Method for distinguishing suspicious spam message
A spam and suspicious technology, applied in the field of communication, can solve the problems of limited identification of spam messages and misjudgment by normal users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Embodiments of the present invention will now be described in detail in conjunction with the accompanying drawings.
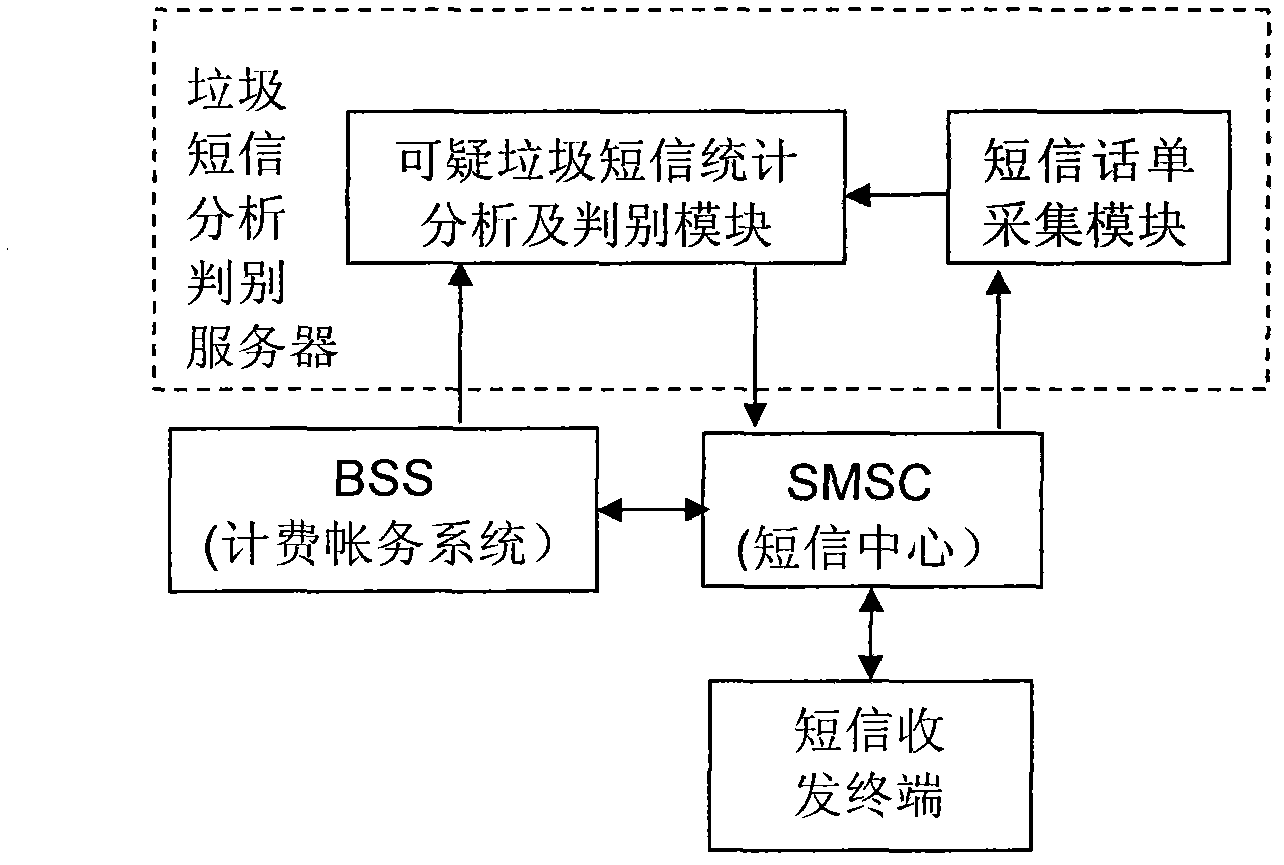
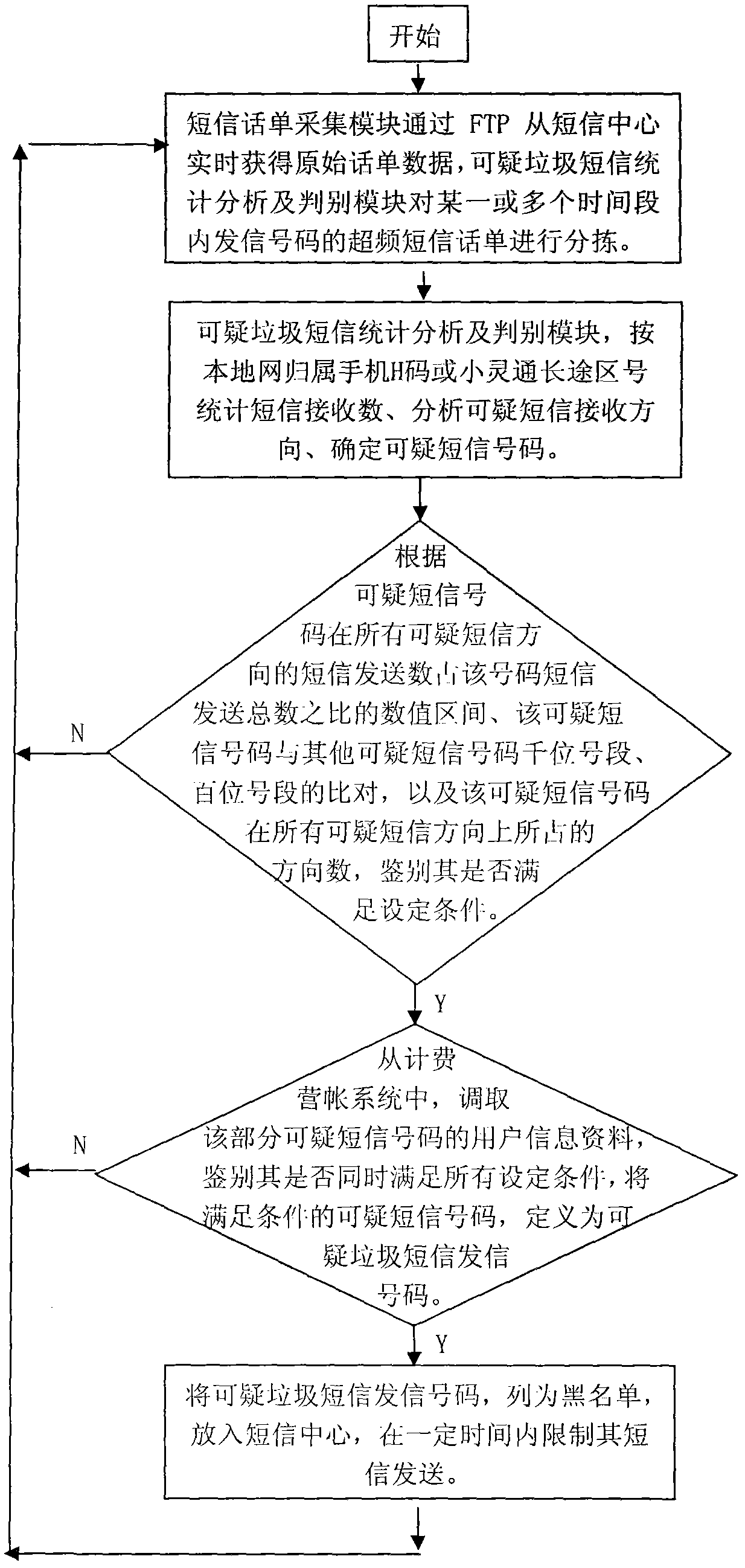
