ECU (Electric Control Unit) security access processing method
A processing method and security access technology, applied in the field of ECU security access processing, can solve the problems of easy leakage and low confidentiality, and achieve the effects of improving security, avoiding tedious calculations, and shortening operation time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
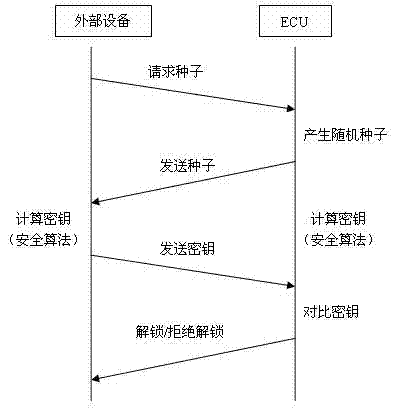
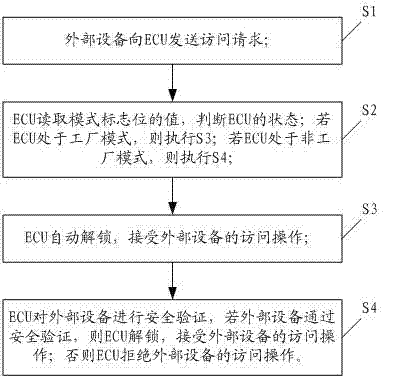
[0021] see figure 2 , is a schematic flow chart of the ECU security access processing method provided by the first implementation of the present invention.
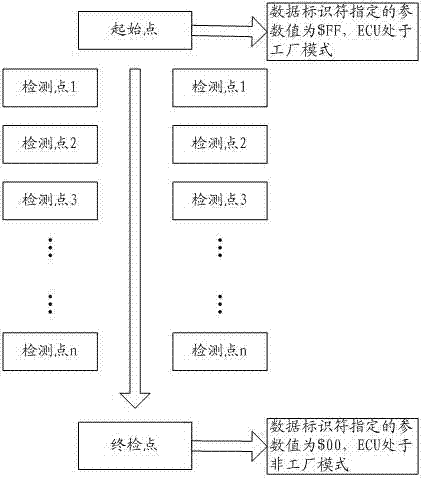
[0022] The embodiment of the present invention divides the ECU sample into a factory mode and a non-factory mode: the ECU is set to the factory mode when it is on the production line, and the ECU is set to the non-factory mode when it leaves the factory. The ECU in the factory mode can accept the access operation of the external device without security verification; the ECU in the non-factory mode must pass the security verification before accepting the access operation of the external device.
[0023] It should be noted that "the ECU is on the production line" includes not only the situation where a single ECU componen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com