Credible electronic transaction method and transaction system
An electronic transaction and transaction technology, applied in the field of information security, can solve problems such as stealing user account/password information, man-in-the-middle attack, transaction fraud, etc., to prevent the leakage of sensitive transaction information, prevent man-in-the-middle attack, and prevent DNS hijacking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be described in more detail through specific embodiments below in conjunction with the accompanying drawings.
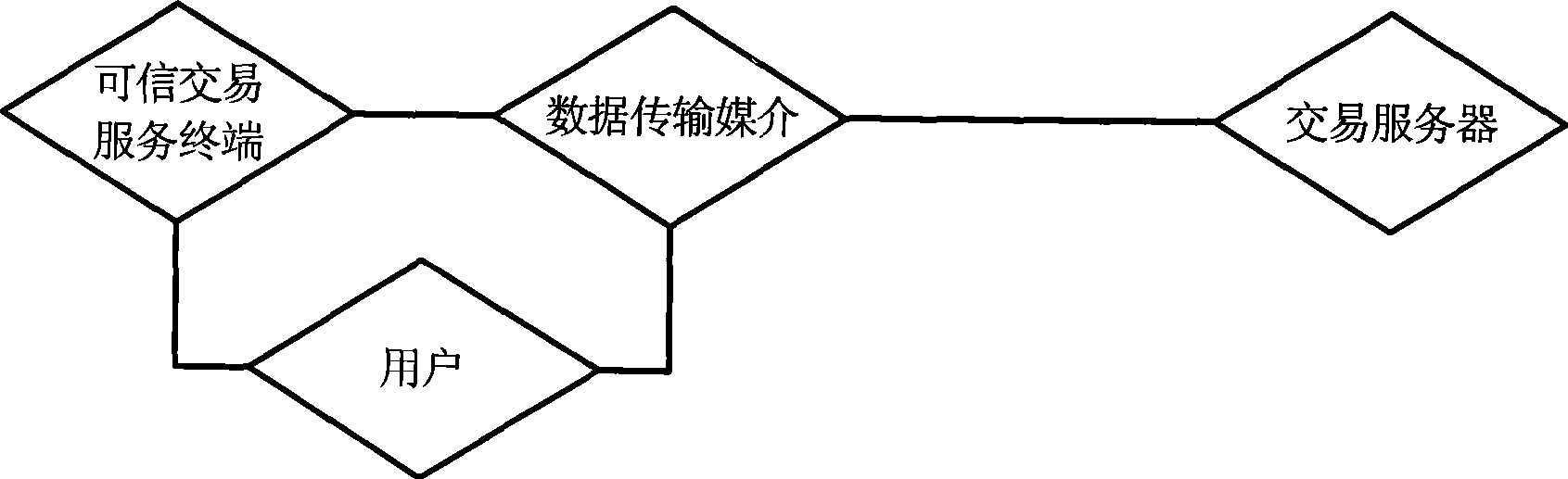
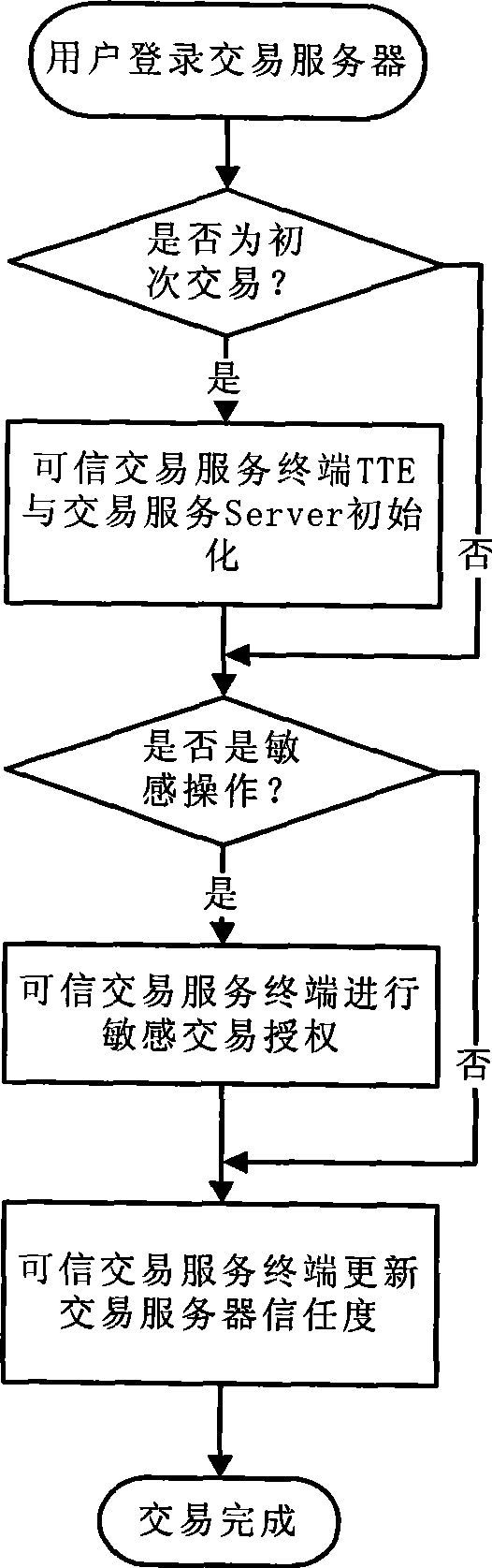
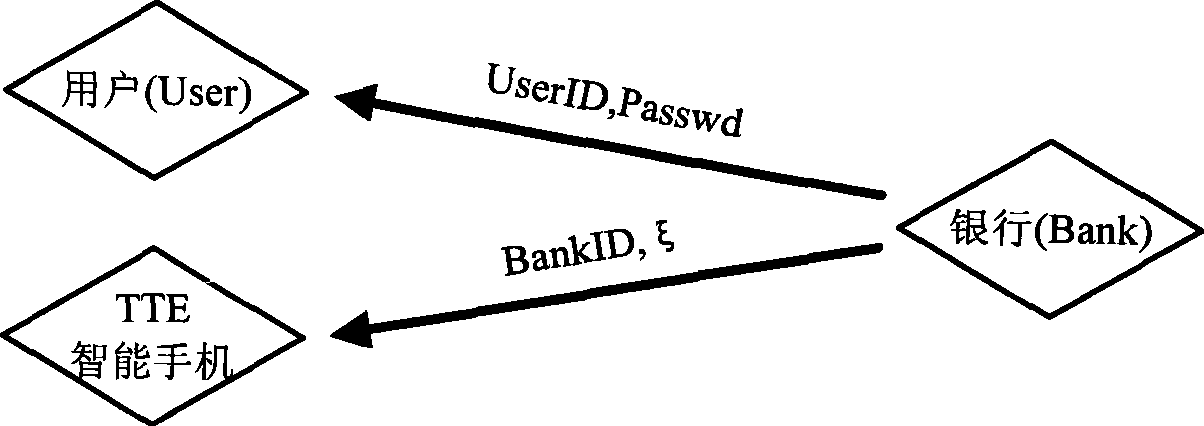
[0053] This embodiment provides a trusted electronic transaction method and a transaction system thereof. The transaction system adopts a mobile phone with a cryptographic operation unit and supports bluetooth as a trusted transaction service terminal. The online banking server acts as a transaction server. A personal computer is installed with a web browser and has access to the Internet in order to log on to the online banking website. Transaction operations involve: business browsing (Browser), account inquiry (Check), payment (Pay), transfer (Virement). Among them, the sensitivity level of "business browsing" is 1, which is considered as a general transaction; the sensitivity level of "account query" is 2, the sensitivity level of "payment" is 3, and the sensitivity level of "transfer" is 3. Transactions with a sensitivity leve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com