Service identification method and system
A service identification and server technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problems of multiple false alarms, achieve the effect of reducing false alarms, reducing the rate of false alarms, and solving false alarms and performance problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
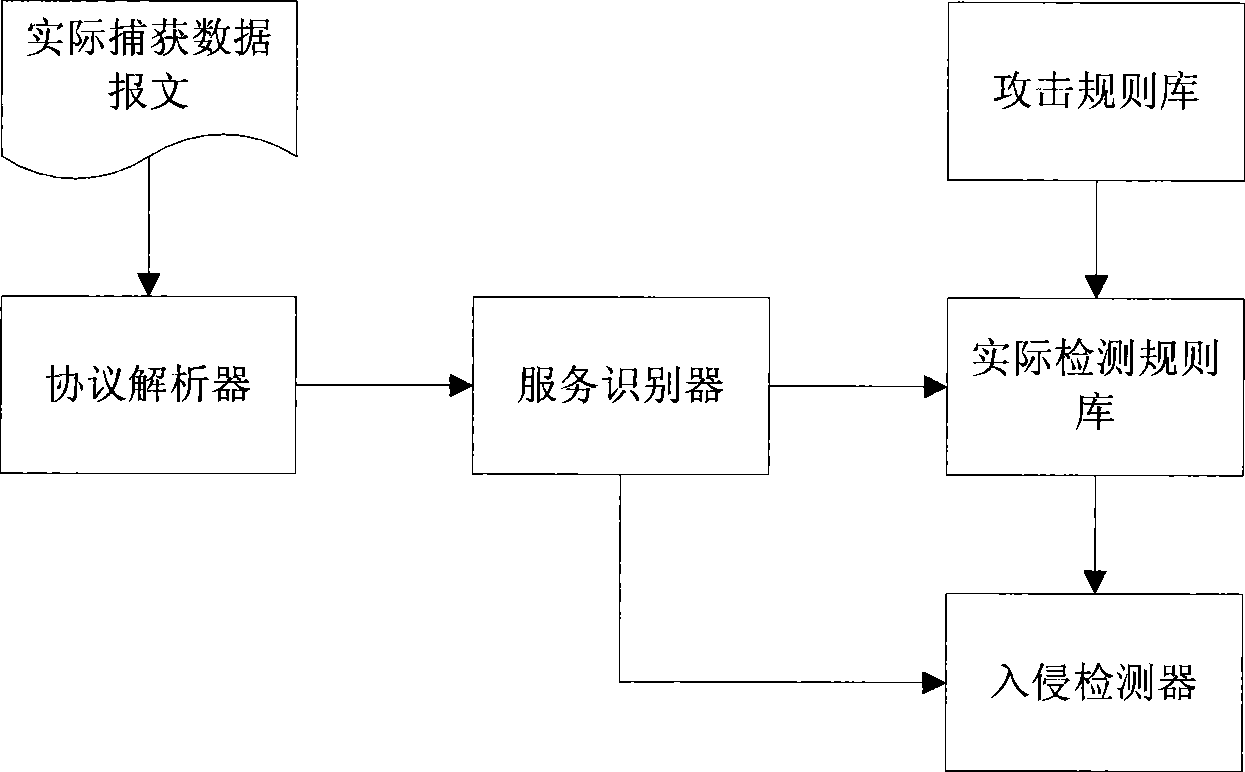
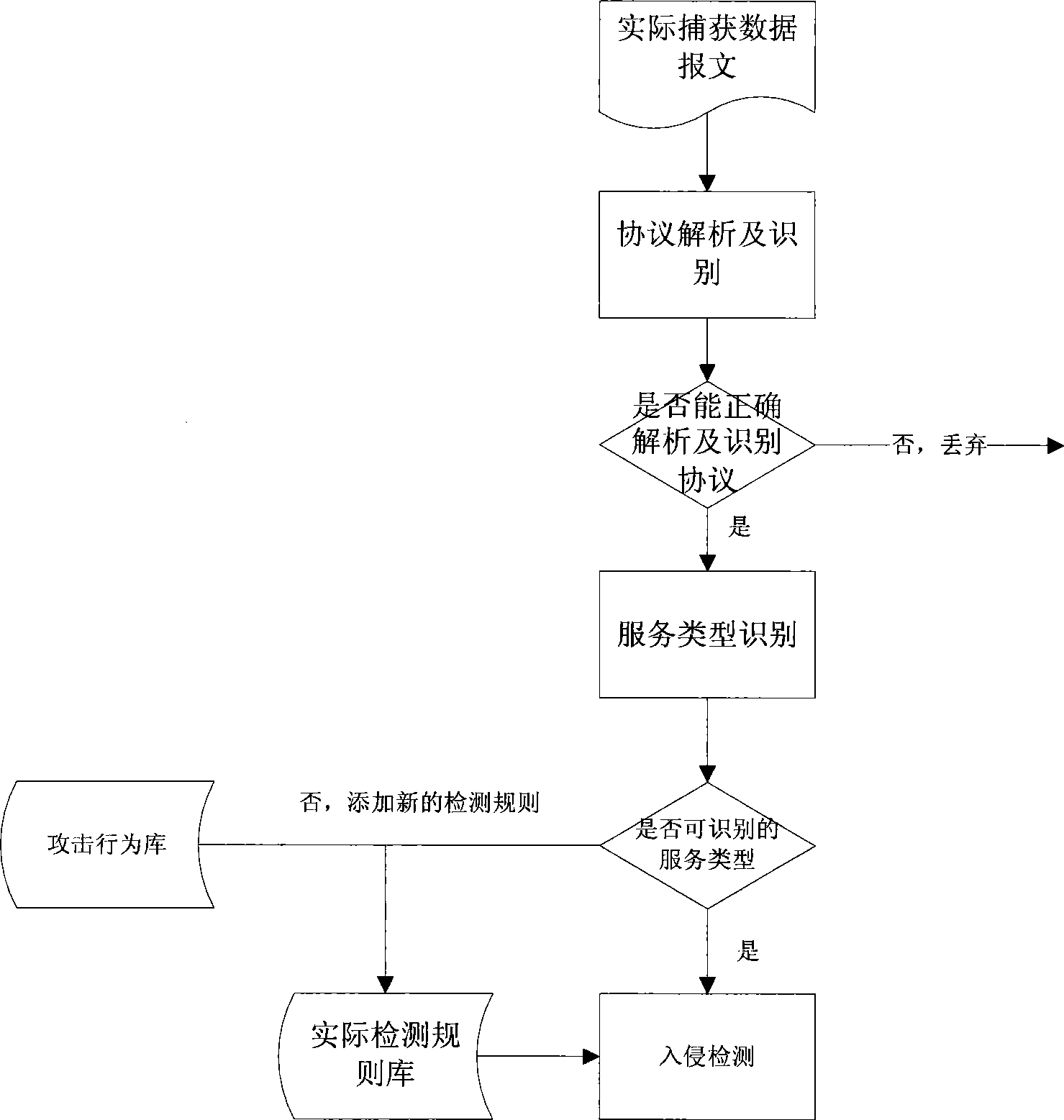
[0022] This embodiment is a basic mode of a service identification method and system for intrusion detection, and its basic structure is as follows figure 1 shown. Including protocol parser, service identifier, attack signature library, actual detection rule library and intrusion detector, the system workflow is as follows: figure 2 Shown:
[0023] A method for service identification for intrusion detection, the steps of which include,
[0024] ① Steps of protocol identification. Protocol identification includes hierarchical analysis of datagrams, based on the actual captured datagrams, port characteristics, protocol static message characteristics and behavior characteristics to identify the actual protocol used and output the analysis results as the basis for the service identification step.
[0025] ② Steps of service identification. The step of service identification depends on the output data result of the protocol identification to identify the type of the actual pro...
Embodiment 2
[0029] This embodiment is a preferred solution of the protocol identification step in Embodiment 1:
[0030] ①Using the hierarchical data packet protocol analysis method to obtain the data packets captured by the packet capture function, then perform protocol analysis and protocol restoration work as a sub-step of protocol tree establishment;
[0031] ②The unstructured data stream at the lowest level is taken as the root node, and the protocols with the same parent node become sibling nodes, and the protocol signature is used to identify the protocol as a sub-step of protocol analysis.
[0032] The basic idea of this embodiment is: protocol identification includes a protocol tree module and a protocol analysis module. Due to the 7-layer protocol model of OSI, protocol data is encapsulated and sent from top to bottom. Protocol analysis needs to be done from the bottom up. Firstly, after identifying the protocol of the network layer, the package is restored, and then the pro...
Embodiment 3
[0034] This embodiment is a preferred solution of the service identification step in Embodiment 1:
[0035] ① From the data packet returned by the captured server, first determine the protocol type in the protocol identification step, and then perform keyword matching to obtain the server type;
[0036] ②The service identification module negotiates and resolves the server type with the intrusion detection engine, and maps it to a digital id recognized by both parties throughout the process, which facilitates the interaction of data and commands.
[0037] The basic idea of this embodiment is: first, perform corresponding keyword matching according to a specific protocol to obtain the server type. Then add the attack mode of attacking this type of server to the actual detection rule base. For example, for the http protocol, the main service extraction package is the server return package, and the matching feature key "server:" in the data message until the first line feed and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com