Software protection device with considerable file memory function
A software protection device and file storage technology, which can be used in program/content distribution protection, computer security devices, instruments, etc., and can solve the problems of small non-volatile memory capacity and inconvenient use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
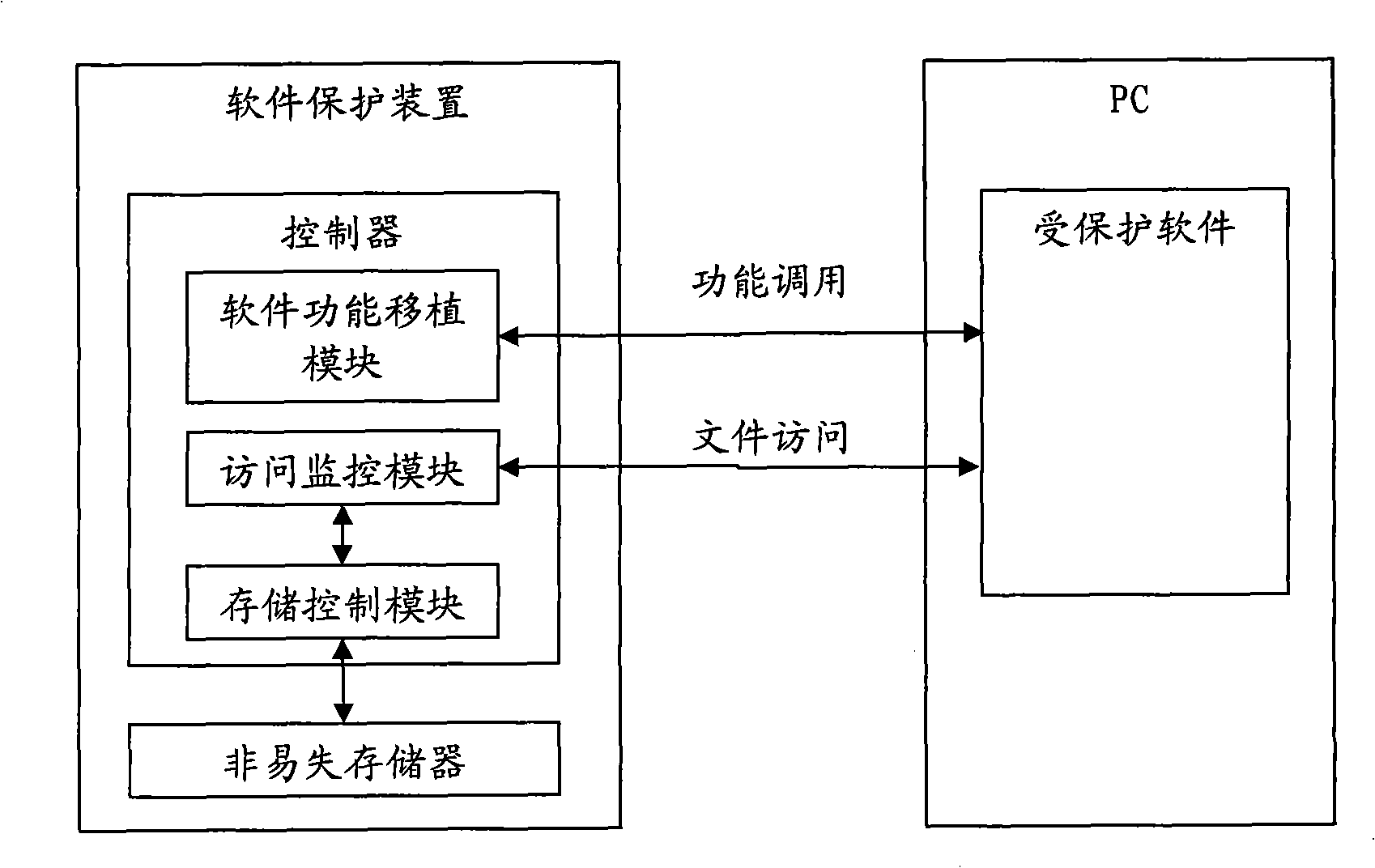
[0033] Such as figure 1 As shown, the software protection device for the large-capacity file storage function includes a controller and a memory.
[0034] The memory is used as a storage medium of the file system, and may be a flash memory or other non-volatile memory.
[0035] Controllers include:
[0036] The software function transplantation module is used for storing and running the function code transplanted from the protected software; the code in the transplantation module can directly access the file data in the non-volatile memory.
[0037] The storage control module is used to operate the non-volatile memory to implement standard storage device management and access functions. The storage control module can encrypt the data written into the non-volatile memory, and decrypt the data read out of the non-volatile memory. The encryption key and the decryption key are stored inside the software protection device, thereby ensuring the privacy of the file data.
