MAC authentication method and apparatus
A technology for authentication equipment and authentication methods, applied in the network field, can solve problems such as unusable ports, increased costs, and network complexity, and achieve the effects of reducing workload, saving costs, and enhancing flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
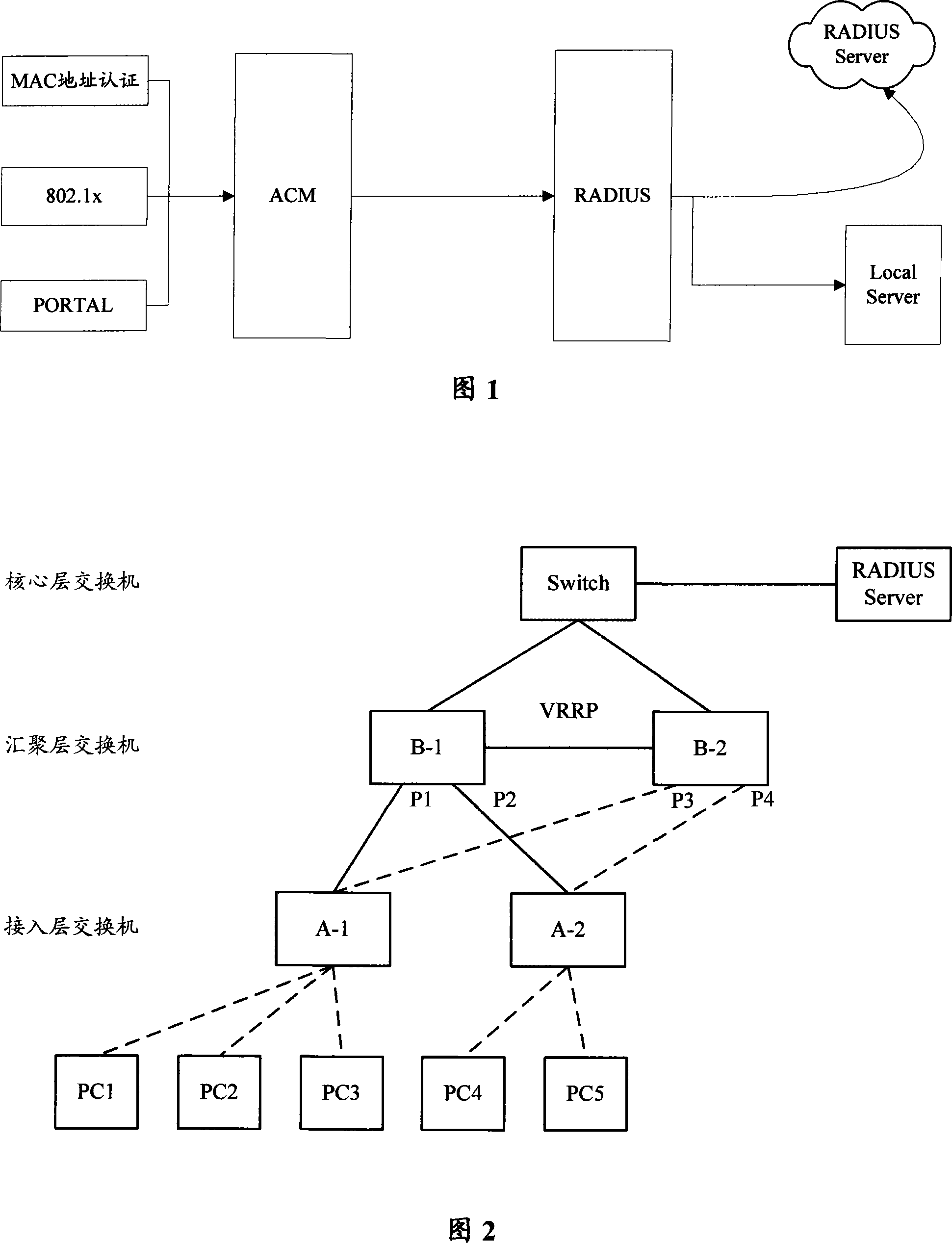
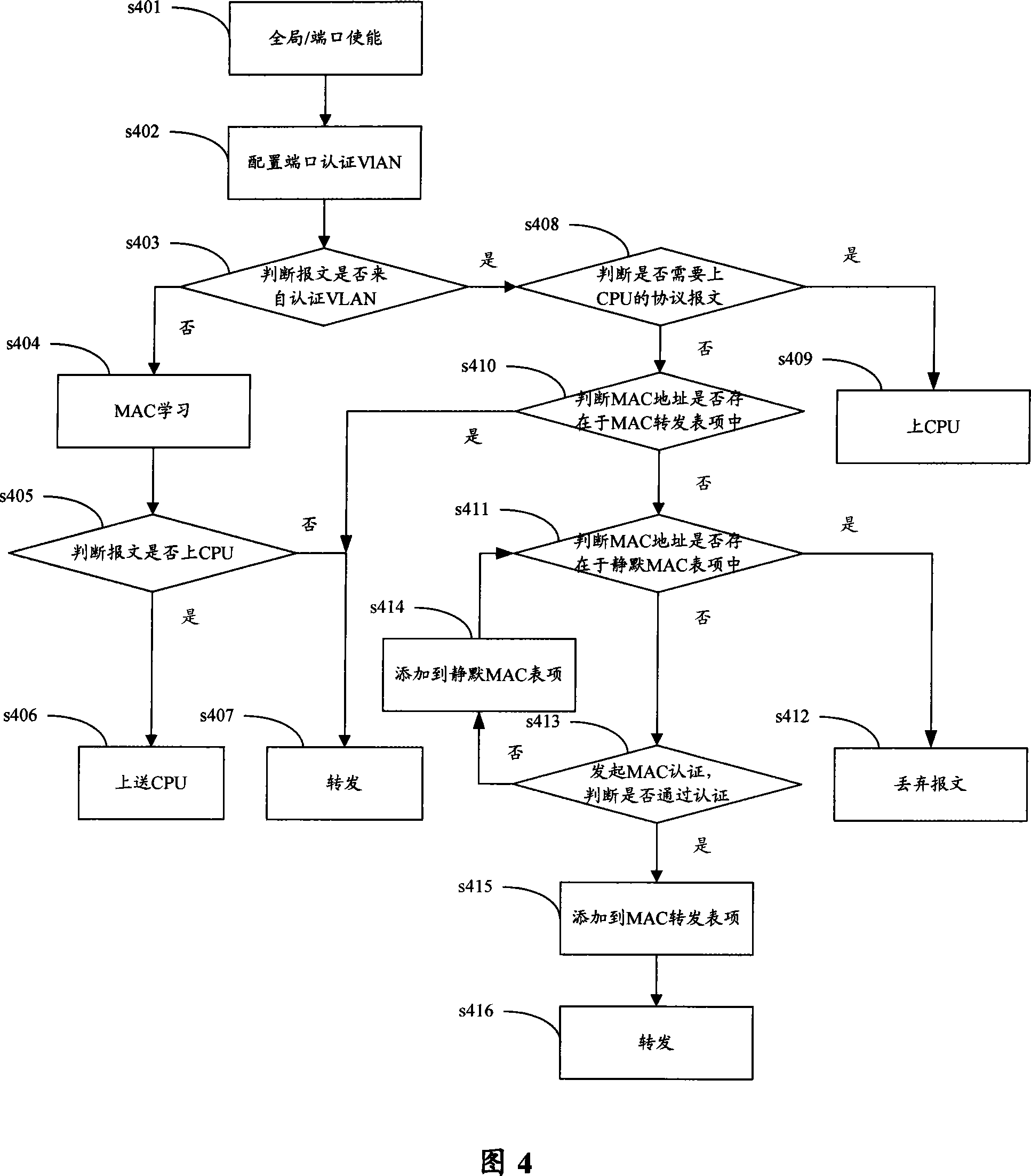
[0050]The core idea of the present invention is to divide the VLAN under the authentication port of the authentication device into two kinds of virtual VLANs, authentication VLAN and non-authentication VLAN. Among them, for the message from the terminal in the authentication VLAN, it is forbidden to send any message in the unauthorized state without MAC authentication, and the message can be transmitted in the authorized state through MAC authentication; for the message from the terminal in the non-authentication VLAN Packets are always allowed to pass through.
