Safety system and method for management of net element
A network element management and security system technology, applied in the field of network security, can solve problems affecting security system performance, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to enable those skilled in the art to better understand the solution of the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
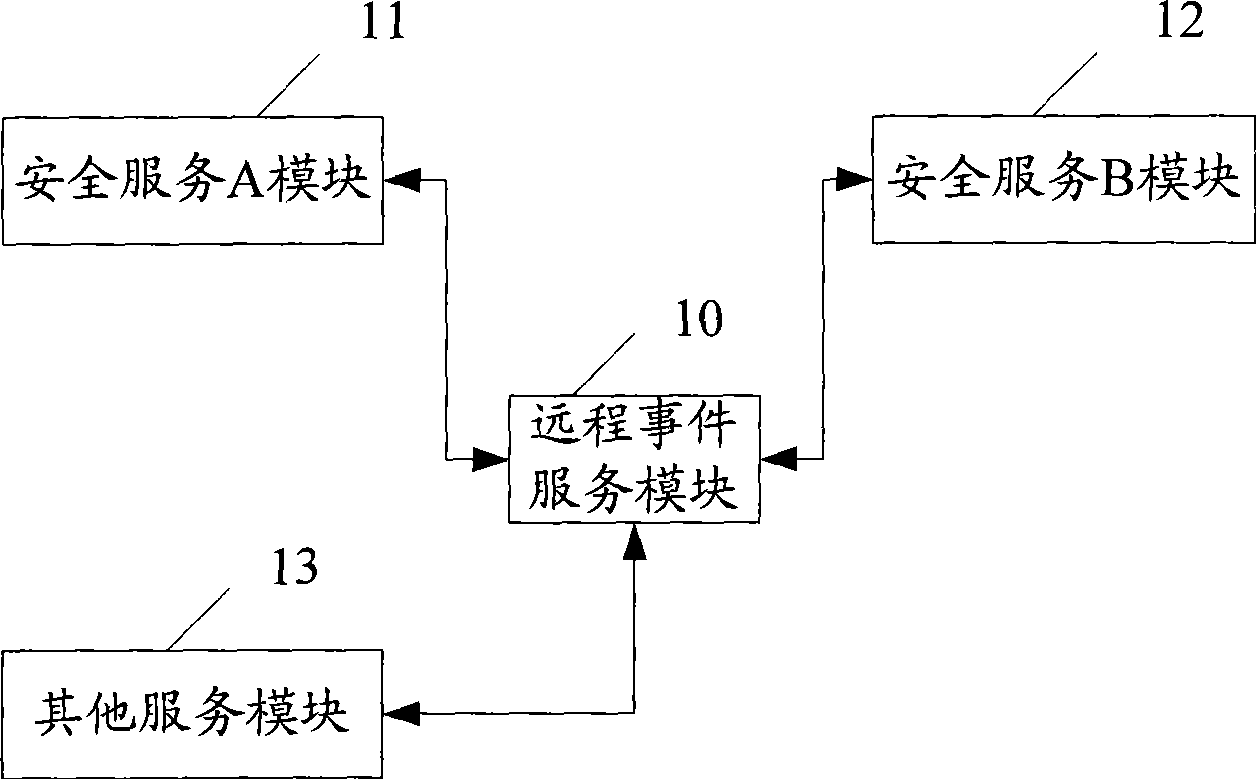
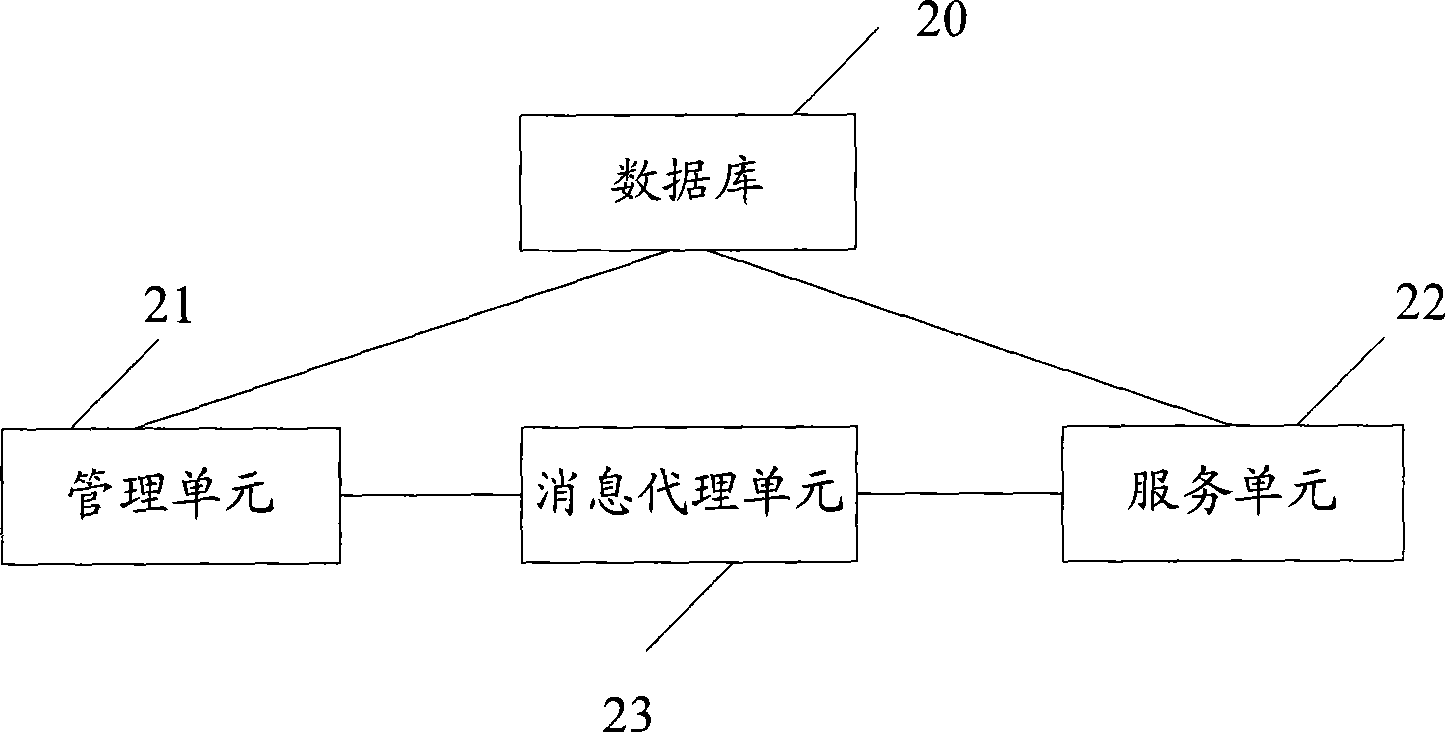
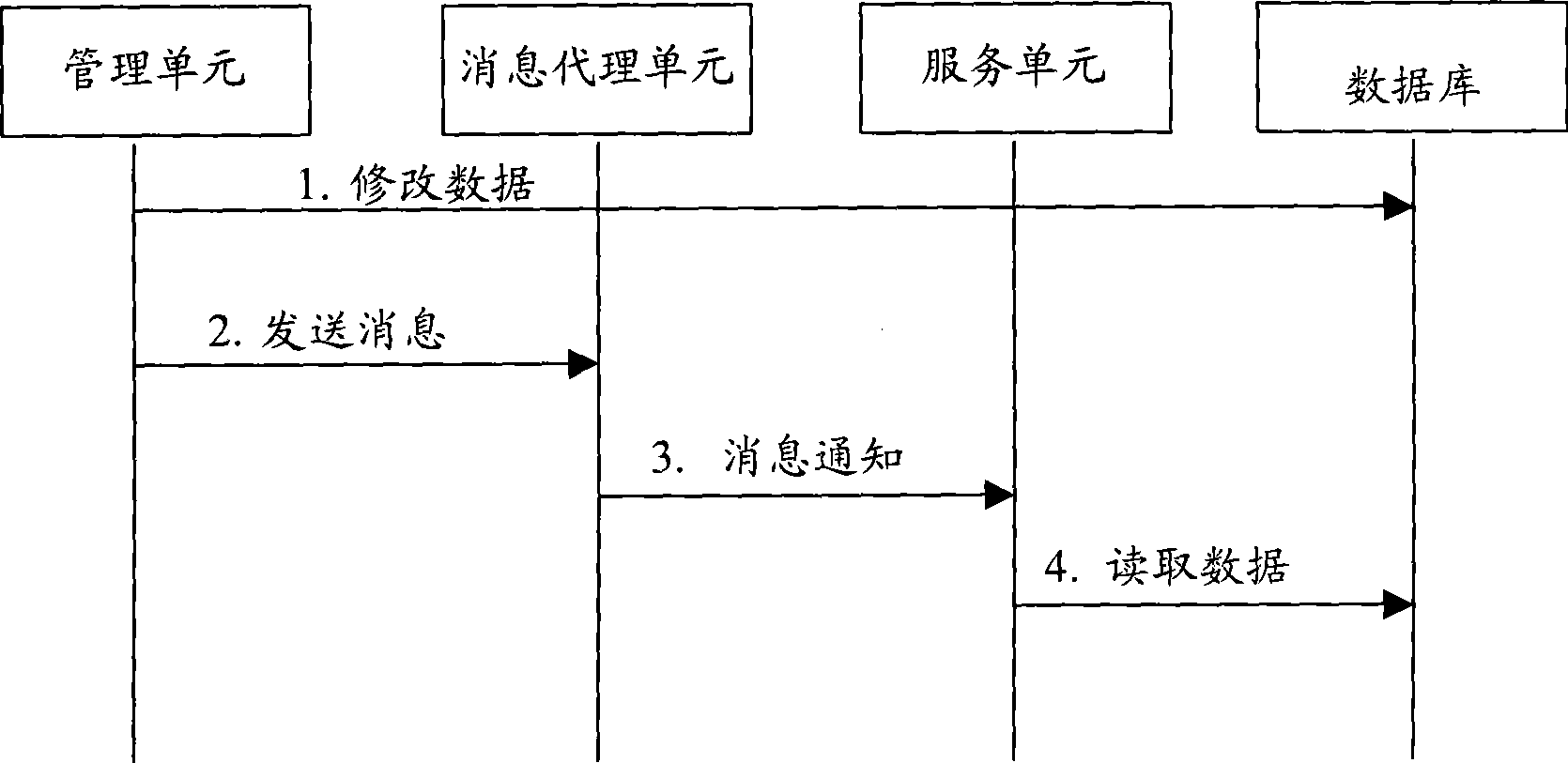
[0033] First, refer to figure 2 The functional block diagram of the first embodiment of the system of the present invention shown:
[0034] In this embodiment, the network element management security system includes: a database 20 , a management unit 21 , a service unit 22 and a message broker unit 23 . Among them, the database 20 is used to store management data in the system; the management unit 21 is used to provide user-oriented management functions. In practical applications, the network element management security system may include one or more management units, such as account management , group management, rights management, log management, session management, etc., there can be multiple individual management units to complete a ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com