Face identification security mobile phone and implementation method thereof
A face recognition and realization method technology, applied in character and pattern recognition, computer security device, telephone structure, etc., can solve the problem that users cannot pass the authentication smoothly, achieve privacy and business security, avoid direct contact, reliable high sex effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
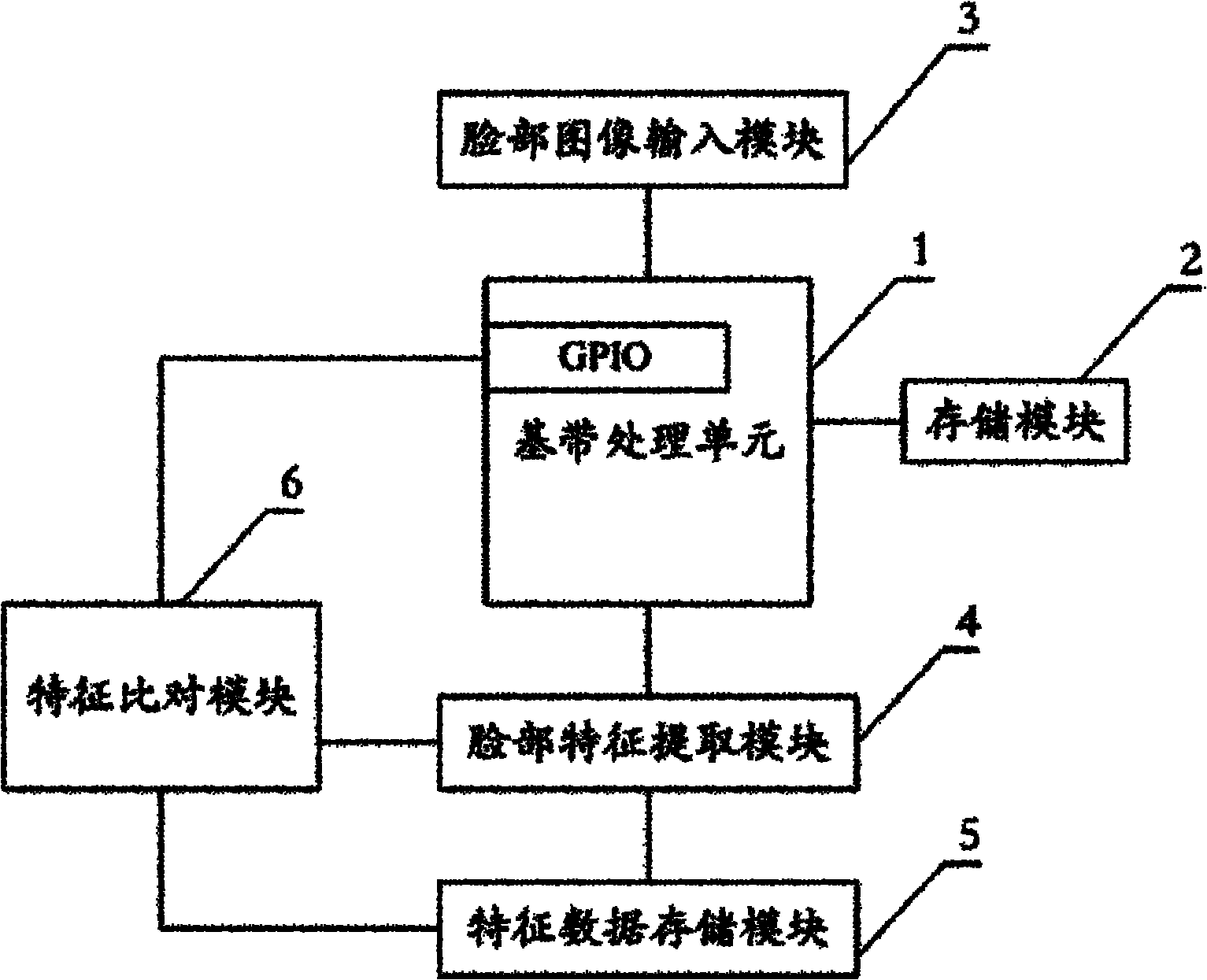
[0015] like figure 1 As shown, the face recognition security mobile phone provided by this embodiment includes a housing, a main board, a baseband processing unit 1 and a storage module 2; Processing unit 1 is connected.
