Authentication device and system and method using same for on-line identity authentication and transaction
An authentication device and identity authentication technology, applied in user identity/authority verification, transmission system, payment system structure, etc., can solve the unavoidable hijacking of networked computer transactions, remote control of transaction tampering, and does not involve USBKey devices and authentication/transaction servers Interactive cooperation and other issues to achieve high security, avoid SMS delay, and strong convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
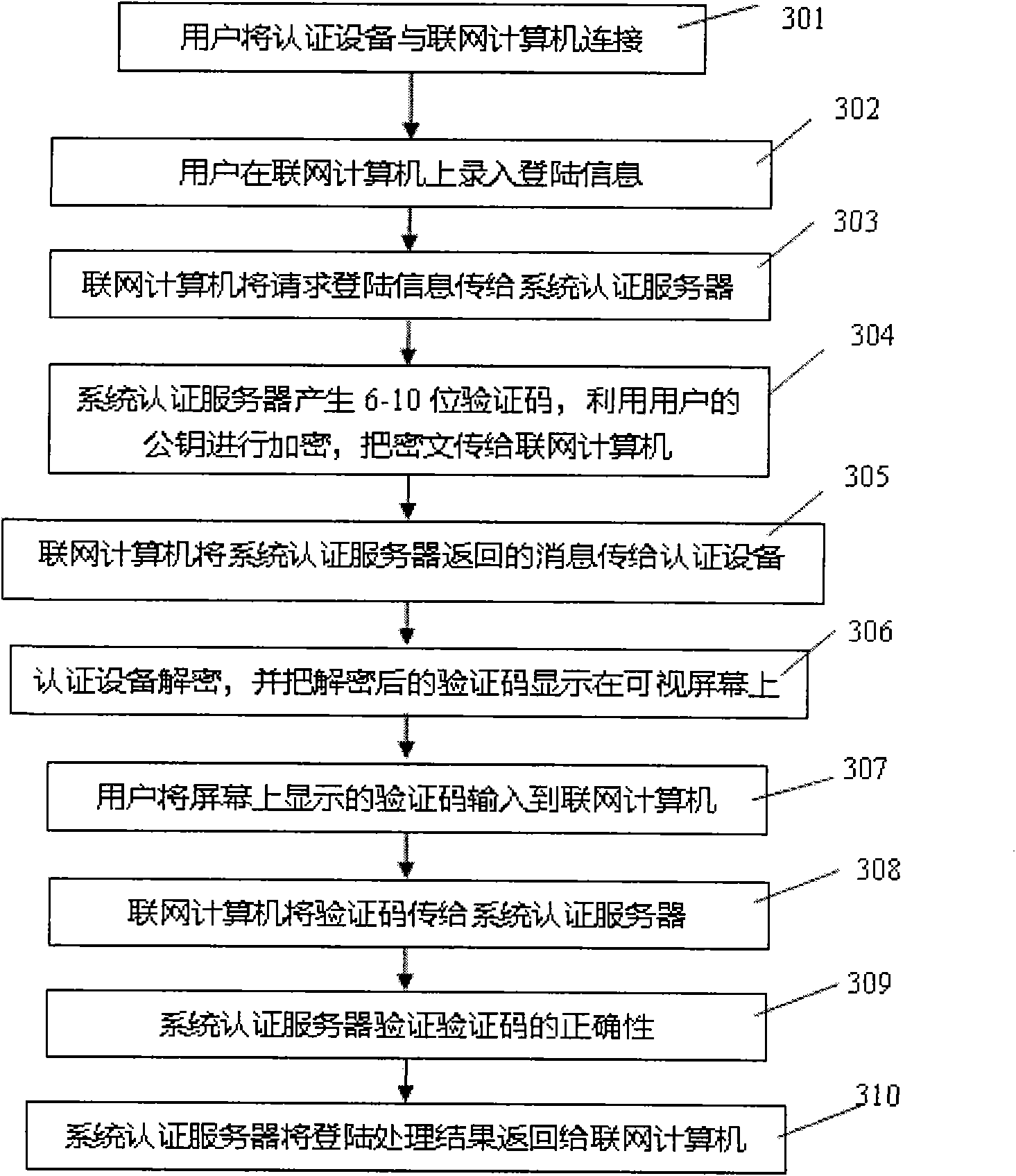
[0073] Example 1: see image 3 , A method for online identity authentication using the above authentication device.
