Method, system and device for mutual authentication
A two-way authentication and vector technology, applied in the field of communication, can solve the problems of indistinguishable, inconvenient for implementers, and difficult to store a large amount of challenge information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
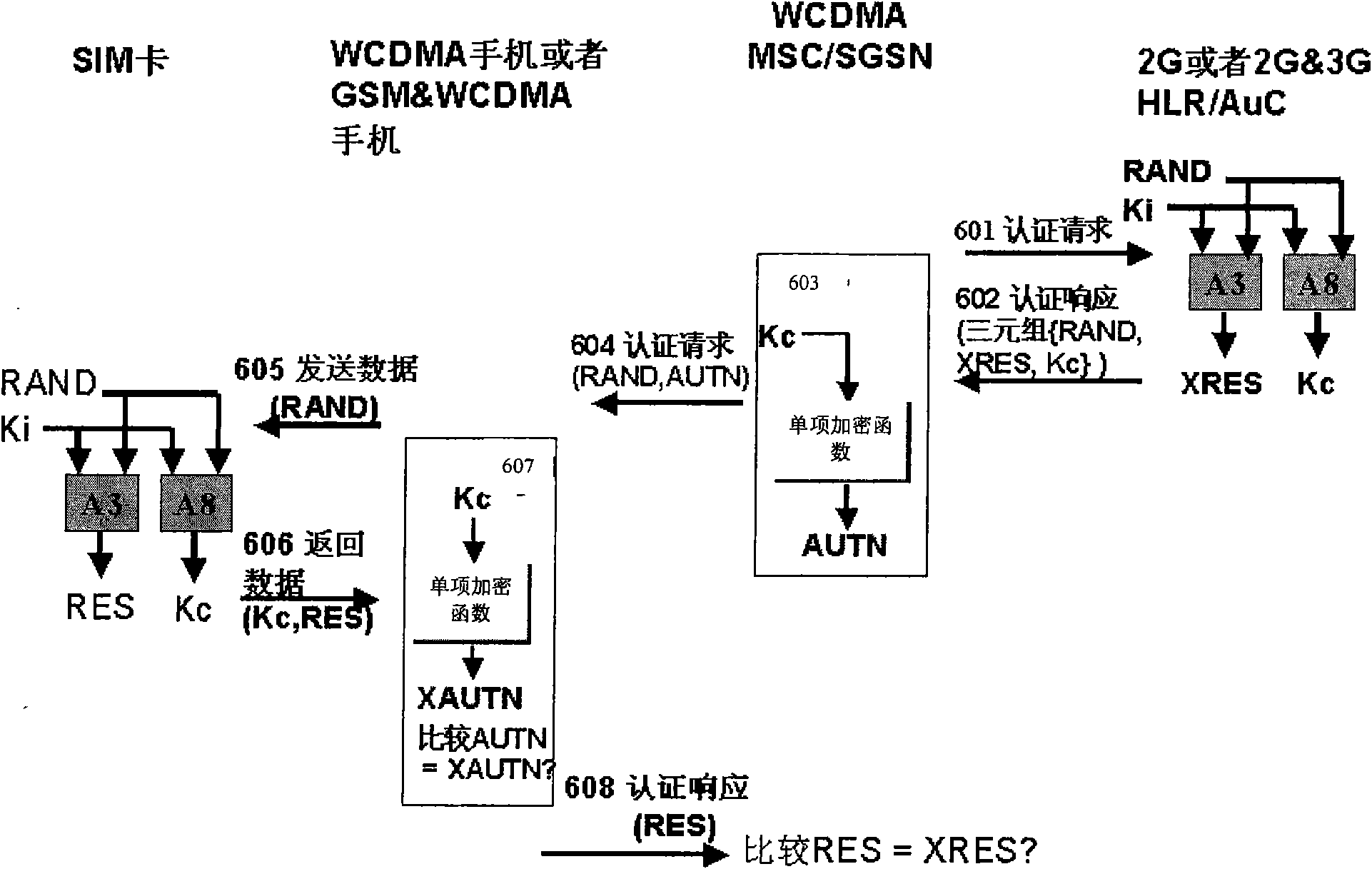
[0064] like Figure 5 As shown, it is a flow chart of the two-way authentication method in Embodiment 1 of the present invention, and can refer to Image 6 A schematic diagram of the two-way authentication method in Embodiment 1 is shown. In this embodiment, MSC / VLR or SGSN refers to equipment in the TD-SCDMA system, and 3G ME refers to TD-SCDMA ME or GSM / TD-SCDMA dual-mode ME. This embodiment comprises the following steps:
[0065] Step S501, in some specific message flows, such as call establishment, routing area / location area update, etc., if the operator needs to be authenticated, the MSC / SGSN of the TD-SCDMA system in the visited place first checks the SIM user's Whether the triplet is a new, unused triplet, if not, execute step S502, step S503; if yes, turn to step S504.
