Short message safety communication method, system and device based on STK (SIM Tool Kit) business
A technology of secure communication and SMS, applied in security devices, wireless communication, messages/mailboxes/notifications, etc., can solve the problems of low security and reliability, and achieve the effect of improving reliability and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
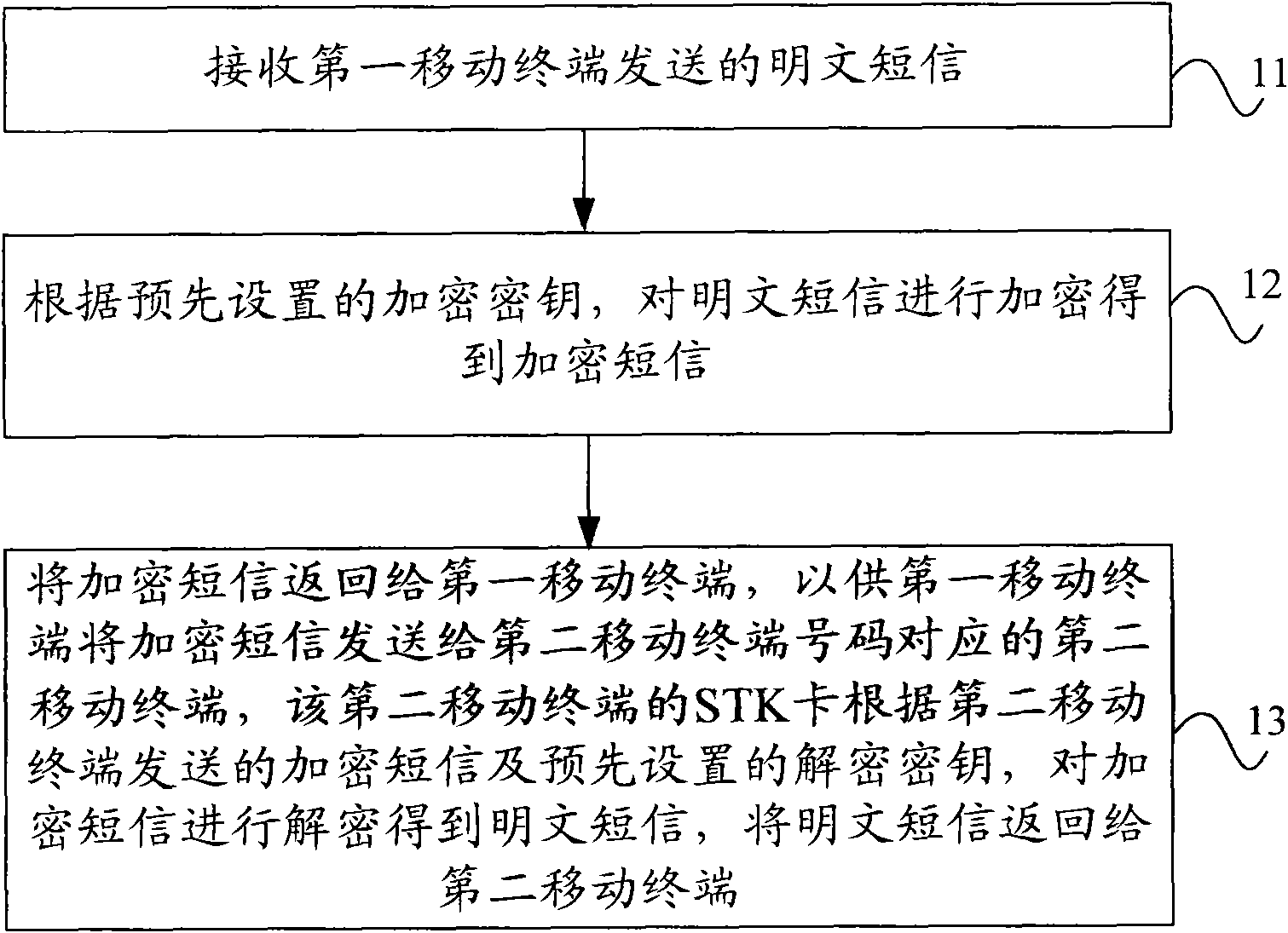
[0032] figure 1 The flow chart of the short message secure communication method based on the STK service provided by Embodiment 1 of the present invention, such as figure 1 As shown, the method specifically includes:
[0033] Step 11, receiving the plain text message sent by the first mobile terminal;
[0034] Step 12. According to the preset encryption key, the plain text message is encrypted to obtain the encrypted message;
[0035] Step 13, return the encrypted short message to the first mobile terminal, so that the first mobile terminal can send the encrypted short message to the second mobile terminal corresponding to the second mobile terminal number, and the STK card of the second mobile terminal is sent according to the second mobile terminal The encrypted short message and the preset decryption key are used to decrypt the encrypted short message to obtain a plain text short message, and return the plain text short message to the second mobile terminal.
