System and method for authenticating network for terminal when SIM card use UMTS terminal and UMTS system
A terminal authentication and terminal technology, applied in the transmission system, digital transmission system, user identity/authority verification, etc., can solve the problems of no f1-f5 function, quintuple parameter calculation, and terminal authentication network, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
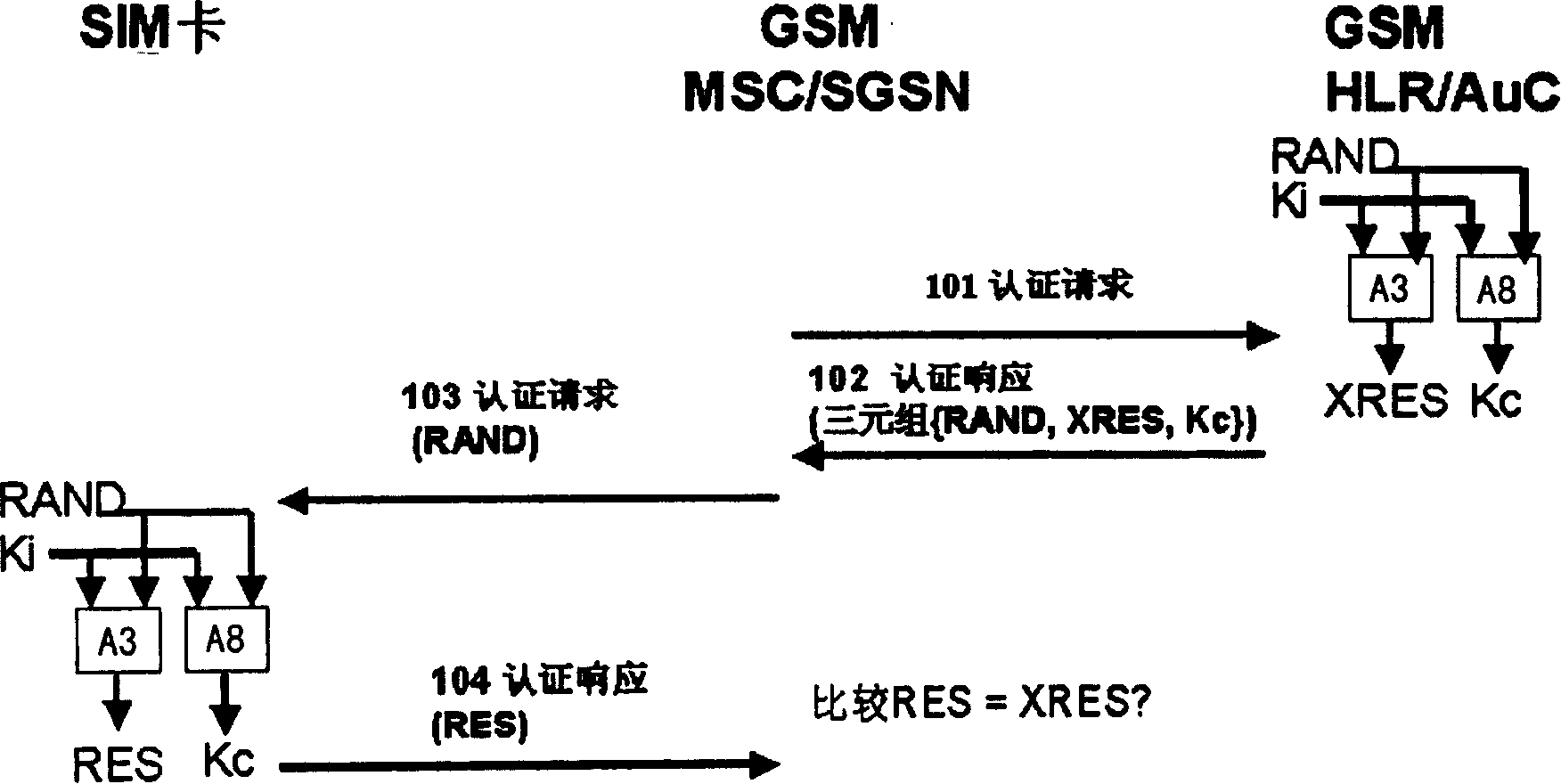
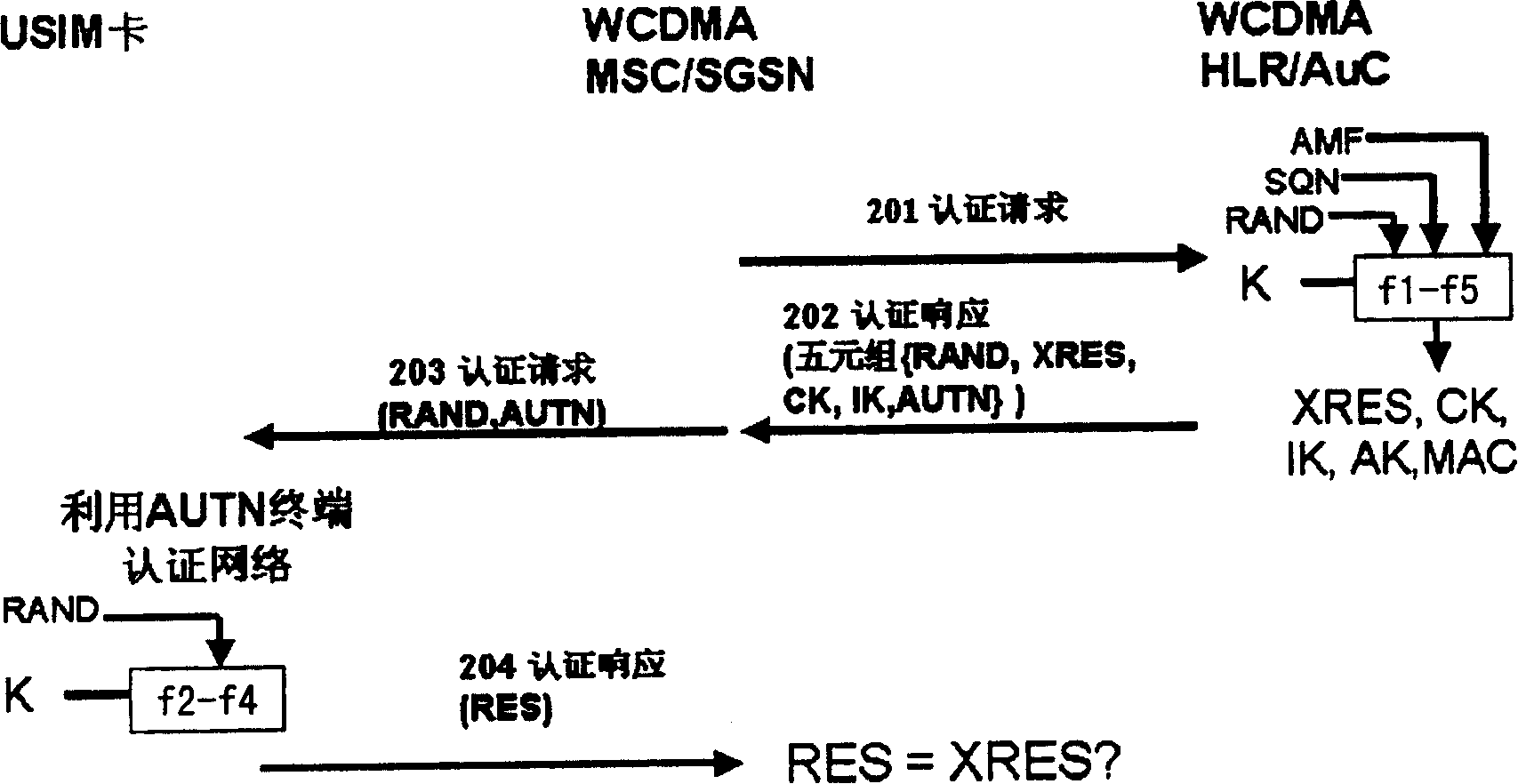
