Method and system for analyzing wireless local area network authentication and privacy infrastructure protocol
A wireless local area network and protocol analysis technology, applied in the field of communication, can solve the problems of inability to test WAPI protocol consistency, no WAPI protocol analysis method and system, etc., and achieve the effects of flexible upgrade, convenient use, and accurate test accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
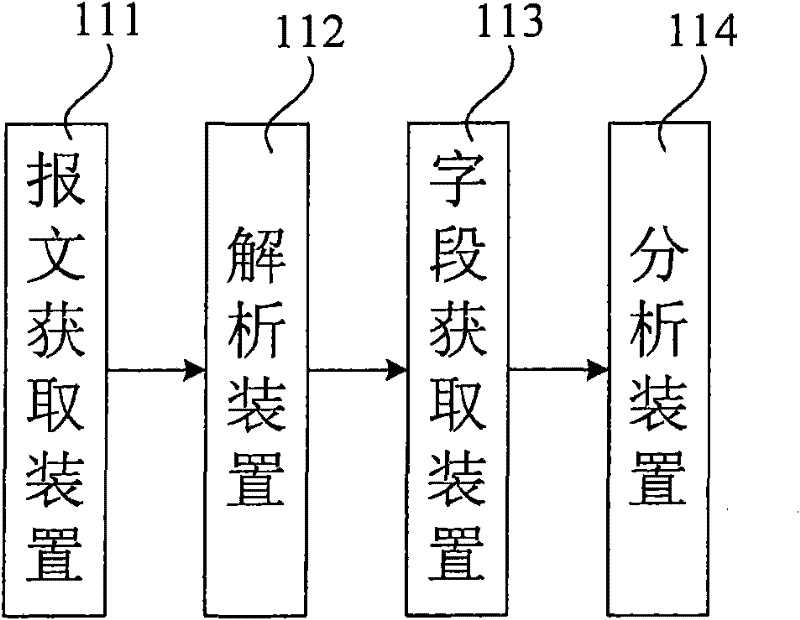
[0070] Figure 7 It is a flow chart of the first embodiment of the WAPI protocol analysis method of the present invention. As shown in the figure, the first embodiment of the WAPI protocol analysis method of the present invention specifically includes the following steps:
[0071] Step 101, acquiring a wireless signal, and extracting a WAPI protocol message from the acquired wireless signal;
[0072] Step 102, analyzing the WAPI protocol message to obtain the grouping information of the WAPI protocol message;
[0073] Step 103, according to the grouping information of WAPI protocol message, obtain the value of each field in the WAPI protocol message of WAI grouping;
[0074] Step 104, judge whether the WAPI protocol flow in the WAPI protocol message of the WAI packet is consistent with the preset WAPI protocol flow according to the value of each field in the WAPI protocol message of the WAI packet.
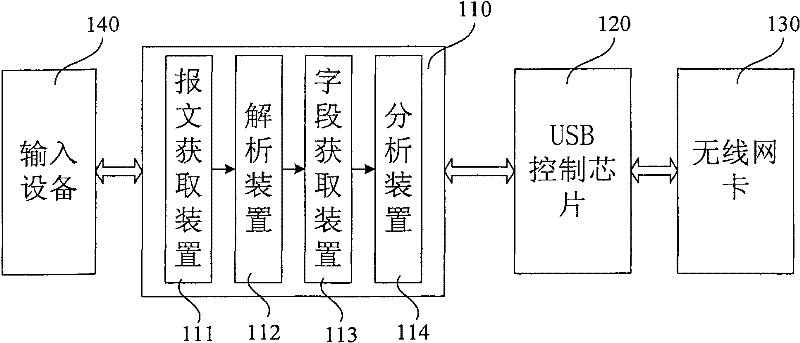
[0075] Figure 8 It is an overall framework diagram based on the WAPI prot...
Embodiment 2
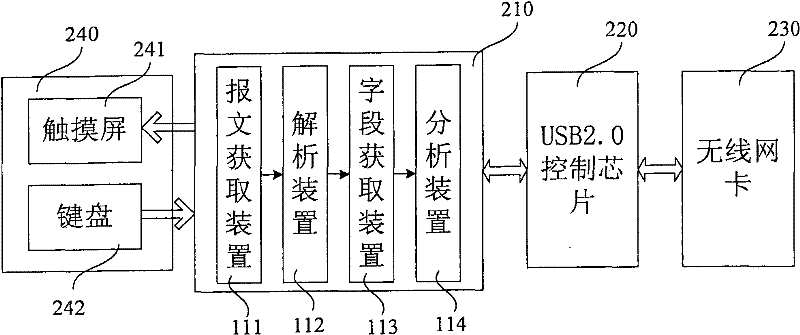
[0082] Figure 10 It is the flowchart of the second embodiment of the WAPI protocol analysis method of the present invention. As shown in the figure, the second embodiment of the WAPI protocol analysis method of the present invention specifically includes the following steps:
[0083] Step 201, initialization process;
[0084] The USB wireless network card driver first registers itself with the USB subsystem, and then judges whether the hardware device has been inserted into the bus through the vendor id and device id. When the wireless network card is inserted into the USB bus, the USB core will call the Probe method to detect the information passed in to determine whether the wireless network card device matches the driver, and at the same time fill in the struct net_device to complete the initialization of the network device. When the wireless network card is pulled out, the USB core will call the Disconnect method to complete the cleaning work. The driver calls module_in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com