Network flow detection method
A detection method and network traffic technology, applied in the network field, can solve problems such as inflexible and comprehensive traffic control policy configuration, traffic fluctuations, blocked connections, etc., and achieve low network infrastructure and operating costs, balanced traffic, and effective bandwidth Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
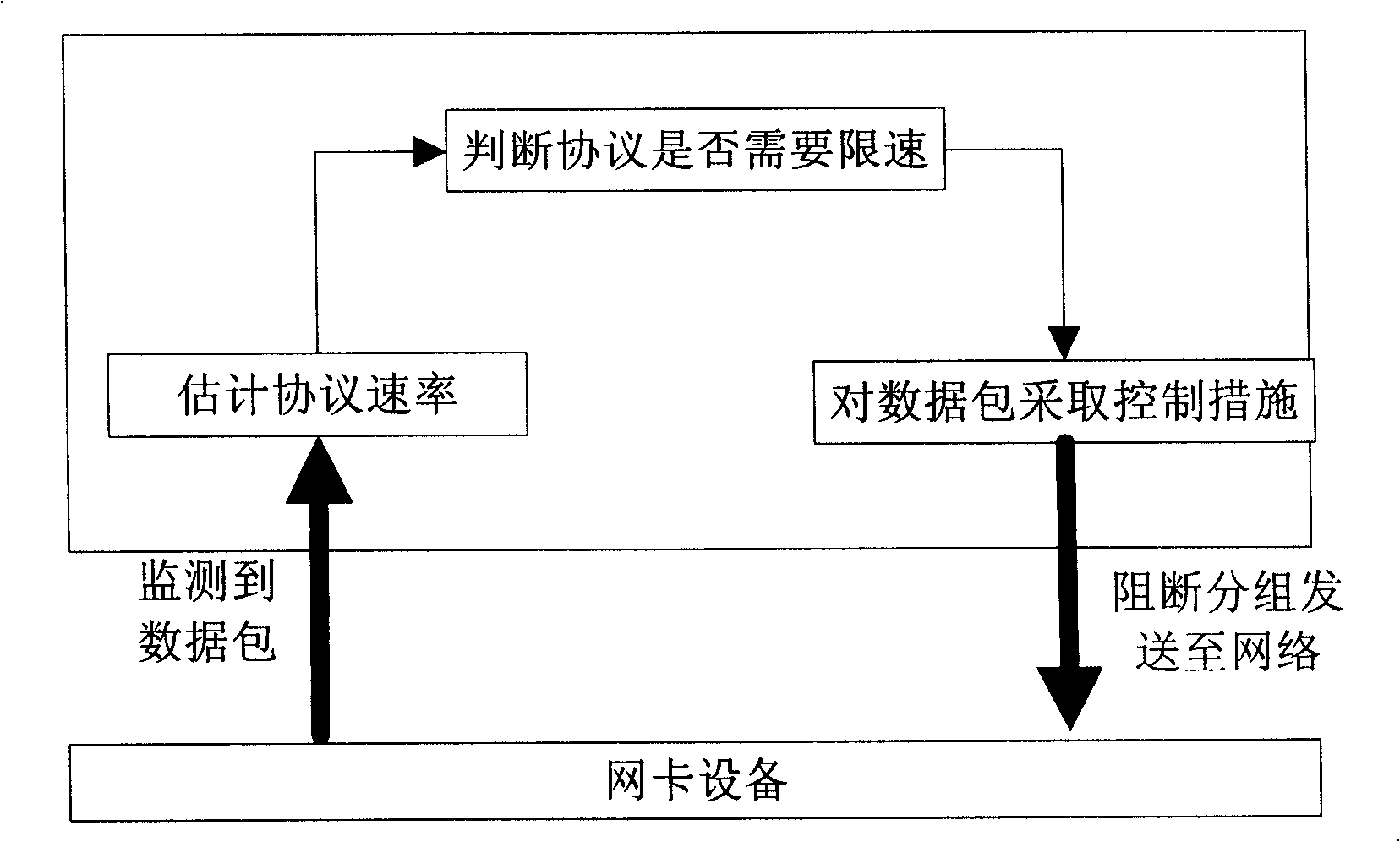
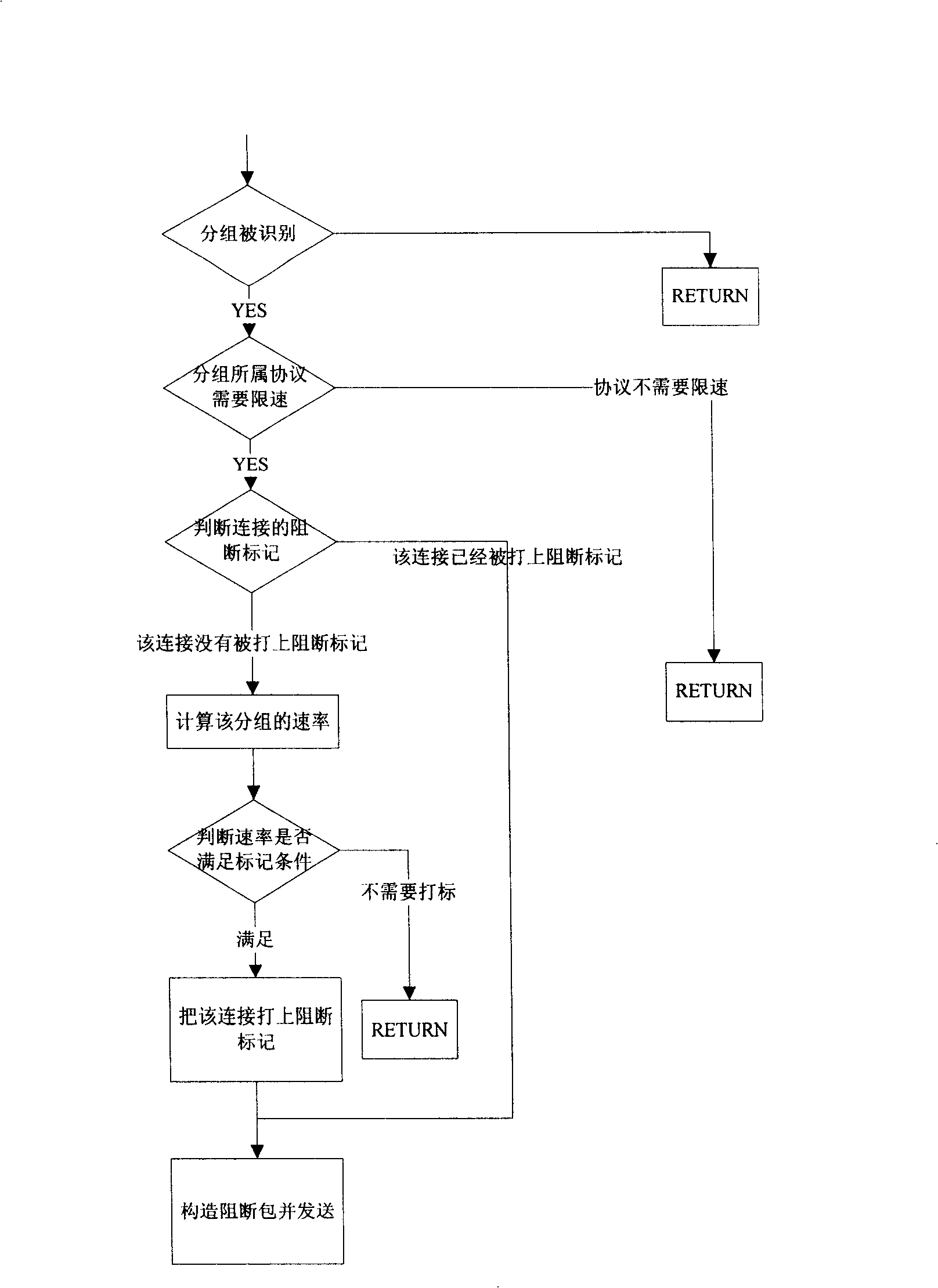
[0045] Before performing flow control, the user first determines the protocol that needs to be controlled. The control strategy can distinguish different protocols / applications, and can set the preset threshold of each protocol flow. The user can also set different preset thresholds in different time periods. Set thresholds for more efficient use of bandwidth. Protocol analysis is the premise of the present invention, but does not belong to the scope of the present invention. After the protocol has been identified, using the present invention can effectively and accurately control the protocol flow of the multi-connection feature.
