Group key server based key management method in sharing encryption file system
An encrypted file system and key management technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as threats to system security, lack of key operations, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
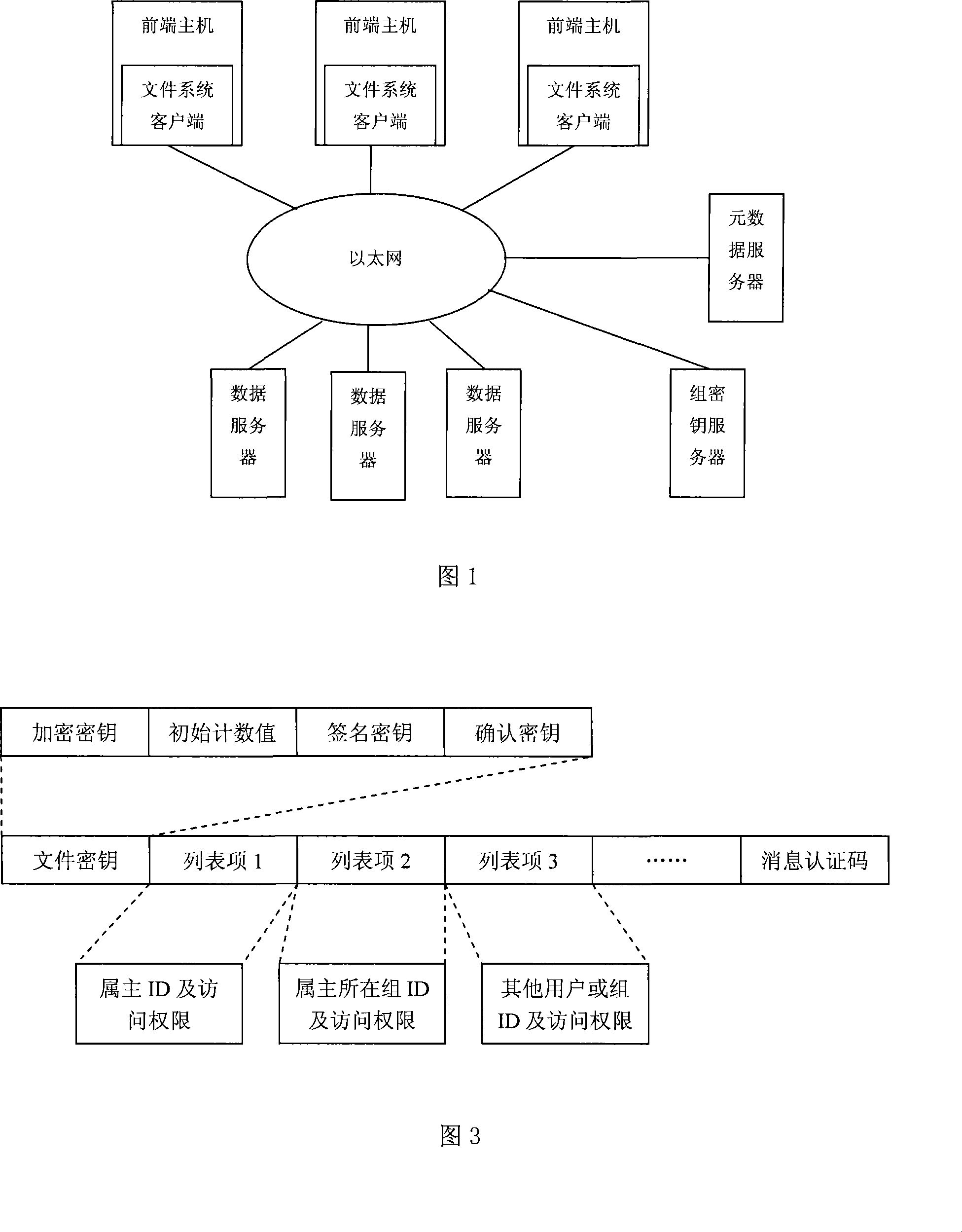
[0051] The shared encrypted file system based on group key server is mainly composed of front-end host, group key server, metadata server and data server. Its hardware structure is shown in Fig. 1.
