Electronic data evidence obtaining method and system for computer
An electronic data and computer technology, applied in the fields of information security and computer systems, can solve problems such as restricting the operability of computer forensics technology, and achieve the effect of improving usability and reliability, easy implementation, and high reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
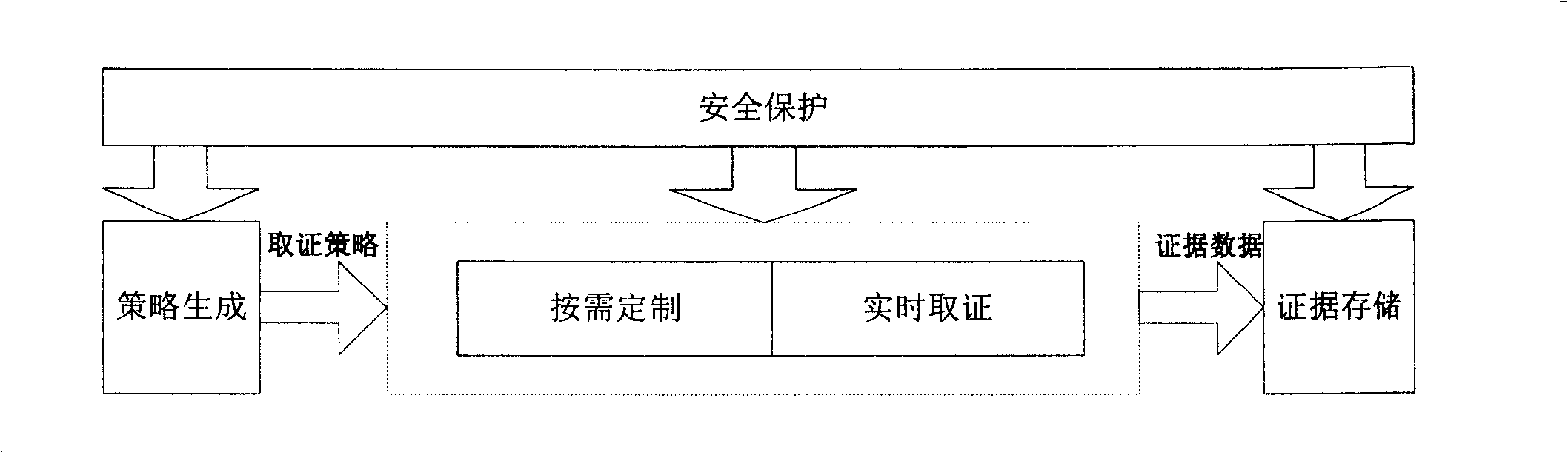
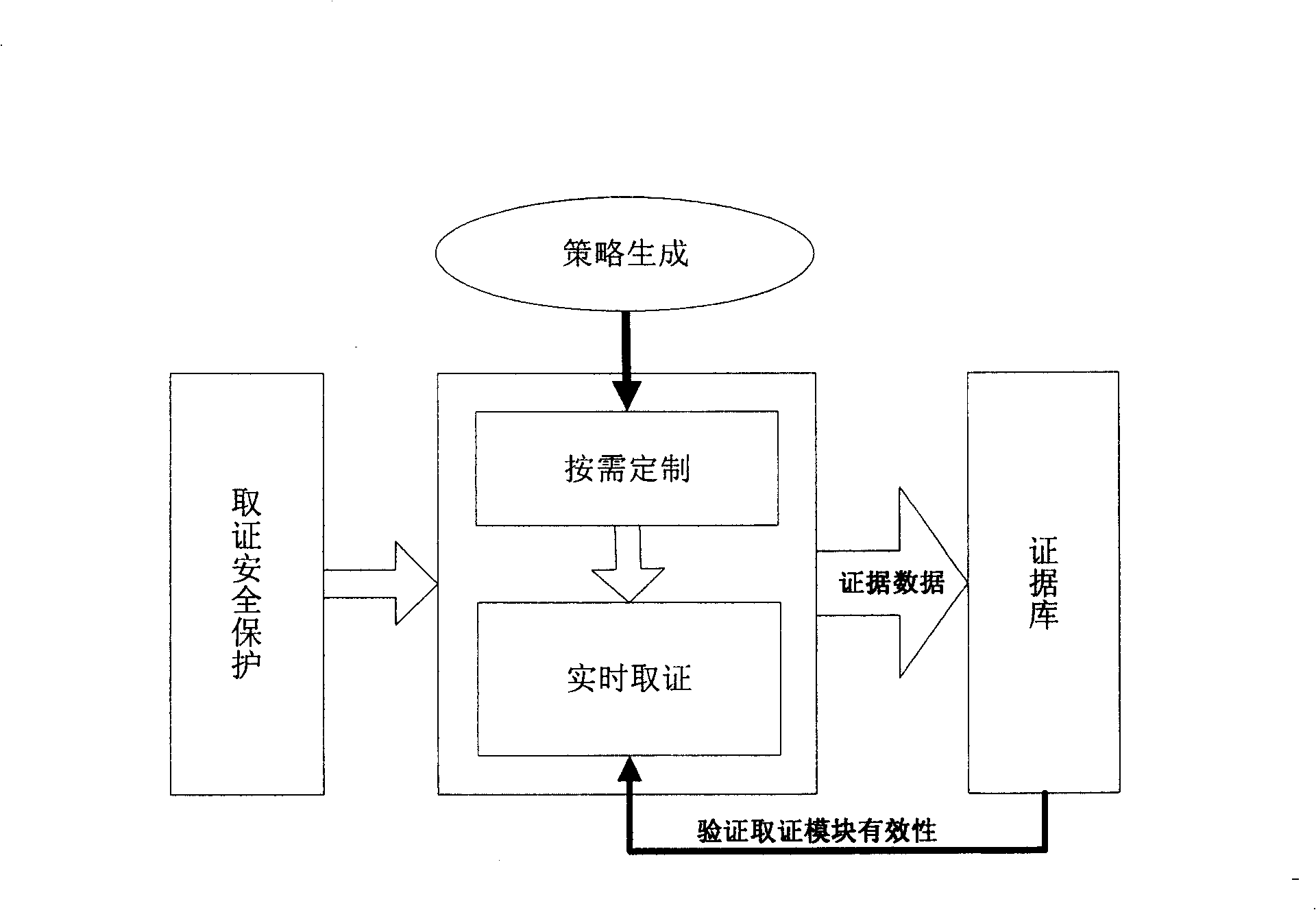
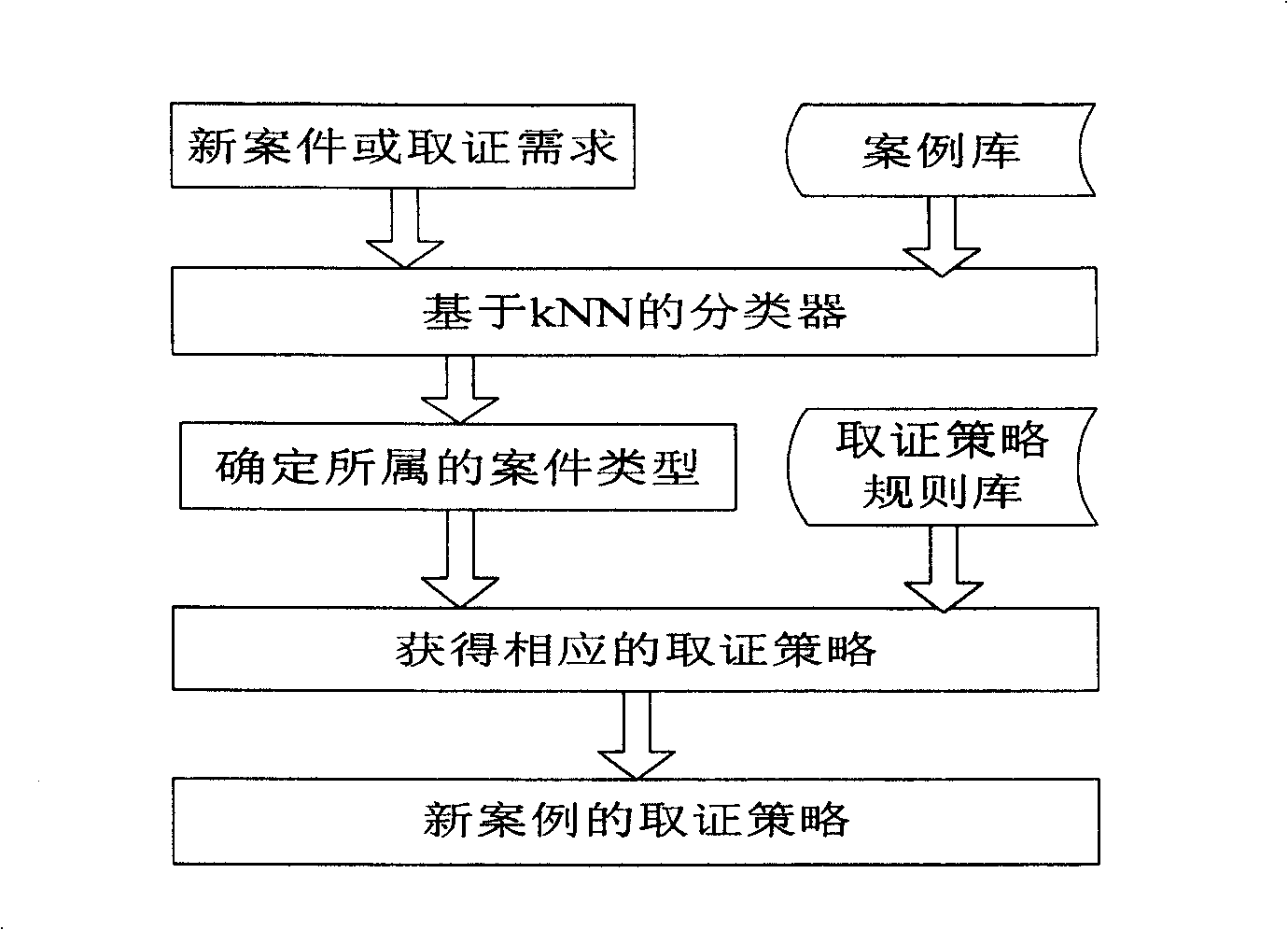
[0032] Based on the 5 processes for implementing the forensics method, we decided to implement each process as a module of the forensics system. The forensic method and system of the present invention will be described in detail below with reference to the accompanying drawings.
[0033] like figure 2As shown, this forensics system mainly includes five parts: strategy generation module, on-demand customization module, real-time forensics module, evidence base module, security protection module, each module cooperates to complete the real-time forensics, dynamic configuration, security protection design goals of the forensics system . Among them, the strategy generation module adopts the data mining method to determine the evidence collection strategy of the current case. The on-demand customization module takes the current forensics strategy as input, generates the current forensic scope parameters, and dynamically updates the forensic scope of the real-time forensics modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com