Method for logining BIOS based on fingerprint verification
A technology of fingerprint authentication and login method, which is applied in the field of BIOS login based on fingerprint authentication, can solve the problems of inability to fundamentally solve the problem, increase the user's memory burden, and the system cannot be protected, and achieves improved security and strong concealment. , the effect of reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
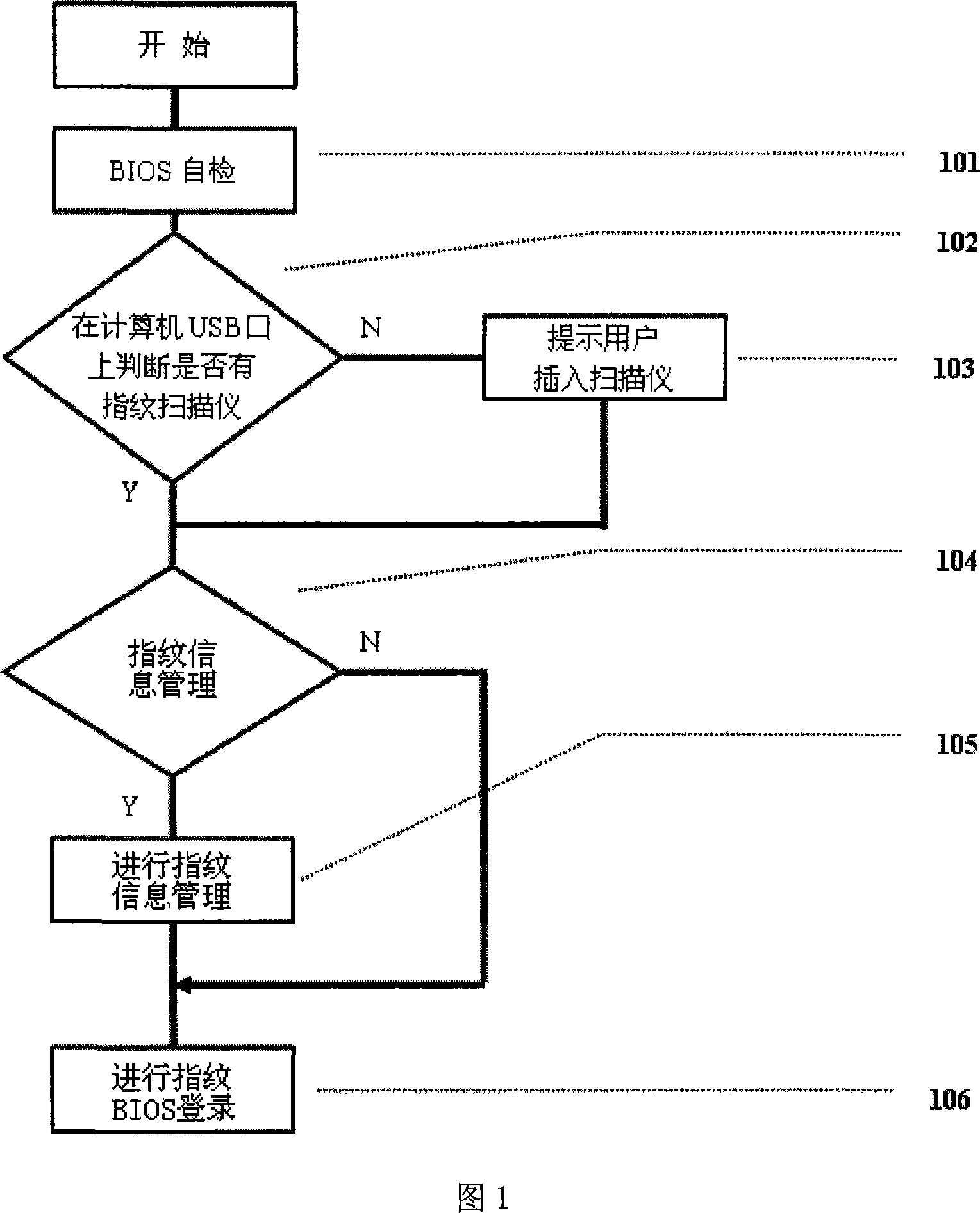
