Method and system for protecting key file
A key file and key technology, applied in the field of key file protection methods and systems, can solve the problems of inability to satisfy security, low security, etc., and achieve the effects of increasing costs, preventing economic losses, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
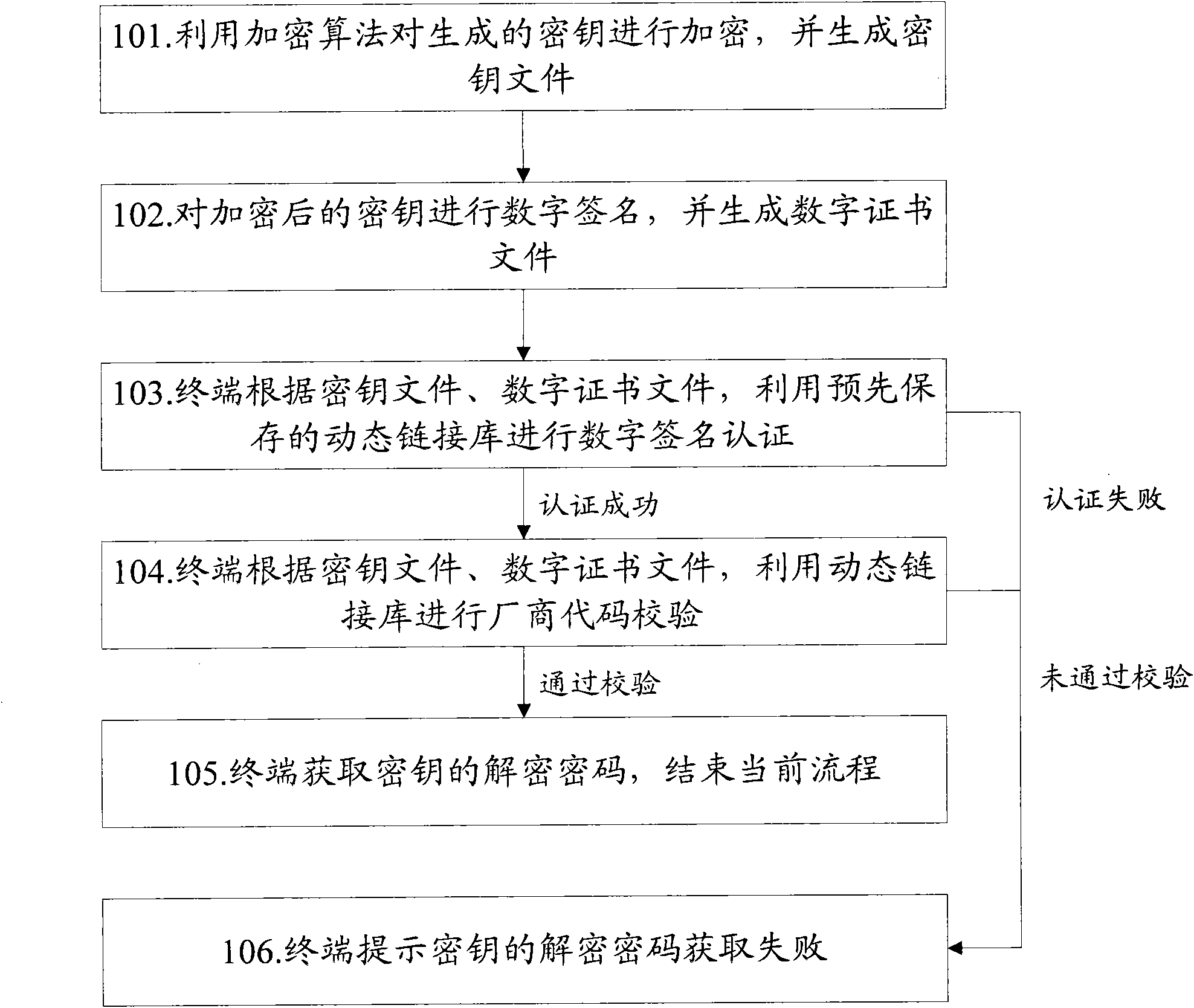
[0031] The basic idea of the present invention is: use the encryption algorithm to encrypt the generated key, and generate a key file; digitally sign the encrypted key, and generate a digital certificate file; the terminal, according to the key file and the digital certificate file, Use the pre-saved dynamic link library to perform digital signature authentication and manufacturer code verification; when the digital signature authentication is successful and the manufacturer code verification is passed, the decryption password of the key is obtained.
[0032] The RSA encryption algorithm was developed by Ron Rivest, Adi Shamirh, and LenAdleman in 1977. The RSA encryption algorithm is named after the development of the three of them. The RSA encryption algorithm is currently the most influential public key encryption algorithm. It can resist until now. All password attacks known so far.
[0033] The present invention will be further described in detail below with reference to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com