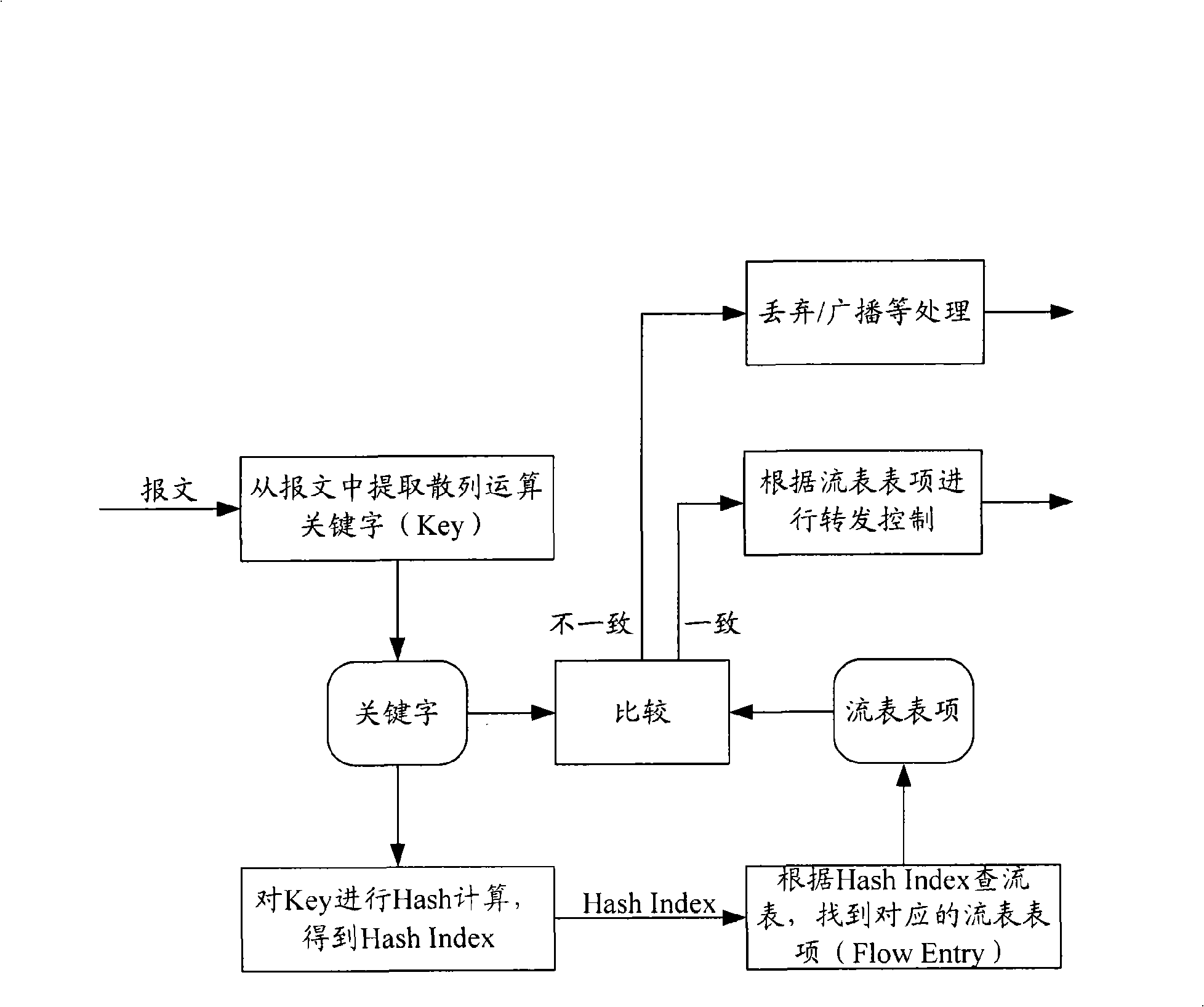
Flow stream searching method and device
A flow table and lookup table technology, applied in the field of data communication, can solve problems such as low search speed, affecting message forwarding performance, and insufficient access speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
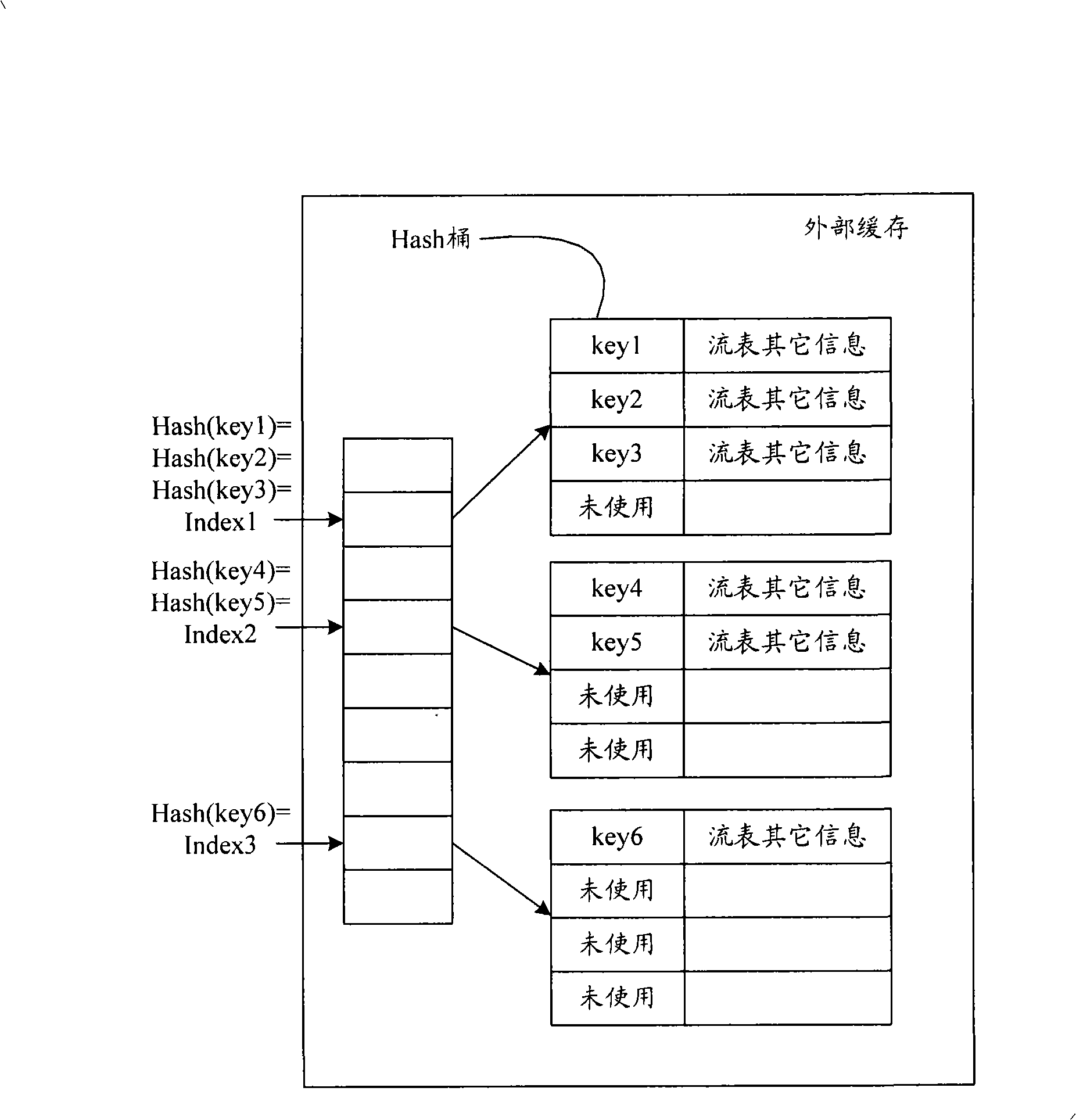
[0067] Using the solution in Embodiment 1 may generate Hash conflicts. Suppose there is Hash(key3)=Index1, and the Hash bucket corresponding to Index1 is full and cannot accommodate the flow table entry of key3, then key3 is a conflicting key. One solution is to adjust the height of the hash bucket to accommodate more entries. However, when adjusting the height of the bucket, all hash buckets need to be adjusted in the same way, which will reduce the utilization of the hash bucket.