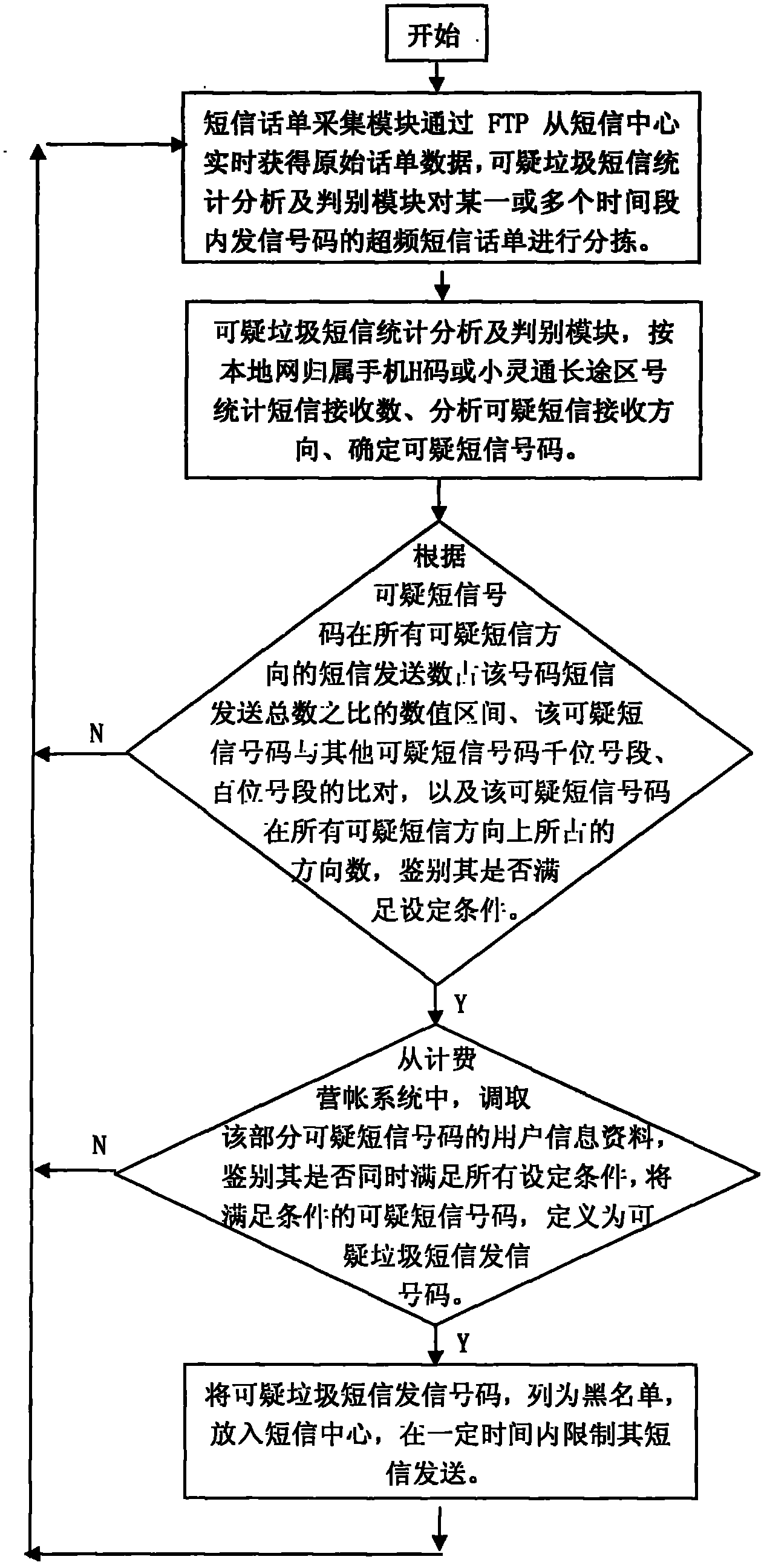
[0029] refer to figure 1 The network diagram of the suspicious spam short message discrimination system implemented by the present invention is shown, according to figure 2 The process of judging suspicious spam text messages shown, except major festivals: such as Spring Festival, Lantern Festival, Dragon Boat Festival, Mid-Autumn Festival, National Day, New Year’s Day, May 1st, Christmas, Valentine’s Day, Father’s Day, Mother’s Day, etc., spam text message analysis and identification server The short message bill collection module collects short message bills from the short message center, and the suspicious spam short message statistical analysis and discrimination module of the server analyzes the suspicious short message receiving direction and suspicious short message number of overfrequency signal codes in one or more time periods, and sends suspi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com