Method for suppressing malicious behavior based on distributed recommendable reputation in peer-to-peer (P2P) network
A P2P network, distributed technology, applied in the network field, can solve the problem of lack of malicious behavior classification and dynamic changes in reputation value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
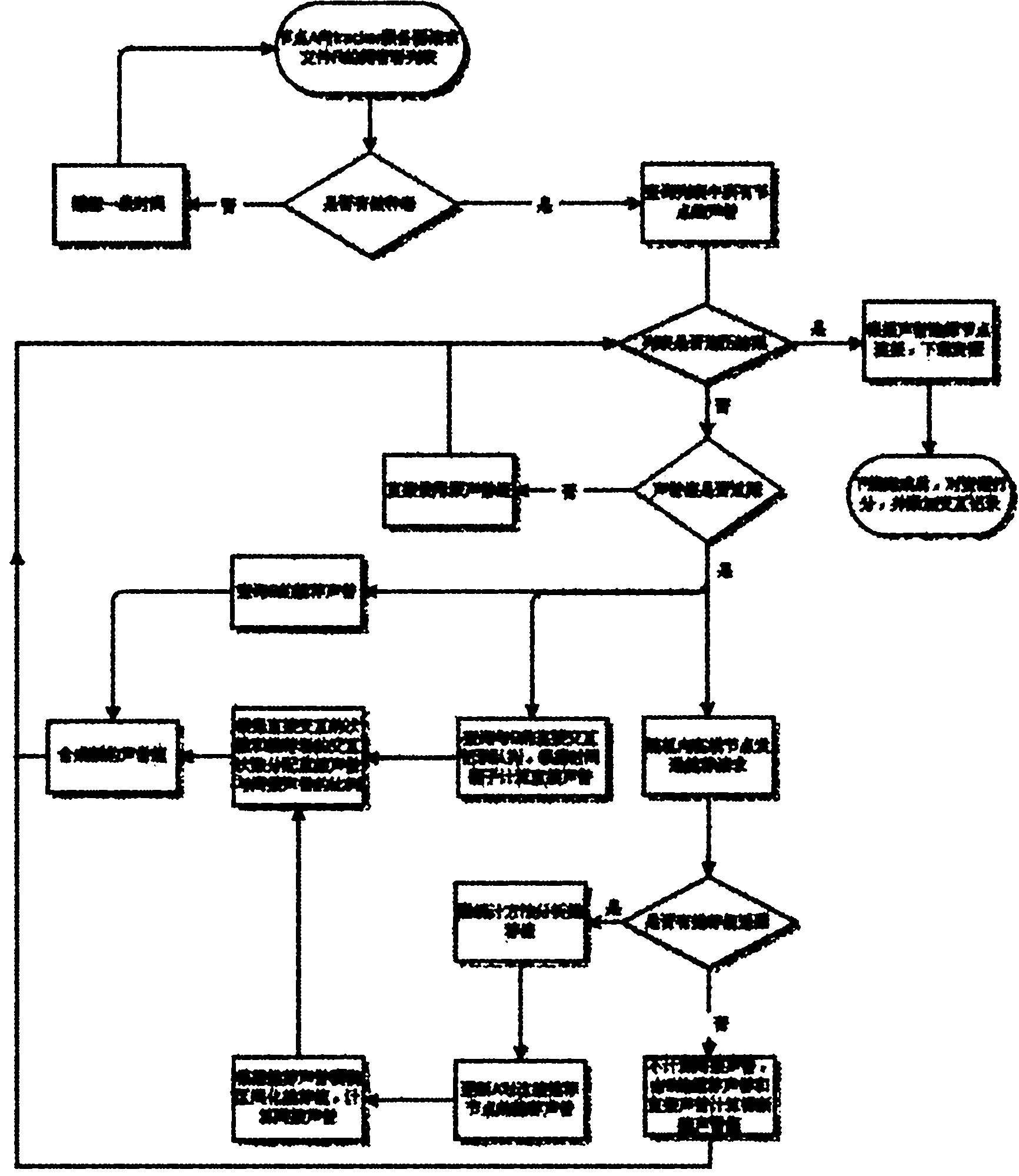
[0081] This embodiment includes the following steps:
[0082] Step 1: Node A requests the owner list of file R from the tracker server. If there is no seeder, try again after blocking for a period of time; if there is a seeder, the current node A queries the local data according to the list returned by the tracker server, and obtains the reputation value of all nodes in the list.
