Flow rate security detection method, equipment and system
A security detection and traffic technology, applied in the field of network communication, can solve the problems of inability to distinguish between different traffic types, hidden dangers of network information and communication security, and inability to realize in-depth detection of packets, so as to achieve the management and control of traffic and content and realize security Monitoring and ensuring the effectiveness of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
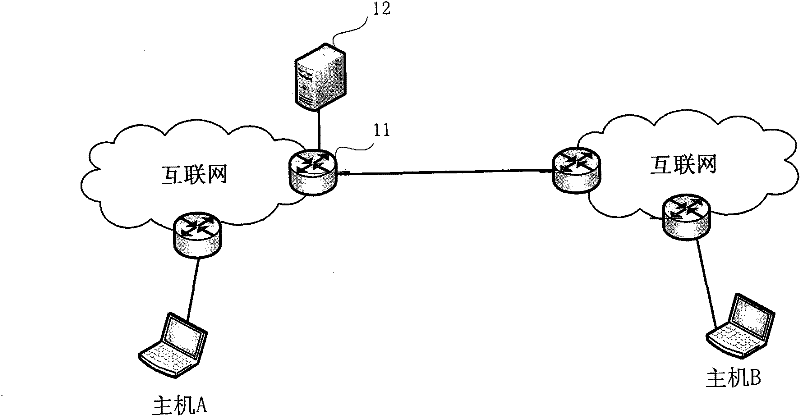
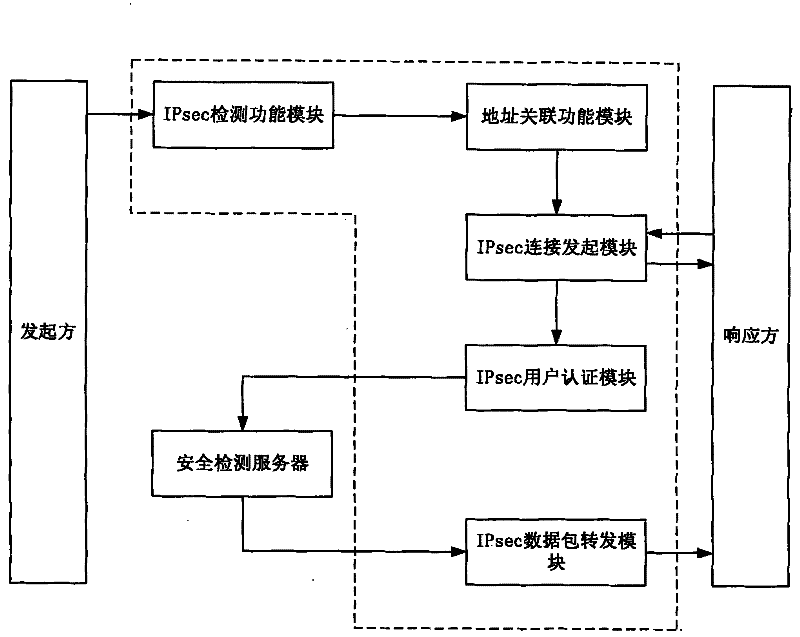
[0067] An embodiment of the IPSec flow security detection system of the present invention, see figure 1 shown. It mainly includes: gateway equipment and security detection server. in,
[0068] Gateway device 11: Placed between the security network domain of the initiator host A and the network of the responder host B, it is a gateway device that supports layer-3 routing functions and can implement the relay and routing functions of user data streams. In the preferred embodiment of the present invention, the gateway device 11 is located at the edge exit of the security area, and realizes the functions of IPsec detection, user authentication, response address association and IPsec data packet forwarding.
[0069] Securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com