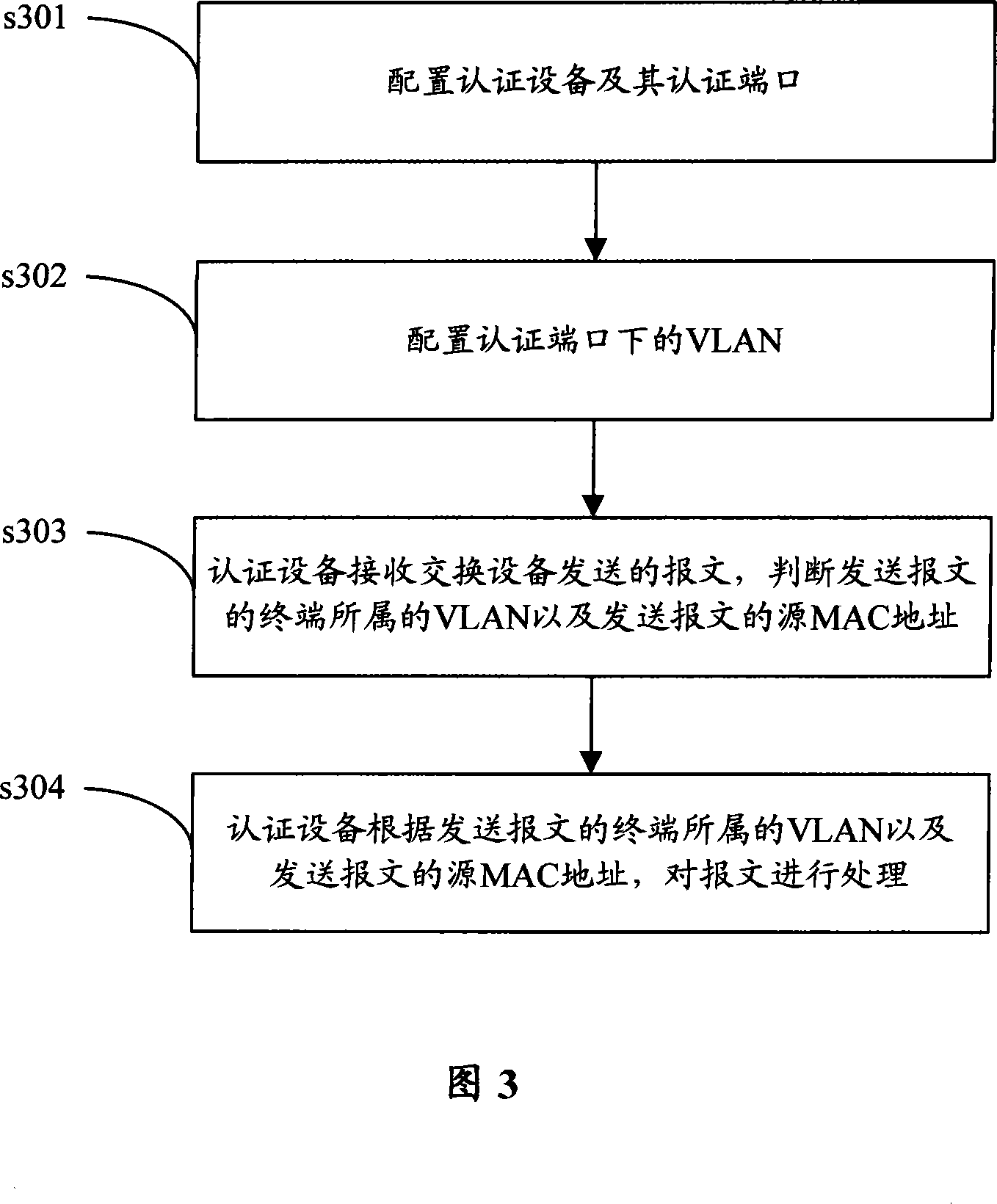
[0051] As shown in Figure 3, a kind of MAC authentication method of the present invention comprises the following steps:
[0052] Step s301, configure the authentication device and its authentication port.
[0053] Specifically, the authentication device is configured to have the MAC authentication function, and its port is configured as an authentication port with the MAC authentication function.
[0054] Step s3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com