Method for network on-line payment double authentication by telephone and identifying card
A phone number and two-factor authentication technology, applied in electrical components, payment schemes/models, user identity/authority verification, etc., can solve problems such as prolonged time to collect payment, leakage, and ignoring consumer credit card rights protection.
Inactive Publication Date: 2008-10-22
林仲宇
View PDF0 Cites 12 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
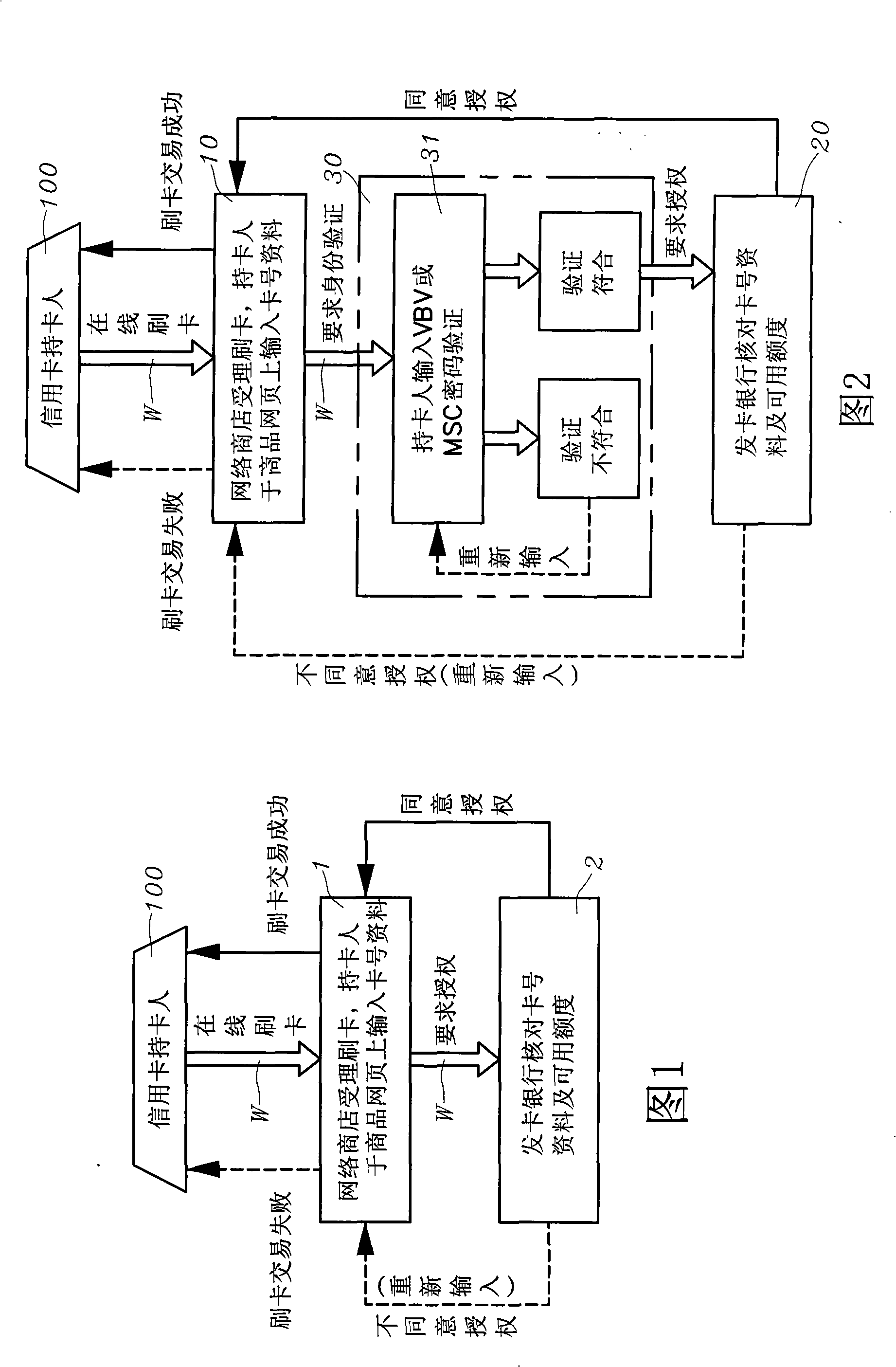
Therefore, the two major international card-issuing organizations, VISA and Master, took the initiative to promote it, and constantly declared to online shopping consumers that they should go to their card-issuing banks to apply for the "self-set password" for VBV or MSC verification identity verification, as long as they use the "self-set password" "In the online store with VBV / MSC verification mechanism, the credit card number of the cardholder will not be stolen, and the protection of online consumption will be obtained; however, from the two major international card issuing organizations VISA and Master to In the statement of the online store operator, it can be understood that this is not the case in fact. The statement of the appeal is: "As long as the online store operator who participates in becoming a member of the online store with the VBV / MSC mechanism, what will be completed on your webpage in the future For every online credit card transaction, the consumer who puts forward "denying the transaction" will get the result that the arbitration is not established, because the consumer has already entered the record of "self-set password" for identity verification by VBV or MSC before swiping the card online , so consumers cannot deny that the transaction was not done by themselves, so the time for claiming payment from the card issuing bank will not be delayed." This shows that under the claim of protecting the rights and interests of online shopping consumers, the euphemism But it has another meaning, because after the above-mentioned additional VBV or MSC verification procedure, the card issuing bank and the online store