Verification implementation method and device
An implementation method and a technology for authentication information, which are applied in the directions of selecting devices, user identity/authority verification, radio/induction link selection and arrangement, etc., and can solve problems such as poor authentication security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
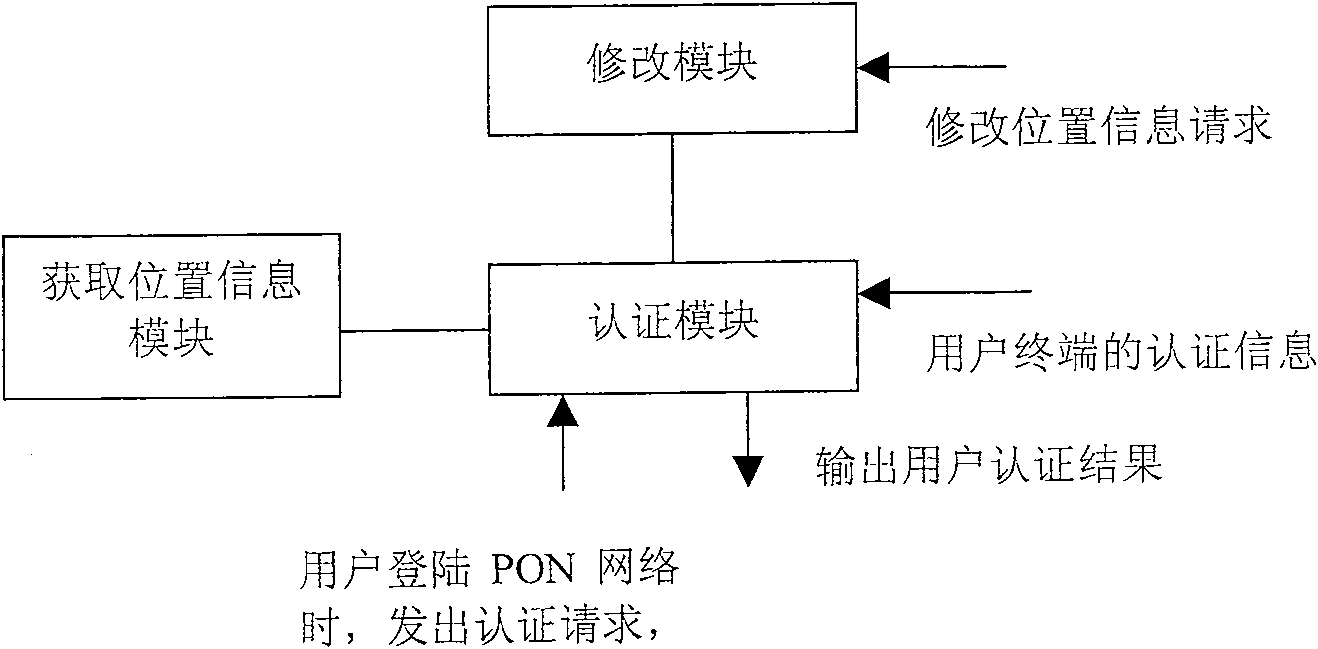
[0045] The core of the method of the present invention is: acquiring the location information of the user terminal, and authenticating the user terminal according to the location information and the predetermined location information corresponding to the user terminal.
[0046] The technical solution provided by the present invention will be further described below based on the core idea of the present invention.
