Method for implementing backup and switch of IPSec tunnel, system and node equipment, networking architecture
A node device and tunnel technology, applied in the field of secure transmission, can solve the problems of reducing network availability, high limitations, and low cost, and achieve the effects of shortening service interruption time, improving availability, and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Specific embodiments of the present invention will be described in detail below. It should be noted that the embodiments described here are for illustration only, and are not intended to limit the present invention.
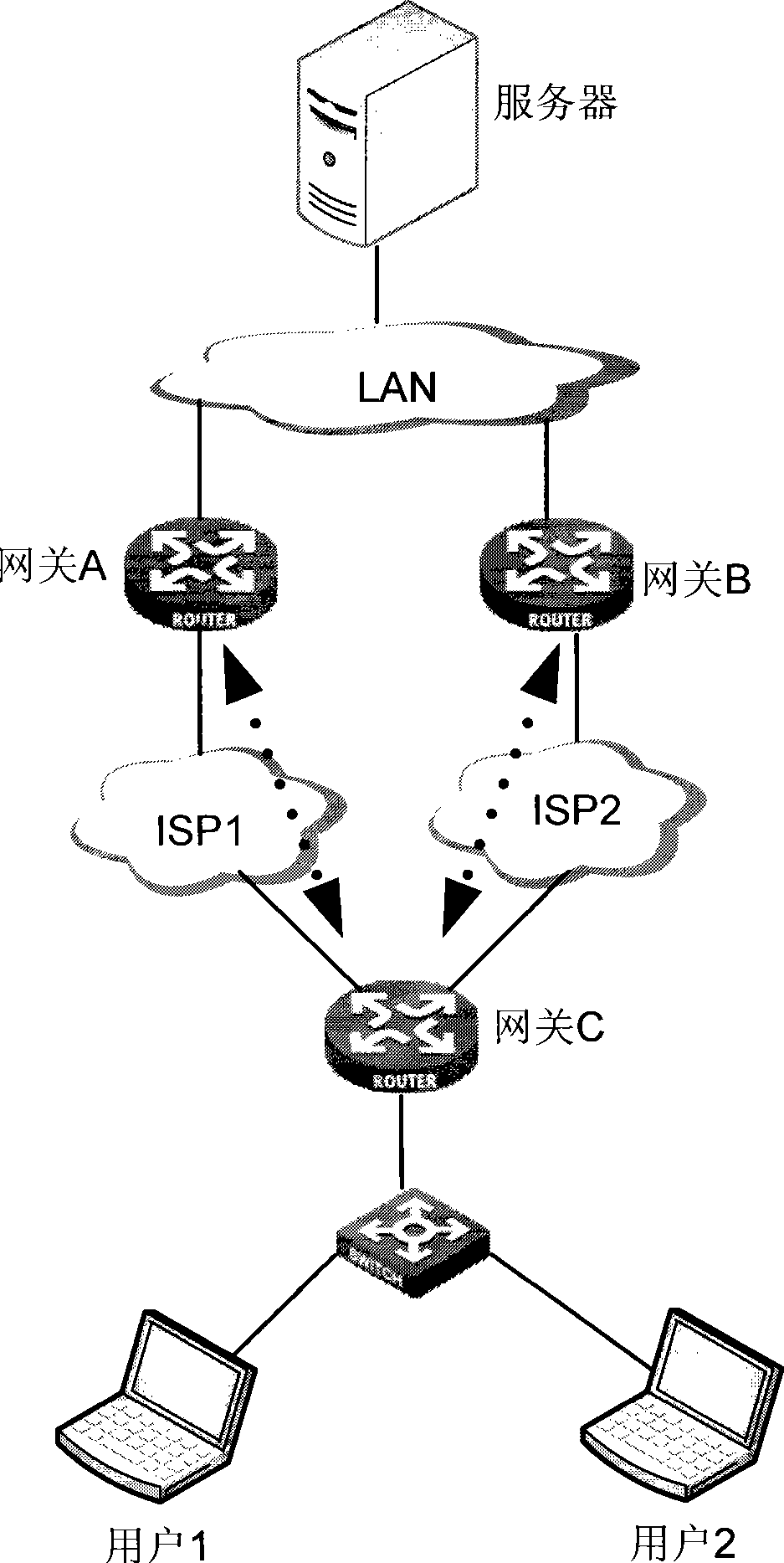
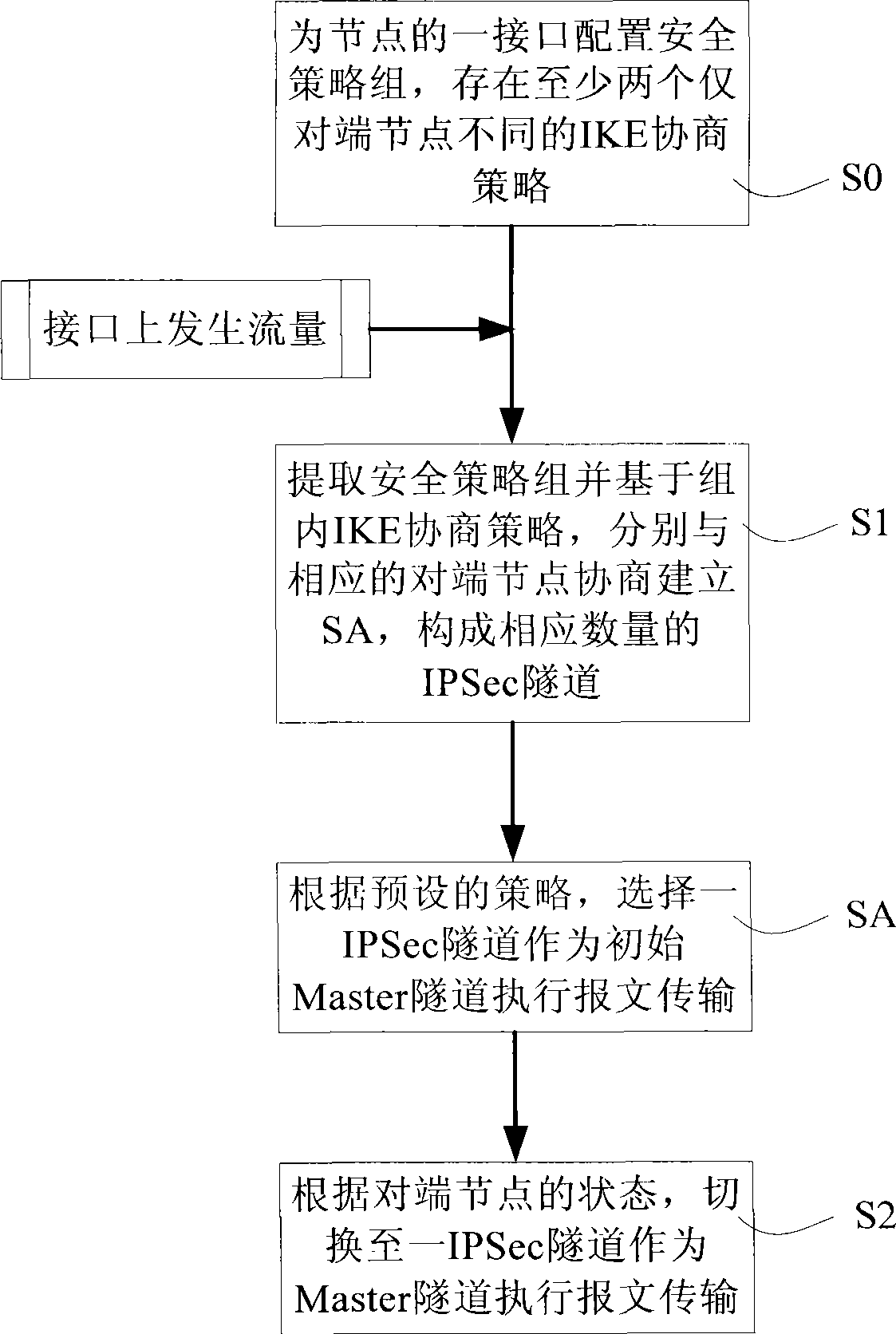
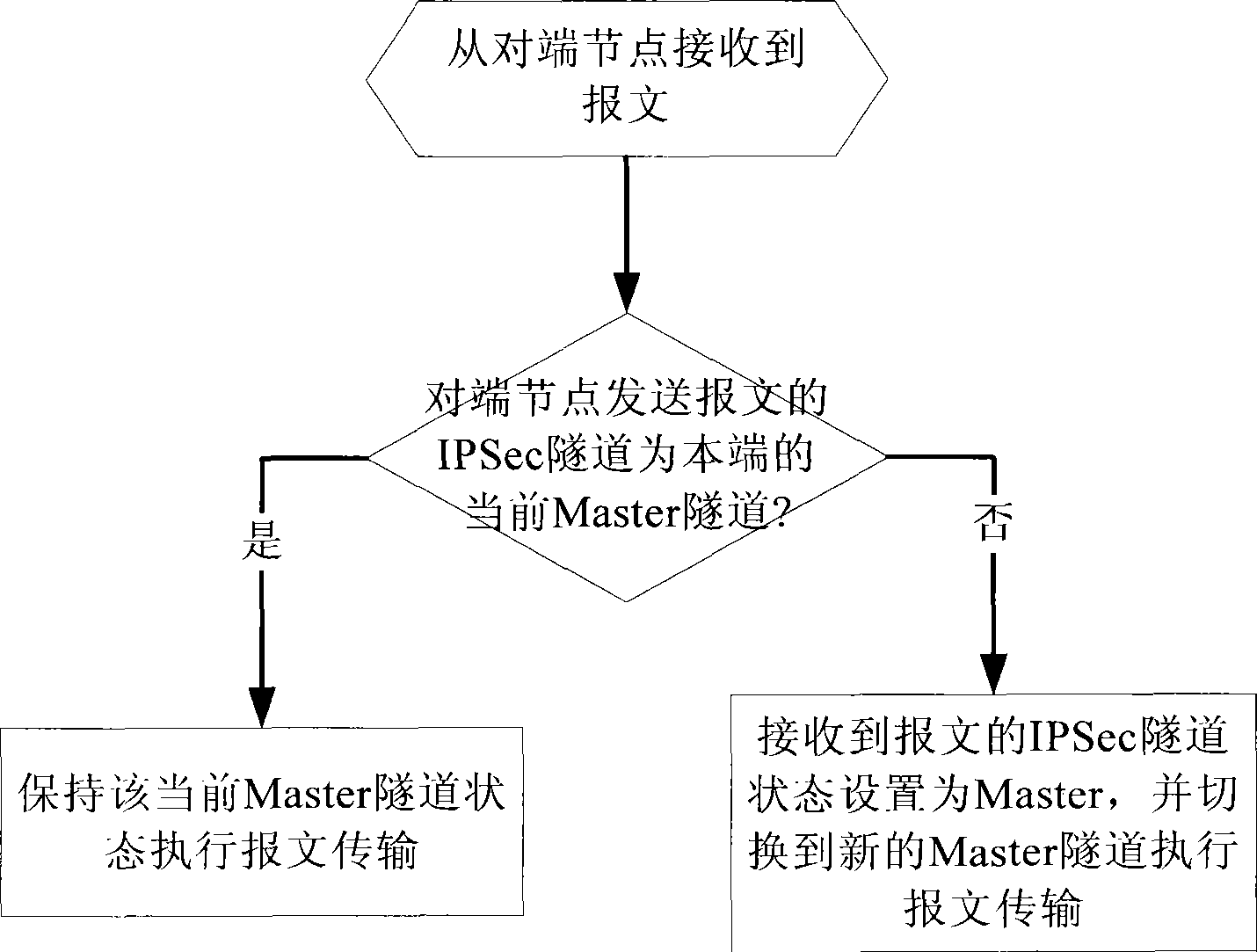
[0039] The main idea of the present invention is to realize the backup of multiple IPSec tunnels based on a single link for the same interface and the same flow, so as to overcome the difference in the prior art that a certain destination node has to be accessed through two or more links respectively. Access devices (such as gateways, routing devices, etc.) to implement IPSec tunnel backup have problems of high cost and switching interruption. The technical solution for realizing IPSec tunnel backup and switching provided by the present invention will be introduced in detail below.
[0040] First, please refer to figure 2 , showing the flow chart of an embodiment of the method for realizing IPSec tunnel backup and switching in the present invention, i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com