can unilaterally and directly regard it as the basis for the cardholder's own consumption, even in the future After receiving the bill, if an online shopping consumer finds out that the credit card information has been illegally stolen by others and the fact that the consumption amount has been fraudulently swiped, but wants to make a claim of "denying the transaction" according to the usual practice, he will If the online store submits VBV or MSC identity verification record data, the arbitration will not be established. The final result is that the appeal arbitration is invalid, and the cardholder has to continue to pay obediently.
Due to the illegal intrusion of the internal computer information system of the card issuing bank or the host computer system of the online store, or the incidents of the cardholder (client) computer being skimmed, there are frequent incidents. To cite the most recent example, in 2007 In March, hackers successively invaded TJX, a multinational retailer with an annual turnover of more than 16 billion U.S. dollars (Note: TJX’s business scope includes the United States, Canada, Puerto Rico and the United Kingdom, and its subsidiaries include A.J.Wright, Bob’sStores, HomeGoods, T.J.Maxx, HomeSense, Winners, TKMaxx and other eight systems, a total of 2,500 stores), and during the 18-month period from July 2005 to December 2006, hackers continuously invaded the computer database of TJX Corporation, and stole at least 45 million The customer's credit card number data, and when the computer of the cardholder (client) is logged, the "self-set password" of its original VBV / MSC authentication is also transmitted on the network using its own computer, Therefore, the VBV / MSC "password" of the cardholder will also be recorded and leaked, and after such a large credit card number data leak of TJX, its presidents Carol and Merowitz only In the open letter of the enterprise management website, I apologized to customers, deeply regretted the inconvenience caused by this illegal intrusion incident, and said that I will work hard to maintain a safe shopping environment in the future, but did not mention any compensation for data leakage.
