Key embedded password
An embedded and key technology, applied in the field of information security, can solve problems such as complex system management, high operating costs, and difficult to eliminate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The realization of the present invention includes two parts of work, that is, the design of the key embedded algorithm module and the construction of the key embedded network security system with the key embedded algorithm module as the basic unit. The following is attached Figures 1 to 4 , to illustrate the implementation method of the present invention.
[0059]1. Design and production of key embedded algorithm module
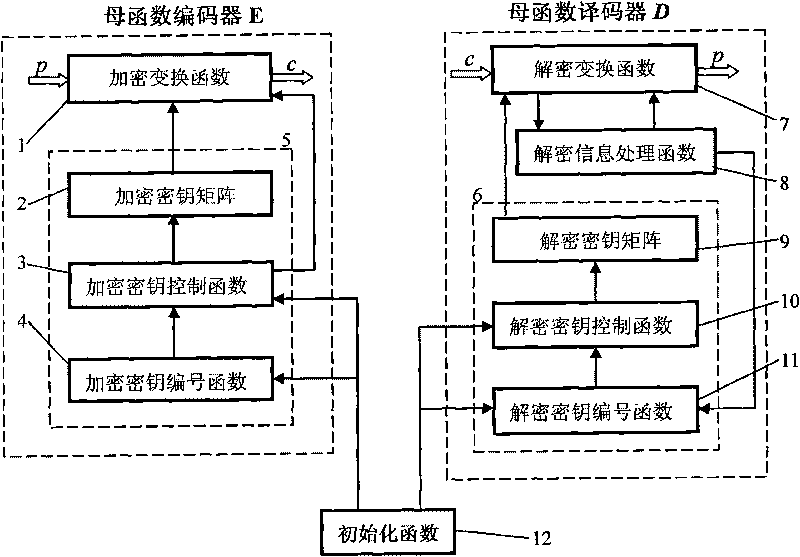
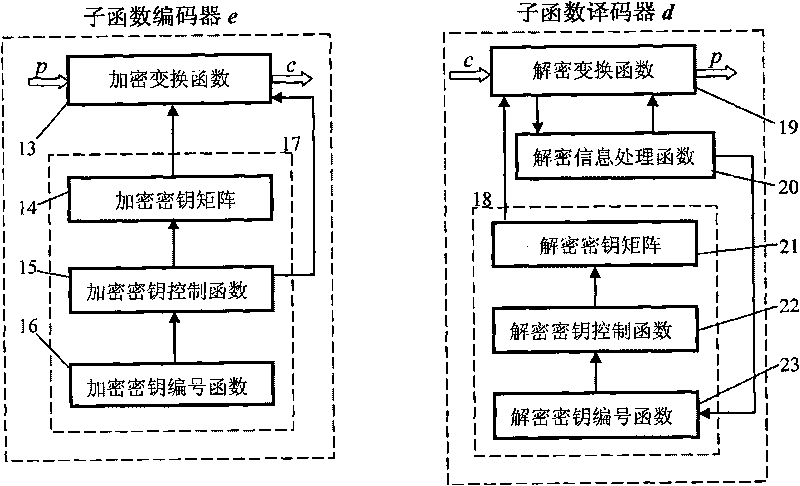
[0060] Select an appropriate computer language, such as VB, C#, C++, and compile the key embedded algorithm program. You can refer to the basic algorithm flow of the key embedded algorithm module ( figure 1 ), design the parent function module according to the following requirements.
[0061] The generating function module consists of three independent sub-modules: generating function encoder E, generating function decoder D, initialization function 12, such as figure 1 shown. The generating function encoder E includes an encryption transformatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com