Method suitable for RSA modular exponentiation calculation
A modular exponentiation and modulus technology, applied in the application of chips, fast and safe, can solve the problems of no randomization, power consumption difference, high time cost, etc., and achieve the effect of reducing the number of cycles, safe calculation, and reducing time cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention proposes a fast and safe method suitable for RSA modular exponentiation calculation, comprising the following steps:
[0018] Step 1. Obtain a random number R';
[0019] Step 2. Calculate the inverse value R of R' to the RSA modulus n, that is, R=R' -1 mod n;
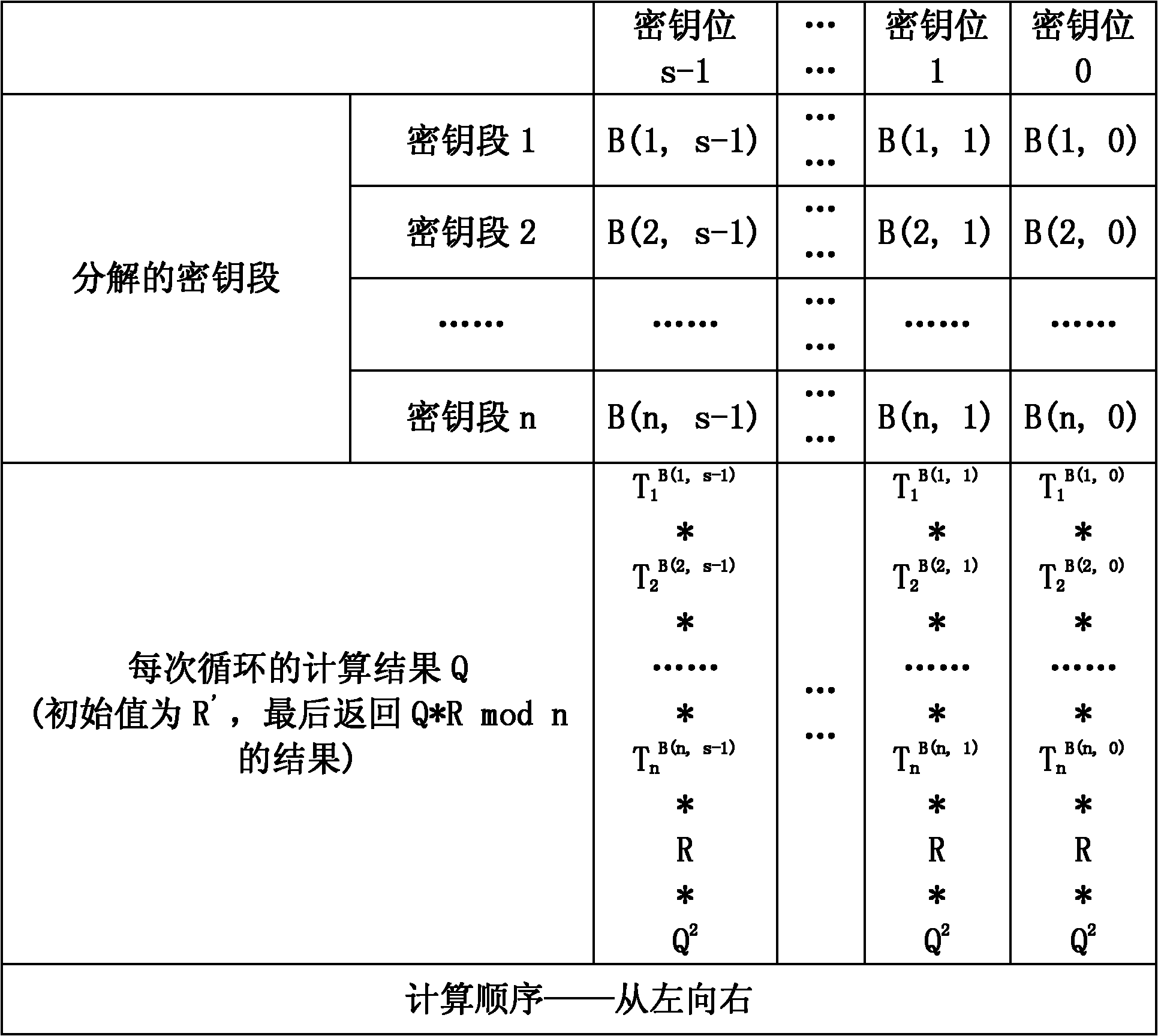