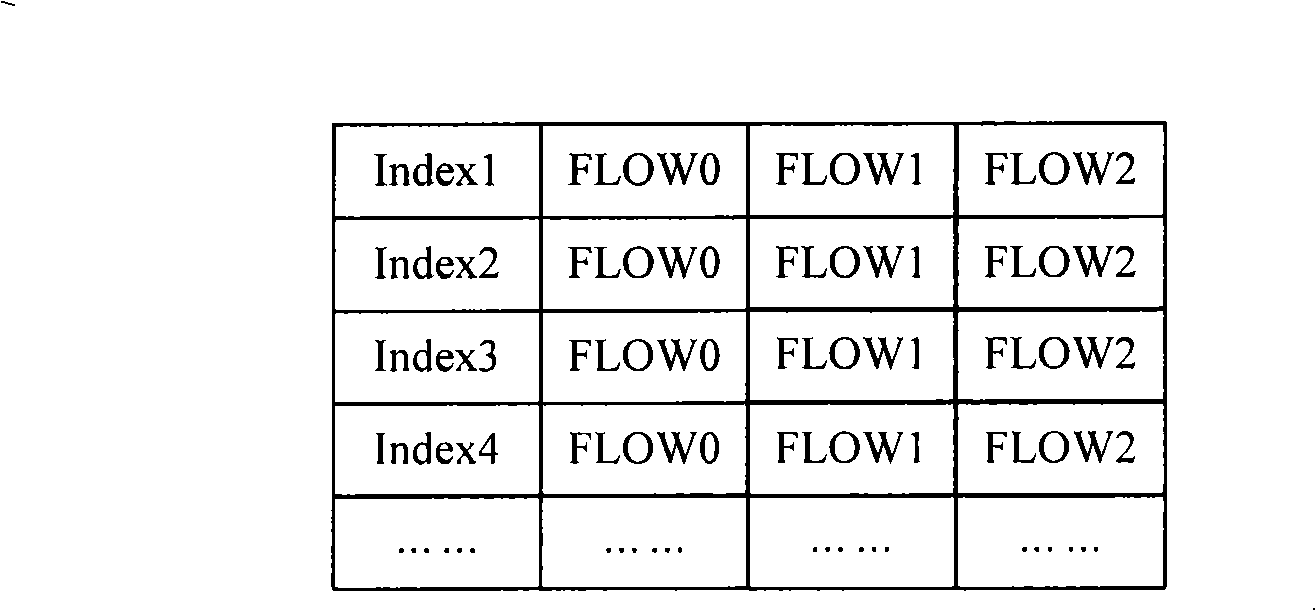
[0068] For this reason, Embodiment 2 of the present invention proposes a multi-level Hash flow table search method, which not only solves the above-mentioned possible Hash conflicts, but also effectively utilizes the remaining space of the Hash bucket. In this embodiment, for using the same Hash function to map more keywords to the same Index value, and the number of more keywords is greater than the depth of the Hash bucket, the more keywords are divided into at least two parts, different parts ...
Embodiment 3
[0095] Considering that there will still be a small probability of conflict events after the multi-level Hash in the above-mentioned embodiment two, such as Hash0(key8)=Index2, and Hash1(key8)=Index1, because the Hash buckets corresponding to Index1 and Index2 are full, thus A conflict arises. Although when the Hash depth is set to 8-16, the probability of conflicts is very small, but in order to further prevent conflicts, in the third embodiment of the present invention, a small standby Hash table is further set in the internal cache of the chip to solve this problem. conflict.
[0096] Figure 8 It is a schematic diagram of the standby Hash table in the third embodiment. For the key values that still conflict after multi-level Hash, use the alternate Hash function (denoted as Hash'(x)) different from Hash0(x) and Hash1(x) to perform Hash operation on these key values, and the obtained Hash index is recorded as Index h’ ; Use the standby Hash table to record the Index o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com