Marginal probability packet marking method based on digital signature technology of combined public key
A technology of digital signature and edge probability, applied in digital transmission system, public key of secure communication, data exchange network, etc. Robustness and other issues to achieve security assurance, fast positioning speed, and reduce system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
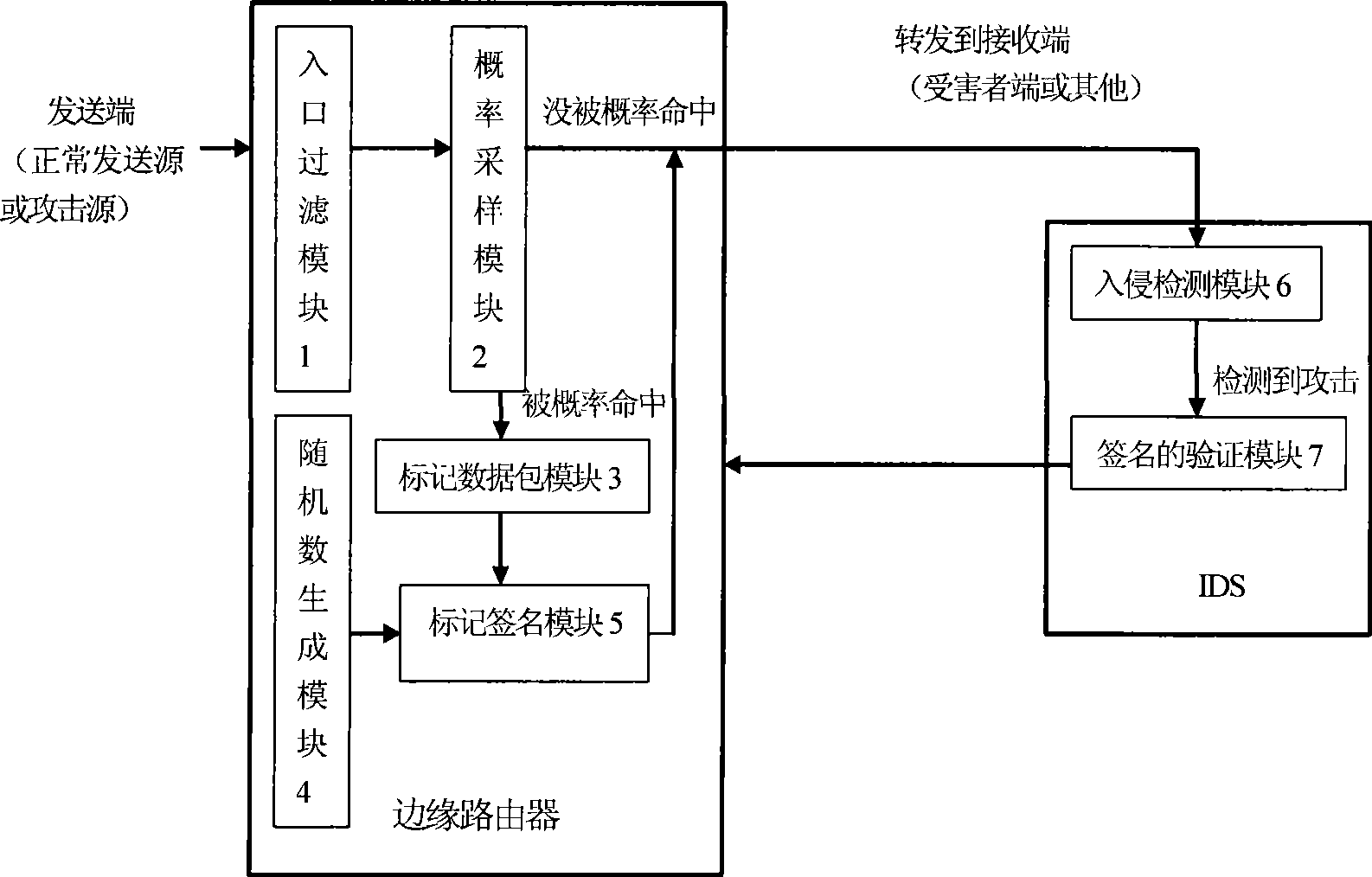
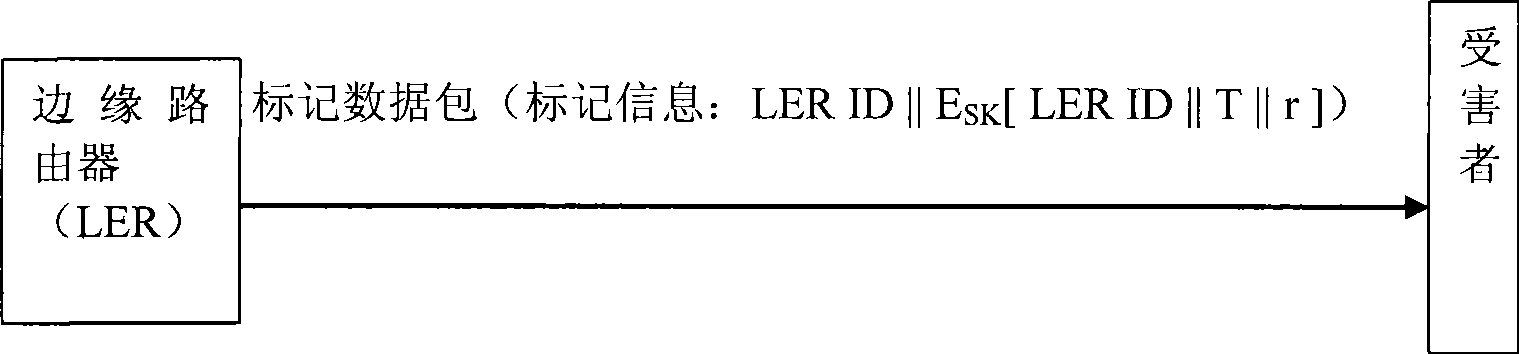
[0024] refer to figure 1 , figure 2 . figure 1 It is a principle block diagram of an embodiment of marginal probability packet marking based on combined public key signature technology in the present invention. It includes an ingress filter module 1, a probability sampling module 2, a marked data packet module 3, a random number generation module 4, a marked signature module 5, an intrusion detection module 6, and a signature verification module 7. Examples of figure 1 Connection lines shown. The present invention comprises steps:
[0025] ①When the data packet sent by the user terminal enters the edge router, the edge router filters the tag field of the data packet. If a forged tag field is found, the tag field is corrected to the initial default value of all '0', otherwise the '0' is not cleared. 'processing, embodiment step ① by figure 1 The ingress filtering module in 1 is complete. The ingress filtering module 1 completes the filtering function of the tag field of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com