Data transparency protected safety read-write system and method
A technology of transparent protection and data protection, applied in electronic digital data processing, computer security devices, protection of internal/peripheral computer components, etc., can solve the problems of intercepting I/O instructions, occupation, and inability to completely prevent viruses and Trojan programs. , to achieve the effect of high availability and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
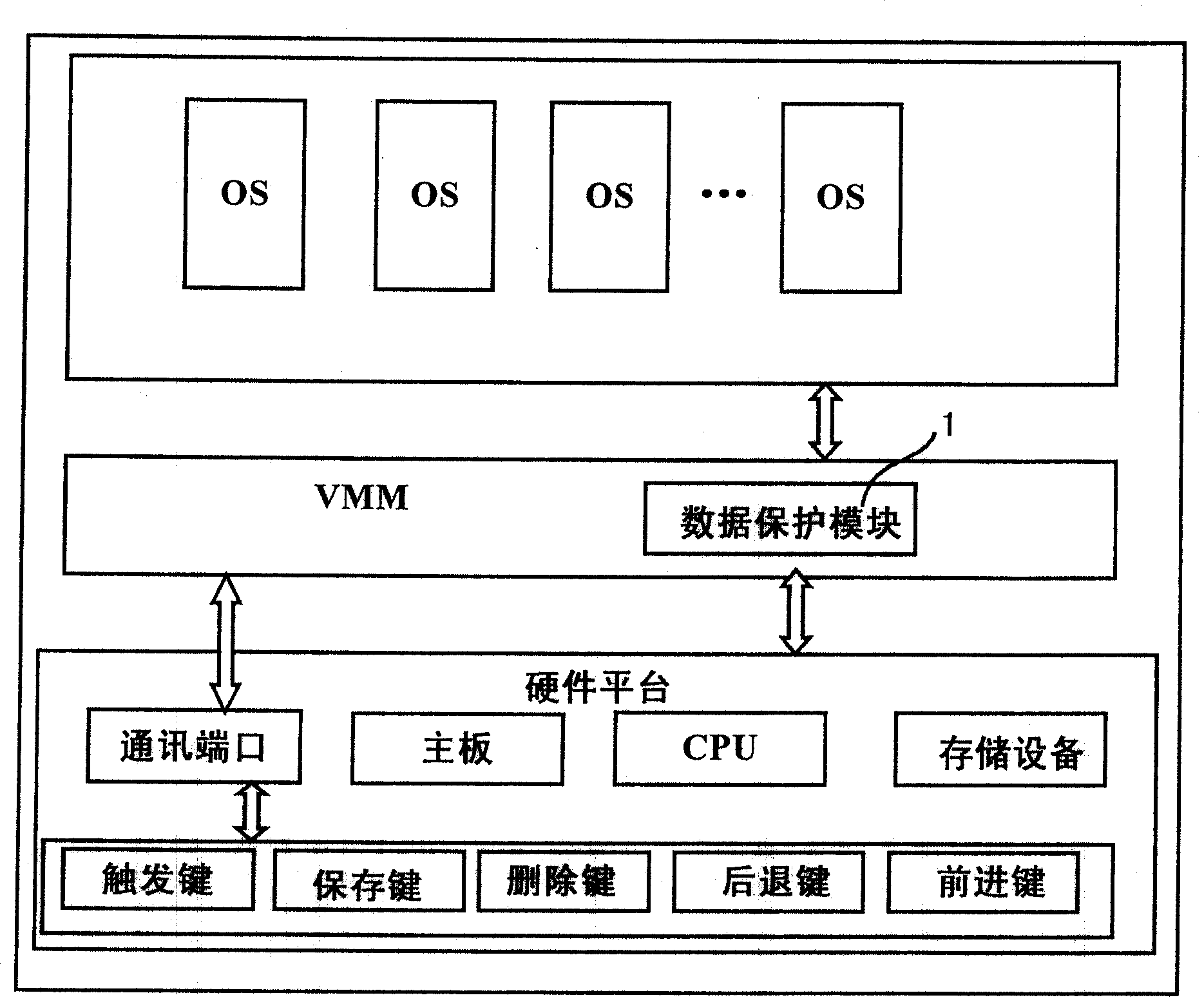
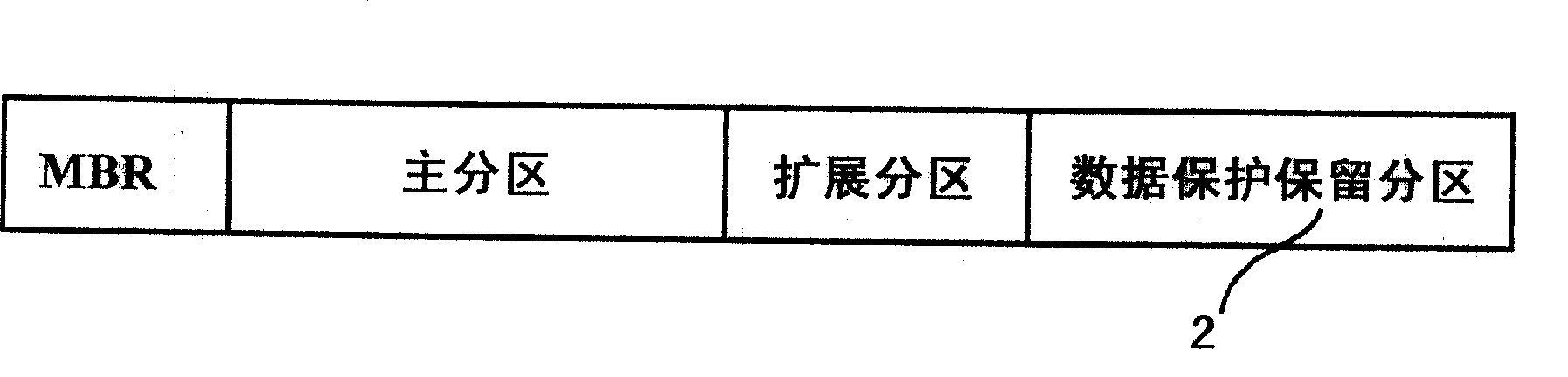
[0061] Attached below Figure 1~5 The system and method for transparent protection of storage device data of the present invention are further described in detail.
[0062] The present invention is particularly described in terms of a computer data transparent protection system and method, but the present invention is equally applicable to any device other than the above-mentioned storage device, such as the case of a storage device of a mobile communication device.
[0063] The core point of the present invention is to run a virtual machine monitor (Virtual Machine Monitor, VMM) earlier on the hardware platform, reside and run the data protection module 1 in the virtual machine monitor, and the operating system runs on the virtual machine monitor (VMM) , the data protection module 1, with the support of the CPU, intercepts all the I / O instructions of the operating system itself and programs running on the operating system to access the computer storage device, and redirects t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com