Malicious program judging method based on cloud security
A malicious program and security technology, applied in the computer field, can solve the problems of large attack harm, contradictory number of signatures, limited detection coverage, etc., to reduce performance overhead, ensure diversity, and improve coverage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
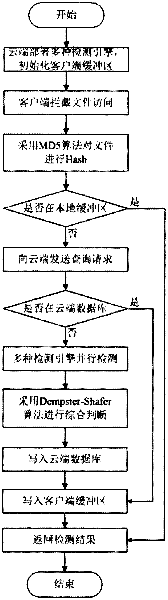
[0036] Example: such as figure 2 As shown, a method for judging malicious programs based on cloud security of the present invention, the steps are:
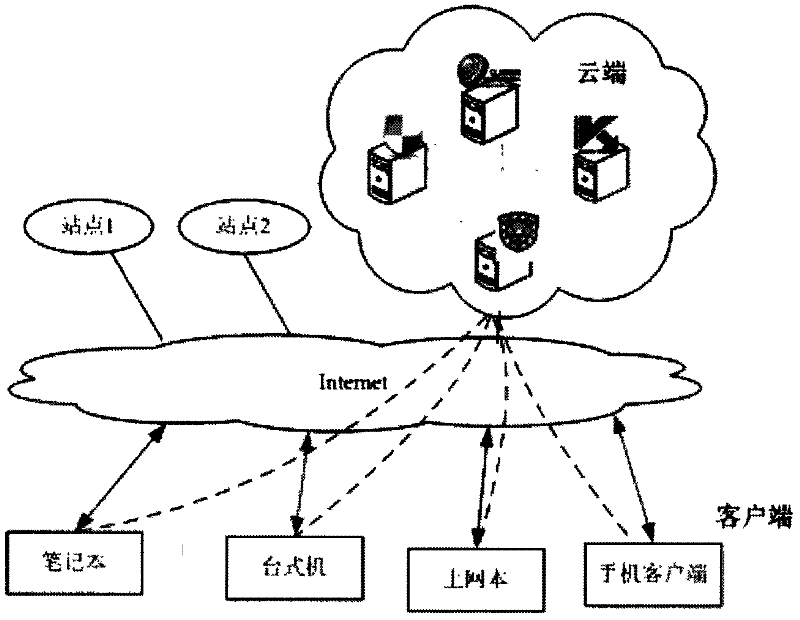
[0037](1) Deploy at least two different types of detection engines in the cloud. These detection engines can be deployed in physical machines or virtual machines. Deploying in virtual machines can improve resource utilization; the detection engine we use Refers to open source antivirus software that scans and kills malicious programs.
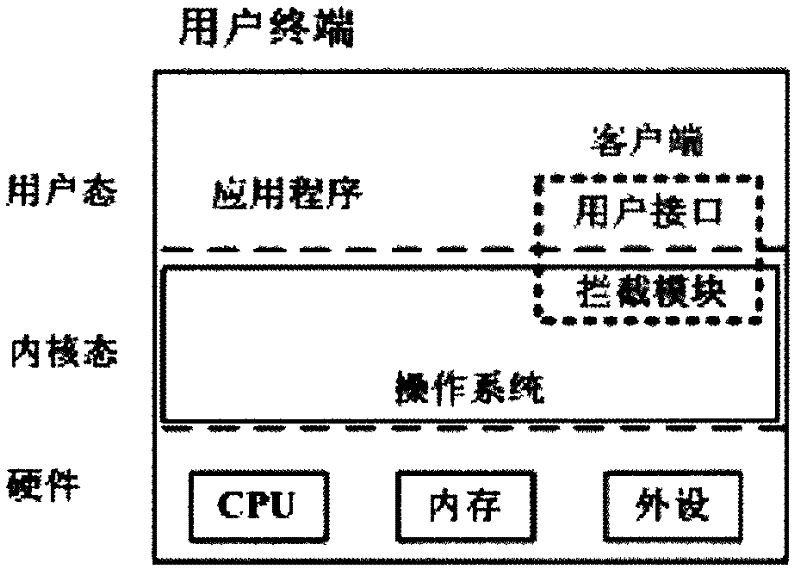
[0038] (2) The client intercepts the execution of the program, and calculates the unique identifier of the program, which can be obtained by hash calculation using the MD5 algorithm, or by using similar algorithms such as SHA1;
[0039] (3) If the unique identification value of the program exists in the local buffer, then directly return the final judgment result, and turn to step (9). Otherwise, send a query message to the cloud. After receiving the query message, the cloud will search in the ...
example
[0058] The configuration situation in the implementation process of this method is illustrated below with an example.
[0059] In order to improve resource utilization, all detection engines are deployed in virtual machines, of course, they can also be deployed in physical machines. First, install the virtual machine manager-Xen on two physical nodes, and the hardware and system configuration of each physical node are shown in Table 1.
[0060] physical node
CPU
Memory
hard disk
virtual machine manager
Node1
2 Intel Xeon E5310
4GB
160GB
Fedora Core 8
Xen
Node2
2 Intel Xeon E5310
4GB
160GB
Fedora Core 8
Xen
[0061] Table 1 Hardware and system configuration of the physical platform
[0062] One management domain and two virtual machines are deployed on each physical node, and one detection engine is deployed in each virtual machine. The basic configuration of each de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com