Electrical anti-misoperation locking system and anti-misoperation locking method based on iris identification
A technology of anti-mislocking and identity recognition, applied in character and pattern recognition, electrical components, circuit devices, etc., can solve problems such as easy loss, inability to control and record illegal operators, poor password storage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
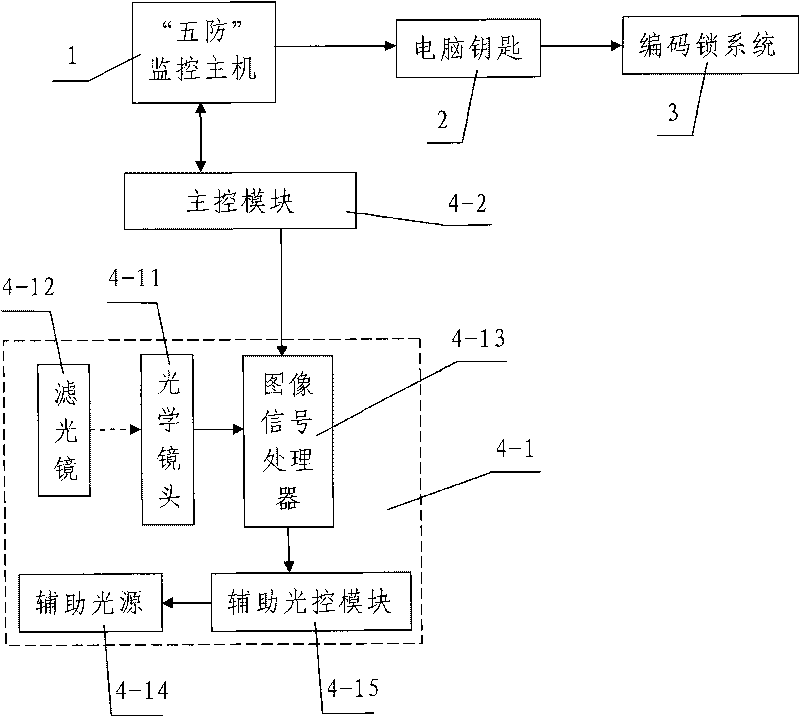
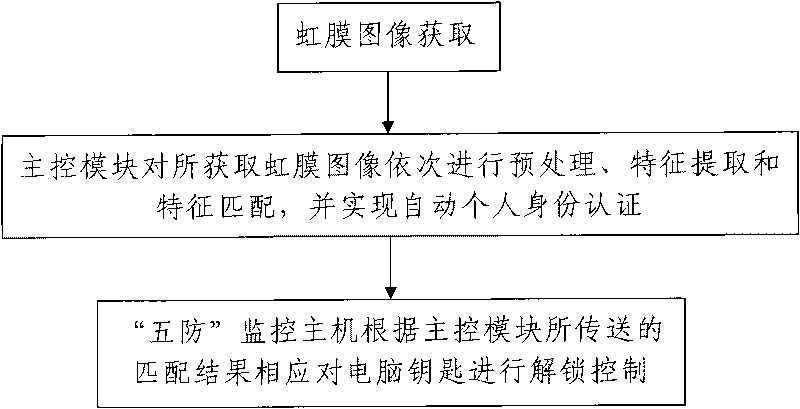
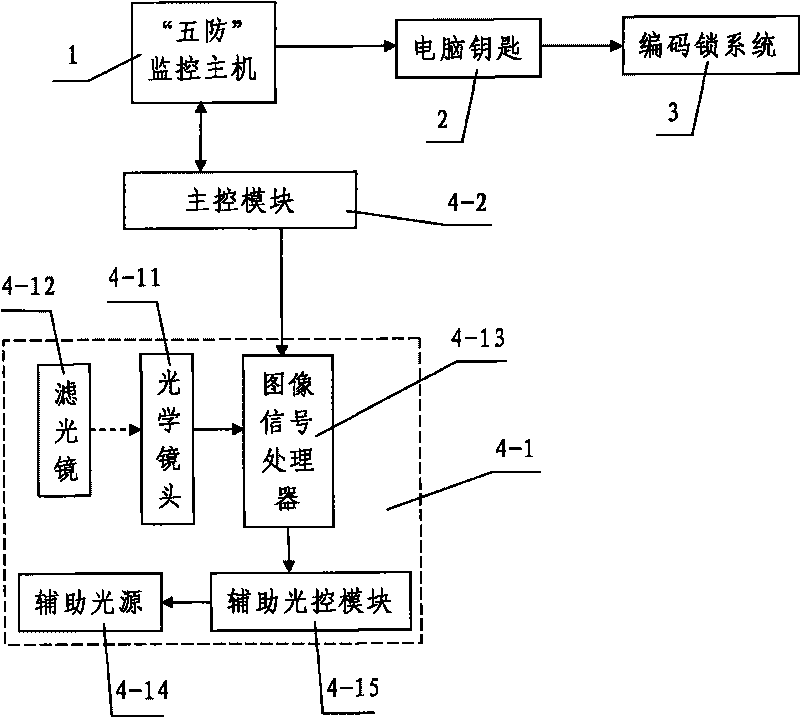
[0070] Such as figure 1 The shown is a power mistake-proof locking system based on iris identification, including a "five-defense" monitoring host 1 and a computer key 2 connected to the "five-defense" monitoring host 1 and correspondingly unlocking and controlling the coded lock system 3, It also includes an iris identification device 4 connected with the "five defenses" monitoring host 1. The iris identifier 4 includes an iris information collection module 4-1 and a main control module 4-2 connected with the iris information collection module 4-1 and analyzing and processing the collected information and realizing automatic personal identity authentication. The main control module 4-2 is connected with the "five defenses" monitoring host 1. The coded lock system 3 includes various coded locks such as intelligent locks, remote locking relays, electric coded locks, and mechanical coded locks.
[0071]In this embodiment, the iris information collection module 4-1 includes an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com