Therefore, under the current situation that the card-issuing bank or online store cannot guarantee that the consumer's credit card data will not be leaked, they reversely require online shopping consumers to handle and use VBV / MSC "self-set password" identity verification to do It is the basis for confirmation of online credit card transactions. This approach only fully takes care of the interests of both online stores and card issuing banks, but ignores the protection of consumers' original rights and interests of swiping cards. Instead, consumers have to bear alone. The risk of fraudulent swiping, and relatively in a weaker position, so how to effectively protect online shoppers’ online card swiping rights from the risk of fraudulent swiping is more urgent and necessary
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
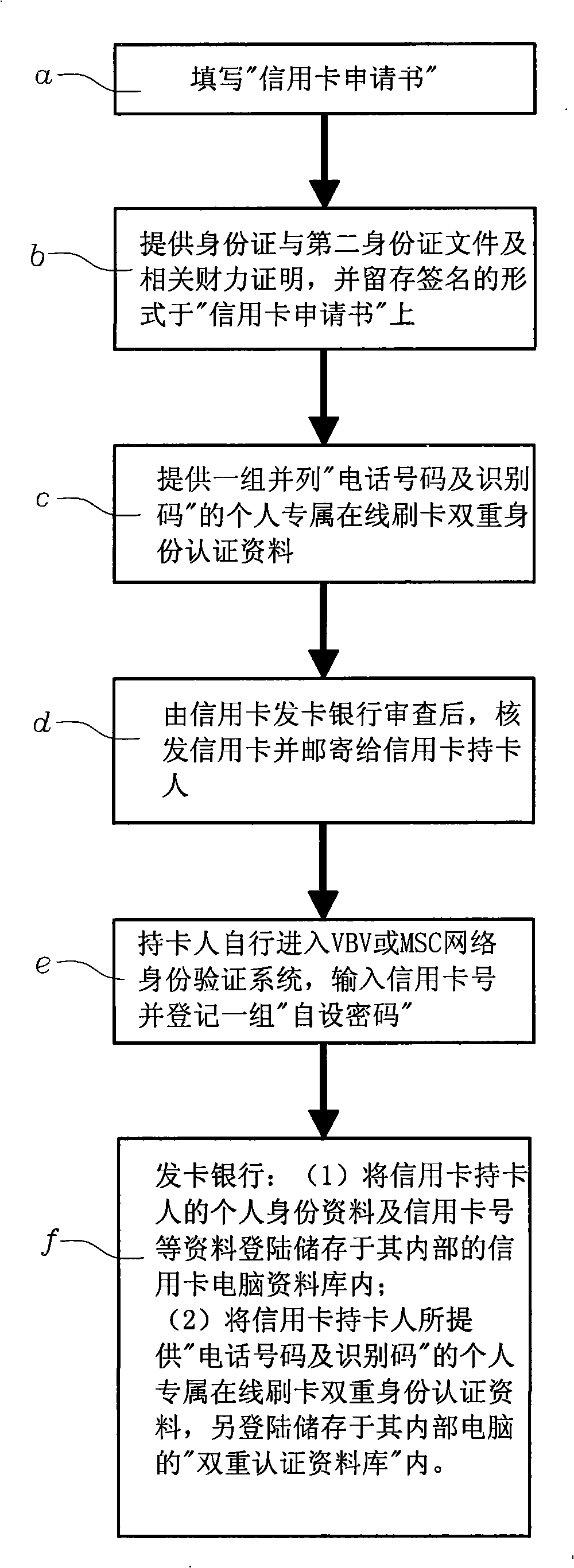
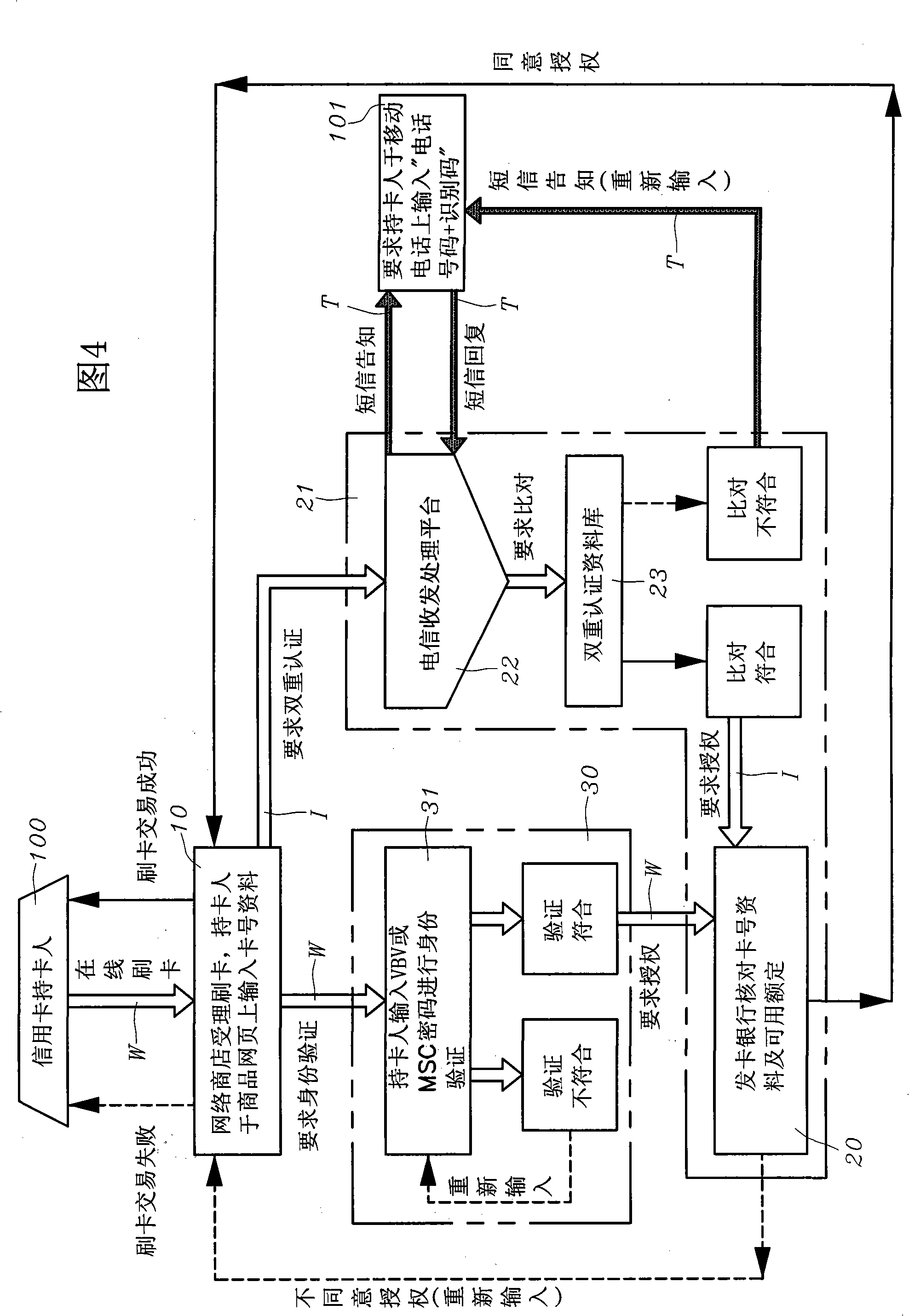
The invention uses the phone number and the identifying codes as the network online dual authentication method. The card holder of the credit card registers the VBV or MSC network identity checking ''self-setting password'' to the card-issuing bank, the holder also provides a group of ''phone number and the identifying codes'' personal special online dual identity authentication data to the card-issuing bank; the data login is stored in the ''dual authentication database'' of the ''credit card dual authentication computer system'' of the card-issuing bank; while the card-issuing bank is processing the online card slotting, the bank informs the card holder in the short message way besides the ''self-setting password'' of the VBV or MSC network identity checking for the card holder; requiring to respond to the personal special online identity authentication data of the ''phone number and the identifying codes''; comparing to the ''phone number and the identifying codes'' in the ''dual authentication database'' as the card slotting transaction on the network for the card holder for the dual rechecking to confirm whether the invention is the network credit card transaction under the entitlement.
Description
Using the phone number and identification code as the method of two-factor authentication for online card swiping (1) Technical field: The present invention provides a double authentication method using phone numbers and identification codes for online online card swiping, which uses the credit card holder's own authentication system in addition to the VBV or MSC network identity verification system used in the existing online online card swiping transactions. Provide a set of parallel "telephone numbers and identification codes" to the card-issuing bank so that they can be used as the basis for re-identification of the cardholder when performing online credit card transactions; in addition to avoiding the loss, theft or In addition to being stolen online due to skimming, it can also form a second-layer firewall to prevent fraudulent brushing, thereby preventing personal credit card information and its VBV or MSC from being stolen due to hackers illegally invading online store...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L29/06H04L9/32G06Q30/00G06Q20/00
CPCG06Q20/24G06Q20/40G06Q20/403G06Q20/425G06Q40/02
Inventor 林仲宇
Owner 林仲宇
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com