[0016] The baseband processing unit 1 is provided with a GPIO interface that can be used as an interrupt, and the face recognition module is connected to the baseband processing unit 1 through the GPIO interface. Those skilled in the art can understand that the face recognition module can send a high-level signal and a low-level signal to the baseband processing unit 1, so that the level on the GPIO interface changes. Unit 1 enters the interrupt according to the level change on the GPIO interface, and controls the mobile phone to run related operations.
[0017] Described facial recognition module comprises facial image input module 3, facial feature extraction module 4 and feature data storage module 5; Described facial image input module 3 and described ...
Embodiment 2
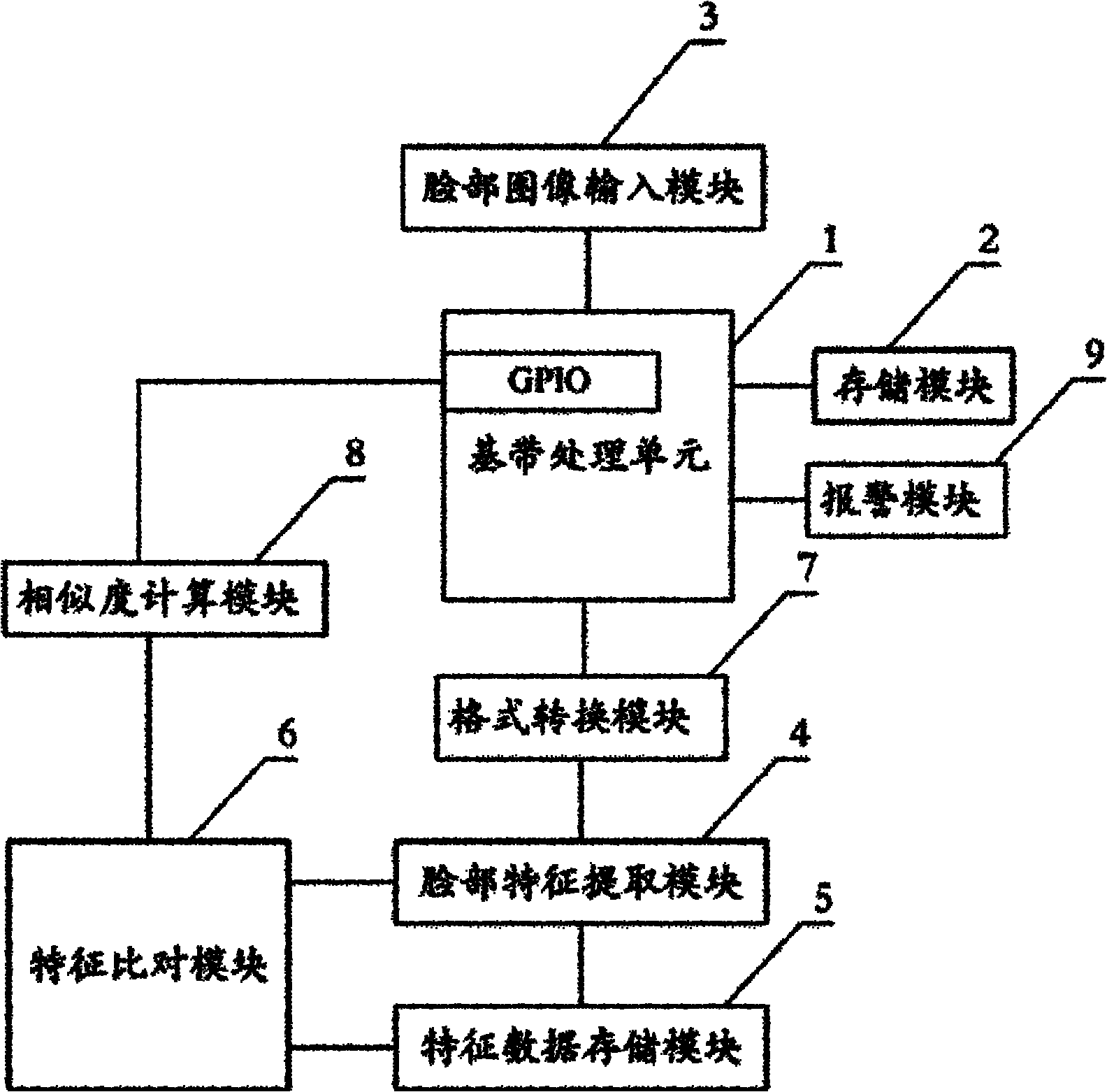
[0022] like figure 2 As shown, it is another embodiment of the face recognition security mobile phone of the present invention, which adds the following content on the basis of the first embodiment above:
[0023] The face recognition module also includes a format conversion module 7 , the input end of the format conversion module 7 is connected to the baseband processing unit 1 and the output end is connected to the facial feature extraction module 4 . Those skilled in the art can understand that the pictures sent to the mobile phone through the camera or various interfaces can include multiple data formats, such as JPG