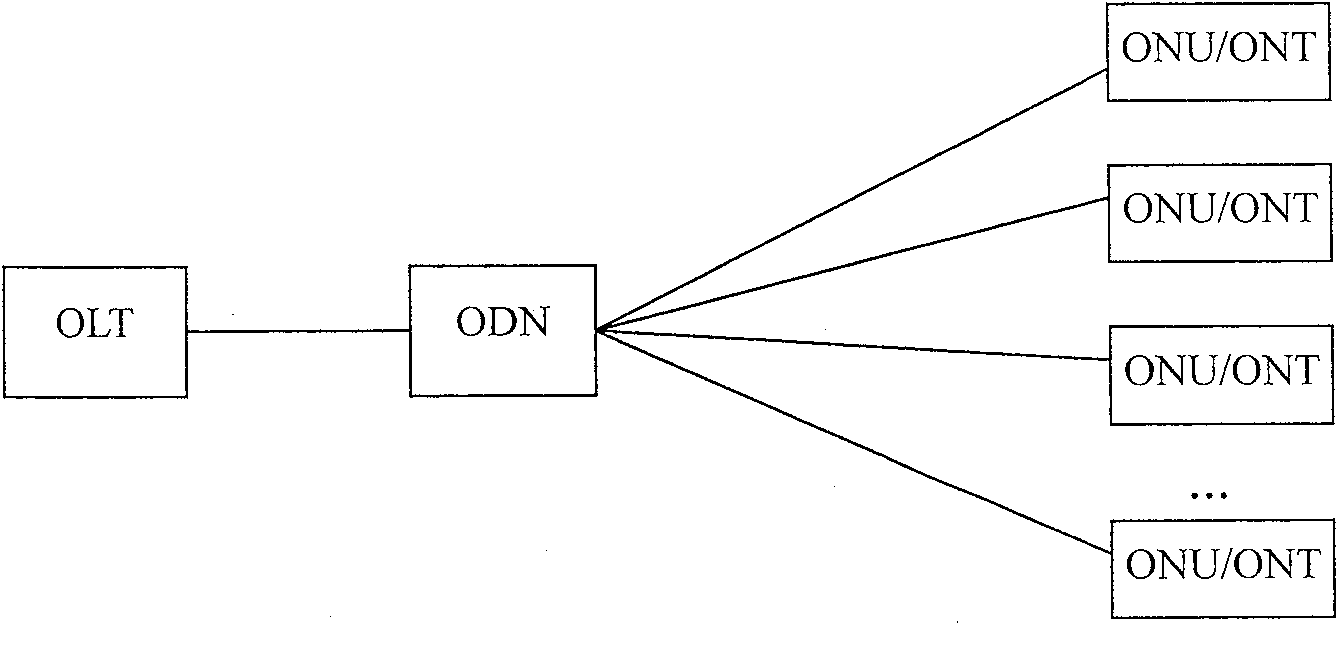
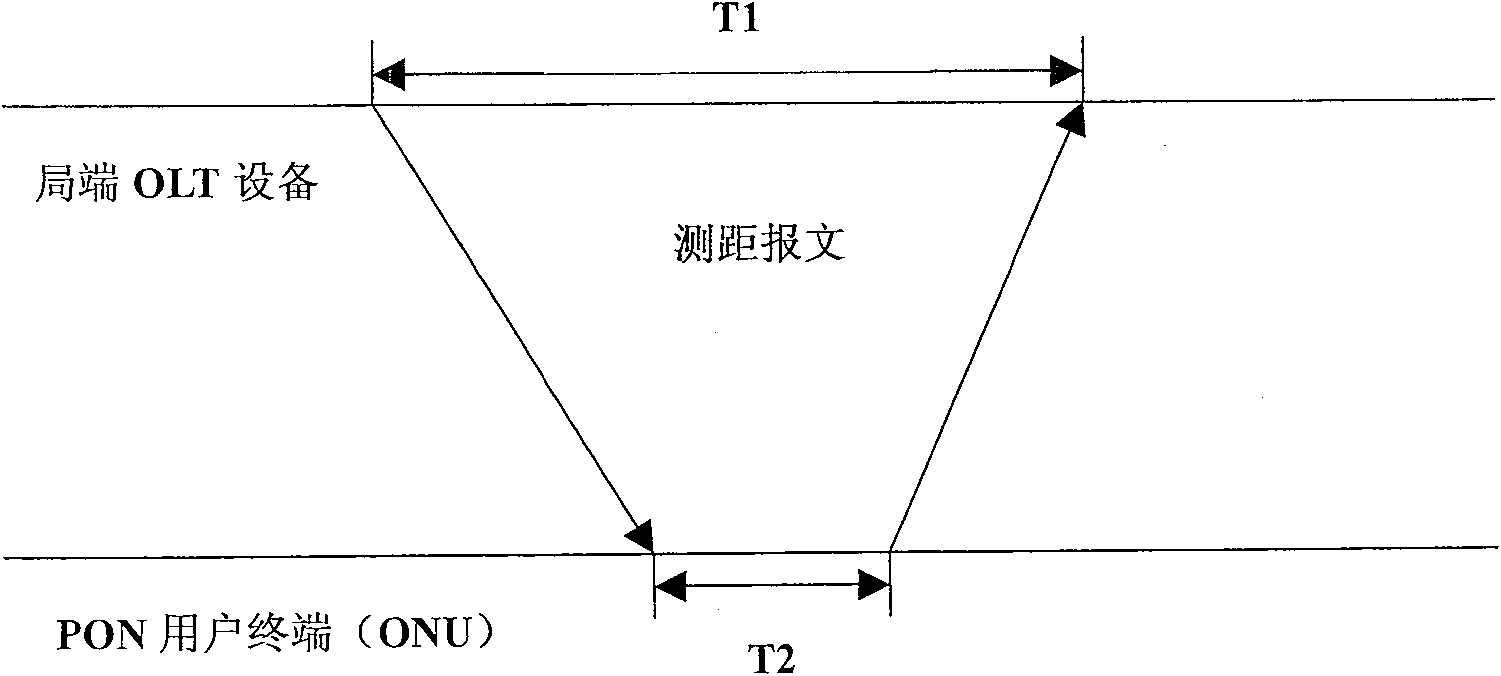
[0047] Since the PON technology uses TDMA (Time Division Multiple Access) technology in the uplink, in order to make full use of the bandwidth, various PON technologies have applied the measurement distance technology to compensate for the distance difference between each PON user terminal and the central office OLT equipment. The realization principle of the distance measurement function in PON is attached figure 2 shown.
[0048] exist figure 2 Among them, the difference between T1 and T2 is the RTT (turnback time) value of the user terminal, and the RTT val...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com