IPSec VPN protocol drastic detecting method based on flows
An in-depth detection and protocol technology, applied in the detection field, can solve the problems of literature reports, parsing errors, and string matching ineffectiveness that have not yet found IPSecVPN in-depth detection methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: this embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the described embodiment.
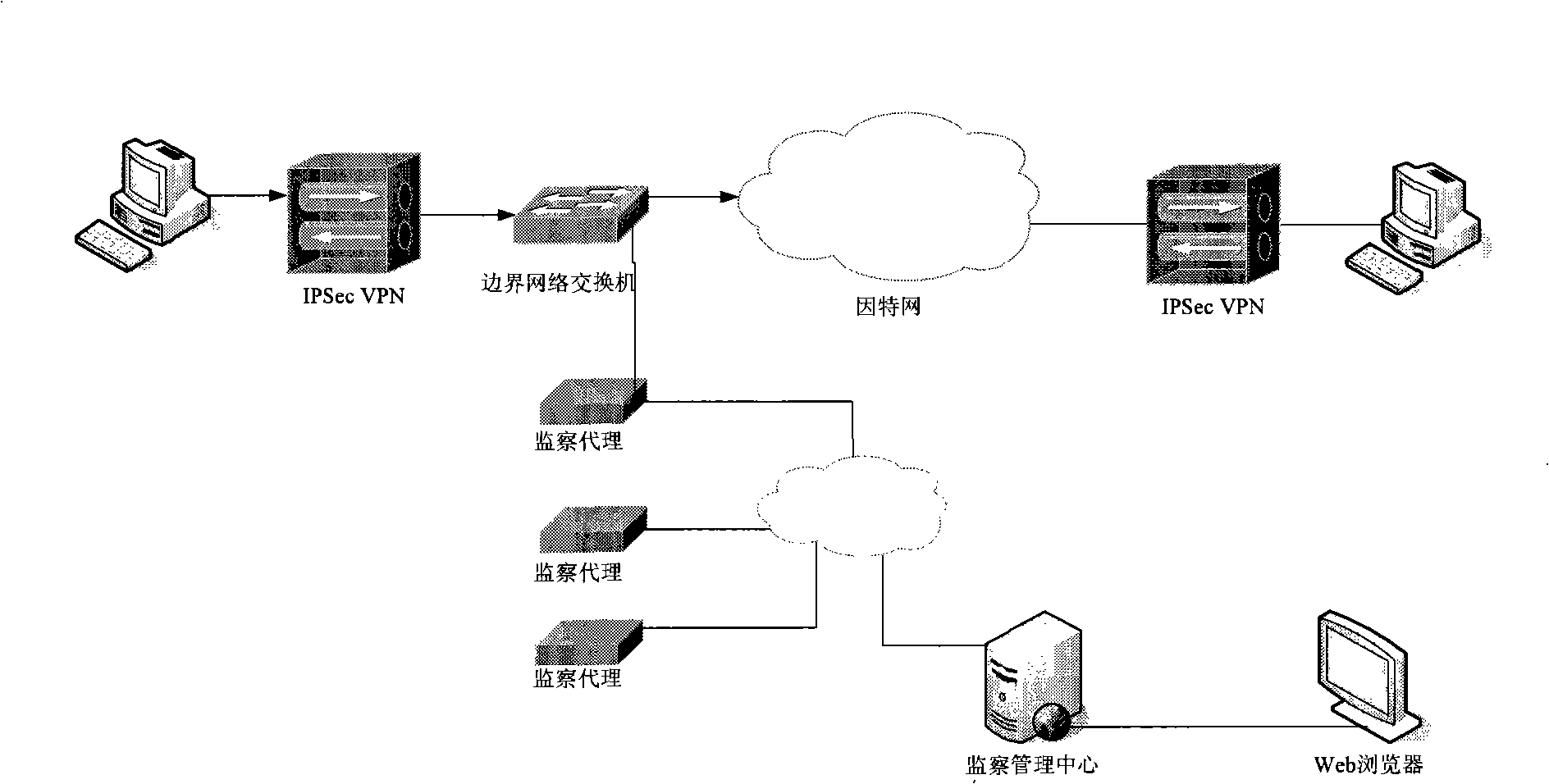
[0055] Such as figure 1 As shown, the IPSec VPN monitoring system is divided into two parts, the central end and the agent end, and this embodiment is specifically described in conjunction with the IPSec VPN monitoring system:
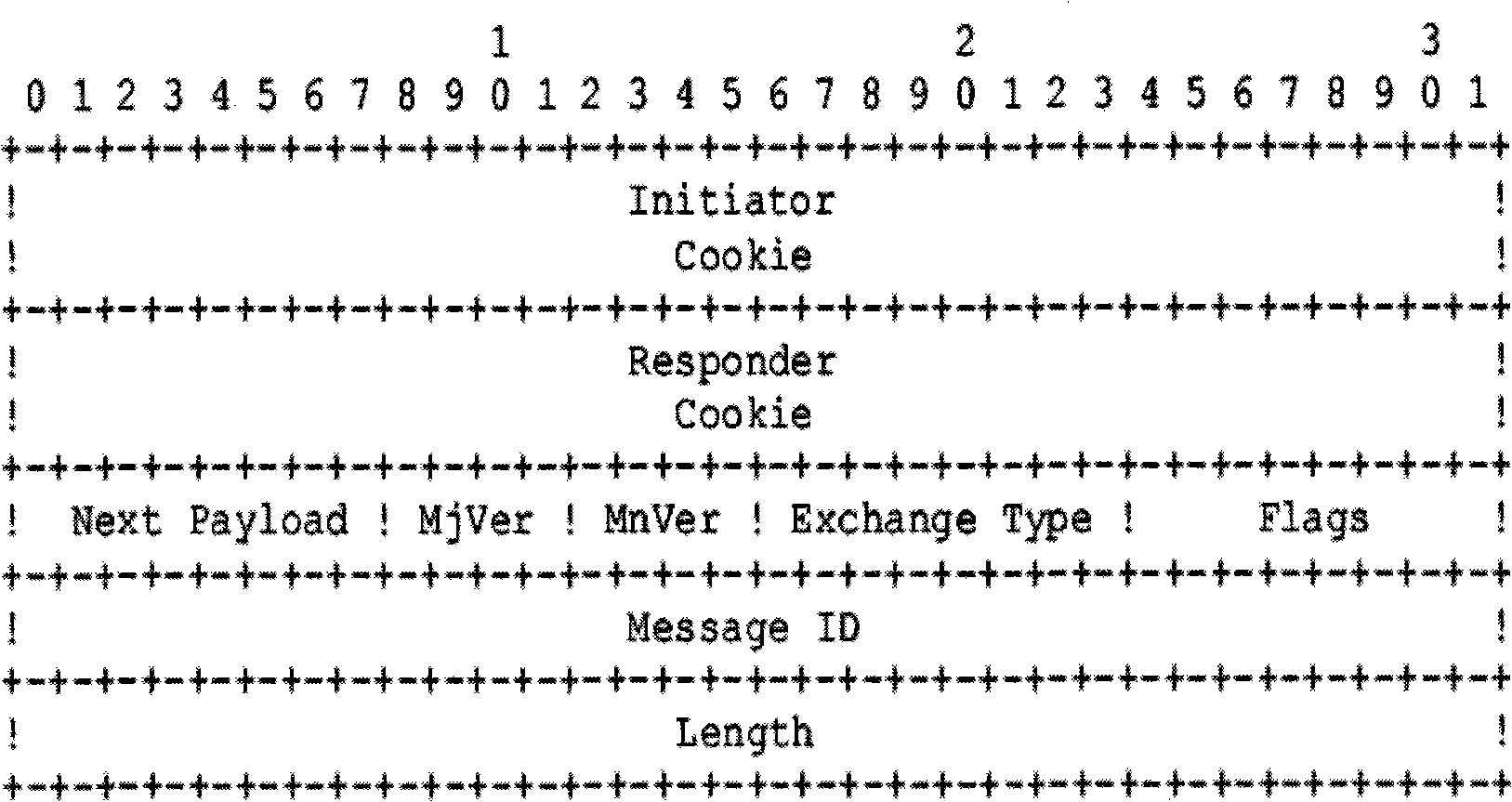
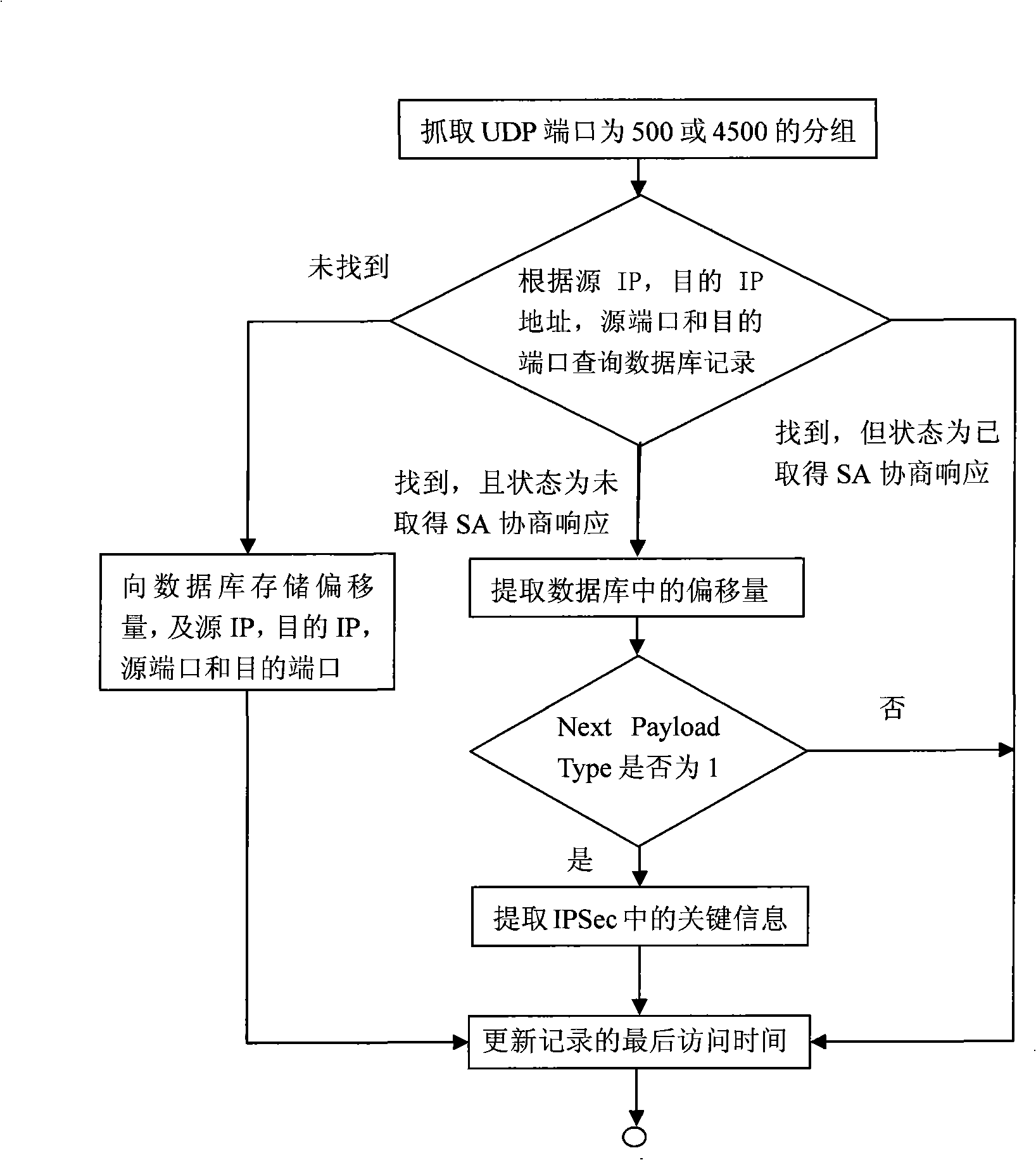
[0056] The agent end is distributed and configured on the switch mirror ports in the border network of each unit. The agent end has two network interfaces, one is used to capture packets, and the other is used to communicate with the central end. The IPSec VPN traffic will flow through the switch of the border network and be captured by the a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com