Method and device in communication system
A technology of equipment and mobile equipment, which is applied in the field of telecommunication systems, can solve problems such as loss of important services, and achieve the effect of avoiding access attempts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
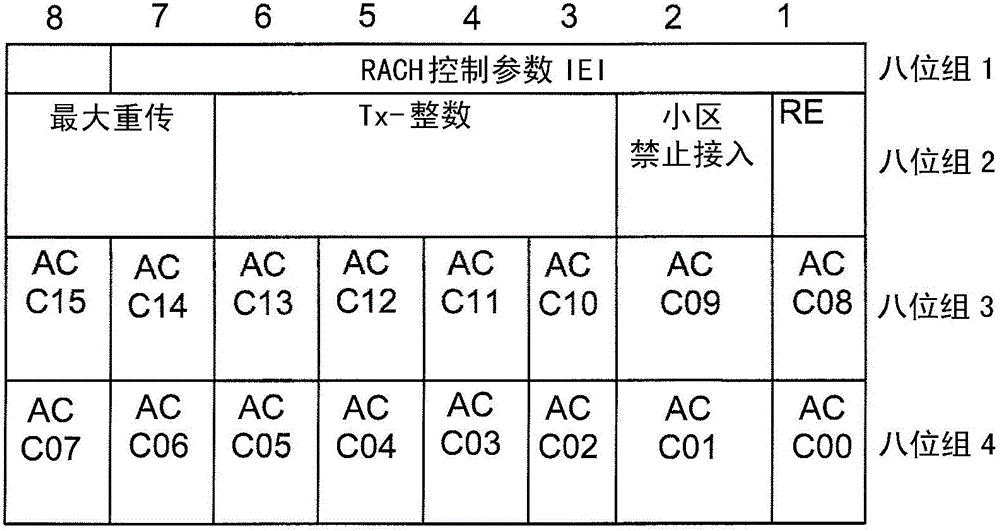
[0103] Example 1: Extension of existing "RACH Control Parameters" information element
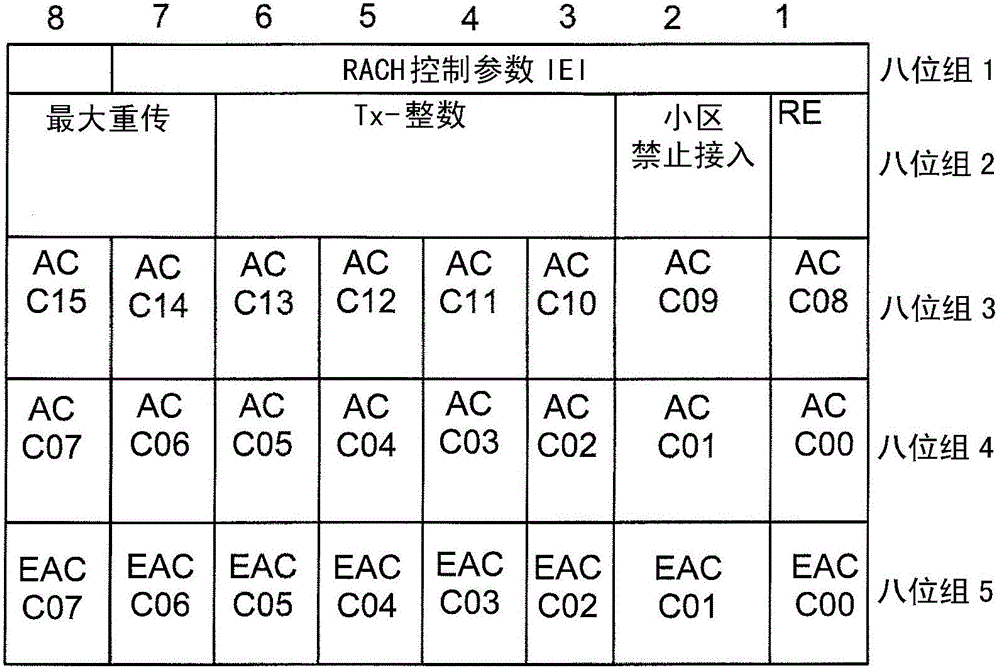
[0104] according to figure 2 , the RACH control parameters are extended for the example case of 8 new "Extended Access Control Classes": EACCC00-C07 in octet 5.
[0105] figure 1 Shows the RACH control parameter information element, extended with 1 octet of "Extended Access Control Class" bits, denoted as "EACCxx". The corresponding description to be inserted in Table 10.5.2.29.1 in 3GPP TS 44.018 is shown in Table 3 below:
[0106] Table 3 RACH control parameter information element (excerpt from Table 10.5.2.29.1 in 3GPPTS44.018)
[0107]
[0108] Alternatively, the above example with 8 "Extended Access Control Classes" can be extended to eg 16 such "Extended Access Control Classes" by adding another octet to the "RACH Control Parameters" information element.
[0109] The disadvantage of this method is that the scheme is not backward compatible, because the existing 3GPPTS44.018 mo...
example 2
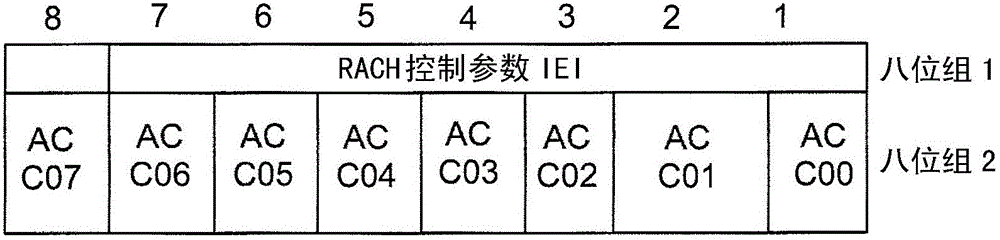
[0110] Example 2: Creating a new "Extended RACH Control Parameters" information element
[0111] To ensure backward compatibility, instead of extending the existing RACH Control Parameters information element of 3GPPTS 44.018 as described above, a new "Extended RACH Control parameters" information element. This does not need to contain any other information than the new "EACCxx" bits (eg Tx integer, cell access barring, etc.) as these are already included in the (mandatory) "RACH Control Parameters" information element. Therefore, the new information element can be as image 3 shown. image 3 The "Extended RACH Control Parameters" information element is shown, containing only the "RACH Extended Control Parameters IEI" and "Extended Access Control Class" bits (denoted as EACCxx).
[0112] In, for example, a system information type 1 message, a new "extended RACH control parameter" may be added as an optional information element, as shown in Table 4 below, where the addition ...
example 3
[0118] Example 3: Add "Extended Access Control Class" information to the remaining octets
[0119] An alternative to the scheme described above in Example 1 and Example 2 is to add "extended access control class" information to the remaining octets of the corresponding system information message, rather than creating a new information element. As an example, for System Information Type 1, this can be achieved by modifying the remaining octets of SI1 described in 10.5.2.32 of 3GPPTS 44.018 as follows:
[0120]
[0121] For 8 instances of such classes, the remaining octets of SI1 are extended with the "extended access control class" bits
[0122] The corresponding description to be inserted in Table 10.5.2.32.1a of 3GPPTS 44.018 is according to Table 5 below:
[0123] Table 5 Details of the remaining octet information elements of SI1 to be added in Table 10.5.2.32.1a of 3GPPTS 44.018 for "Extended Access Control Category"
[0124]
[0125] Any (3GPPTS 44.018) legacy MS o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com