TCP connection managing method for internet bypass monitoring system
A monitoring system and Internet technology, applied in the field of network security, can solve problems such as the complexity of timer management, and achieve the effect of guaranteed analysis and processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
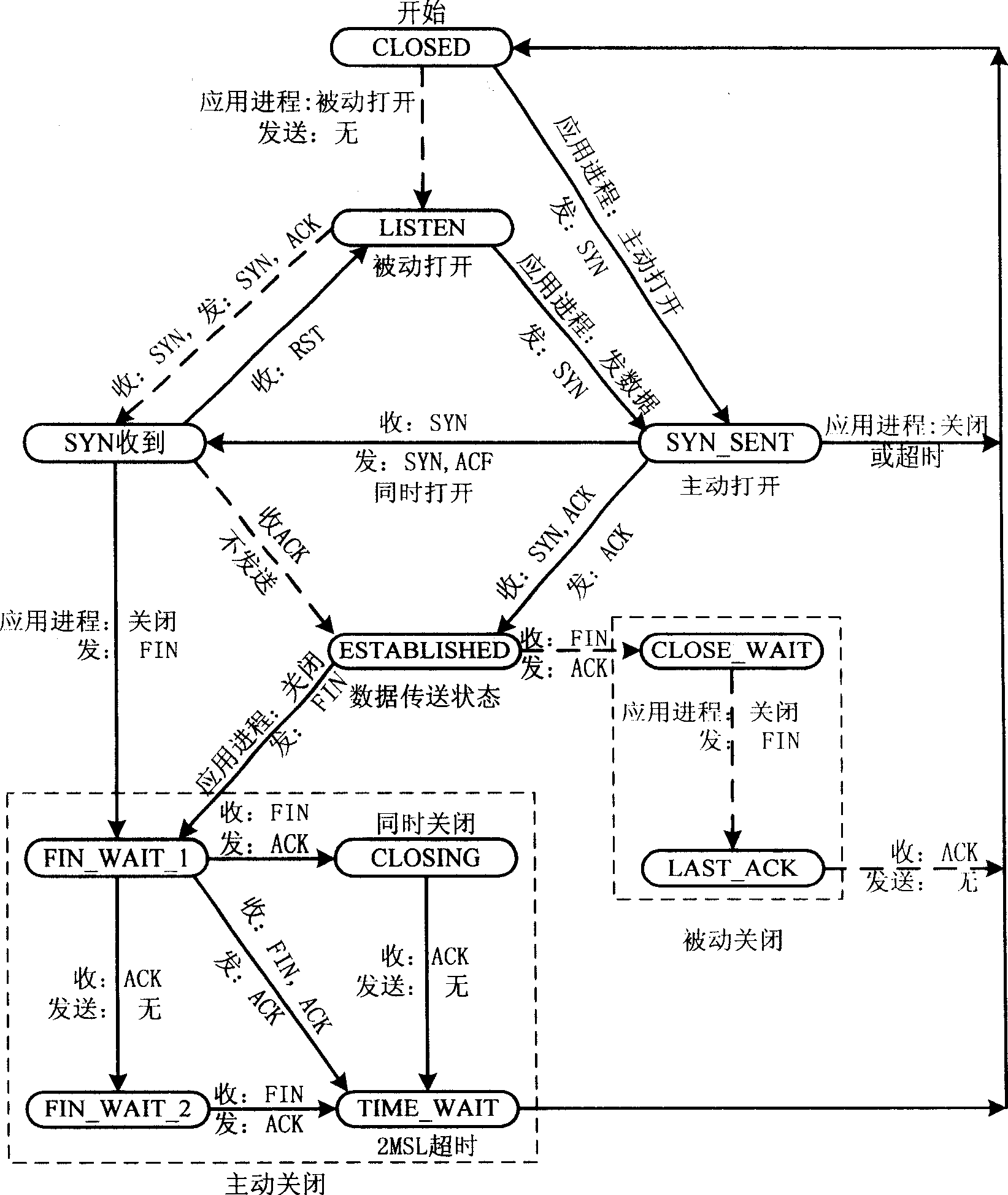
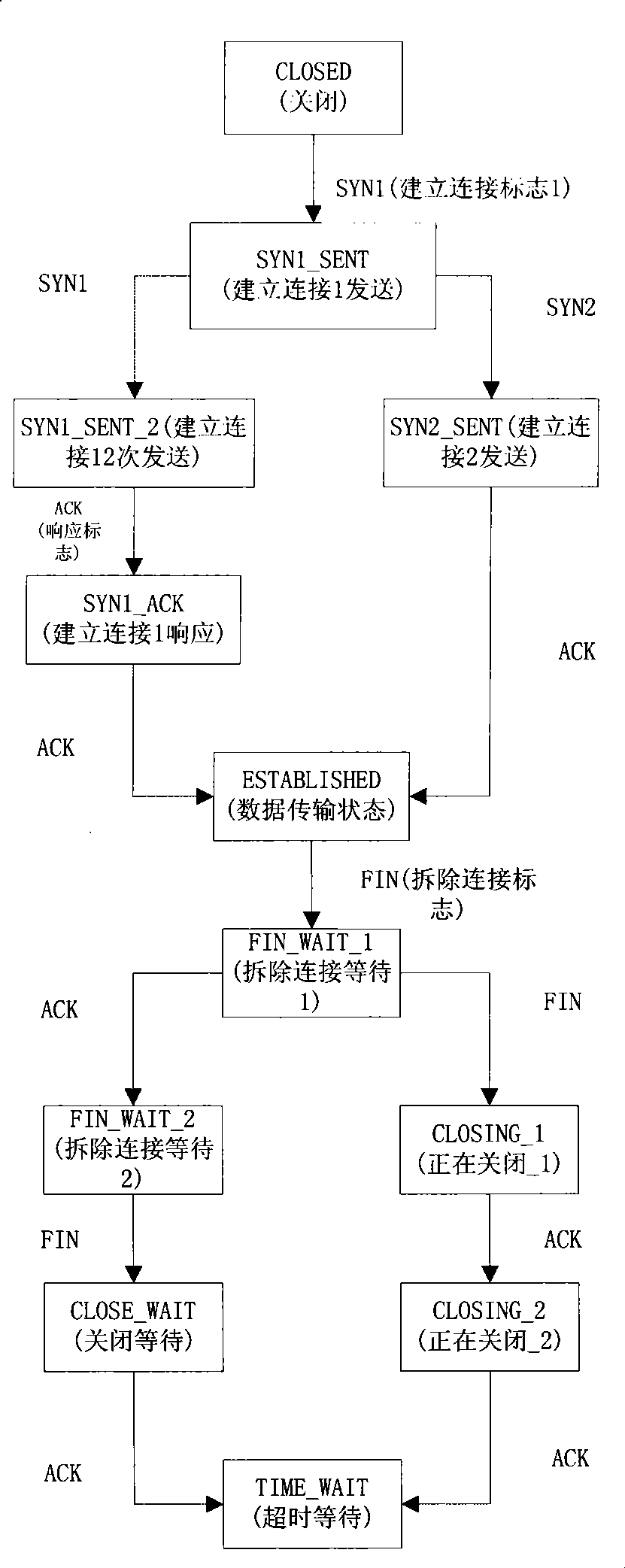
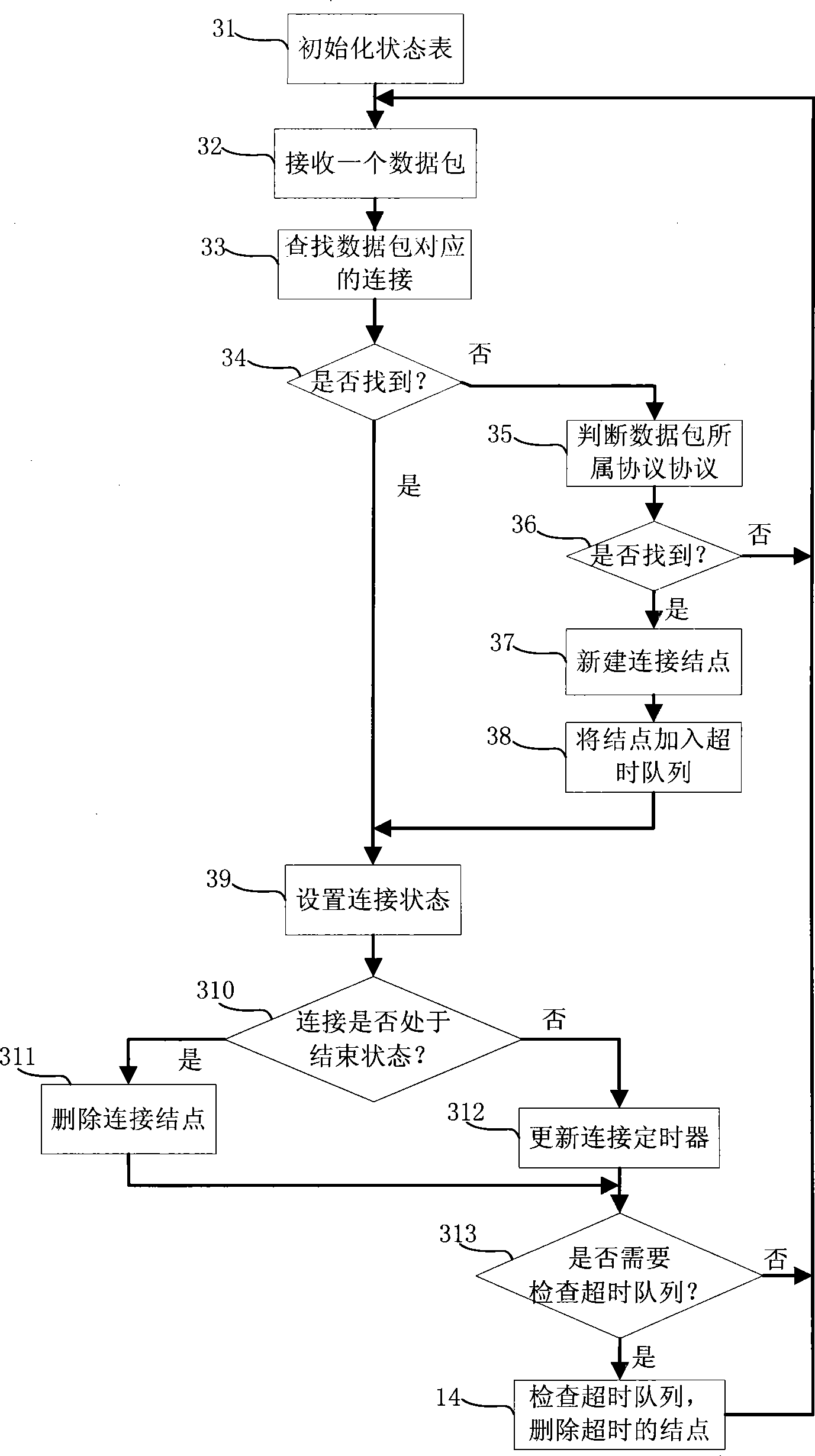
[0034] The embodiment of the present invention is a TCP connection management method of an Internet bypass monitoring system, and the method specifically includes the following processing steps:
[0035] After the monitoring system is initialized, the data packet is received, and the connection node corresponding to the data packet is searched according to the data packet;
[0036] If the connection node corresponding to the data packet is found, the connection state of the node is set; if the connection node corresponding to the data packet is not found, the application layer data processing is carried out, and the result is found according to the processing result. The application layer protocol to which the data packet belongs to establish a connection node, and add the established connection node to the timeout queue;
[0037] Set and check the connection status of the node. If the connection status changes to the end state, delete the connection node and update the timeou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com