[0036] In ...
Embodiment 2
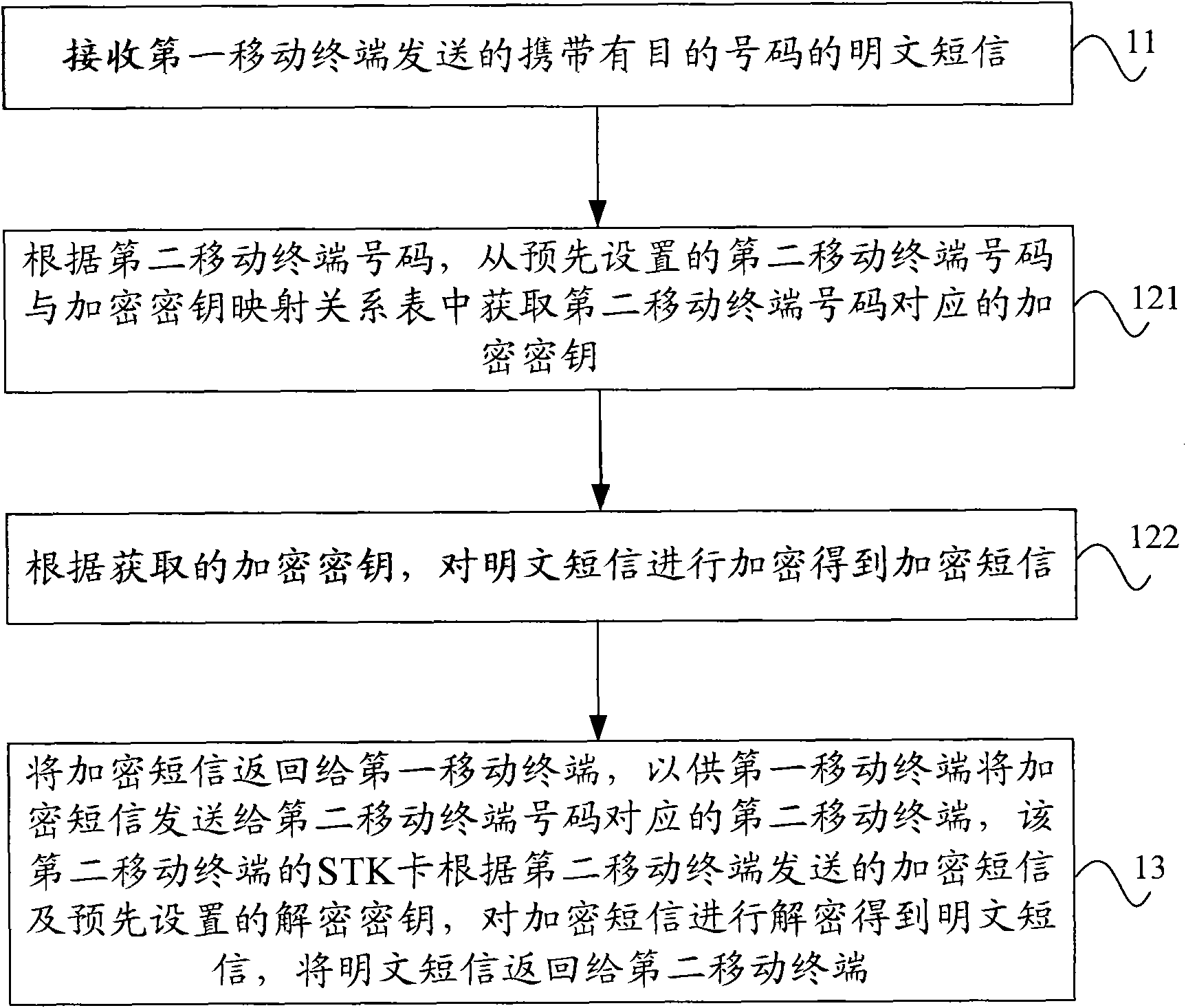
[0042] figure 2 The flow chart of the short message secure communication method based on the STK service provided by Embodiment 2 of the present invention, such as figure 2 As shown, on the basis of the above-mentioned embodiment one, in order to further improve the security and reliability of the short message, take the built-in SIM extension card in the mobile terminal to encrypt the short message as an example, introduce the technical solution of the present invention in detail, and step 11 specifically for:
[0043] Step 11, receiving a plain text message carrying a purpose number sent by the first mobile terminal;
[0044] Then step 12 specifically includes:
[0045] Step 121, according to the second mobile terminal number, obtain the encryption key corresponding to the second mobile terminal number from the preset mapping relationship table between the second mobile terminal number and the encryption key;
[0046] Step 122: Encrypt the plain text message according t...