[0074] A method for online identity authentication using the above authentication device, the method sequentially includes the following steps:
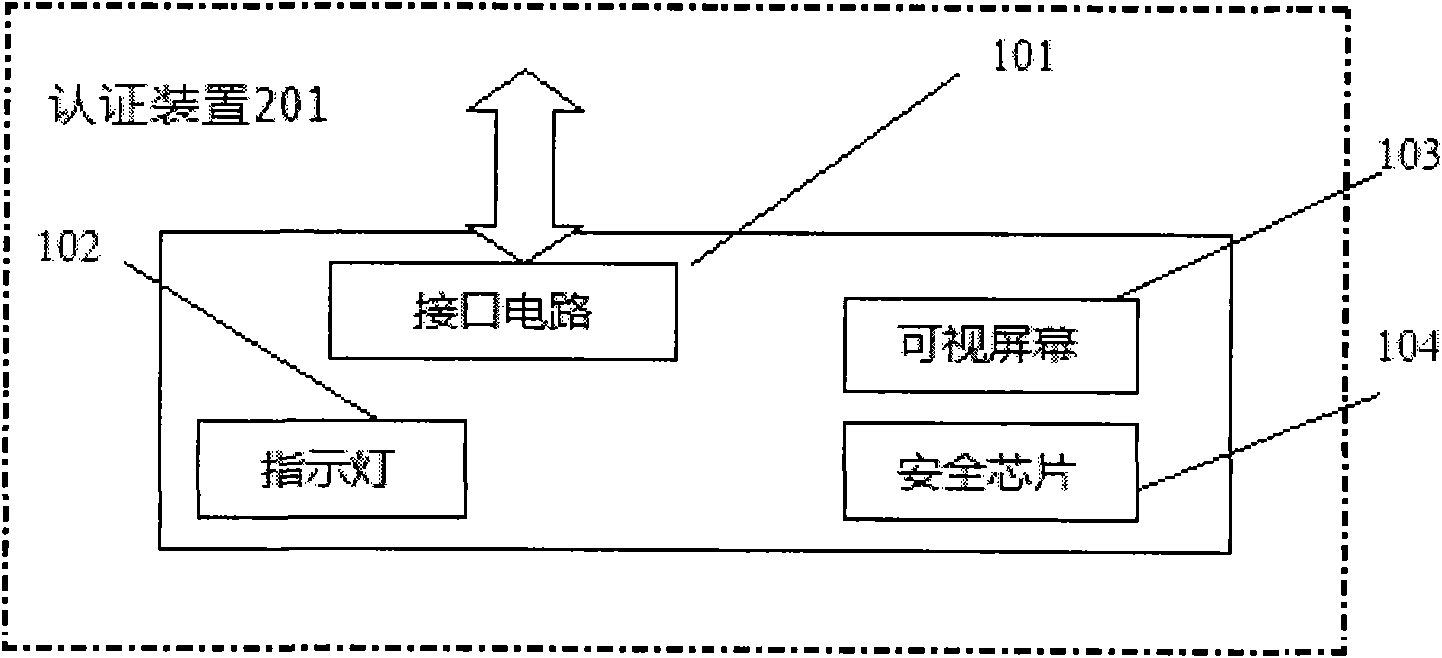
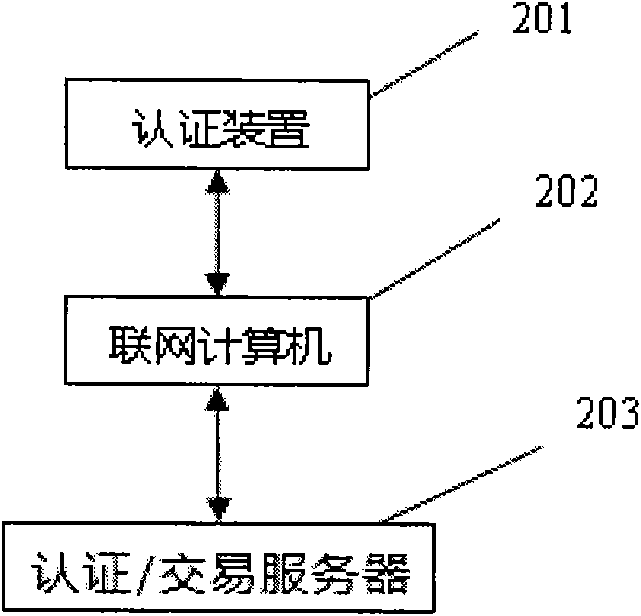
[0075] In step 301, the user connects the authentication device 201 of the present invention to the networked computer 202 through the interface circuit 101;
[0076] In step 302, the user uses the networked computer 202 to enter login information, such as a user name;
[0077] In step 303, the above-mentioned networked computer 202 transmits the login information to the authentication server 203 via the network;
[0078] In step 304, after receiving the login request, the authentication server 203 randomly generates a 6-10 digit verification code, and then uses the user's public key to encrypt the verification code. The encryption method uses 1024-bit or above RSA encryption or 192 The elliptic curve encryption of bits and ab...
Embodiment 2
[0086] Example 2: see Figure 4 , A method for online transactions using the above authentication device.
[0087] A method for online transactions using the above authentication device, the method sequentially includes the following steps:
[0088] In step 501, the user connects the authentication device 201 of the present invention to the networked computer 202 through the interface circuit 101;
[0089] In step 502, the user uses the networked computer 202 to enter the requested transaction information, such as account name, account number, and transaction amount;
[0090] In step 503, the networked computer 202 transmits the requested transaction information to the transaction server 203 via the network;
[0091] In step 504, after receiving the login request, the transaction server 203 randomly generates a 6-10 digit verification code, and then uses the user's public key to encrypt the transaction information, such as the account name, account number, and transaction amount, and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com