[0038] ...
no. 2 example
[0045] For example, a dictionary software, the basic function is that the user enters a word or grabs a word from the screen, and the software searches and displays the meaning of the word; another function is that the user grabs an image from the screen, and the software obtains the word in it through OCR (image recognition) technology Then search and display the word meaning. The dictionary used by the software determines the quality of word meanings, and the OCR algorithm determines the ability and accuracy of image recognition, so software developers should protect these two core data and technologies.
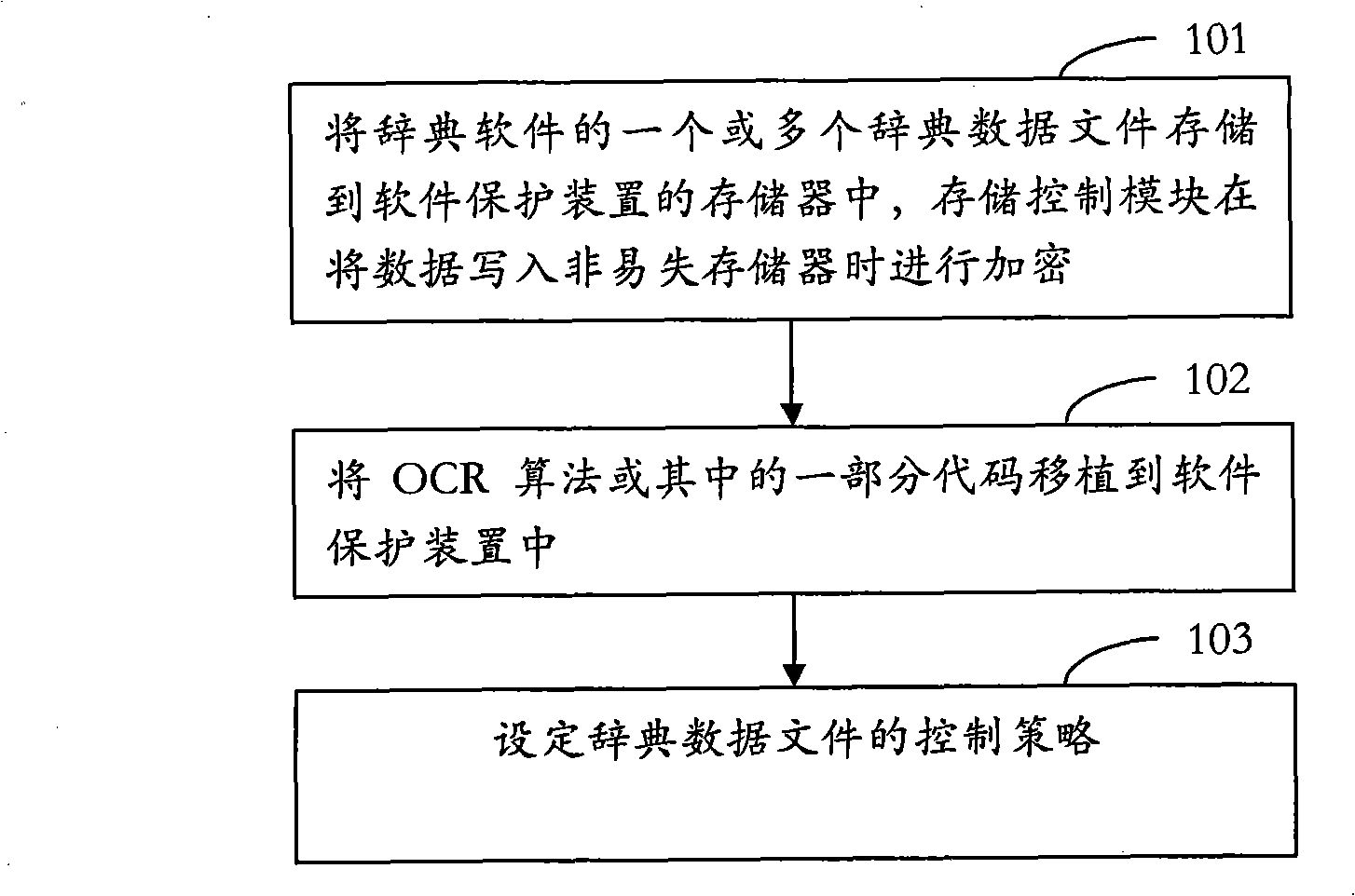
[0046] see figure 2 , the flow process of using the software protection device of the present invention to protect the above-mentioned dictionary software is as follows:
[0047] Step 101, the software developer stores one or more dictionary data files of the dictionary software in the memory of the software protection device, and the storage control module encrypts the ...