Embodiment 3
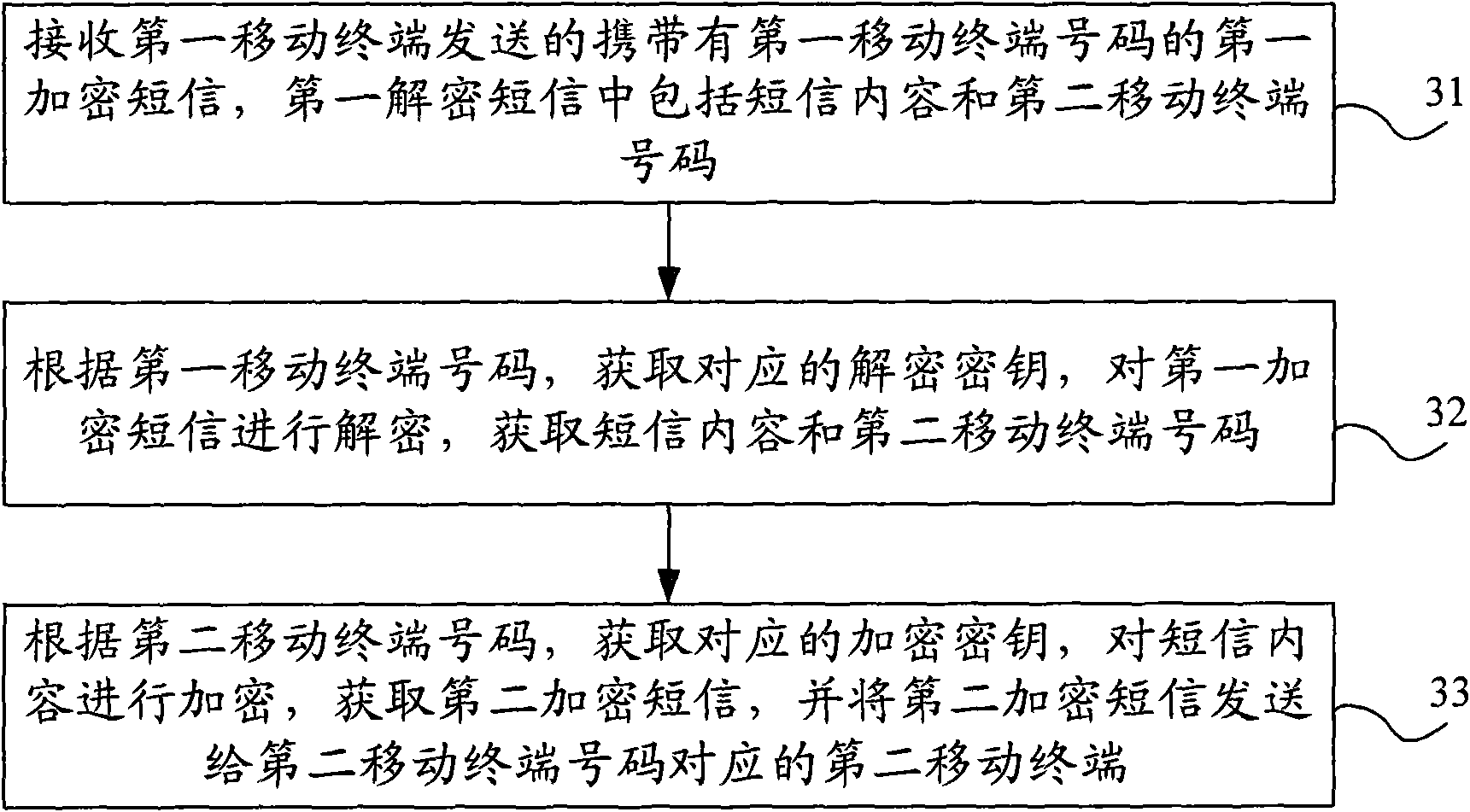
[0051] image 3 The flow chart of the short message security communication method based on the STK service provided by Embodiment 3 of the present invention. In this embodiment, taking the transmission of encrypted short messages through the short message gateway platform as an example, the technical solution of the present invention is introduced in detail, as image 3 As shown, the method includes:
[0052] Step 31, receiving the first encrypted short message carrying the first mobile terminal number sent by the first mobile terminal, the first decrypted short message includes the content of the short message and the second mobile terminal number;
[0053] Step 32, according to the first mobile terminal number, obtain the corresponding decryption key, decrypt the first encrypted message, and obtain the content of the message and the second mobile terminal number;
[0054] Step 33: According to the second mobile terminal number, obtain the corresponding encryption key, encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com