[0035] In order to make the purpose, technical solutions and advantages of the present invention clearer, the present invention will be described in further detail below with reference to the accompanying drawings and examples:
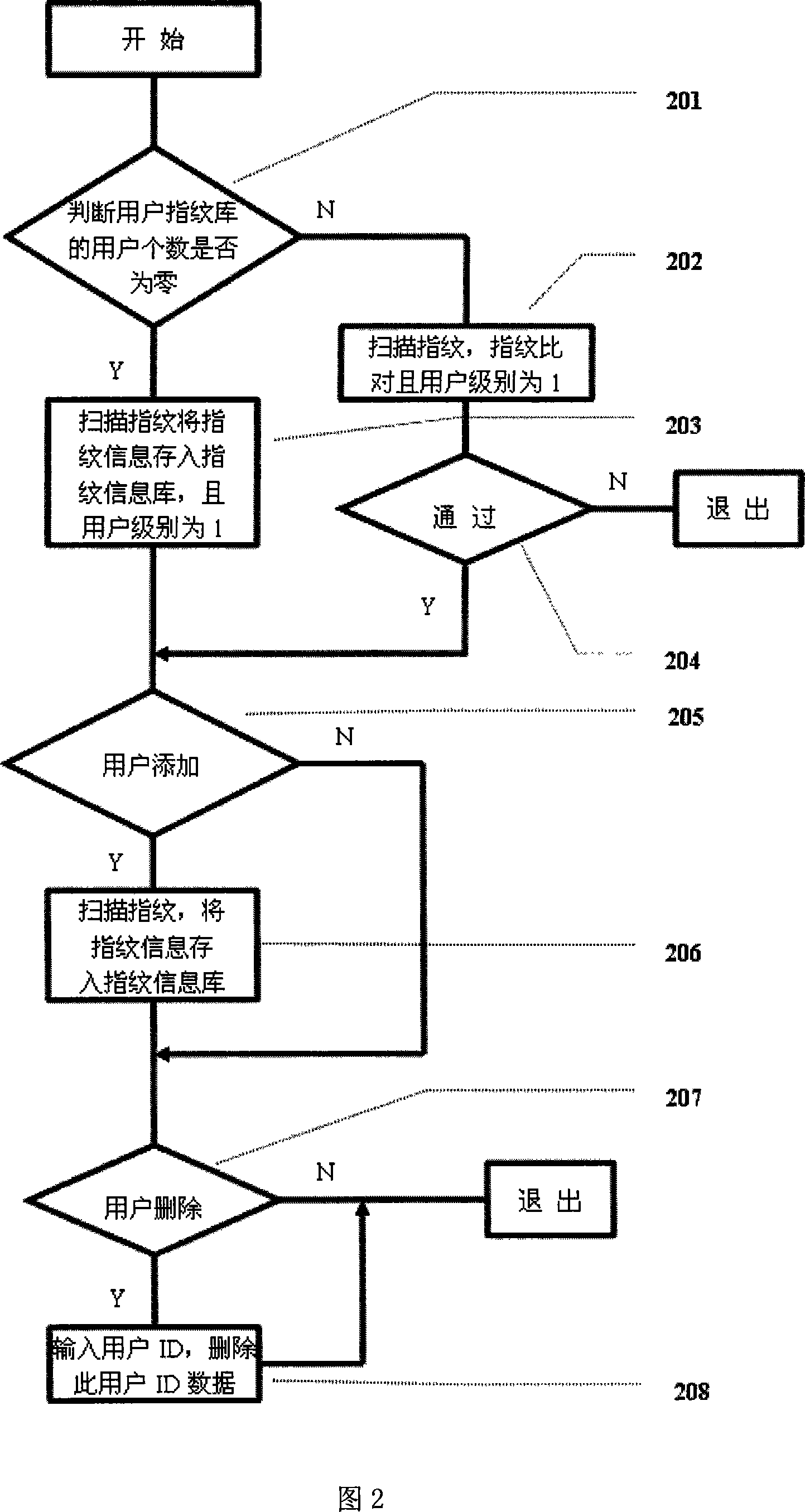
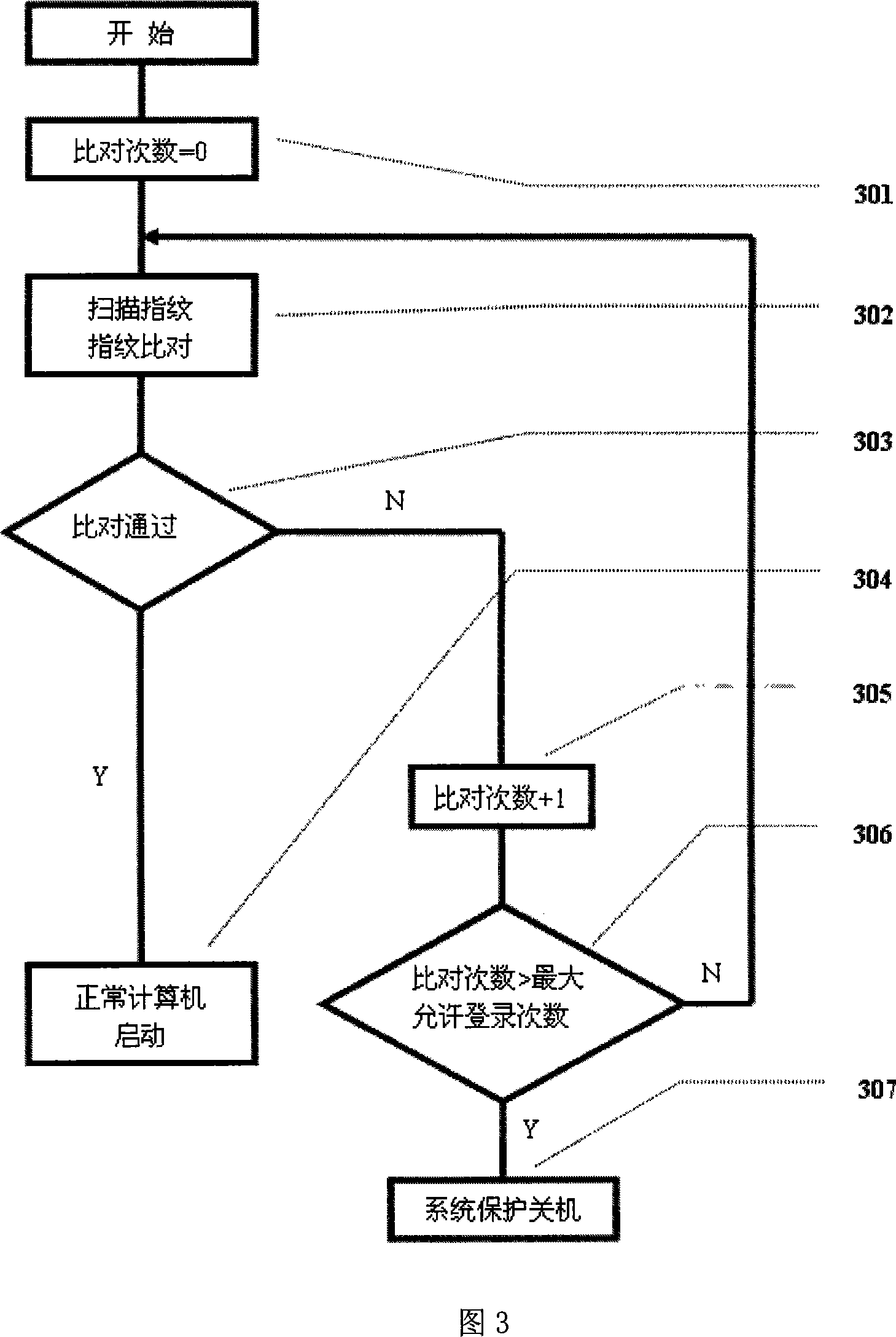
[0036] The idea of the present invention is: fingerprint recognition and fingerprint image collection are both carried out in the BIOS. In order to save users' expenses, fingerprint identification and image acquisition do not use embedded system solutions. Insert the fingerprint authentication module complying with the module format of the BIOS into the BIOS, start the computer, and when the BIOS self-check is completed, the computer automatically invokes the fingerprint authentication module, which completes the management of fingerprint information and the fingerprint authentication login work of the BIOS. Users can choose fingerprint information management and fingerprint authentication. If fingerprint authentication is selected, the fingerprint...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com