Systems and methods for verifying trust of executable files
A technology for executing files and credibility, which is applied in transmission systems, digital transmission systems, electrical components, etc., and can solve problems such as document destruction of integrity verification, invalidation of initial credibility verification estimates, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0010] Overview
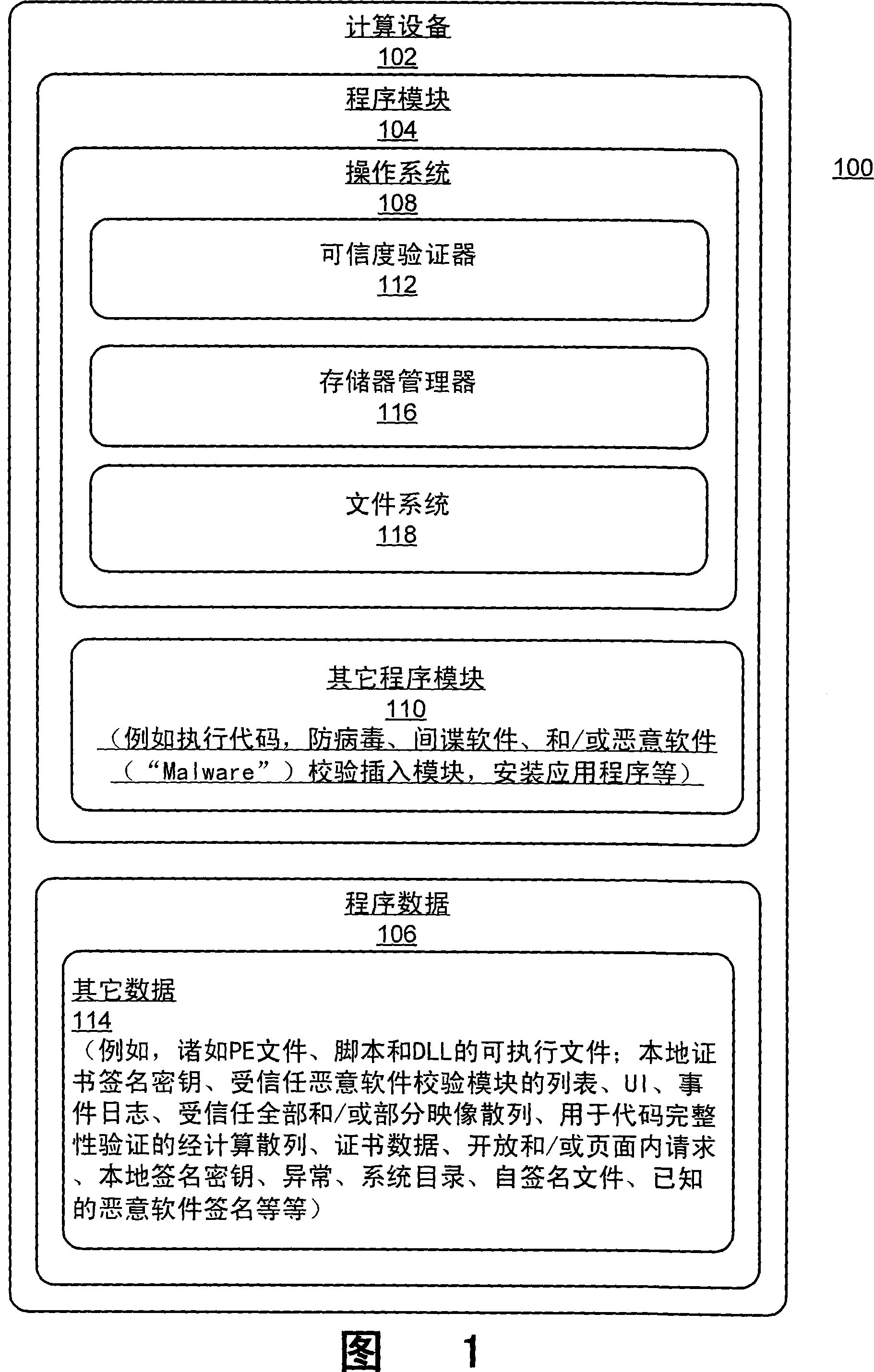
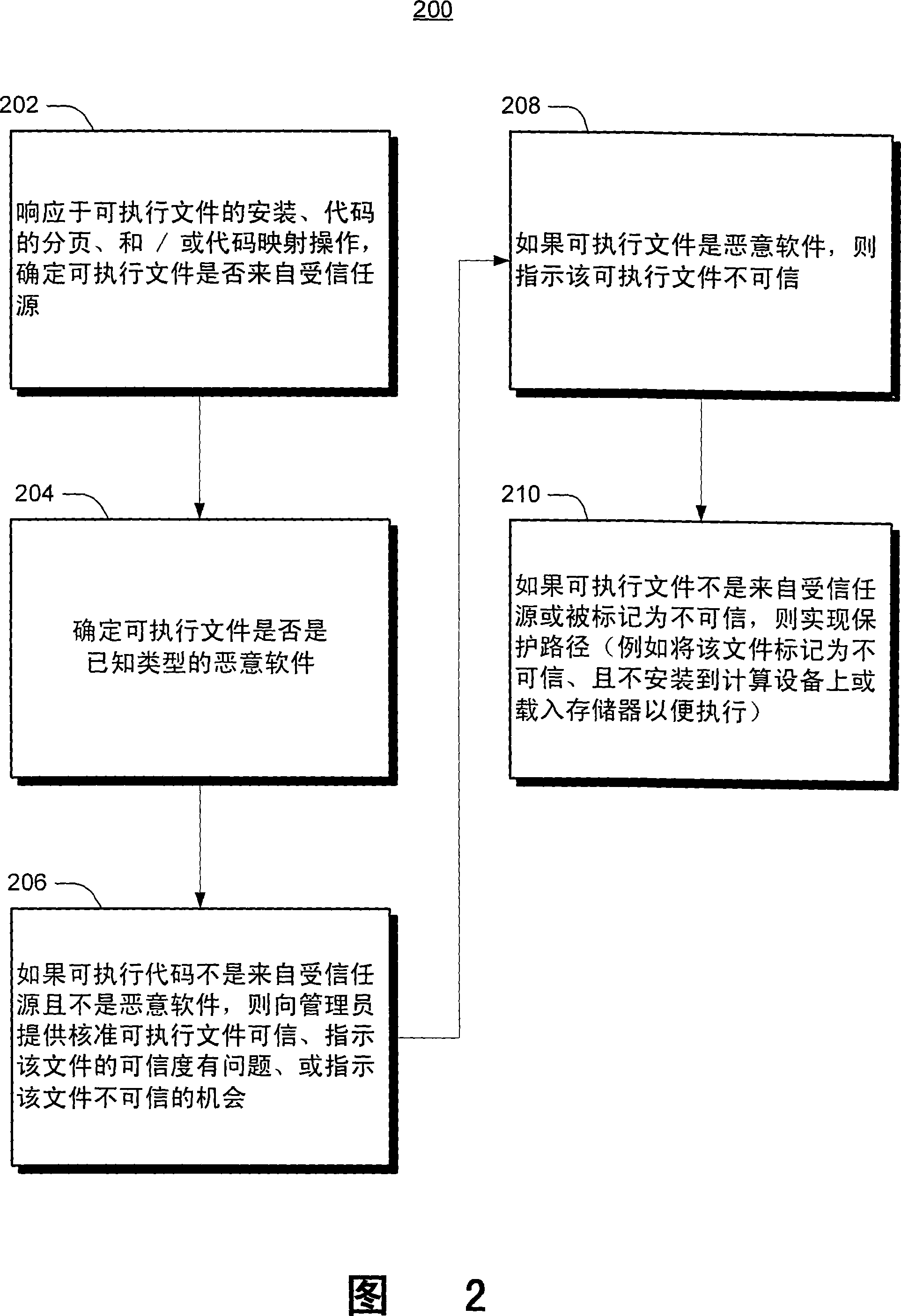
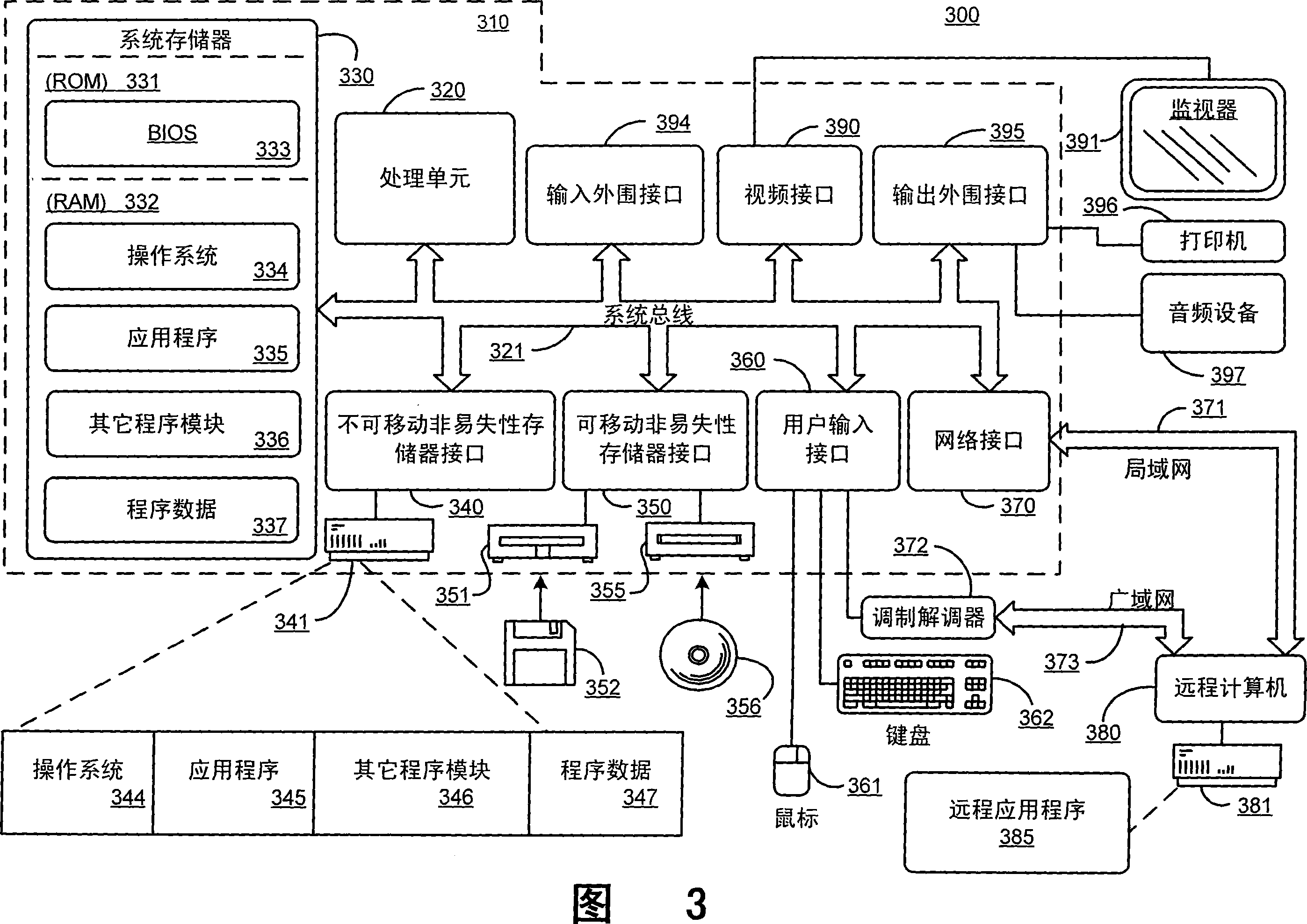
[0011] Systems and methods for verifying the trustworthiness of executable files address conventional code integrity verification techniques and stand-alone (non-integrated) malware proofing techniques by providing a comprehensive trustworthiness verification tool integrated into an operating system (OS). test limits. The authenticity verification tool includes a plurality of authenticity verifiers that are automatically invoked when an executable file is loaded into the system, and when code is mapped into memory for execution. Each of these credibility verifiers determines whether the executable code is from a trusted source (e.g., code signed by a trusted certificate authority), and further evaluates the executable code to find out Trojan horses (code integrity), viruses, spies software, and / or other types of known malware. Known malware is malware associated with known malware signatures or other known malware characteristics.
[0012] The system and m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com