[0020] Step 3. Divide the index into r segments on average, and the length of each segment is s bits;
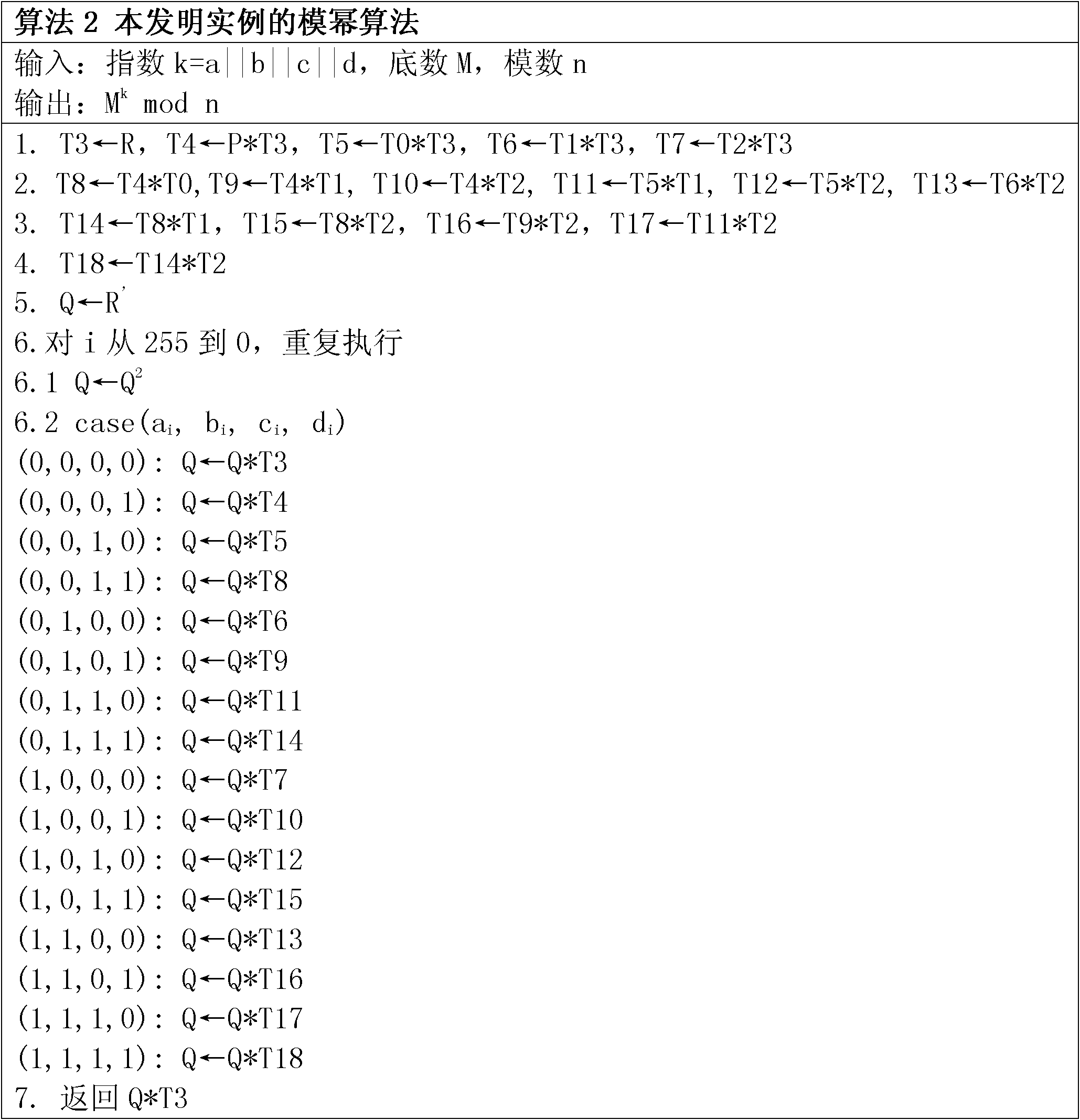
[0021] Step 4. Calculate T 1 =M(RSA modular power base), T i+1 = 2 s ·T i , where (i=1, 2, ..., n);
[0022] Step 5, pass figure 1 The flow shown performs RSA modular exponentiation calculation, where "*" represents a modular multiplication operation, and "X 2 "Indicates the modular square operation, the modulus is the modulus n of RSA, and the value of B(i, j) is {0, 1}.
[0023] A random number R' described in step 1 includes all random numbers with more than 16 bits (including 16 bits).
[0024] Calculation R' described in step 2 is to the modular inverse value R of RSA modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com