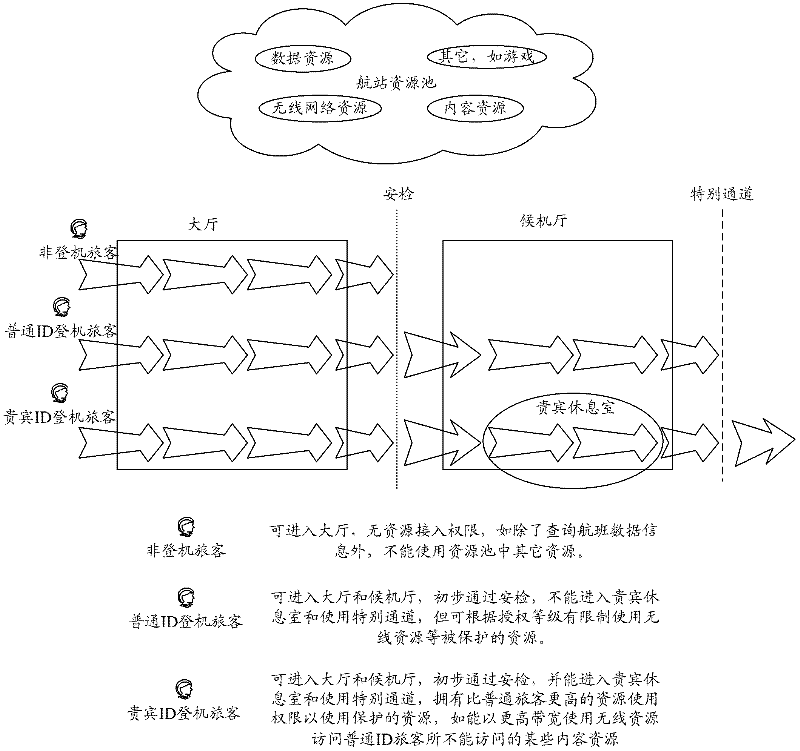
A method and system for implementing resource personalized security access control
A secure access and resource technology, applied in the field of communication, can solve problems such as low efficiency, difficulty in development and deployment, and poor resource service user experience, and achieve the effects of easy development, improved satisfaction, and easy deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
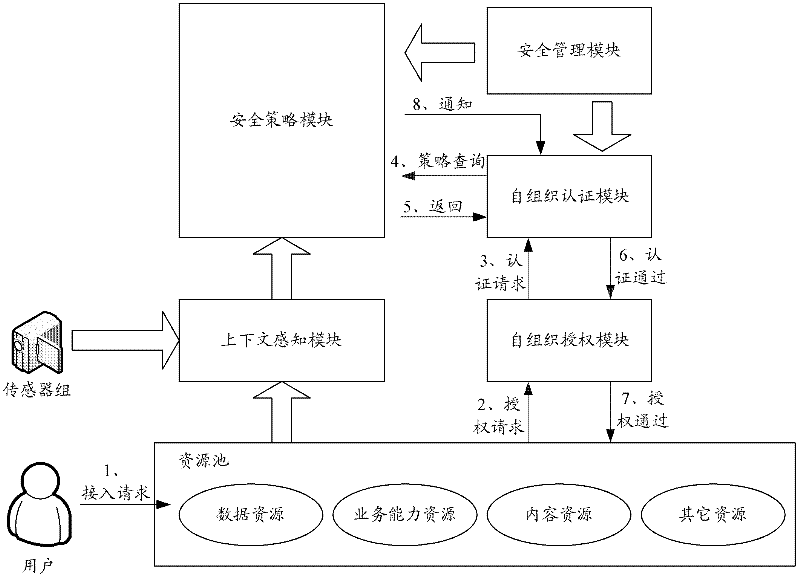
[0056] In practical applications, a system capable of realizing personalized security access control of resources in the Internet of Things can be provided, including:
[0057] The security management module is used for the input and management of the basic security policy parameters of the system security policy module, the self-organization authentication module and the self-organization authorization module.
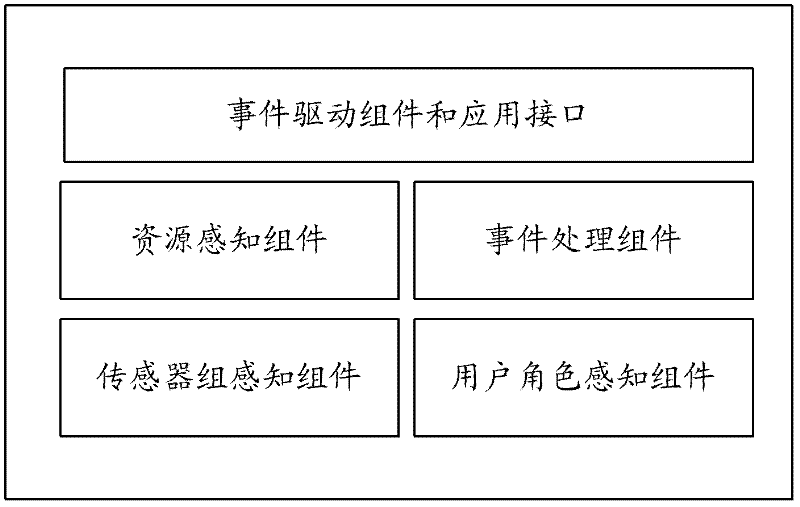
[0058] The context awareness module is used to receive user resource access requests, and receive, process and send the user's environment, various resource states related to user access requests, and other related events and object contexts. The context awareness module at least includes but is not limited to sensor group awareness components, user role awareness components, resource awareness components, event processing components, event drive components and application layer interfaces.
[0059] The security policy module is configured to receive the basic paramet...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com