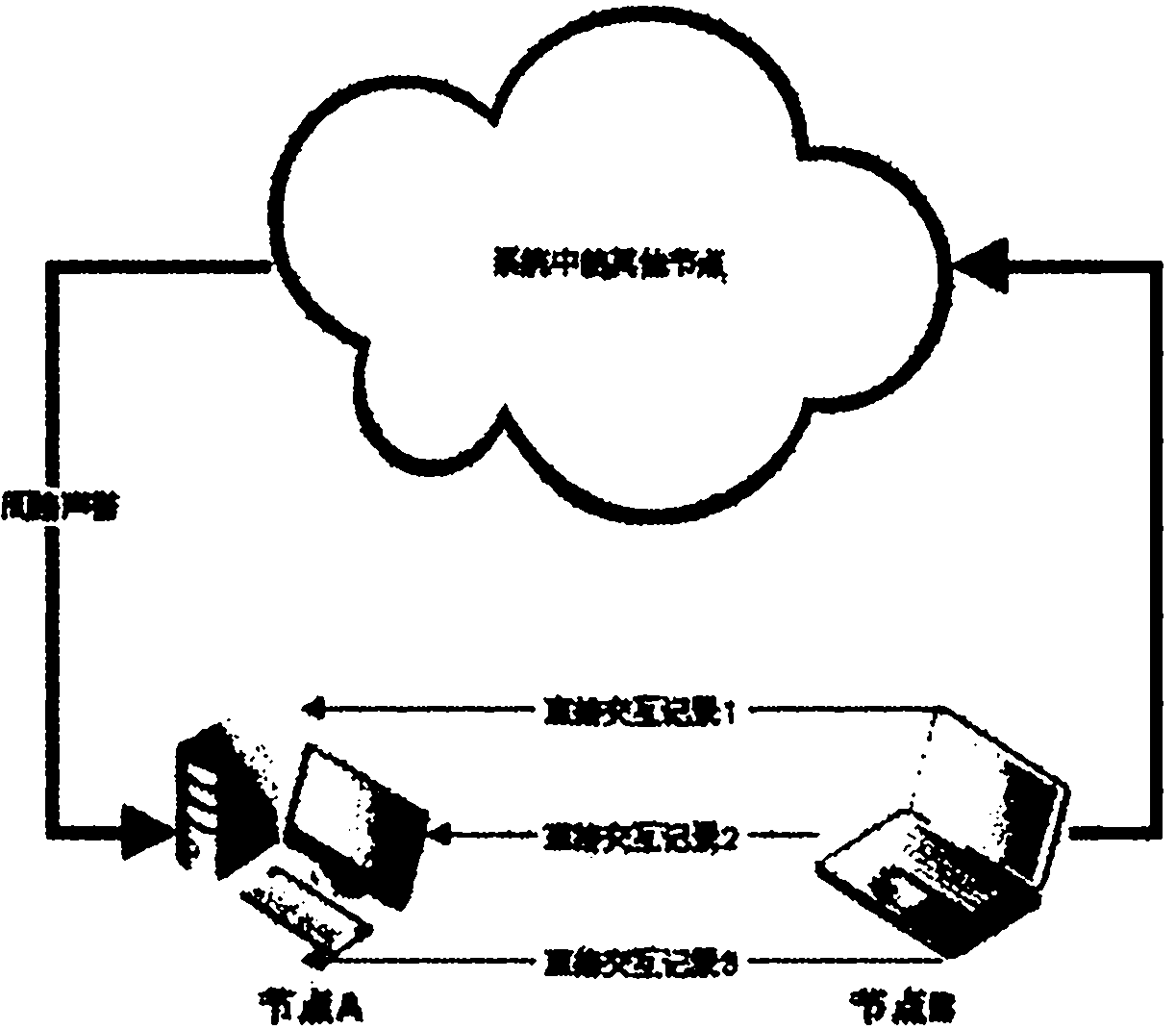
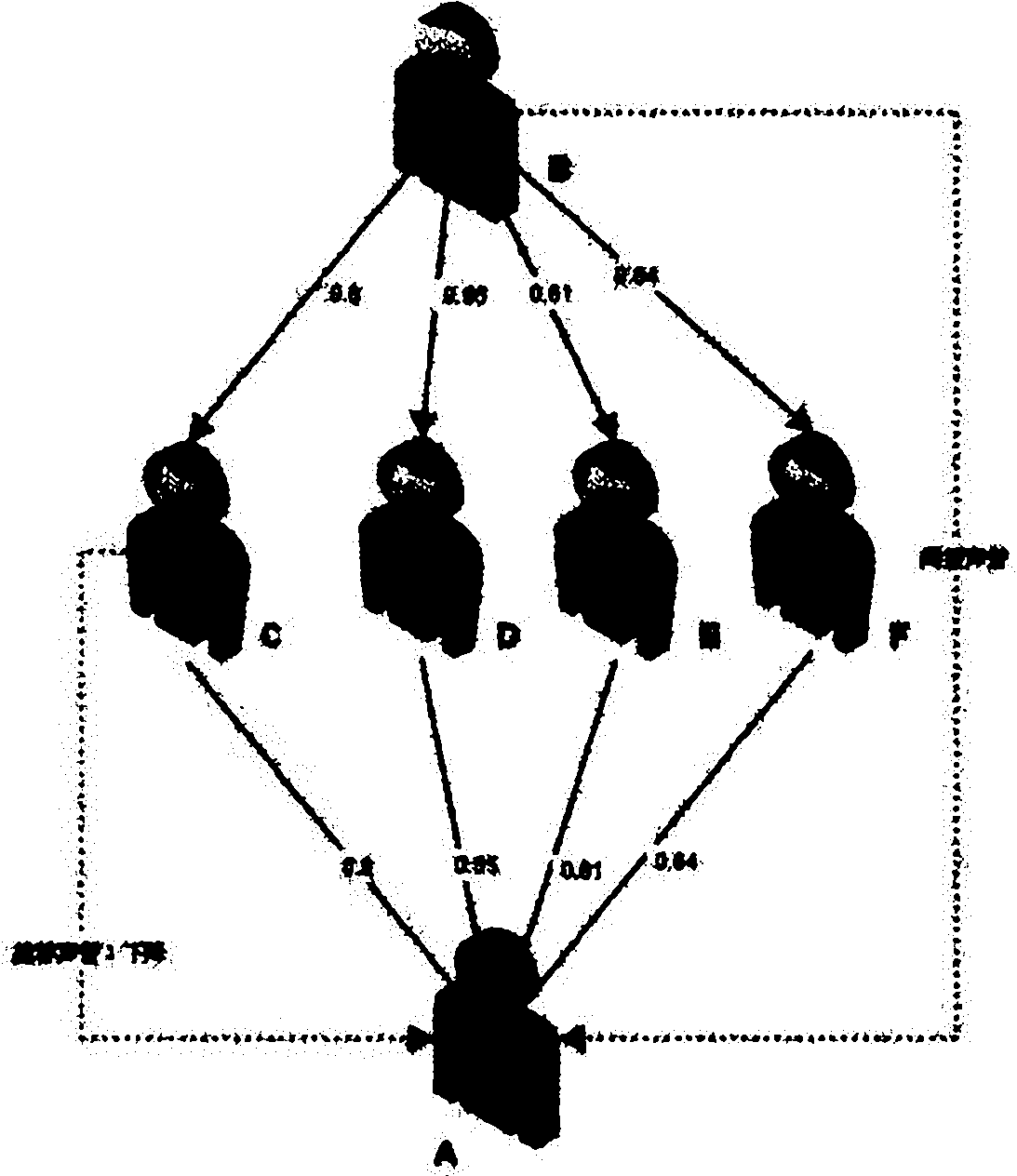
[0083] Such as figure 1 As shown in Fig. 1 , a node wants to download resources, firstly it sends a request to the Tracker server, and the Tracker server responds to the node's request by providing it with a list of IP addresses of other downloaders (including publishers and completers). According to this list, the node queries the reputation of the node that can provide services for itself. The reputation value is composed of direct reputation, indirect reputation and recommended reputation. While all three were previously interrelated, when it comes to building trust, all come from different sou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com