Grid visit control method based on extendible markup language security policy
A technology that extends markup language and access control, and is used in data exchange networks, digital transmission systems, electrical components, etc., to achieve the effect of easy implementation, guaranteed compatibility, and simple content
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
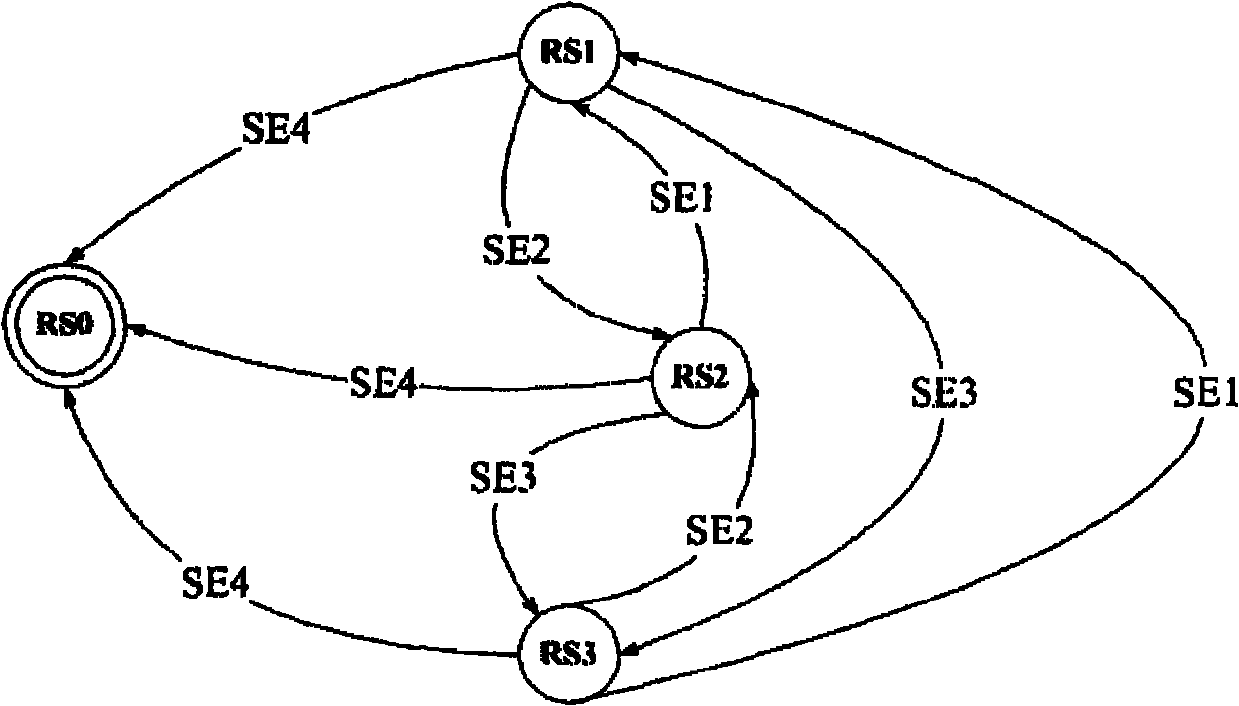
[0103] Example: Only allow users to access a resource from 8:00 am to 8:00 pm; allow users to access resources when the CPU load of the resource is 80%; there is only one session When using a resource, the resource can be read, written, and executed, but when multiple sessions use the resource, the resource cannot be written.
[0104] Table 4-3 and Table 4-4 give the information description of the permission status and events in this example. Again we can use the Permission State Machine (PSM) to describe these situations. like Pic 4-1 0 is a schematic diagram of the permission state machine, where each node represents a state, each edge represents an event, and PS0 represents the prohibited state of the permission.
[0105] Table 3 permission state table
[0106] permissions
status number
Resource readable, writable and executable (P1, P2, P3)
PS1
Resource readable and executable (P1, P2)
PS2
Resource readable (P1)
PS3
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com