Pseudo random sequence generation method based on t semi-order and sequence generator
A pseudo-random sequence and sequence generator technology, applied in the field of sequence cryptography, can solve problems such as inability to guarantee absolute reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
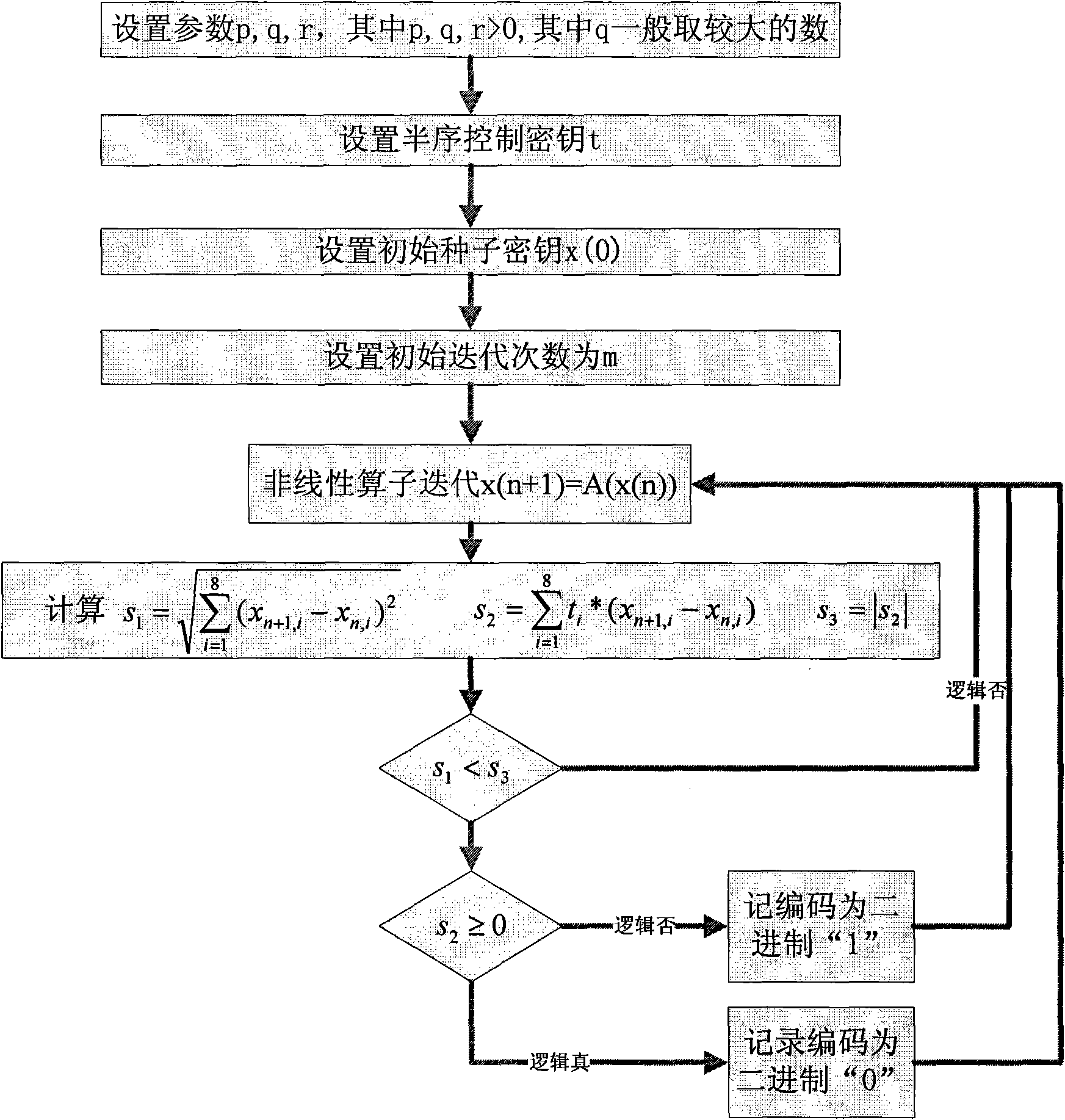
[0056] Below we give a specific example. The space we choose is R 8 , that is, when u=8, set:
[0057] x(n)=(x n,1 , x n,2 , x n,3 , x n,4 , x n,5 , x n,6 , x n,7 , x n,8 ), x n,i ∈R + .
[0058] The following nonlinear operator iteration is established: x(n+1)=A(x(n)), where:
[0059] x n+1,1 =|p.sin 2 (qx n,8 x n,1 -rx n,2 x n,2 )| (1.1)
[0060] x n+1,2 =|p.sin 2 (qx n,1 x n,2 -rx n,3 x n,3 )| (1.2)
[0061] x n+1,3 =|p.sin 2 (qx n,2 x n,3 -rx n,4 x n,4 )| (1.3)
[0062] x n+1,4 =|p.sin 2 (qx n,3 x n,3 -rx n,5 x n,5 )| (1.4)
[0063] x n+1,5 =|p.sin 2 (qx n,4 x n,5 -rx n,6 x n,6 )| (1.5)
[0064] x n+1,6 =|p.sin 2 (qx n,5 x n,6 -rx n,7 x n,7 )| (1.6)
[0065] x n+1,7 =|p.sin 2 (qx n,6 x n,7 -rx n,8 x n,8 )| (1.7)
[0066] x n+1,8 =|p.sin 2 (qx n,7 x n,8 -rx n,1 x n,1 )| (1.8)
[0067] (where p, q, r>0, where q generally takes a larger number)
[0068] Taking this form of operator is mainly to consider that ...
