Traffic characteristic-based P2P application identification system and method
A technology of application identification and traffic characteristics, applied in the field of network management, can solve the problems of inaccurate identification and loss of effect, and achieve the effect of improving identification accuracy, good implementation flexibility and applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
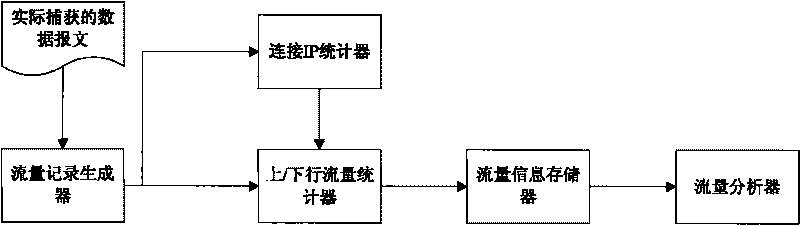
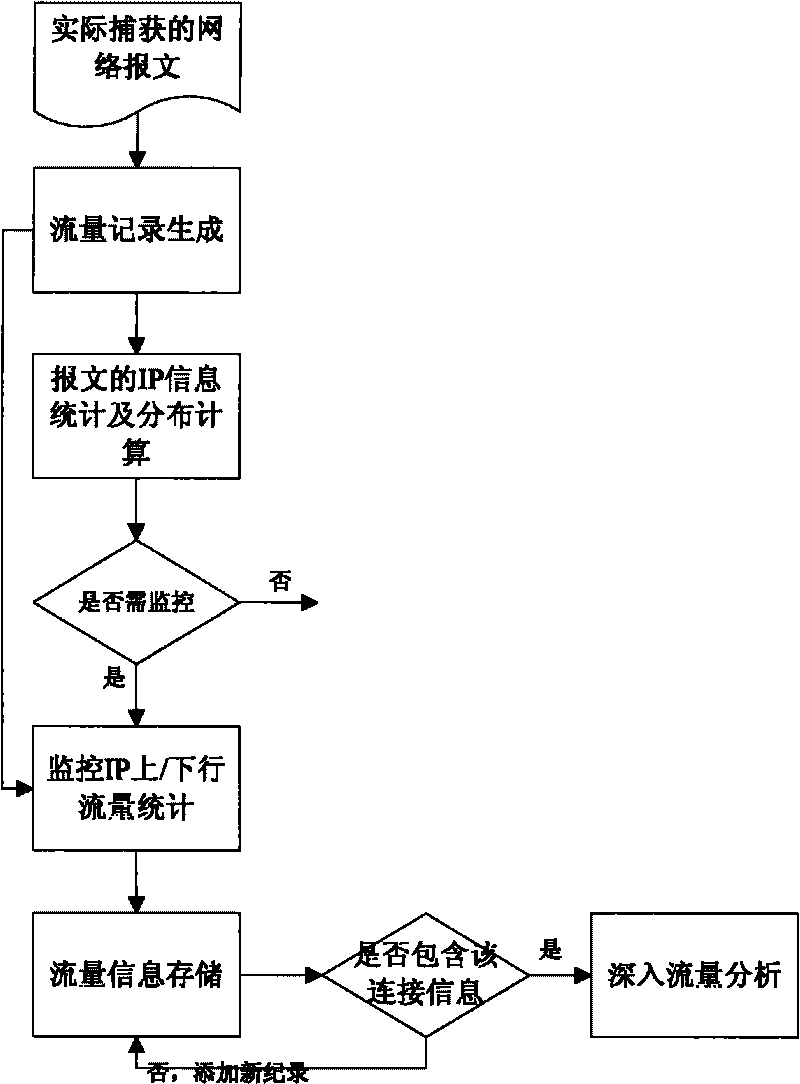
[0023] Embodiment 1: This embodiment performs specific applications according to actual network traffic, and provides a basic mode of a P2P application identification system and method based on traffic characteristics. like figure 1 As shown, the basic architecture of the basic mode includes: a flow record generator, a connection IP statistic, an up / down flow statistic, a flow information storage, and a flow analyzer. The system workflow of this basic mode is as follows figure 2 As shown, the P2P application identification method based on traffic characteristics includes the following steps:
[0024] Flow record generating step; monitoring IP screening step; uplink / downlink flow statistics step; flow information storage step; and flow analysis step.
[0025] in:
[0026] The flow record generation step uses a hierarchical protocol analysis method and a standardized record generation format to generate flow records for each connection in the network within a fixed time inte...
Embodiment 2
[0031] Embodiment 2: This embodiment is a preferred solution for the flow record generation step in Embodiment 1. In this embodiment, the flow record generation step is responsible for generating the flow records of each connection in the network within a fixed time interval based on the actually captured data packets with a hierarchical protocol analysis method and a standardized record generation format, and according to the pre-established The traffic records generated by the time interval are provided to the IP screening step and the upstream / downstream traffic statistics step.
[0032]The basic idea of this embodiment is: first take the actually captured network message as a sample, perform protocol analysis according to the standard protocol format, and obtain various information of the message, for example, the transport layer protocol used by each message is TCP , UDP, ICMP, etc., the source IP, destination IP, source port, destination port, number of bytes, etc. sen...
Embodiment 3
[0036] Embodiment 3: This embodiment is a preferred solution of the monitoring IP screening step in Embodiment 1. In this embodiment, the monitoring IP screening step counts the source IP and destination IP of each connection in the current network environment according to the flow records provided by the flow record generating step; the standard entropy calculation formula is used to calculate the entropy values of the source IP and destination IP distribution respectively , and compare it with the preset threshold; when the source IP is found to be lower than the threshold and the destination IP is higher than the threshold, the N IP addresses with the largest number of connections in the source IP statistical results will be recorded in the monitoring IP set, and at the same time, monitoring will be required The set of IPs provided to the upstream / downstream traffic statistics step as the object of traffic statistics.
[0037] The basic idea of this embodiment is: accor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com