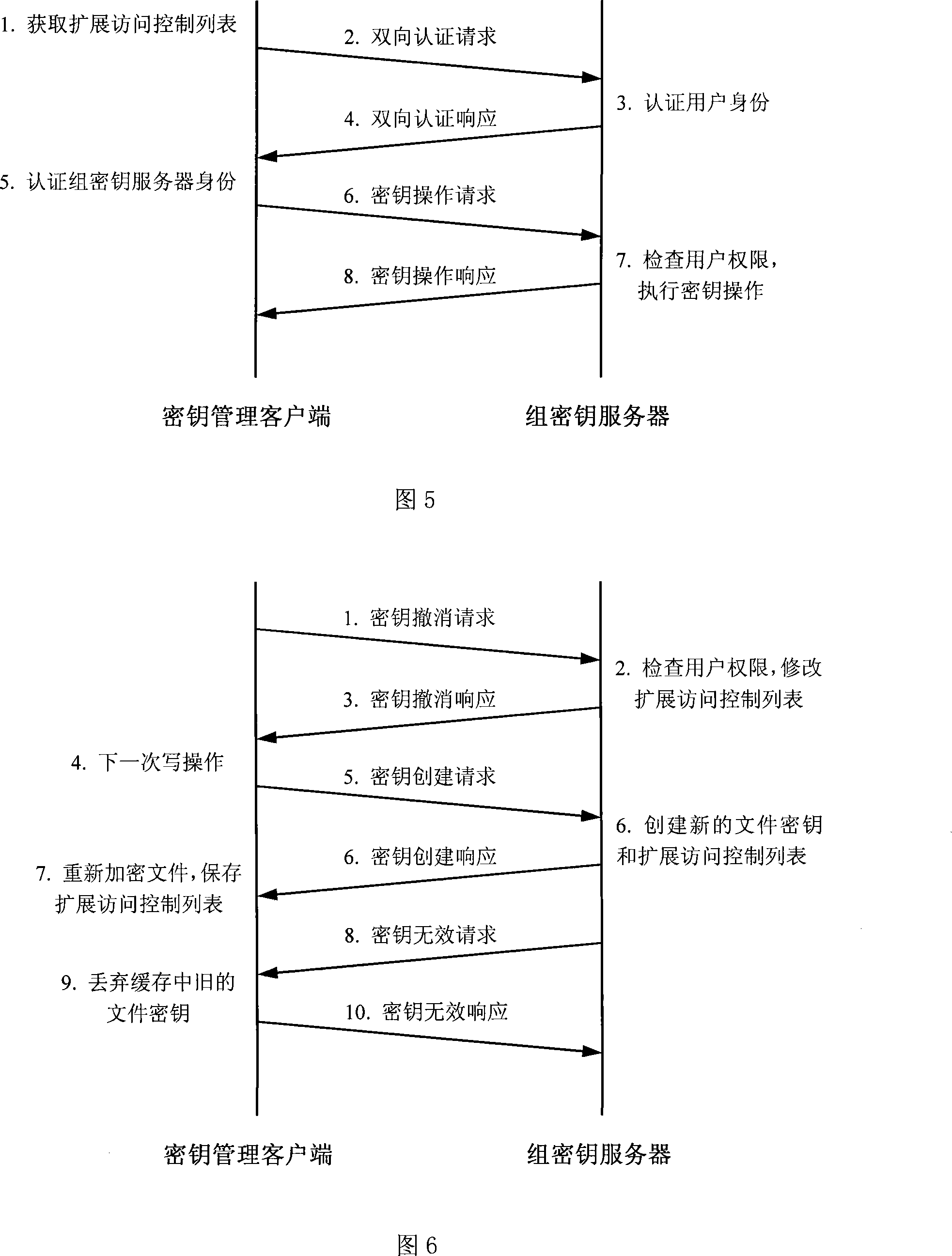
[0052] The file system client running on the front-end host provides various file services to users. The group key server is responsible for performing all key management operations in the system, and implements strict user identity authentication and file access control to ensure the legitimacy of key operations. The metadata server maintains the metadata of all files in the system, including file keys, and provides various metadata services for the front-end host. The encrypted file data is stored on the data server. The various components of the system are connected using Ethernet and communicate via TCP / IP.