format, JPEG format, GIF format, PNG format or BMP format, etc., the format conversion module 7 It is used to convert the pictures of the above-mentioned multiple data formats into a format recognizable by the facial feature extraction module 4 . Those skilled in the art can understand that the image data format recognized by the facial feature extraction mo...
Embodiment 3
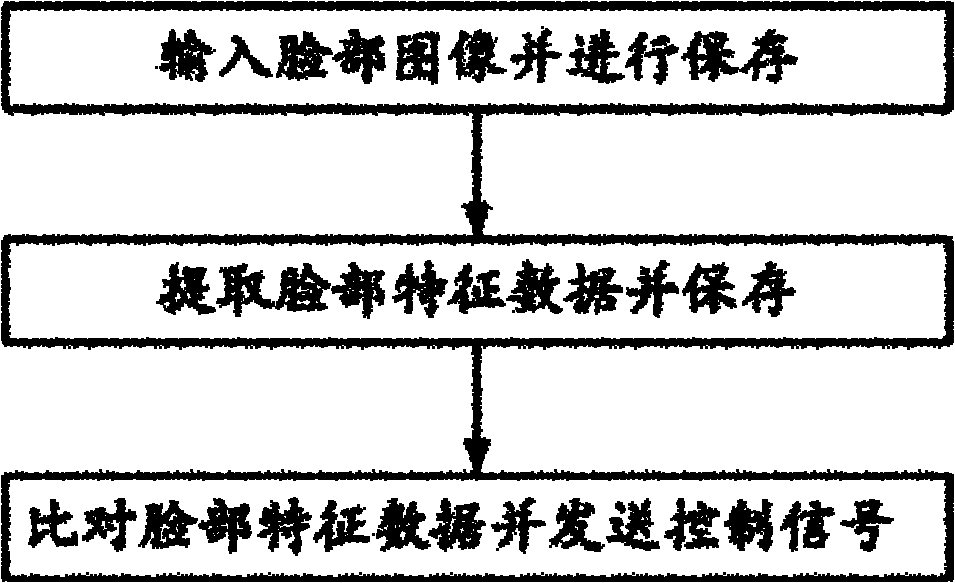
[0028] like image 3 As shown, this embodiment provides a method for implementing a facial recognition security mobile phone, which includes in turn:
[0029] Step 1) A step for inputting a face image and saving it; this step can be realized by using a camera or various interfaces.
[0030] Step 2) a step for extracting facial feature data and saving the facial feature data;
[0031] Step 3) A step for comparing facial feature data and sending a control signal according to the comparison result.
[0032] Described step 2) also comprises: the step that is used to carry out format conversion to the facial picture of input; The picture data format that described facial feature extraction module 4 identification can be set in the present embodiment is TIFF format, as described in step 1 If the input picture format is JPG format, JPEG format, GIF format, PNG format or BMP format, the above format must be converted to TIFF format.
[0033] like Figure 4 As shown, the step 3) co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com