no. 3 example
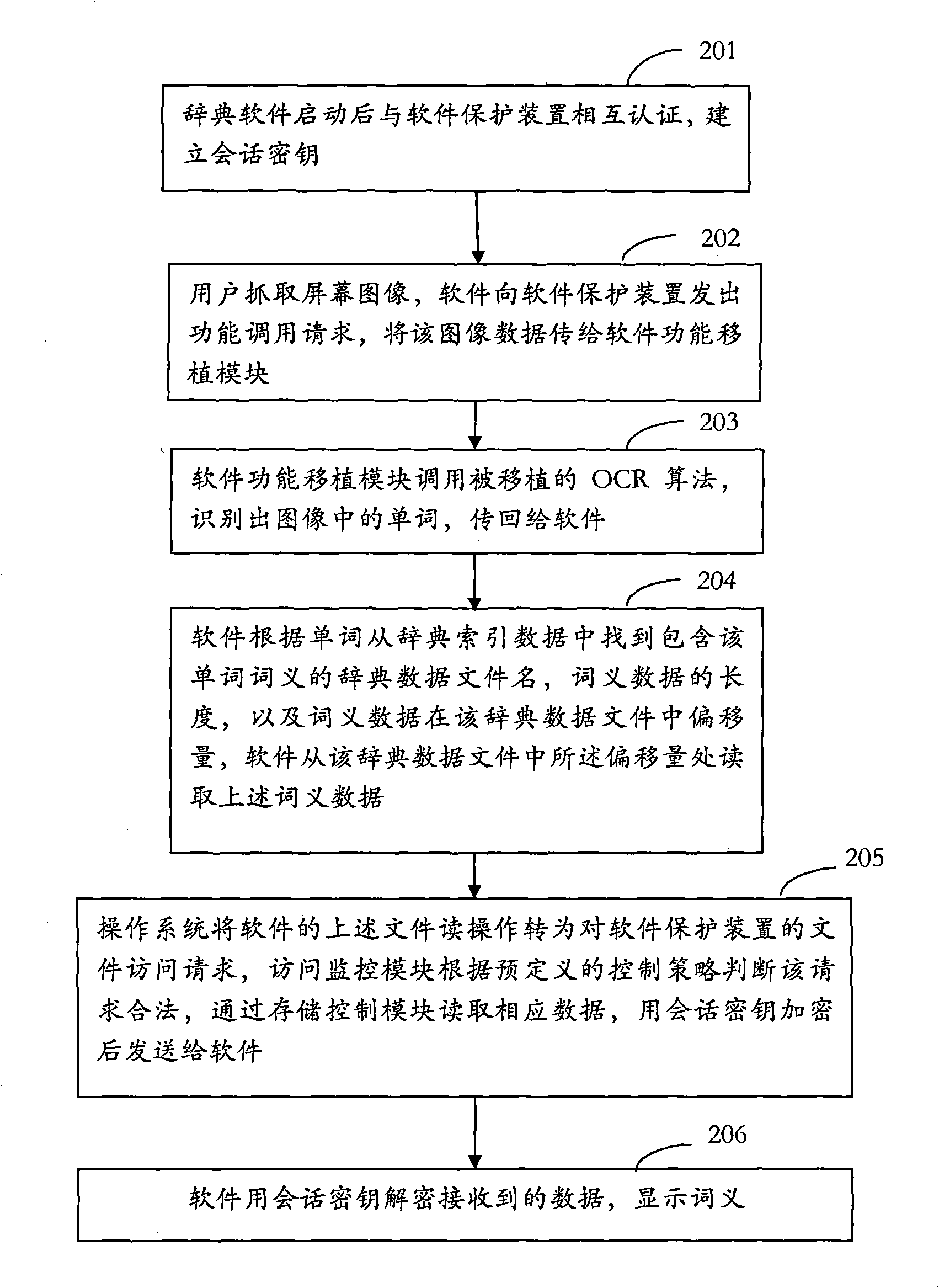
[0051] image 3 It is a schematic flow diagram of the interaction between the dictionary software and the software protection device when the dictionary software is running in the embodiment of the present invention.
[0052] Step 201, after the dictionary software is started, mutually authenticate with the software protection device, and establish a session key;
[0053] Step 202, the user captures the screen image, the software sends a function calling request to the software protection device, and transmits the image data to the software function transplantation module;
[0054]Step 203, the software function transplantation module calls the transplanted OCR algorithm, recognizes the words in the image, and passes back to the software;
[0055] Step 204, the software finds the dictionary data filename containing the meaning of the word, the length of the meaning data, and the offset of the meaning data in the dictionary data file from the dictionary index data according to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com