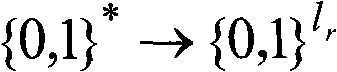Method for switching three-partner key with privacy protection based on password authentication
A technology of key exchange and password authentication, applied in the fields of security technology and privacy protection technology, it can solve the problems such as the inability to effectively protect the privacy of participating users, and achieve the effect of ensuring that it will not be leaked.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
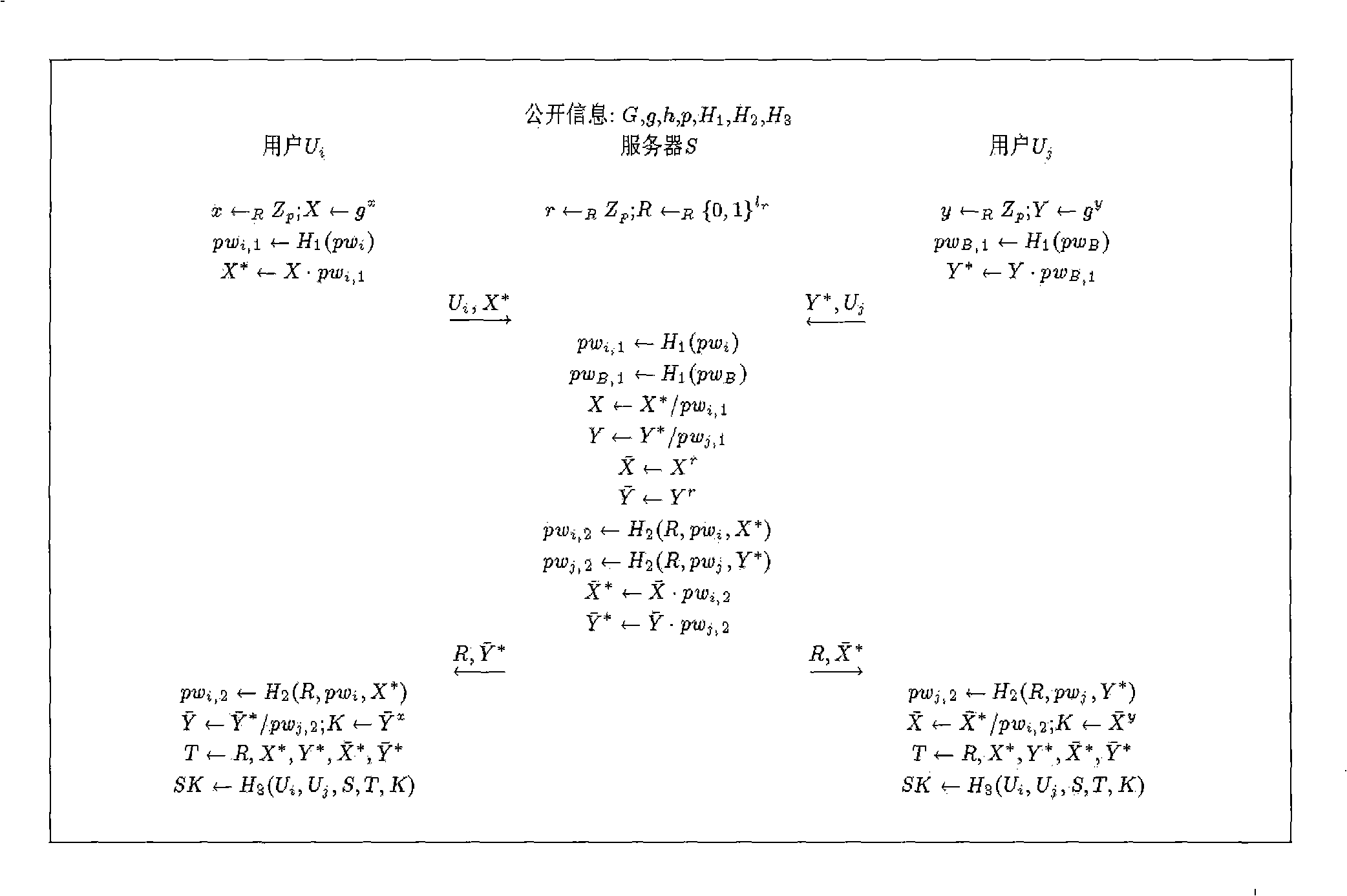
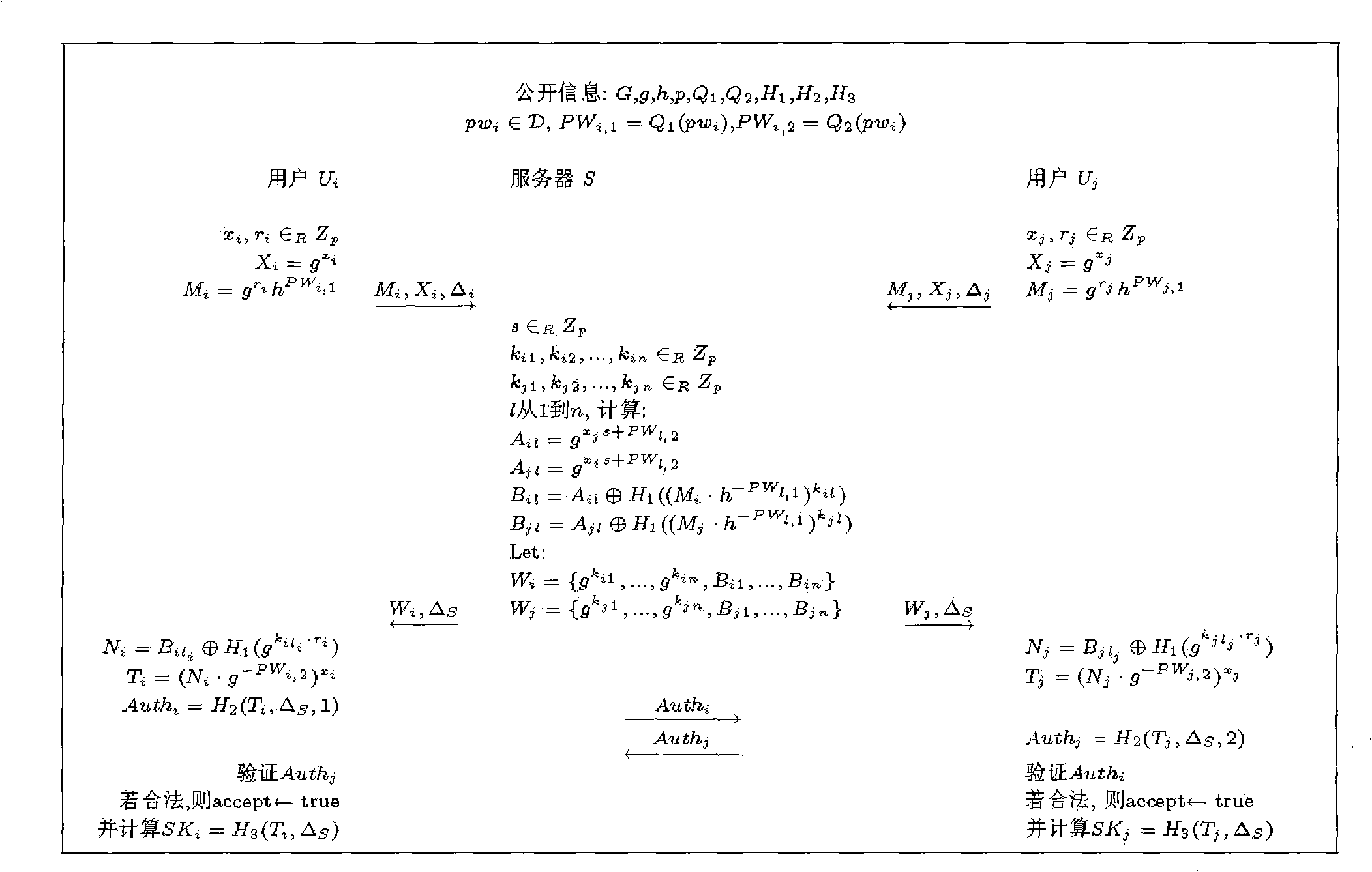
[0025] In the concrete structure of this embodiment, we will forget to transfer (oblivious transfer: OT) scheme (Wen-Guey Tzeng.Efficient 1-out-n oblivious transfer schemes.In David Naccache et al., editors, Public Key Cryptography of Tzeng) of Tzeng -PKC 2002, LNCS 2274, pages 159-171. Springer, 2002) embedded in the 3PAKE scheme of Abdalla et al. (M. Abdalla and D. Pointcheval. Interactive diffie-hellman assumptions with applications to password-based authentication. In A.S.Patrick et al ., editors, Financial Cryptography and Data Security-FC 2005, LNCS 3570, pages 341-356. Springer, 2005.), to implement a password-based authentication-based key exchange method with privacy protection.
[0026] Suppose G is a cyclic group of prime number order with order p, and g and h are two generators of G respectively. let l r is a security parameter, and Q 1 , Q 2 、H 1 、H 2 and H 3 yes { 0,1 } * ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com