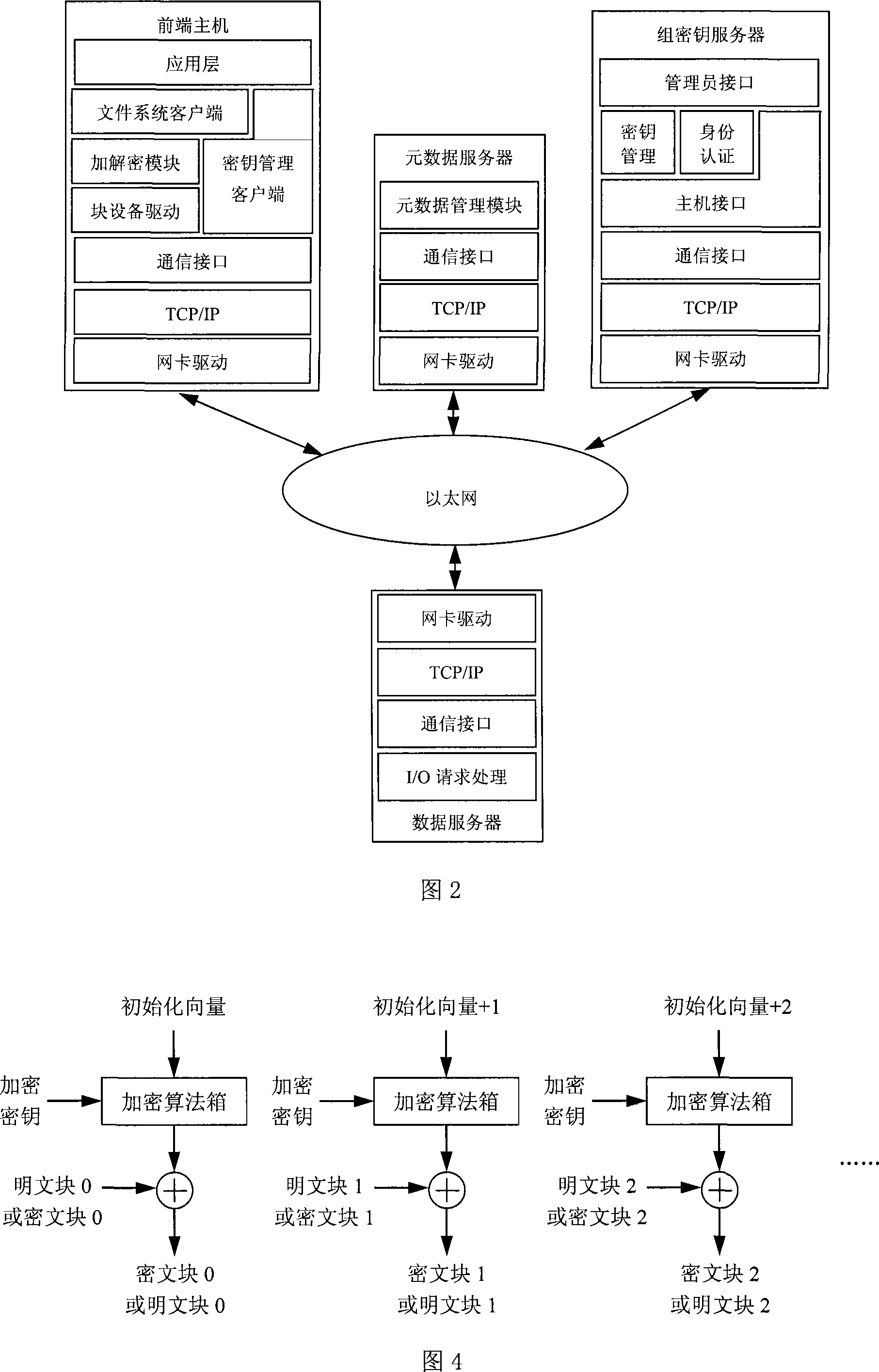
[0053] The software structure of the shared encrypted file system based on the group key server is shown in Figure 2. The file system client on the front-end host pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com