[0066] In step S502, the MSC / SGSN sends an authentication information request (MAP_SEND_AUTHENTICATION_INFO Request) message to the HLR / AuC through the MobileApplication Part (hereinafter referred t...
Embodiment 2
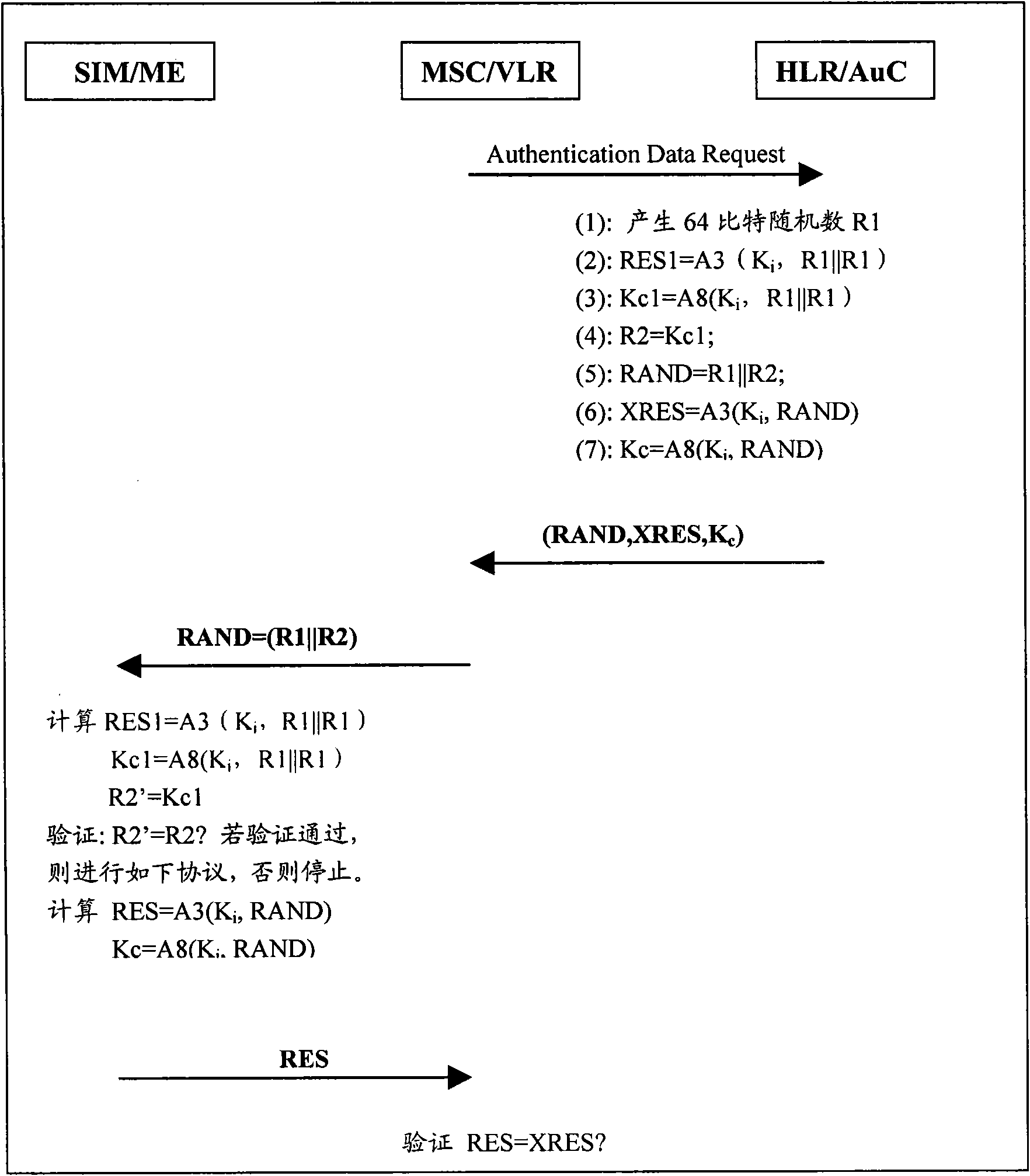
[0079] Can refer to Figure 7 A schematic diagram of the two-way authentication method in the second embodiment is shown. In MSC / VLR or SGSN and ME, in this embodiment, except cryptographic algorithm AES, also has another cryptographic algorithm (recorded as f1), for the convenience of realization, f1=AES can be allowed, and during concrete implementation, f1 can also be Select an algorithm other than AES. The difference between this embodiment and Embodiment 1 is that on the network side, the network side first uses Kc and RAND as input parameters to generate another 64-bit output parameter MAC, and uses the combination of MAC and CNR instead of the combination of RAND and CNR as another An AES input parameter, using Kc as the encryption key, generates AUTN. Similar to Embodiment 1, after ME receives it, it also uses Kc to decrypt AUTN to generate XAUTN, and still separates and verifies CNR' according to the method of Embodiment 1. On the ME side, it needs to be added to us...