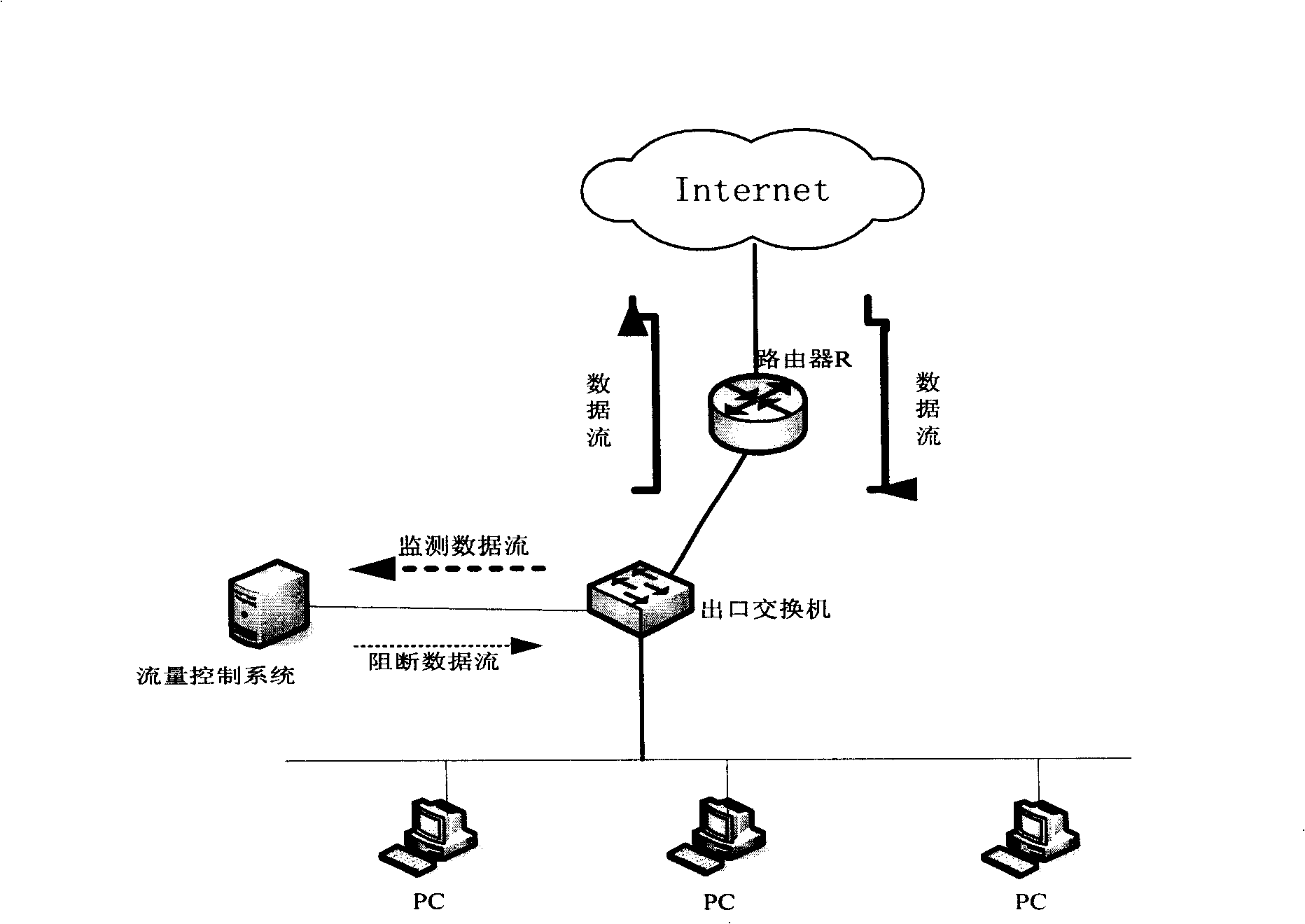
[0046] The flow control method of this embodiment adopts the bypass access mode, and its network topology is as follows figure 1 As shown, in the bypass access model, use the network monitoring equipment of this embodiment (ie figure 1 The flow control system in the network) is in the middle of the internal / external network, but is independent of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com