Safety virtualization method of trusted crypto module
A cryptographic module and virtualization technology, applied in computer security devices, software simulation/interpretation/simulation, instruments, etc., can solve the problem that a single physical TCM cannot meet the specific needs of multiple virtual machines for TCM.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
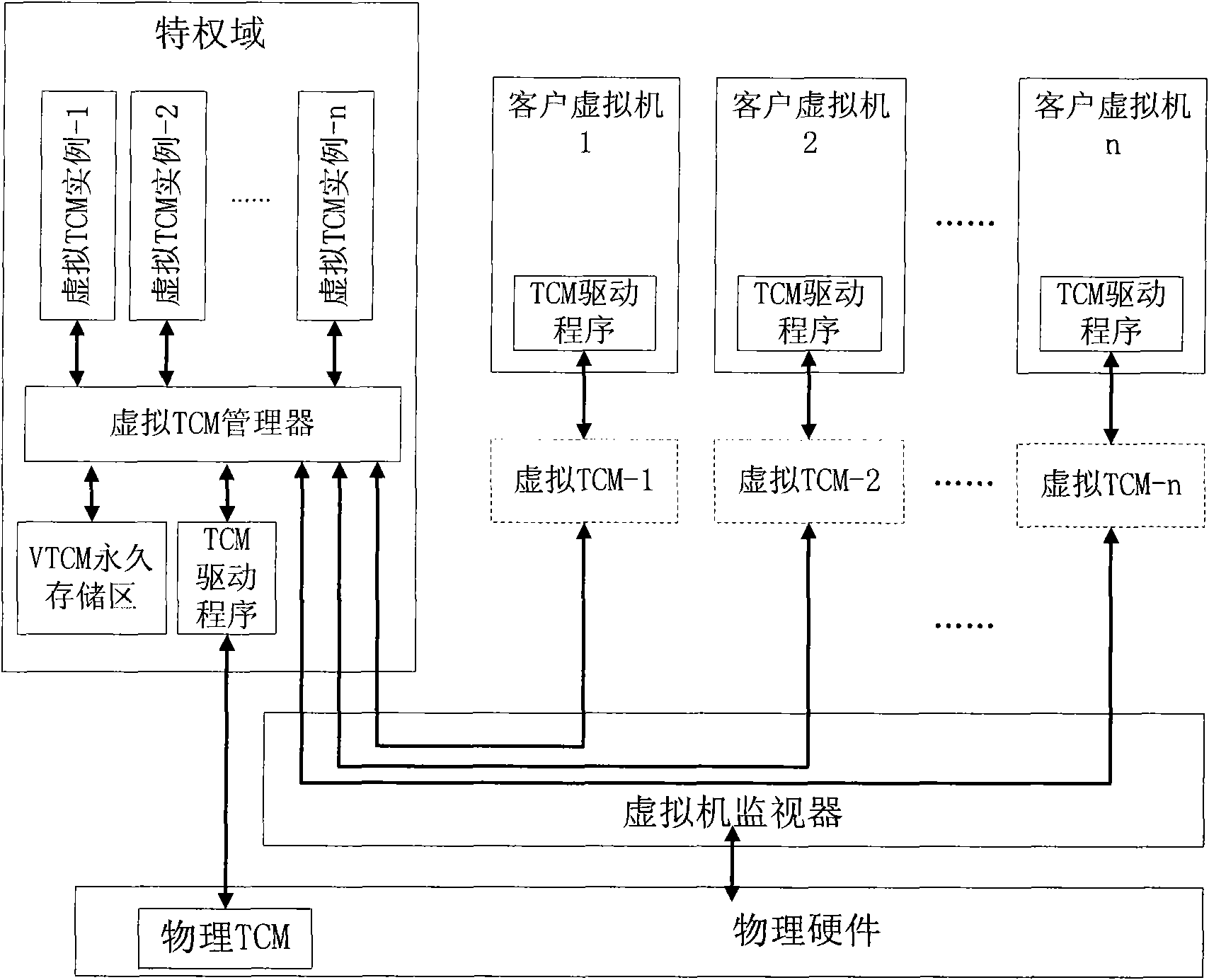
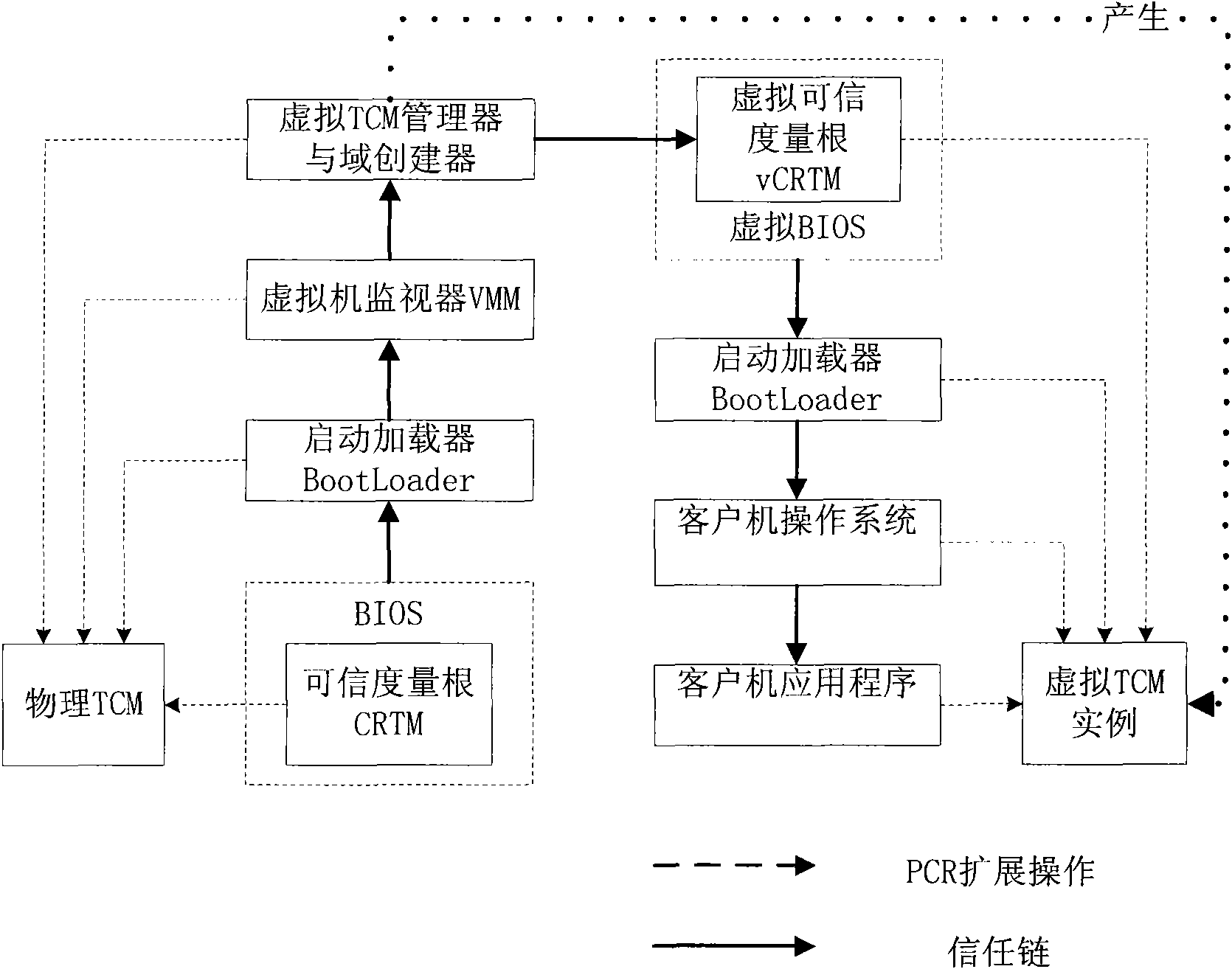
