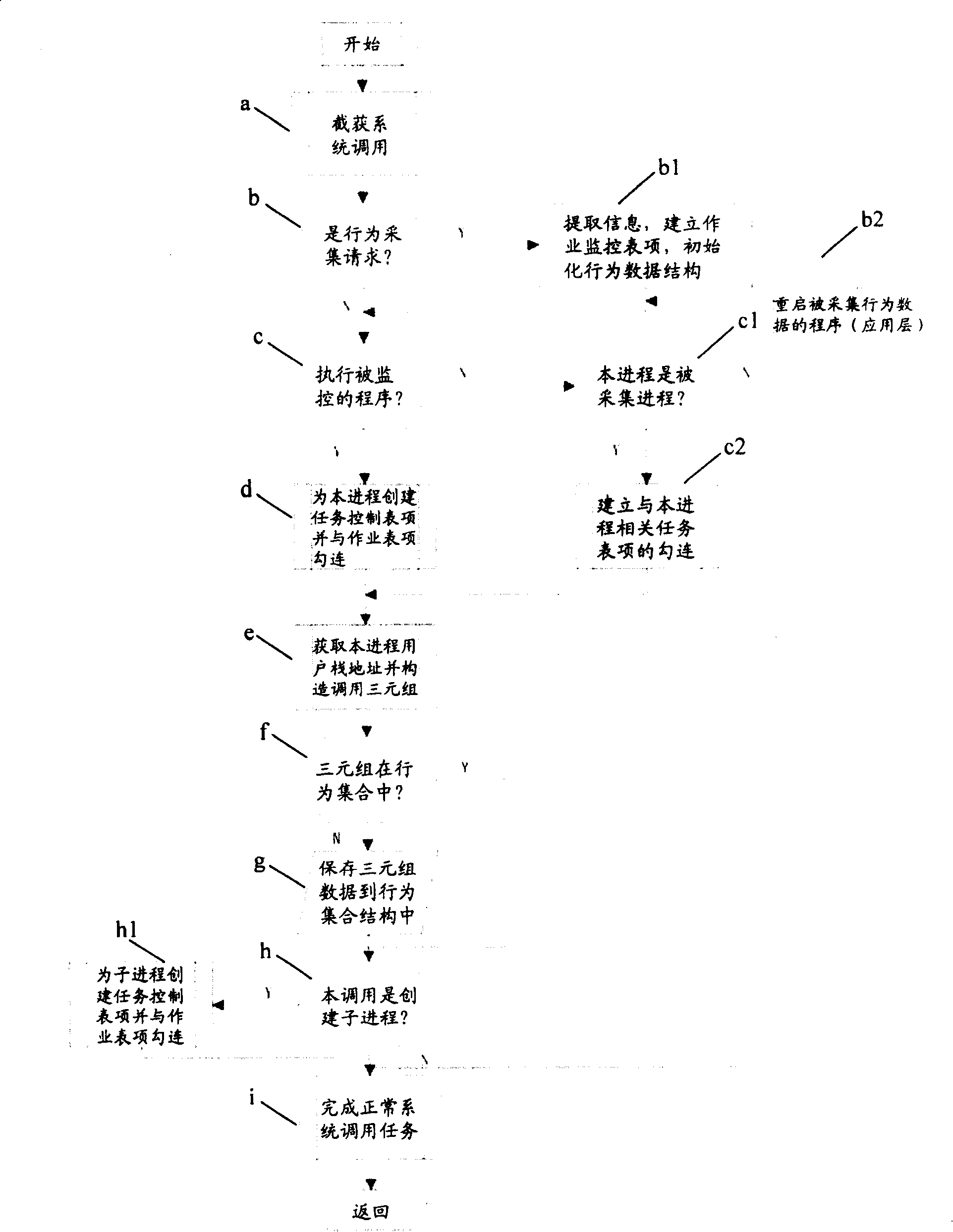
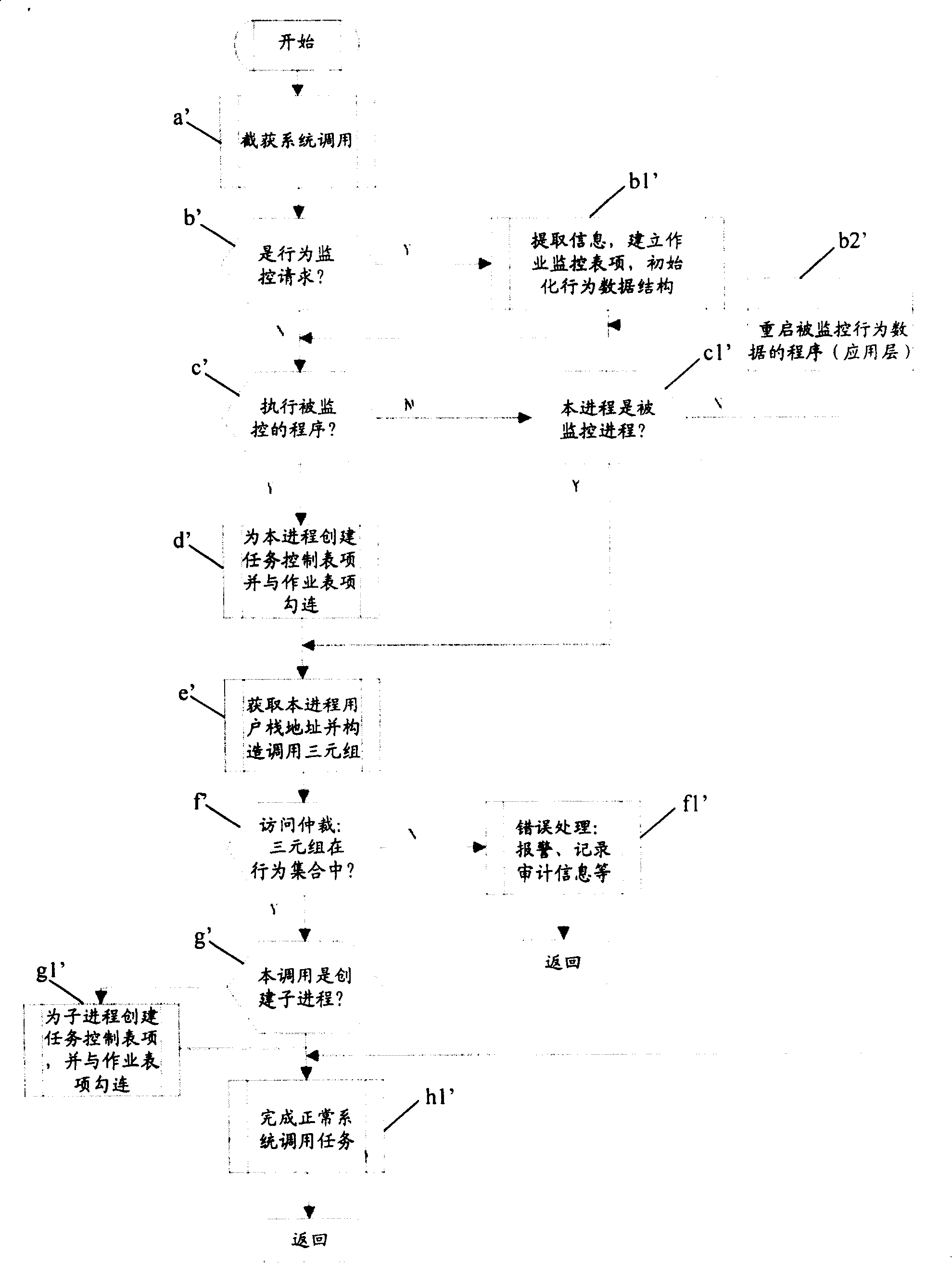
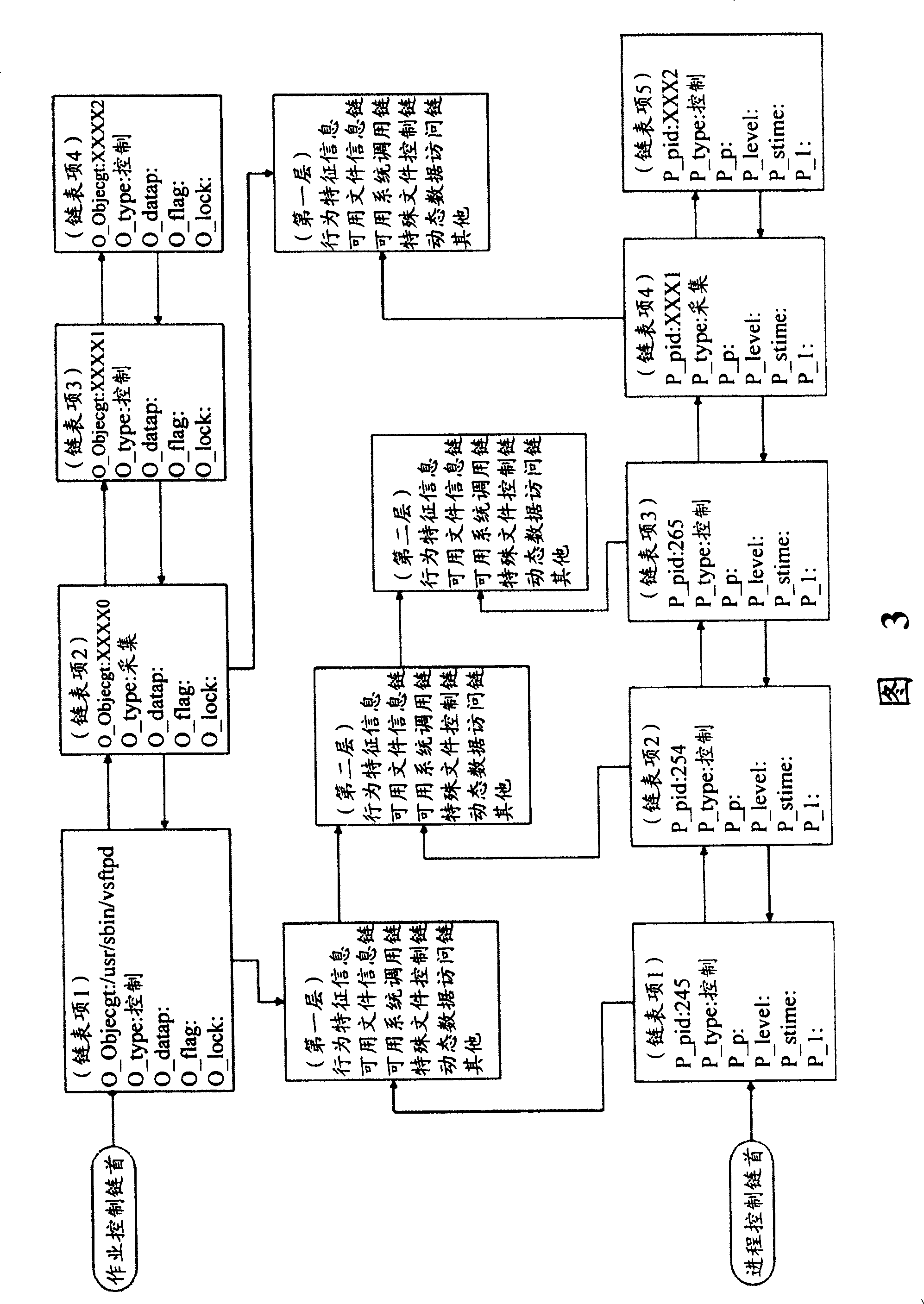
[0058] First, the present invention provides a detection and protection method for abnormal software behavior, including: acquiring a software behavior and its address attribute and establishing a corresponding characteristic data set; and applying the established characteristic data set to detect and protect software abnormal behavior, wherein, The feature data set has a virtual space address attribute. In the method of the present invention, the description of the software line with the address attribute can be provided, wherein the basic elements are as follows:
[0059] 1) Take system calls as the basic elements of software behavior. System calls refer to various service interfaces provided by the operating system to the application layer software to complete specific tasks that can only be completed by the system for the application software...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com