Embodiment 2
[0084] MATLAB Implementation Example of the Algorithm
[0085] According to the method of the present invention, the present embodiment combines a MATLAB example program for generating a binary stream of semi-sequential pseudo-random sequences to illustrate the establishment and work of the algorithm:
[0086] % Program 1: Generate Semi-Order Sequence Cipher Binary Stream Demonstration Program 1.0
[0087] t=[2.5, 3.2, 4, 1.2, 3, 5, 2.5, 4]; % semi-sequence control key
[0088] q = 2137; % parameter q
[0089] p=3.7; % parameter p
[0090] r=7; % parameter r
[0091] m=43; % initial iteration number
[0092] MAXSIZE=512; % length of binary sequence to be generated
[0093] % define initial seed key
[0094] x(1)=0.43;
[0095] x(2)=2.3;
[0096] x(3)=1.52;
[0097] x(4)=3.4;
[0098] x(5)=2.78;
[0099] x(6)=5.34;
[0100] x(7)=7.42;
[0101] x(8)=4.51;
[0102] y=[0, 0, 0, 0, 0, 0, 0, 0]; % define a temporary array to save the iteration result
[0103] z=[0, 0,...
application example 1-
[0146] Application example 1 - sequence cipher program based on semi-ordered random sequence
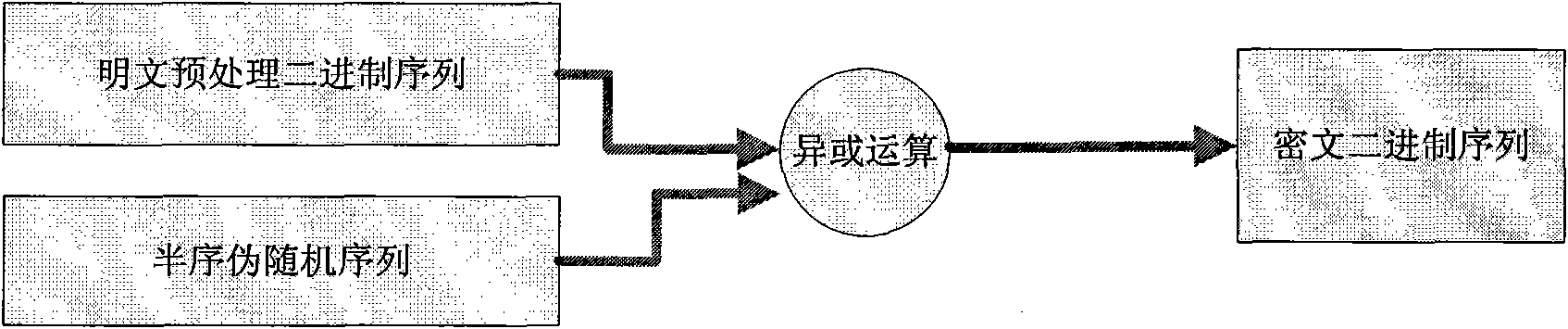
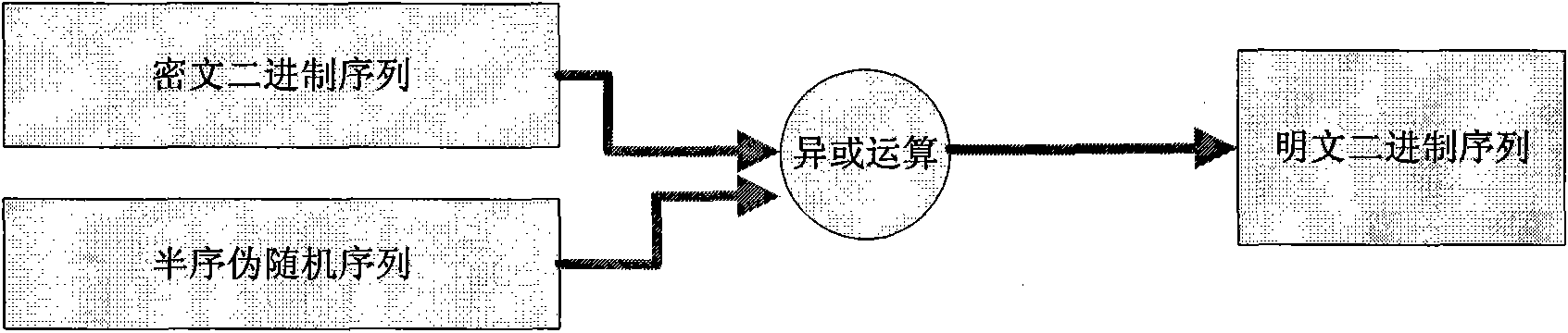
[0147] It is very simple to use the partial-sequence cipher algorithm, as long as the plaintext is pre-processed and encrypted to obtain the plaintext binary stream, and XOR operation is performed with the partial-sequence cipher binary stream (such as figure 1 shown). The decryption process only needs to perform an XOR operation with the semi-sequence cipher binary stream (such as figure 2 shown). The key of the algorithm is to obtain the semi-ordered pseudo-random sequence binary stream.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com