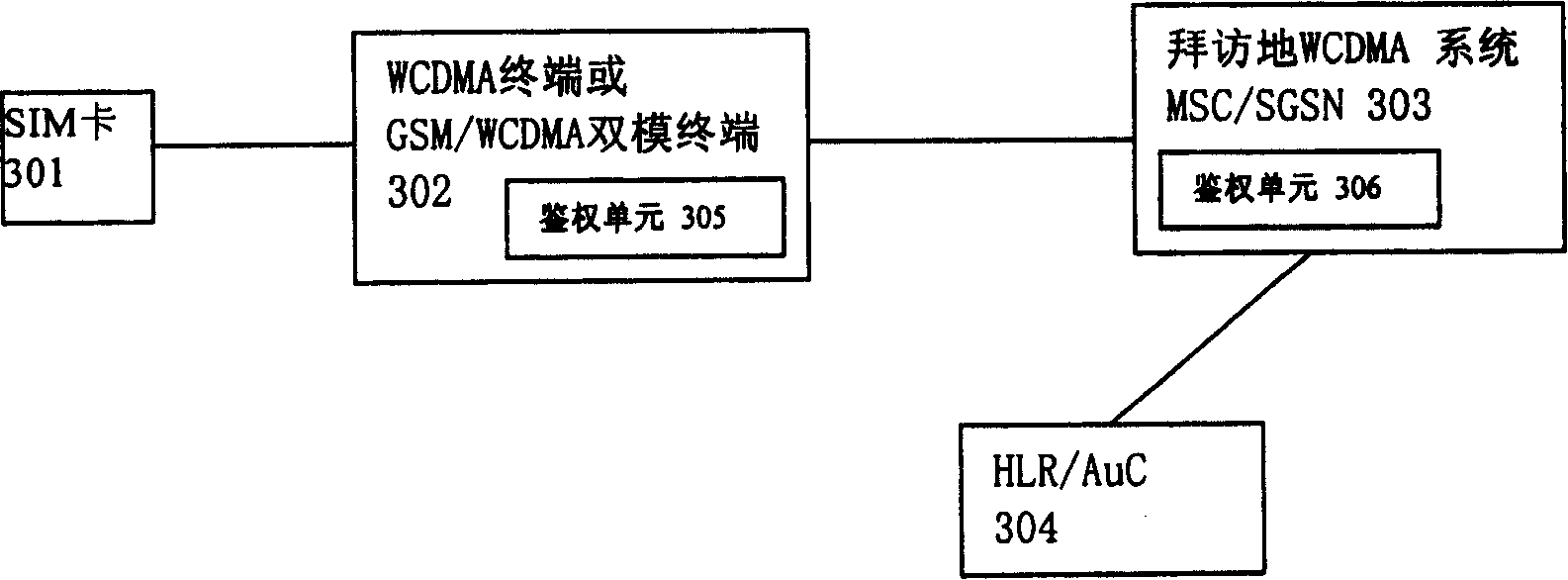
[0039] For the convenience of implementation and application, the present invention is based on the principle of minimum modification to the existing mechanism, and does not add messages or parameters in the standard interface of the 3rd Generation Partnership Project (hereinafter referred to as 3GPP) international standard. According to the existing 3GPP protocol specification, when the SIM card is used in the WCDMA system, although the AUTN parameters have been defined, they are not transmitted or have no effect. The present invention will take full advantage of this parameter. The specific solution for this transmission is: in the MSC / SGSN and the WCDMA terminal or the GSM / WCDMA dual-mode terminal in the WCDMA system, an authentication unit is added respectively, and the authentication unit includes an authentication algorithm and corresponding calculation functions, The authentication algorithm here should have the following two characteristics:
[0040] 1) The algorithm sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com