'Gene network identity management' method based on depth identification and registration
An identity management and network technology, applied in the field of information security, can solve problems such as inability to meet accurate identity identification and control, identity identification uncertainty, and poor accuracy, and achieve the effects of improving accuracy, ensuring accuracy, and reducing coincidence probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but not as a limitation of the present invention.
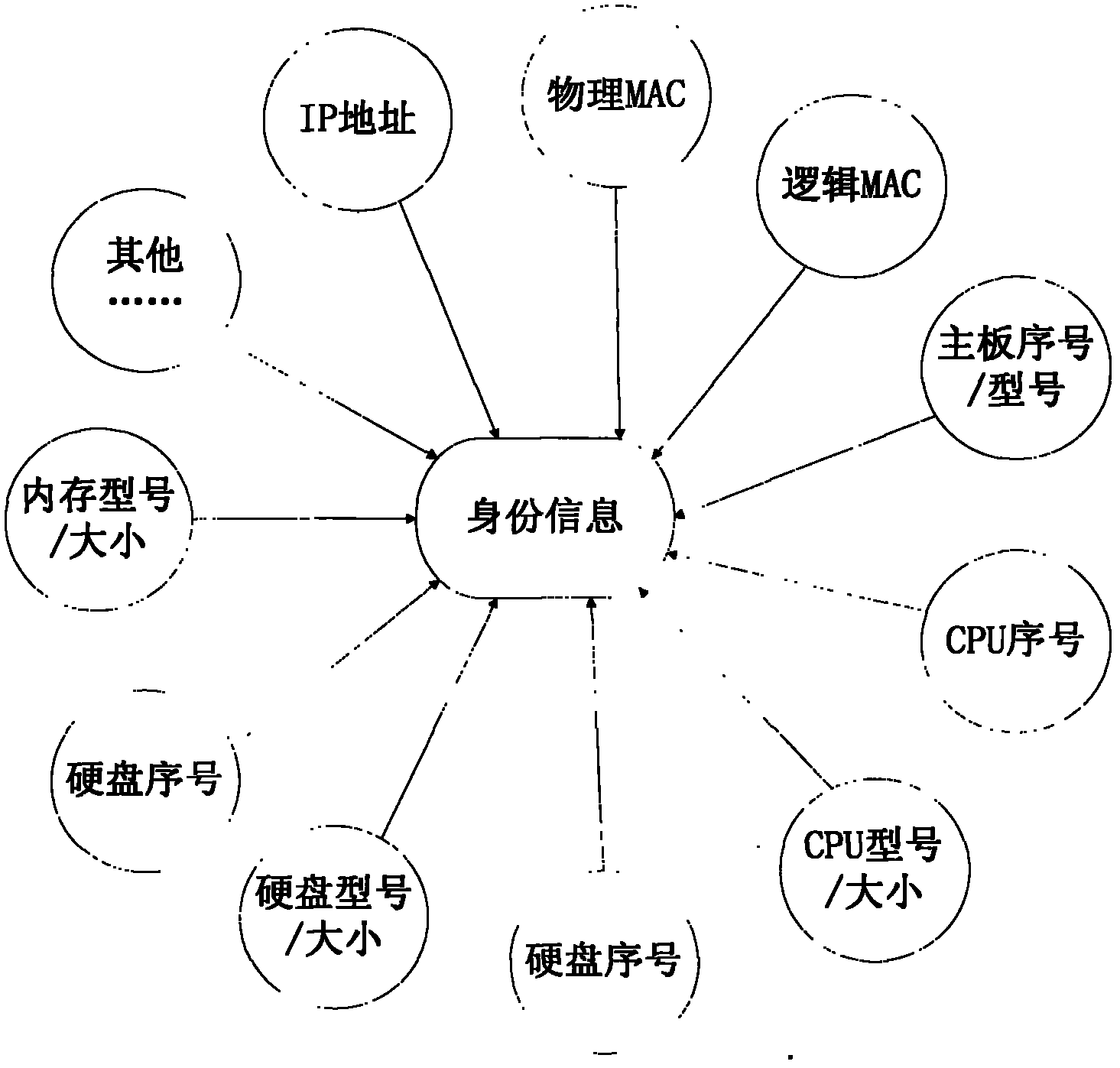
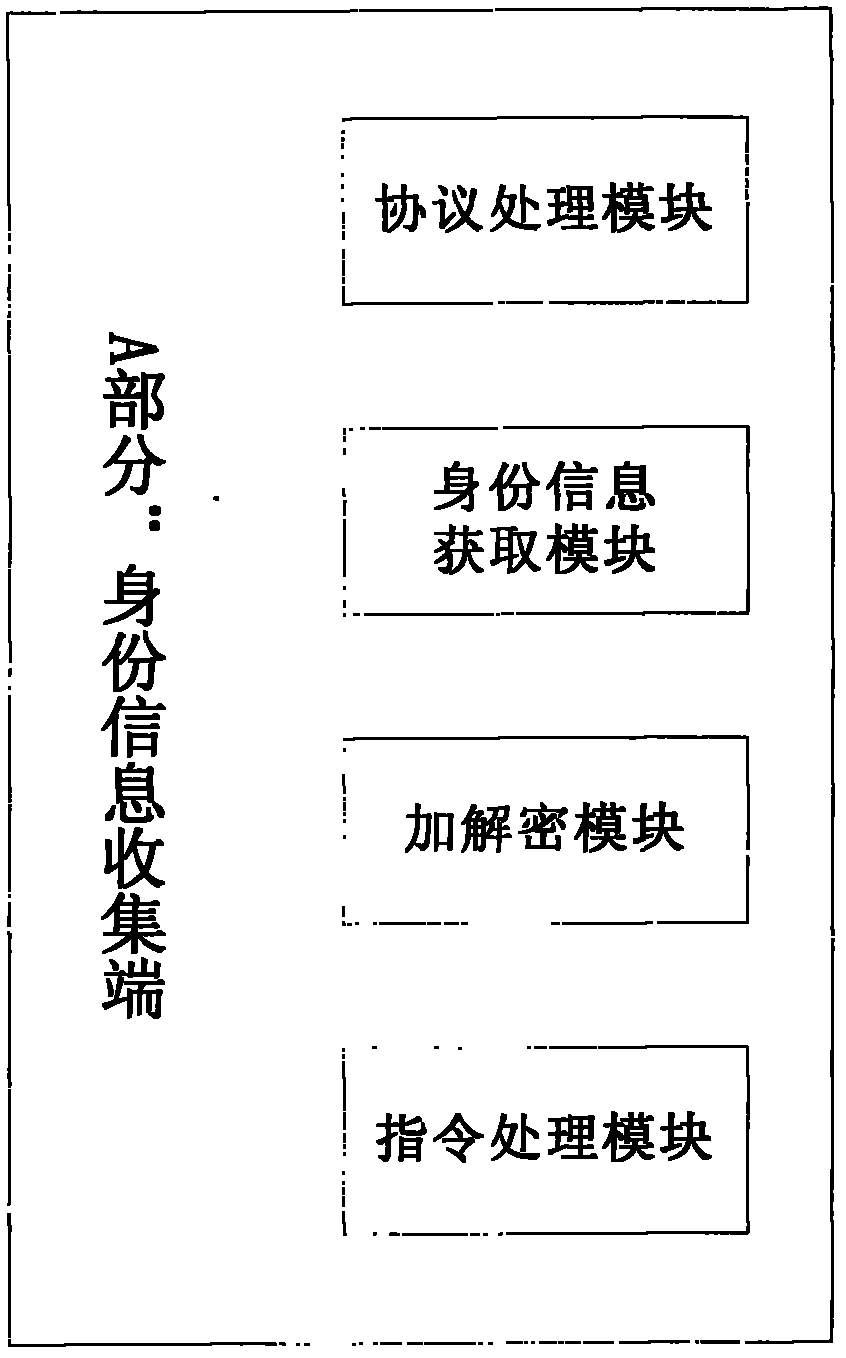
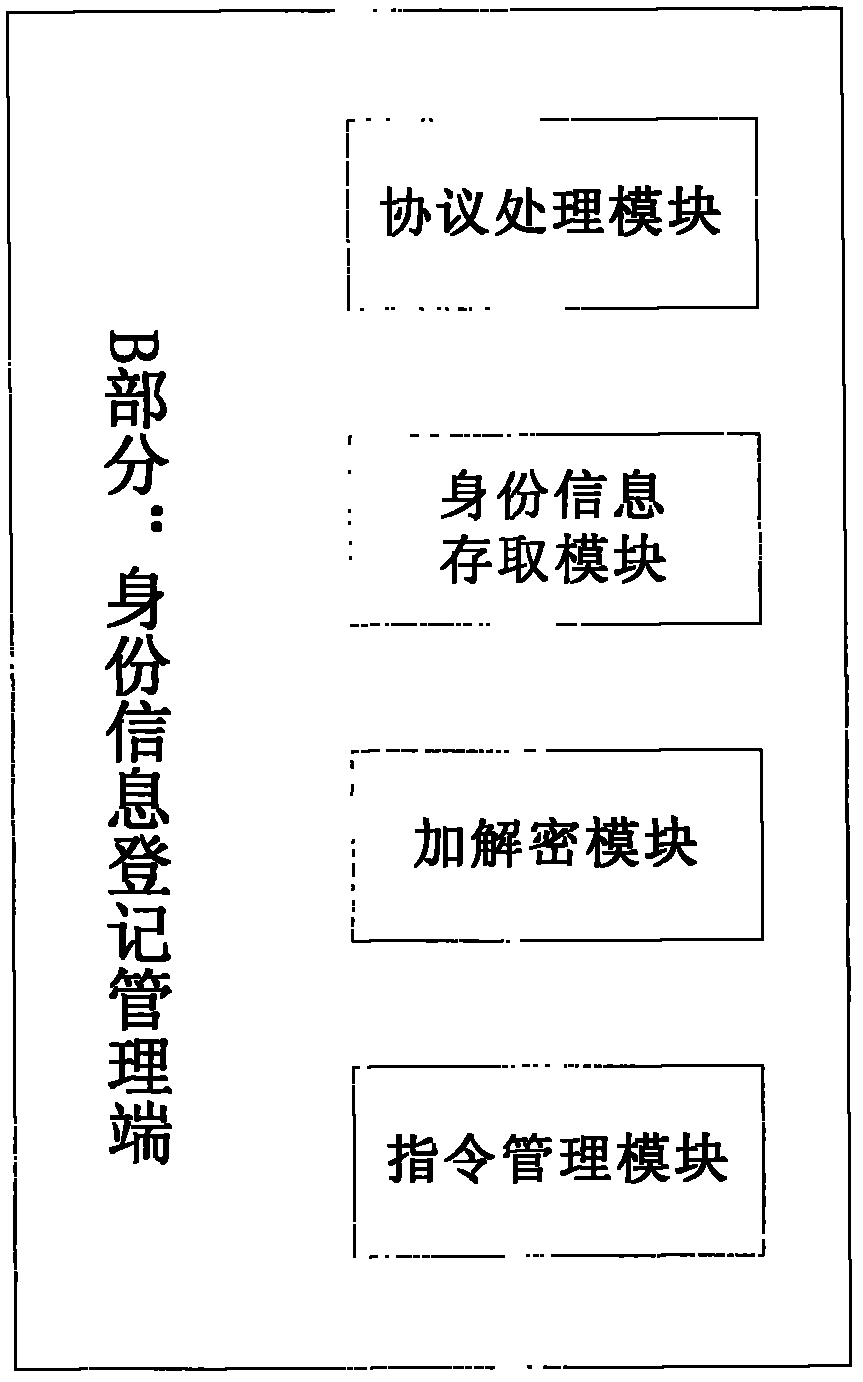
[0022] The present invention adopts the following technical solution: obtain the identity information of the device through a specified program running on the network device or terminal, the identity information includes IP address, physical MAC, etc., and transmit these information to the registration management terminal through an encrypted private protocol, so as to To prevent information from being modified, the system running on the management terminal can be an open system or a dedicated embedded system device. Under higher security requirements, the management terminal must be an embedded special device, so that the storage of identity information is more secure. The characteristics of the genetic identity registration adopted by the present invention are mainly manifested in: 1. Informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com