Embodiment 3
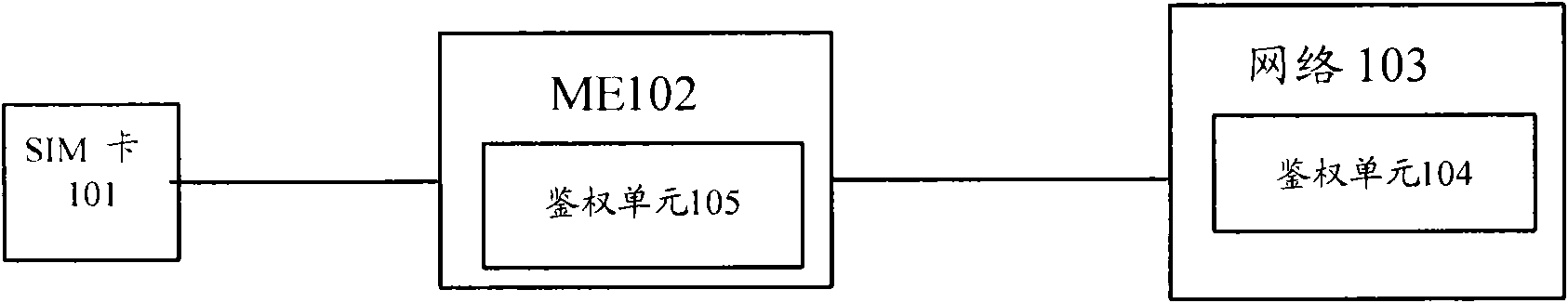
[0082] like Figure 8 Shown is a system structure diagram of the two-way authentication of the embodiment of the present invention. The system includes ME 810 , network entity 830 and HLR / AuC 840 . The ME 810 can be TD-SCDMA ME or GSM / TD-SCDMA dual-mode ME, or other 3G communication ME. The ME has a GSM SIM card 820 . The GSM SIM card 820 has the same function as the 2G SIM card. It stores the root key Ki and the 2G authentication and encryption algorithm A3 / A8. According to the root key Ki and the random number RAND sent by the network, A3 / A8 generates a temporary Key Kc.
[0083] Among them, the network entity 830 is mainly used to calculate the parameters of the ME authentication network, and compare them with the corresponding parameters sent by the network, so as to realize the authentication of the ME to the network; here only TD-SCDMA ME or GSM / TD-SCDMA dual-mode ME is described as an example. In fact, the method in this implementation is also applicable to multi-mode...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com