[0028] The technical solution of the trusted cryptographic module security virtualization method provided by the present invention is to implement a virtual TCM instance supporting the use of a client virtual machine on a virtual machine based on a VMM model, and establish a trust root from a physical machine to a virtual machine. The specific way of realizing the virtual TCM instance is as follows:
[0029] Set up a virtual TCM manager and a virtual TCM persistent storage area in the privileged virtual domain of the virtual machine;
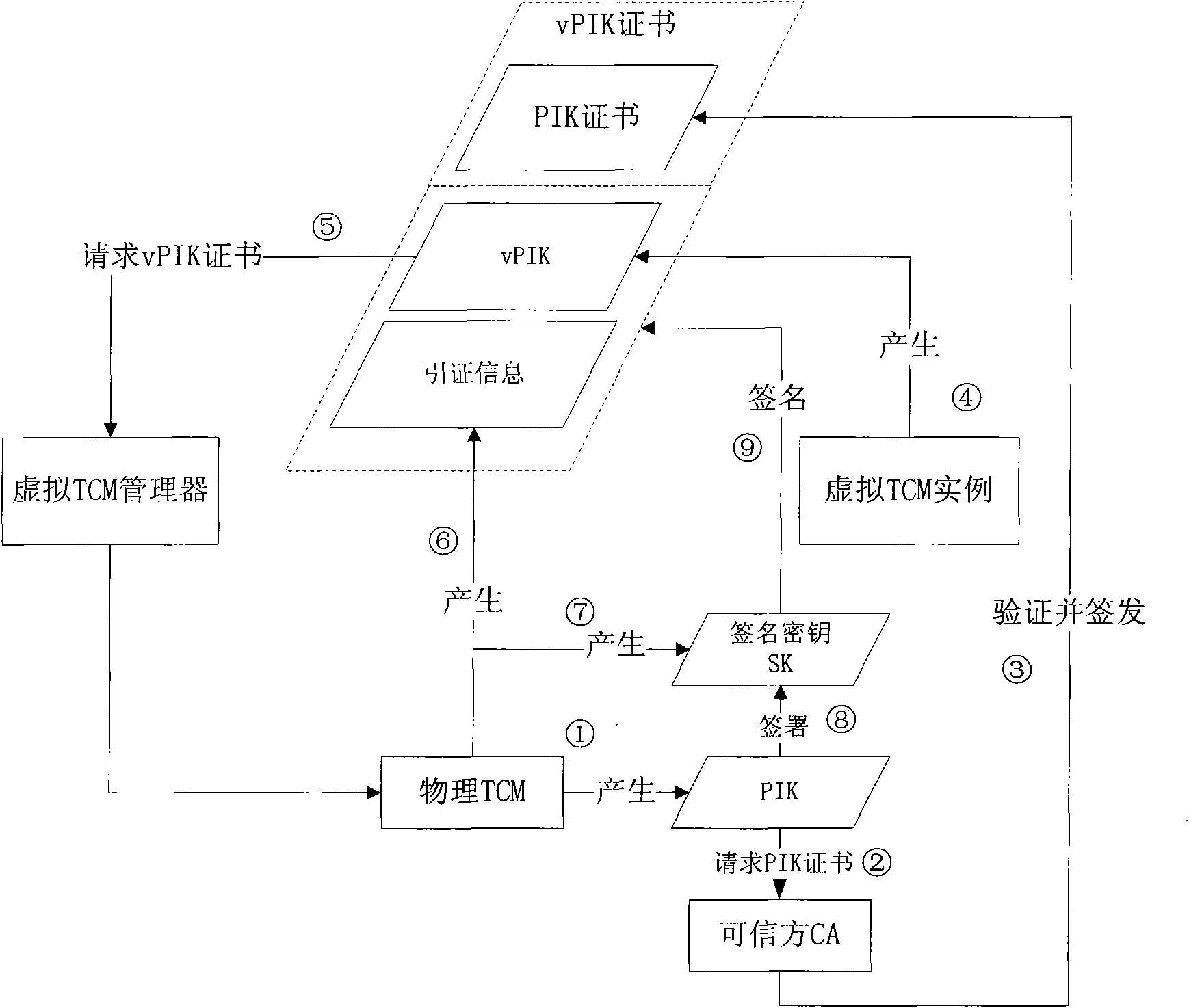
[0030] Create and manage a virtual TCM instance through the virtual TCM manager, the established virtual TCM instance simulates the physical TCM, and provides the function of the physical TCM (such as sealed storage, remote certification, key management) for the customer virtual machine; and through the virtual TCM manager Provide channels for communication between client virtual machines and virtual TCM instances, issue certificates for virtual...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com