Method and system for silent hiding network transmission
A technology of network transmission and data transmission, applied in the direction of transmission system, electrical components, etc., can solve the problem that network data cannot pass normally and cannot meet the needs well.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
[0070] (1) The specific communication process of silent and concealed network transmission equipment
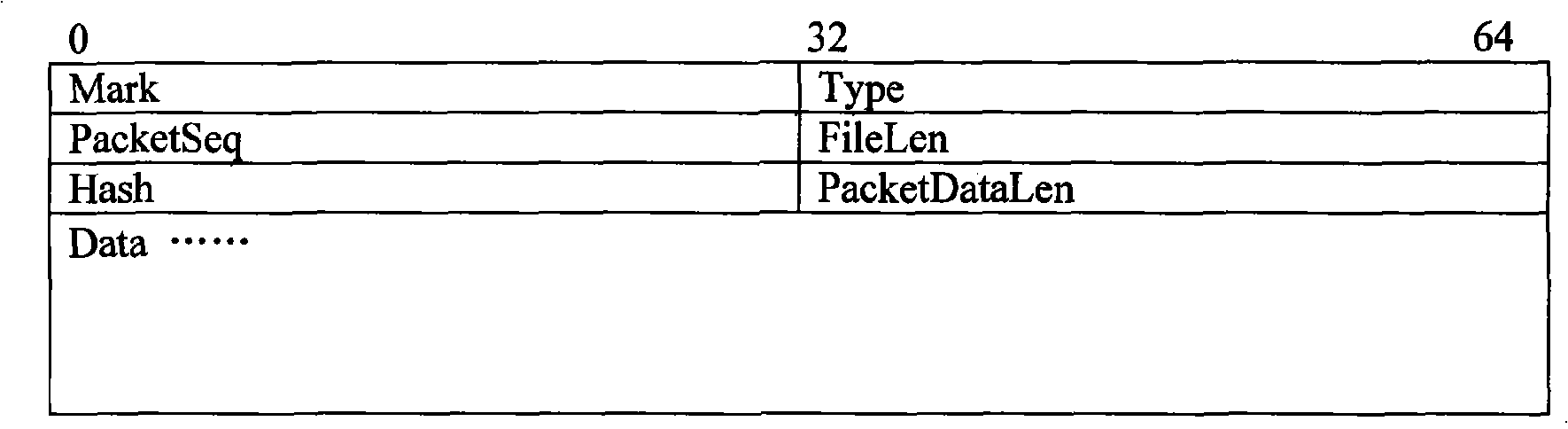
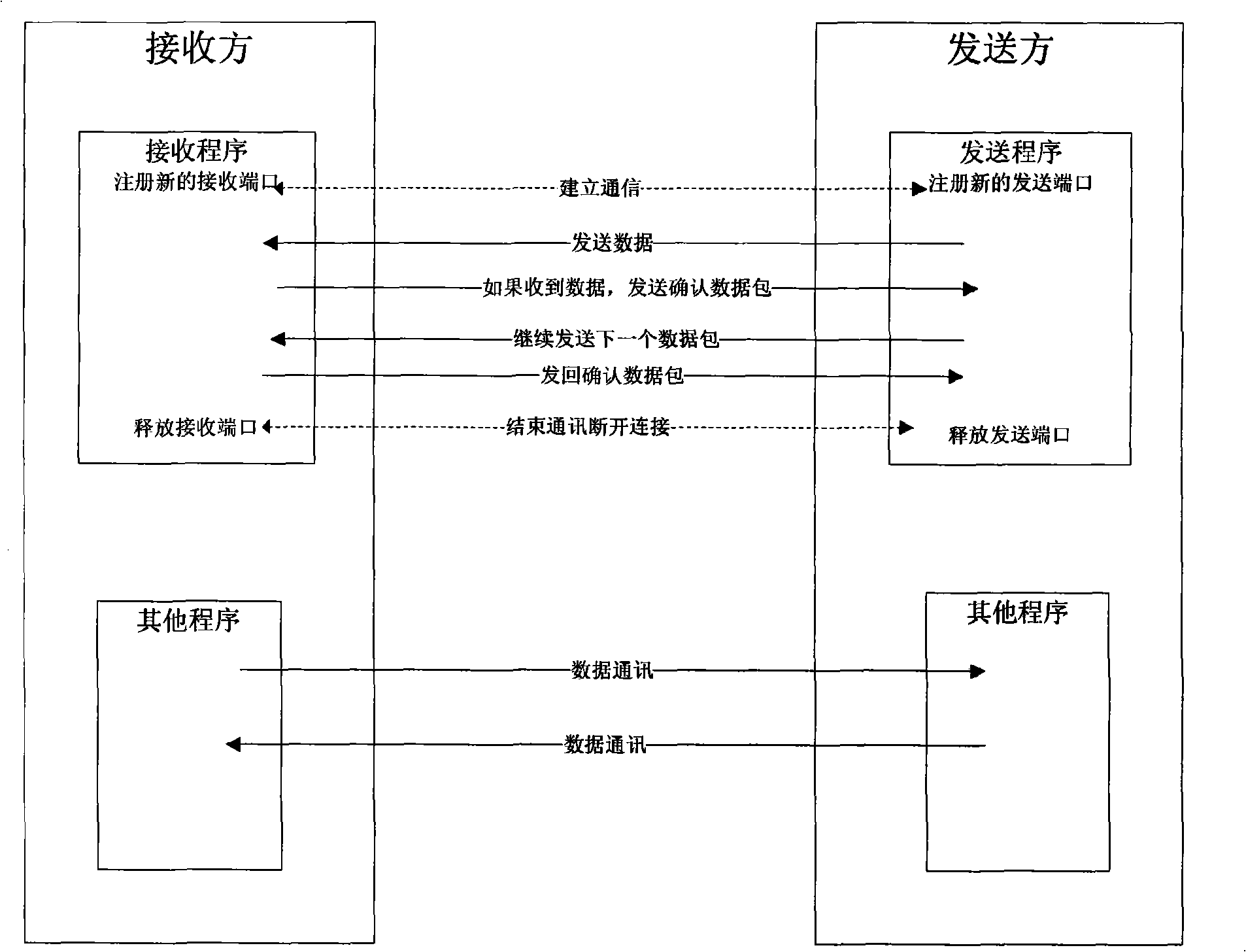
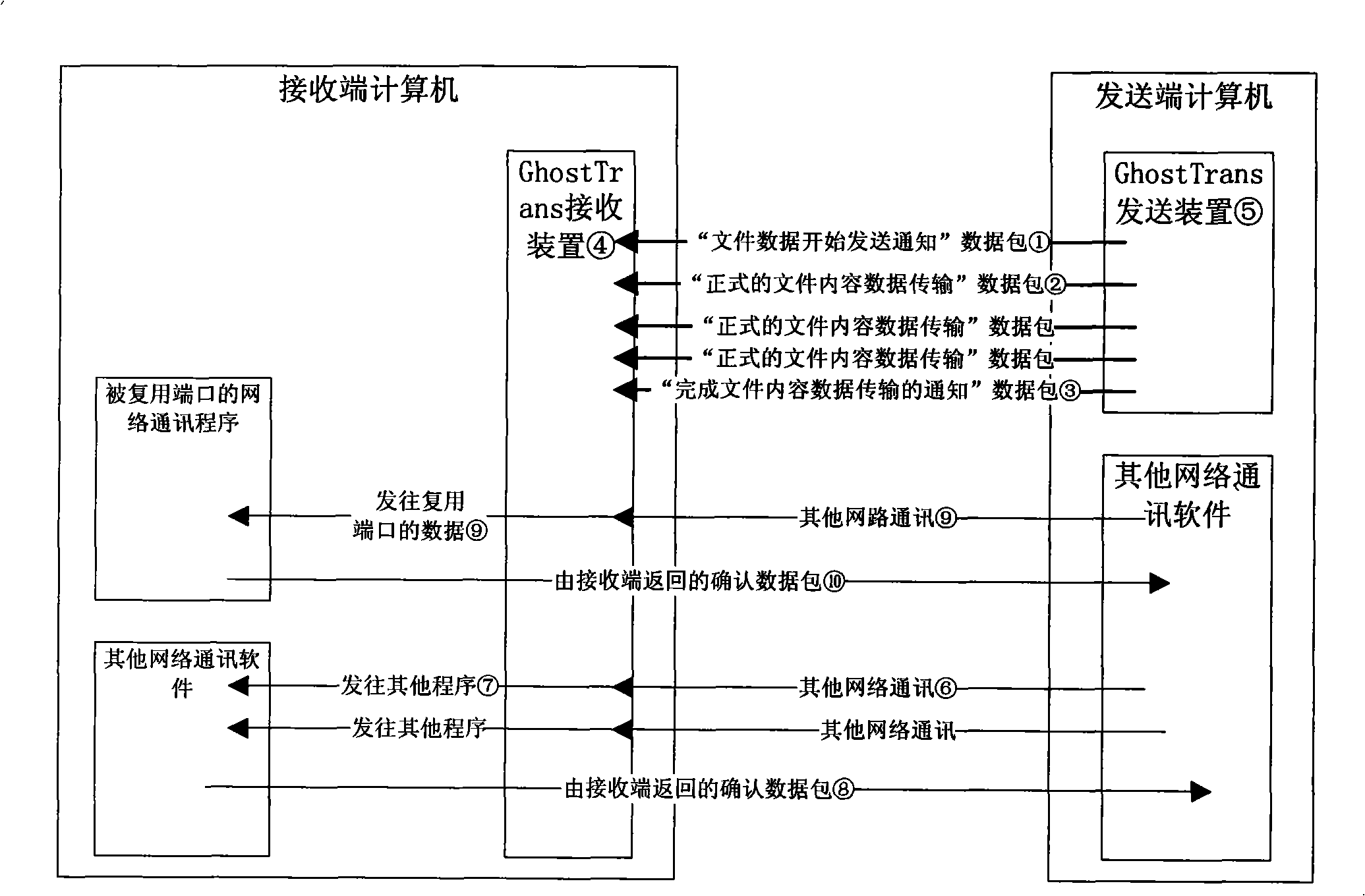
[0071] In this implementation process, the sender device sends a file to the receiver device, and the protocol uses the GhostTrans protocol as an example to illustrate the specific implementation of the device, such as image 3 structure diagram and Figure 4 Flow chart of sending data.
[0072] 1. Start the GhostTrans receiving device at the receiving end (such as image 3 Middle ④), the GhostTrans receiving end device starts to monitor all data packets that the receiving end computer receives, and this specific embodiment adopts the monitoring mode of the original socket technology, as Figure 4 shown.
[0073] 2. When sending files to the receiving end, start the GhostTrans sending device at the sending end (such as image 3 Middle ⑤). ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com