Method and system for security verification of data among non-contact equipments
A safety verification and non-contact technology, applied in the field of safety verification, can solve problems such as technical content that does not include safety enhancement, and achieve the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Hereinafter, preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings. In the drawings, the same reference numerals are used to designate the same or similar components, although shown in different drawings. For clarity and conciseness, detailed descriptions of known functions and constructions incorporated herein will be omitted since they would otherwise obscure the subject matter of the present invention.
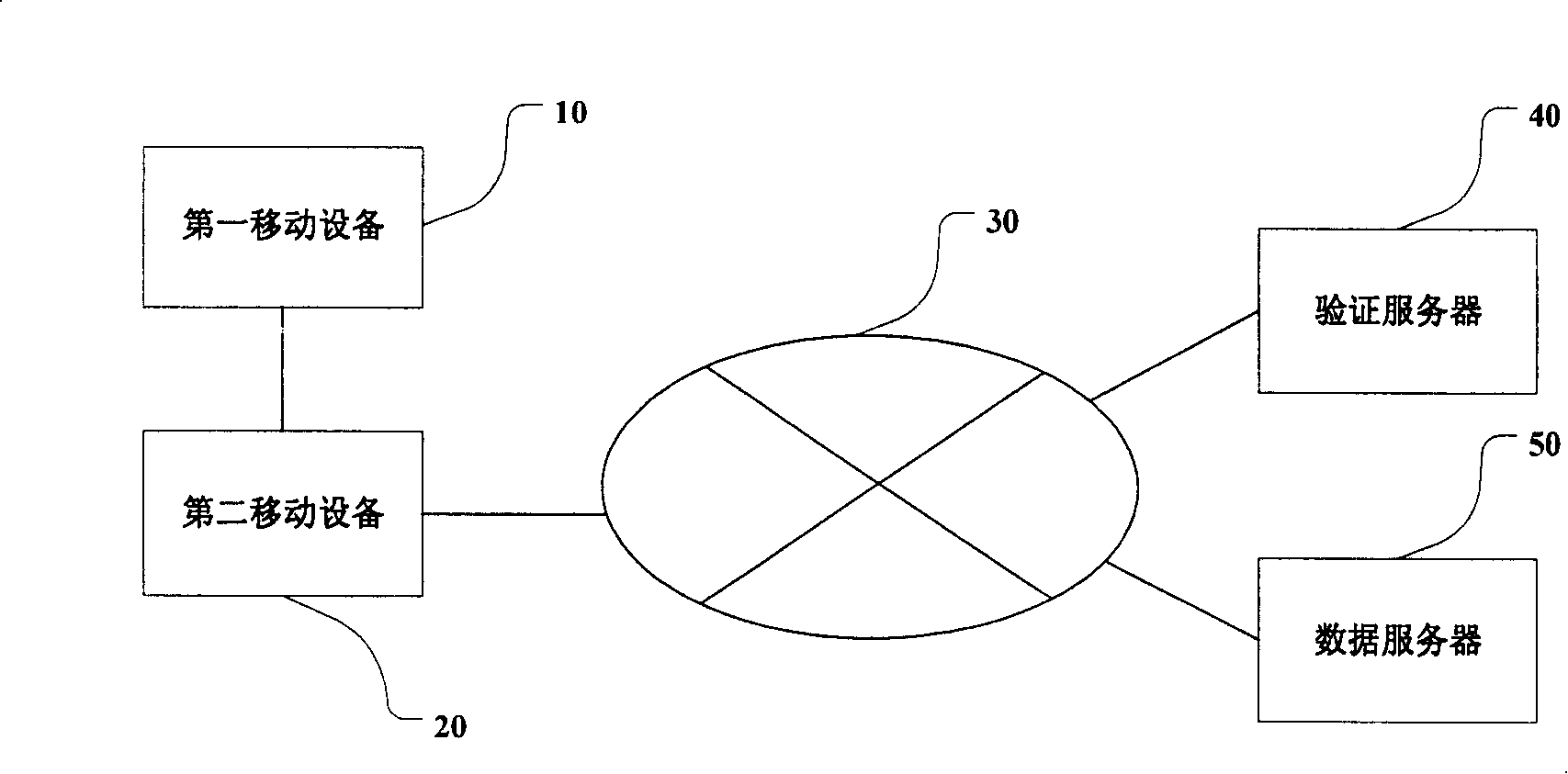
[0040] figure 1 It is a schematic diagram of the structure of the data security verification system used to illustrate the embodiment of the present invention.
[0041] Such as figure 1 The shown non-contact inter-device data security verification system includes a first mobile device 10 , a second mobile device 20 , a wide area wireless communication network 30 , a verification server 40 and a data server 50 .
[0042] After the first mobile device 10 generates the data credential, it transmits it t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com